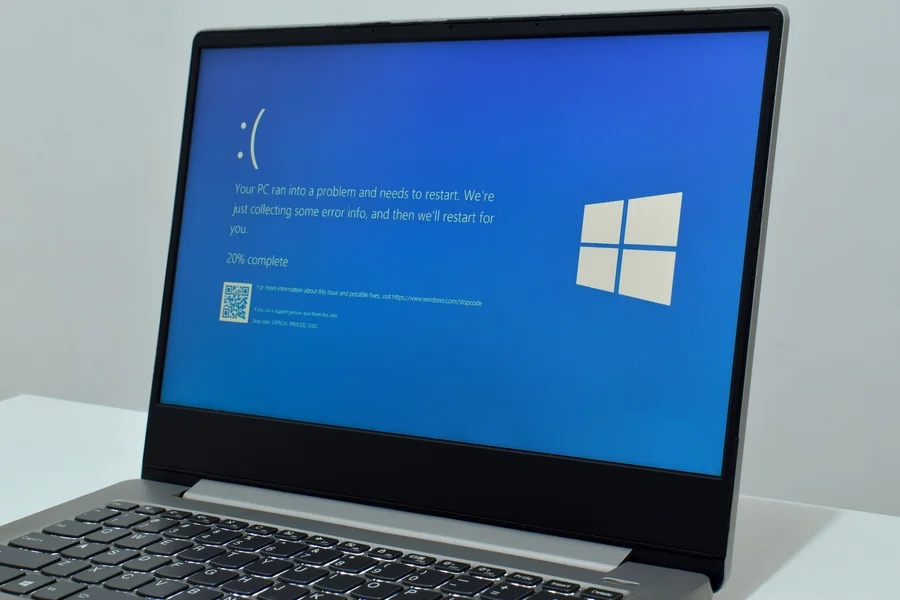
Will Windows 10 stop working? See if your PC will survive the switch to Windows 11
Microsoft reminded users this month that Windows 10 support officially ends on October 14, 2025, but here’s what’s new: for the first time, regular users will have to pay to keep getting security updates after that.
The company confirmed it will offer Extended Security Updates (ESU) starting in late 2025, a program once reserved for businesses. Pricing hasn’t been finalized for individuals, but Microsoft has made it clear: no more free patches after the deadline.

Chaos RAT malware strikes Linux and Windows as hackers exploit its flaws
Chaos RAT is back and causing trouble on Linux and Windows systems. This open source remote access tool was once pitched as a legitimate way to manage computers remotely. Now, it is being used to spy on users, steal data, and possibly set the stage for ransomware. But in an ironic twist, attackers are now turning the tables and exploiting Chaos RAT itself.
Originally written in Go and designed for cross platform compatibility, Chaos RAT has evolved from a basic tool into a very dangerous piece of malware. It has been spotted in real world attacks including a recent sample disguised as a Linux network utility. Victims were likely tricked into downloading a fake troubleshooting tool containing the malware.

Lack of 'digital dexterity' set to harm public sector AI investment
We reported a few weeks ago on the challenges businesses face in getting workers to adapt to new generative AI technology.
The latest report from digital experience specialist Nexthink, based on a survey of 220 public sector IT decision makers, shows that this is a particular problem in the public sector, with 96 percent of IT leaders believing this new era of digital transformation will increase digital friction.
Shadow AI a major concern for enterprise IT
A new report reveals that nearly 80 percent of IT leaders say their organization has experienced negative outcomes from employee use of generative AI, including false or inaccurate results from queries (46 percent) and leaking of sensitive data into AI (44 percent).
Notably the survey of 200 US IT directors and executives from Komprise shows that 13 percent say that these poor outcomes have also resulted in financial, customer or reputational damage.

84 percent of attacks now use legitimate tools
New research from Bitdefender shows that 84 percent of high severity attacks are using Living off the Land (LOTL) techniques, exploiting legitimate tools used by administrators.
One of the findings is that the netsh.exe tool -- used for network configuration -- management is the most frequently abused tool, appearing in a third of major attacks. While checking firewall configurations is a logical initial step for attackers, this clearly demonstrates how data analysis can spotlight trends that human operators might instinctively disregard.

