
8GB Raspberry Pi 4 now available
When the Raspberry Pi Foundation launched the Raspberry Pi 4 last year it described it as a "complete desktop computer", but the truth is it isn’t powerful enough to run many of the tasks you’d use a desktop computer for, even if you opted for the 4GB model.
Today however, the Raspberry Pi 4 gets an upgrade with a new 8GB version joining the ranks.

Wow! Windows 10 May 2020 Update has a LOT of issues
Microsoft had previously warned that the latest feature update for Windows 10 would be released with one known issue, but it turns out it has a lot more than that.
The Windows 10 May 2020 Update, also known as Windows 10 version 2004, started rolling out to users yesterday, being first made available to users running Windows 10 version 1903 or 1909.

How to ensure communication security when working from home
With millions working from home for the first time thanks to coronavirus, many businesses have had to act quickly in order to facilitate remote communication which may never have been an option before the virus struck. Though these businesses may have already made the switch to internet-hosted calls and communications at work, providing access to all employees from home will not have been common. One of the most common concerns of using internet communication software is its security capacity, so how secure is it? And how can business leaders ensure the highest levels of safety for a remote workforce?
From news stories of vulnerable video conferencing software to threats from less secure home networks, navigating the security issues of a remote workforce may be a trial by fire for businesses attempting to maintain levels of normality during this time. Therefore, it will be important to understand both the benefits and drawbacks of internet communications to know what to look out for and how to inform staff of the best practice.

Microsoft releases Windows 10 May 2020 Update -- here's how to download it now
As predicted earlier today, Microsoft has now released Windows 10 May 2020 Update. This latest update has been available to developers for a little while, but the proposed general release that had been scheduled for the middle of this month had been postponed.
But now Microsoft has decided the update is ready for public consumption. Here's what you need to know, and how you can get hold of it.

News flash: People working from home are just as productive
As a result of the coronavirus pandemic most companies have shifted to having employees working at home. For some that is ideal, for others the lack of human contact can be depressing. It’s a double-edged sword in many ways -- you want people around but enjoy being home.
There is some good news for employers though -- new research released by Hibob finds that people working from home are just as productive as they were in the office.

Can AI bring back productivity that other technology has squandered?
How do you know you had a good day at work? If you did, how would your boss know?
These questions are especially important in the current environment where so many people are working from home without the insight that watercooler discussions, office pop-ins and other face-to-face contact would typically provide. Our reliance on technology to get work done has been growing for decades, but work-from-home orders due to the coronavirus pandemic have accelerated that reliance even more.

6 tips to maximize security while working from home
Cyberattacks are on the rise as cybercriminals look to exploit the current COVID-19 pandemic which has left an unprecedented amount of people working from home which is highly unlike any normal working from home situation. As many begin to adjust to life away from the office, it is critical that people remain vigilant and have the knowledge of basic cybersecurity practices which can be easily implemented while working remotely.
Here are some of our top tips for how you can remain digitally secure while working from home and reduce your risk of becoming a victim of a cybercrime.

Trump threatens to close social media platforms following Twitter spat
There have long been complaints from the right that online platforms censor conservative opinions because of a liberal bias. Now after being fact-checked by Twitter, Donald Trump has threatened to close down social media platforms.
In the last 24 hours, Twitter added a "Get the facts" link to a false claim made in a tweet by the president about mail-in votes. Clearly incensed, Trump tweeted that "we will strongly regulate, or close them down".

How to block the Windows 10 May 2020 update
The Windows 10 May 2020 update, aka Windows 10 version 2004, is due to begin rolling out to users shortly.
As normal, it will be a phased rollout so not everyone will be offered it straightaway -- it could be months before it reaches your machine. But if previous major updates are anything to go by, you should avoid installing it for a while anyway as these releases typically come with issues and it could be more hassle than it’s worth.

Microsoft implores you to stop using Cmd and switch to PowerShell
Rich Turner, a senior program manager at Microsoft, has taken to Twitter to practically beg people to move away from Cmd to PowerShell. Why? Well Cmd is an ancient hangover from the days of MS-DOS, for a start!
He explains that Cmd is in maintenance mode, and only continues to exist for the purpose of backward compatibility. Stating "PowerShell is the future", he states categorically that the old command line interpreter "should not be used for interactive shell work".

