New incident response platform aims to improve cyber resilience

According to a recent study by the Ponemon Institute, more than 90 percent of organizations recognize cyber resilience as an essential part of protecting their core assets and business interests.
Part of creating that protection is to have an effective plan for when things go wrong and incident response solutions specialist Resilient Systems is releasing version 24 of its Incident Response Platform (IRP). The release features strategic integrations with IBM X-Force's threat intelligence feed and HP ArcSight, enabling organizations to gain insight more quickly and respond more intelligently to cyber threats and attacks of all types.
What's the real cost of the UK's Investigatory Powers law?

The Home Office has issued an Impact Assessment, looking into the price of the proposed Investigatory Powers law, which would allow government agencies to intercept digital communications.
Secretary of State Theresa May’s department estimates a price of some £247m over a 10-year-period to cover the costs of the spy law, but according to The Register, which calls upon industry sources, little to no consultation has taken place so far. The true price of the bill can be significantly larger and can go up to £2 billion, with the bulk of finances going to telecom firms to cover the costs of storage.
Apple's giant iPad Pro goes on sale this week

After years of rumors regarding a super-sized tablet, Apple finally took the wraps of its iPad Pro two months ago. The new device has a 12.9 inch screen, with a 2,732 x 2,048 resolution and 5.6 million pixels.
If you’ve been thinking of buying one, the good news is the device will be available to order online from Wednesday and will be in stores later this week.
Apple IDs targeted in global phishing scam

A new phishing threat is targeting businesses and consumers with Apple IDs in an effort to steal IDs, passwords and credit card information.
The attack has been identified by Comodo Antispam Labs and looks like an official Apple email. It has the Apple logo and includes Apple's physical address, as well as an email address that, at a quick glance, appears to to be from Apple -- giving the recipient the illusion of the message being authentic.
Xiaomi's new Mi Band 1s offers a heart rate sensor for less than $16

Xiaomi has taken the wearables market by storm with Mi Band. The unassuming fitness tracker arrived more than a year ago with a price tag shy of $30 but with a feature set that rivals other offerings costing more than three times as much. Thanks to sales of over 10 million units, it has turned the ever-growing Chinese company from the new kid on the block into the third-largest wearables maker.
But, in the time following the launch of Mi Band, Xiaomi's competitors have diversified their lineups, introducing new models with novel features that make it seem a bit dated in comparison. Enter the second-generation Mi Band, called Mi Band 1s.
Post-Stagefright analysis shows Android users remain indifferent to attacks

In the past few months, Android users have seen a series of attacks by hackers exploiting bugs, collectively putting more than a billion devices at risk worldwide.
In late July, Stagefright hit the news as a weakness in the system that was being exploited by hackers. This was followed by Stagefright 2.0 and Kemoge, making for massive malware attacks on Android phones in three out of the last four months.
Poor management of admin accounts puts businesses at risk

Login details for an administrator or other privileged account falling into the wrong hands can have serious consequences for a business.
But a new global security survey from Dell reveals that organizations have haphazard processes for managing administrative or other privileged accounts, making them vulnerable to security breaches.
Most IT pros are against UK's Investigatory Powers bill

Late last week, the UK government introduced a new Investigatory Powers bill, which requires Internet service providers to keep a record of the Internet activity of everyone in Britain, as well as cracking down on encryption and increasing government surveillance.
The initial reaction from industry professionals was mixed, but a new survey from Swiss data bank Artmotion has found that a massive 87 percent of IT leaders disagree with the government’s plan to reduce the strength of data encryption.
Pinterest's crazy new search tool helps out when words fail you
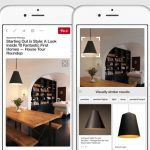
For years now we have been using words to perform searches -- but words have their limitations. It is said that a picture is worth a thousand words, and this is something that Pinterest has taken to heart with its latest search tool.
There are times when words fail us all. You might know exactly what it is you want to say, but you have no idea how to say it. To help on such occasions, Pinterest today unveils a "crazy-fun new visual search tool" that lets you select an object in an image to search for other pictures of it. Confused?
How to easily access Google Drive files from Microsoft Office
AMD hit with deceptive marketing lawsuit over Bulldozer chip core claims

Chip-maker AMD faces a lawsuit for misleading adverts for its Bulldozer processors. The legal action has been started by Tony Dickey at the US District Court for the Northern District of California, San Jose Division; the allegation is that the Bulldozer CPU is advertised as having 8 cores, but it effectively has just 4.
The architecture of the chip is such that each of the cores is unable to operate independently meaning that it functions in the same way as a 4-core processor. AMD faces allegations under the Consumer Legal Remedies Act, California’s Unfair Competition Law, as well as false advertising, fraud, breach of express warrant, negligent misrepresentation and unjust enrichment.
Facebook censors links to social network Tsu.co

Anyone who tries to post links to Tsu.co on Facebook, Facebook Messenger, or Instagram will find that they are unable to do so. If you've not heard of Tsu.co, it's another social network, and your initial thought may be that Facebook is trying to censor people from talking about rivals.
Facebook blocks any messages containing the URL from being posted, warning that the site is 'unsafe'. Tsu.co different from other social networks in that it is invite-only and promises to share ad-revenue with users. This has resulted in huge levels of Tsu.co-related spam appearing on Facebook and the susequent ban.
Pandora makes music discovery even easier
Music services are an ever increasing market, with new ones popping up all the time. There are a few that have distanced themselves from the pack, though. One of those is Pandora which takes a song and analyzes it in an effort to create a station with similar music. You can argue if this works, but it does in most cases, at least based in my experience,
Now Tim Westergren's little hobby is launch an enhanced discover service in an effort to make it even easier to find music.
Want a Pebble Time Round? It's heading to stores and begins shipping soon

While I have made a bit of fun of the Pebble Time Round's Swatch-type look, that doesn't mean it's a bad product. Honestly Pebble is the product that opened the public's eyes to smartwatches. It wasn't the first, but it set the tone of what to expect with the future of wearable technology.
The round version of the latest watch was creatively called Time and it was a huge hit on Kickstarter when it debuted. The round version came along later and now it's here, hitting retail outlets and ready to start shipping for those who have, or wish to, get it online.
The NSA keeps 9 percent of the vulnerabilities it discovers to itself

Openness and the NSA are not happy bedfellows; by its very nature, the agency is highly secretive. But in recent years, post-Edward Snowden, the organization has embarked on something of a PR campaign in an attempt to win back public trust.
The latest manoeuvre sees the NSA promoting the fact that when it discovers security vulnerabilities and zero-days in software, it goes public with them in 91 percent of cases... but not before it has exploited them. No information about the timescale for disclosures is given, but what most people will be interested in is the remaining 9 percent which the agency keeps to itself.
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.