Elon Musk confirms everyone is getting the 'all new' XChat this week, complete with 'Bitcoin style encryption'
Looking to compete with the likes of Signal, Elon Musk is ready to rollout XChat to all users of his X social platform. Rather than being a separate app for chatting, however, XChat is essentially just direct messaging within X -- so who is it for, and what does it have to offer?
Taking inspiration from numerous sources, Musk says that in addition to text-based messaging, there is also video and audio calling. Other features include vanishing messages, the option to “send any kind of file”, and an undetailed encryption system.
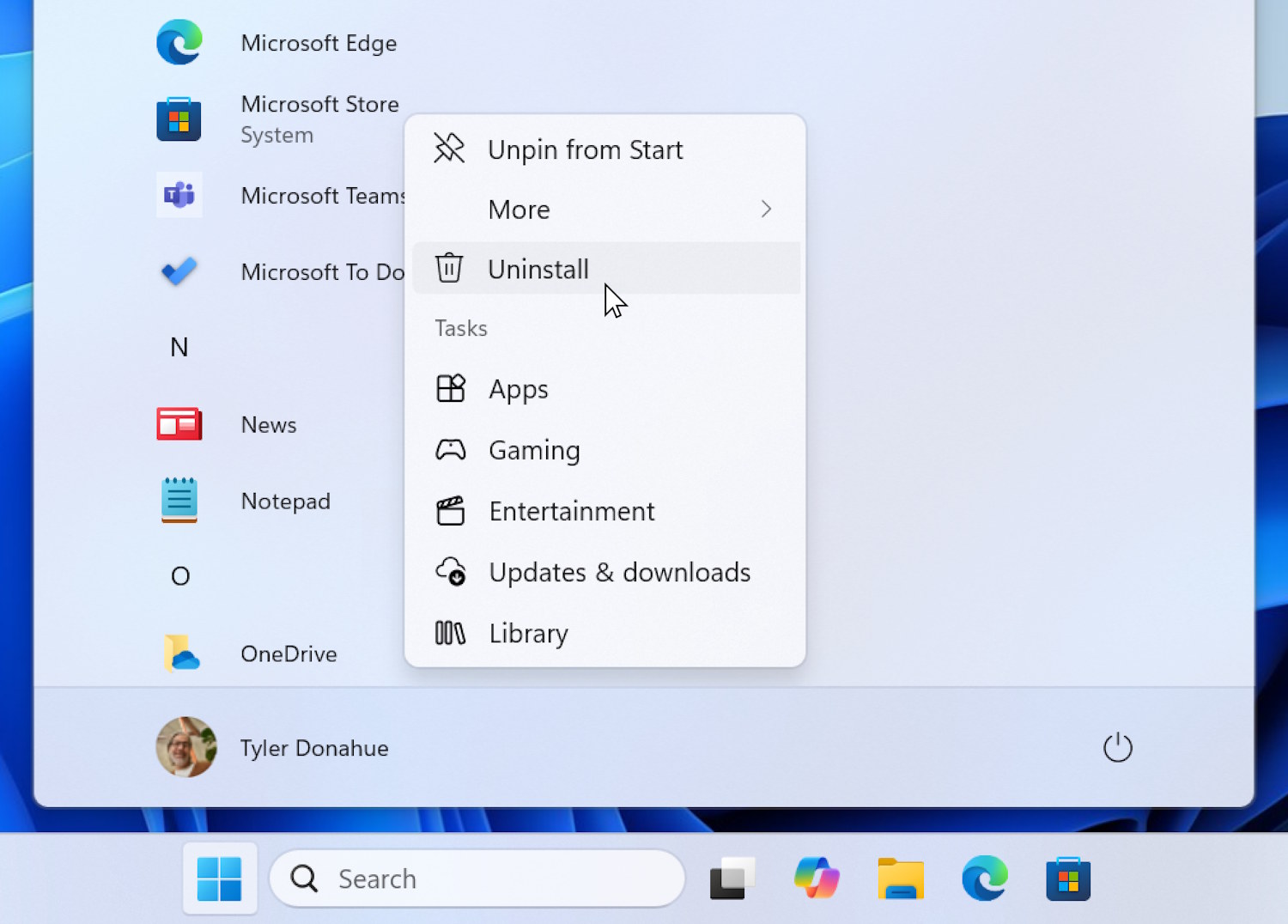
Microsoft is making huge changes to Windows 10 and 11, cutting out nagging to use Edge... for some
There can be few Windows users who have not been frustrated by notifications suggesting that they use Microsoft Edge as their browser. Microsoft’s heavy-handed promotion of its own web browser has been the source of annoyance, frustration and lawsuits for some time.
Now the company is relenting, making sweeping changes across Windows 10 and Windows 11 that will stop some of the pestering to use Edge, and also make it easier to change default browsers. More than this, it is making changes to Windows Search, the Microsoft Store and many other apps... but not for everyone, and not because it wants to.