Windows 10 May 2020 Update should be released today
There has been speculation about just when Microsoft would release Windows 10 May 2020 Update / Windows 10 version 2004 / Windows 10 20H1 after a bug delayed the launch earlier this month.
Rumors generally agreed that the release date would be somewhere between May 26 and May 28, and it seems the correct date is actually smack in the middle -- May 27. While the update is, at time of writing, yet to start rolling out, an update to the Windows lifecycle page of the Microsoft site appears to reveal that today is the big day.
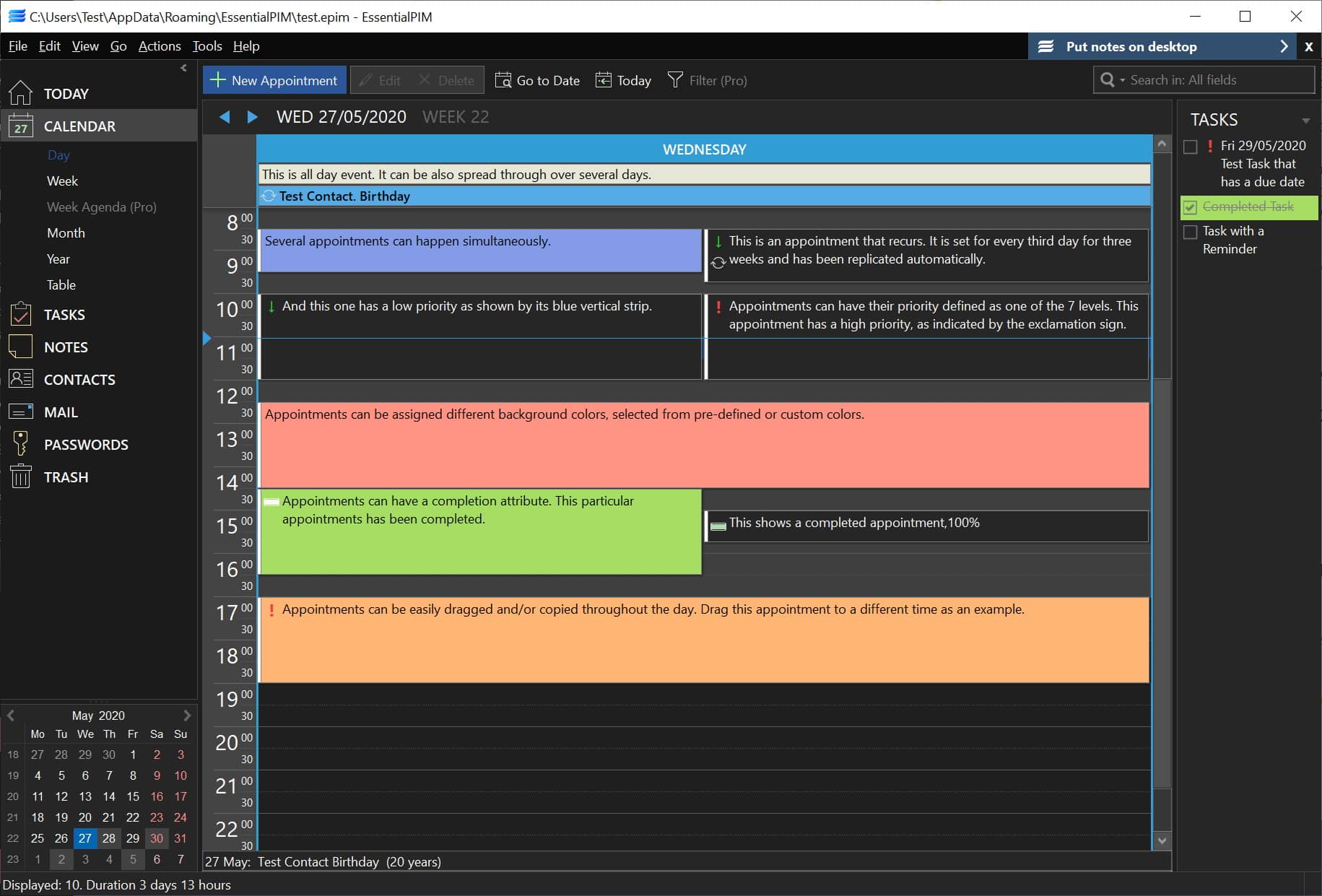
EssentialPIM 9.0 is here with added dark mode, new tagging options and additional mail rule options
A good personal information manager (PIM) is a great way to stay on top of the information you need on a daily basis, such as email, calendar, tasks and notes. EssentialPIM has long offered an approachable and powerful way to access such information, and now EssentialPIM 9.0 has been released with a range of new features.
From an aesthetic point of view, there's a new dark mode option, but this is a significant release which is about much more than just a new coat of paint. There are also new rules to help you manage an unruly inbox, bookmark-style anchors to make it easier to navigate notes, and a powerful tagging system that not only lets you organize a range of different data together, but also to quickly jump to it using keyboard shortcuts.

Organizations want to continue remote work but aren't equipped for secure access
The current crisis has led to a big increase in numbers of people working remotely. Many businesses seem set to continue that when normality returns, but a new report suggests they're not equipped to do so securely.
The study from cloud security company Bitglass shows that 41 percent have not taken any steps to expand secure access for the remote workforce, and 50 percent are citing proper equipment as the biggest impediment to doing so. Consequently, 65 percent of organizations now enable personal devices to access managed applications.

DNS traffic and DDoS events rise during pandemic
New research from DNS intelligence specialist Farsight Security, focusing on over 300 leading websites, finds that between March and April there has been an increase in DDoS events involving popular brand names.
It also reveals that DNS cache misses (which occur when the data fetched is not present in the cache) showed an increase of between four and seven times.

How to move beyond the burden of legacy systems [Q&A]
These days, companies are seeking to stay competitive and current by pursuing and succeeding at end-to-end digital transformation.
Successful digital transformation brings a myriad of benefits to organizations of all types, including operational efficiencies, improved customer engagement and digitally-enabled sales and service. However, organizations can't fully embrace and reap the benefits of digital transformation if they're still relying on their old legacy environment.