Vendor email compromise attacks get more effective in large enterprises
A new report from Abnormal AI shows that employees in large enterprises engage with malicious vendor messages 72 percent of the time.
Drawing on behavioral data from over 1,400 organizations worldwide, the report reveals the extent to which employees are actively engaging with advanced text-based threats like vendor email compromise (VEC) and explores the blind spots attackers are exploiting with highly targeted, socially engineered attacks.

Meeting the challenges of running a modern service desk [Q&A]
In today's interconnected world, the IT service desk often serves as the invisible backbone of any successful organization, from troubleshooting minor glitches to resolving critical system outages.
But beneath this seemingly straightforward function lies a complex web of challenges that can significantly impact efficiency, user satisfaction, and ultimately, an organization's bottom line.

Microsoft releases emergency fix for Windows 11 startup problems
Following the release of the KB5058405 update last month, Microsoft acknowledged that it was causing problems for some users. Affected users were left with startup issues and a warning of a 0xc0000098 error in the ACPI.sys file.
Now the company has released an out-of-band fix for the issue in the form of the KB5062170 update. Such is the impact of the original problem that Microsoft recommends installing this update in place of the May 2025 security update for Windows 11.
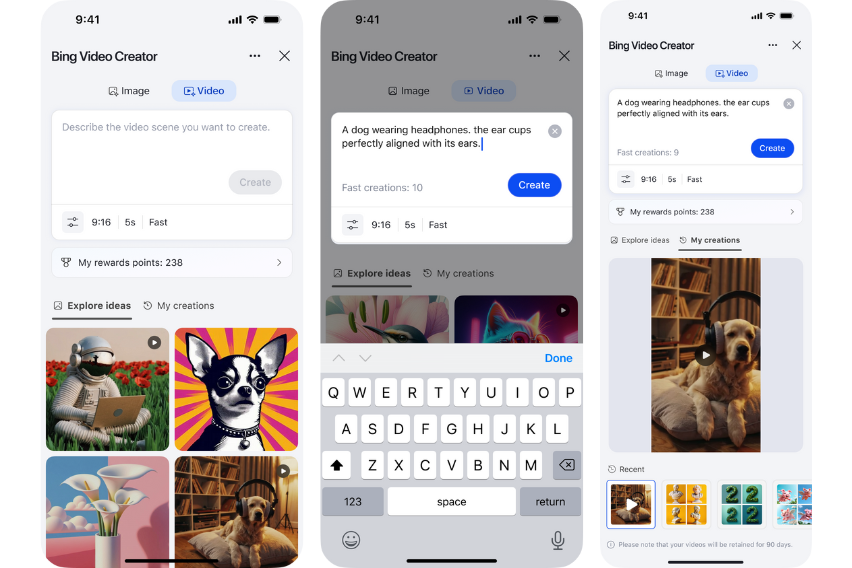
Free AI video tool from Microsoft lets you create wild videos in seconds with Bing
If you’ve ever wanted to make your own video without picking up a camera, editing anything, or paying a dime, Microsoft just dropped something you absolutely must check out. It’s called Bing Video Creator, and yes, folks, it’s completely free.
This new tool, powered by OpenAI’s Sora model, turns simple text prompts into five-second videos. Just type what you want to see and boom, a video appears. No editing software, no experience, and absolutely no money required.

Microsoft and CrowdStrike finally fix the stupidest problem in cybersecurity
In cybersecurity, every second counts. But when the same hacking group goes by half a dozen different names depending on which company you ask, defenders are left wasting time instead of stopping attacks. Now, Microsoft and CrowdStrike are teaming up to clean up the mess they helped create.
The two companies just announced a joint effort to map their threat actor naming systems to each other. Basically, it’s a cheat sheet for decoding the confusing and conflicting names used across the industry. Midnight Blizzard? That’s Microsoft’s name for what CrowdStrike calls Cozy Bear. Others call it APT29 or UNC2452.

Fences 6.0 is the essential desktop upgrade for Windows 10 and 11 users -- get it today!
Stardock has released Fences 6.0, a major new release of its desktop organization tool for Windows users. The app, which allows users to create windowed 'fences' to keep desktop icons under control, adds two major new features in this latest release.
The biggest update by far is the support for tabbed fences. Like web browsers, each window can now support multiple tabs to provide an additional level of organization for both desktop shortcuts and Folder Portals, which make it possible for users to mirror any folder to the desktop for ease of access.
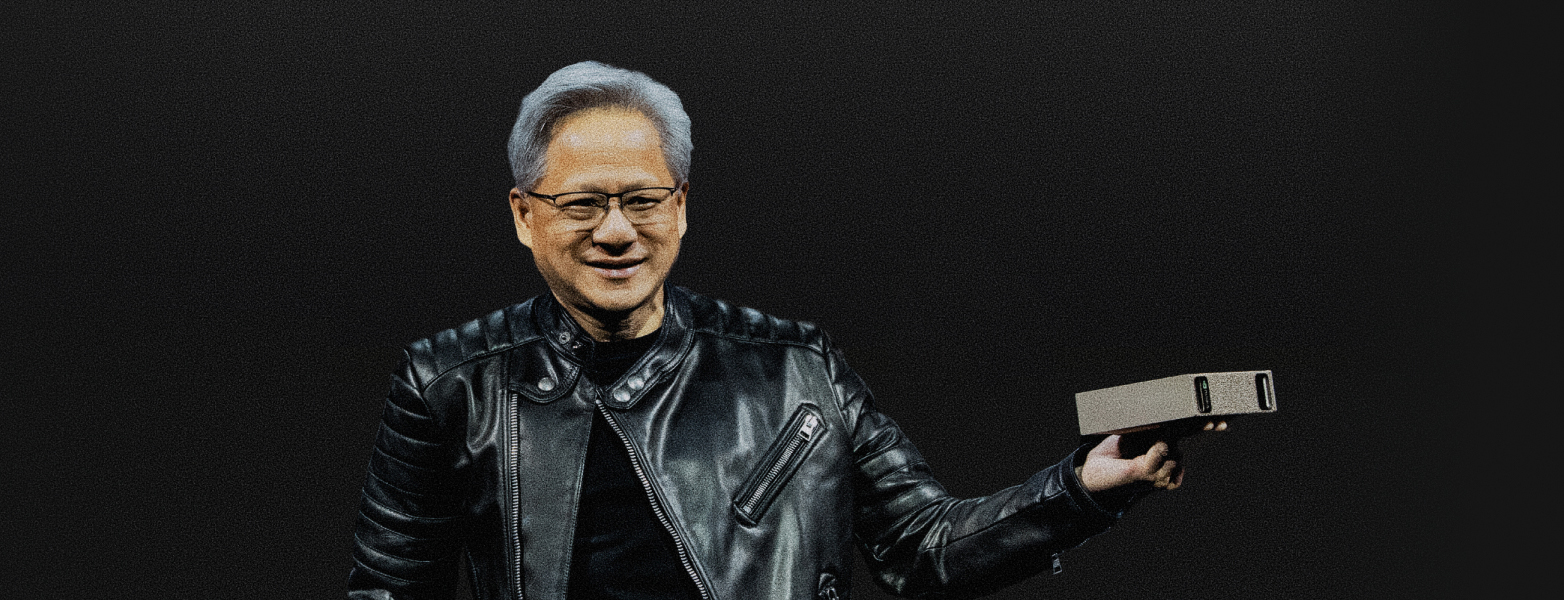
What does Nvidia's palm-sized AI supercomputer, DGX Spark, really mean for the future of AI development at the edge?
Nvidia CEO Jensen Huang’s now-famous GTC 2025 reveal where he held up a palm-sized AI supercomputer and likened it to the original DGX-1 “with Pym particles” wasn’t just a show of engineering flair.
The DGX Spark, as it’s now officially called, marks a turning point in how we think about AI infrastructure. For the first time, Nvidia’s Grace Blackwell superchip architecture has been distilled into a 1.2kg box that fits on a desktop, priced accessibly for research teams and small-scale deployments.

New AI analytics platform is designed for enterprise frameworks
As data demands across organizations intensify they need to scale productivity and enable business users to explore data independently.
Cube is launching an agentic AI analytics platform built on a universal semantic layer which allows it to operate autonomously within enterprise frameworks, automating work while preserving trust, governance, and transparency.
