
Happy 25th Birthday, SD memory card!
Happy birthday, SD card. It’s been 25 years since the launch of the original SD memory card back in 2000, and somehow, it’s still going strong. While plenty of storage formats have come and gone, the SD card has quietly kept doing its job -- storing our photos, videos, music, and games without much fuss.
The SD Association is celebrating this big milestone by reminding everyone just how far things have come. In those 25 years, over 12 billion SD and microSD cards have been sold. That’s not a typo. 12 billion. From point-and-shoot cameras to smartphones and gaming handhelds, these little cards have shown up everywhere.

TP-Link launches new Wi-Fi 7 gear for inside and outside your home
TP-Link has launched new Wi-Fi 7 gear designed for users who want stronger wireless both indoors and out. The networking company just pulled the curtain back on several new products, including what it claims is the world’s first outdoor Wi-Fi 7 mesh system built specifically for home use.
At the top of the pile is the Deco BE68. This 3-pack mesh system promises wireless speeds up to 14Gbps and can cover a massive 8,100 square feet. That’s a whole lot of bandwidth and range for families with tons of connected devices.

Is Google AI Ultra worth $250 a month or is the price completely tone deaf?
Google has officially launched Google AI Ultra, a high-end subscription plan that unlocks the company’s most powerful AI tools. It’s being pitched as the best way to experience everything Google AI has to offer. Sure, maybe it is, but at $249.99 per month, it’s hard not to question the timing.
Look, with inflation still hitting wallets and layoffs continuing across industries, launching a $250 monthly plan feels completely disconnected from reality. Google’s positioning it as a VIP pass for filmmakers, researchers, and creatives. But let’s be honest, folks, that’s a very steep price in today’s economy.

Yubico helps more enterprises go passwordless
Hardware authentication company Yubico is announcing the expanded availability of YubiKey as a Service to all countries in the European Union (EU). This allows organizations to be more agile and flexible in their adoption of phishing-resistant YubiKeys.
It's also announced the greater availability of YubiEnterprise Delivery across 117 new locations around the world. This makes it available 199 locations (175 countries and 24 territories) and more than doubles existing delivery coverage of YubiKeys to both office and remote users in a fast and turnkey way.

Red Hat Enterprise Linux 10 arrives with AI assistant and post-quantum security
Red Hat has just taken the wraps off Red Hat Enterprise Linux 10, and honestly, there’s a lot for the Linux community to get excited about. You see, this new version brings some real substance, pushing enterprise Linux in directions that truly matter for today’s IT world.
First and foremost, there's Lightspeed -- the new AI-powered assistant baked right into RHEL 10. Instead of spending all day searching for answers or poking through documentation, admins can simply ask questions directly from the command line and get real-time help. This is the kind of smart, hands-on support that can actually make life easier, especially for those just getting started or managing sprawling environments.

Threat intelligence is crucial but organizations struggle to use it
While 92 percent of respondents to a new survey say collaboration and information sharing are either 'absolutely crucial' or 'very important' in the fight against cyber threats, the results tell a different story when it comes to the adoption of this practice.
The study from Cyware, conducted among cybersecurity professionals at the RSA Conference 2025, finds only 13 percent say their current automation between cyber threat intelligence (CTI) and SecOps tools is working well. Nearly 40 percent day they struggle to coordinate data across critical security tools like Threat Intelligence Platforms (TIPs), SIEMs, and vulnerability management platforms.

Marshall Heston 120 TV soundbar brings Dolby Atmos and iconic design to home audio
Marshall has announced its first-ever TV soundbar, the Heston 120. Marshall says it’s engineered for both music and TV, refusing to settle for the usual compromise most soundbars offer. Dolby Atmos and DTS-X are both on board, with 11 drivers positioned to bounce sound around your space.
You’ll find plenty of modern features packed inside. HDMI eARC support is here, along with HDMI passthrough for extra flexibility. The Heston 120 also supports Wi-Fi connections via Google Cast, AirPlay, Spotify Connect, and Tidal Connect. Bluetooth is on deck, too, and even old-school analog fans get RCA input support, so vintage music gear isn’t left out.

AI-powered threats highlight the need for a unified approach to SOCs
With new threats such as AI-powered attacks, enterprises must be fully prepared and confident about protecting themselves and their customers and build a unified security operations center (SOC) that combines human expertise with AI advancements.
A new report from Splunk looks at the mounting challenges faced by SOCs. It uncovers the pain points that hamper organizations and open their doors to threats -- 46 percent of respondents say they spend more time maintaining tools than defending the organization, while only 11 percent trust AI completely for mission-critical tasks. Furthermore, 66 percent experienced a data breach in the past year, making it the most common security incident.

97 percent of CIOs are deploying or looking at edge AI
New research shows that 97 percent of CIOs have edge AI either already deployed or on their
roadmap, with only three percent reporting no current plans to implement these technologies.
The report from ZEDEDA, based on a survey by Censuswide of over 300 US CIOs, finds 80 percent of CIOs with deployed edge AI solutions use them for customer experience improvements, while nearly as many (77 percent) focus on risk management applications, including predictive maintenance.
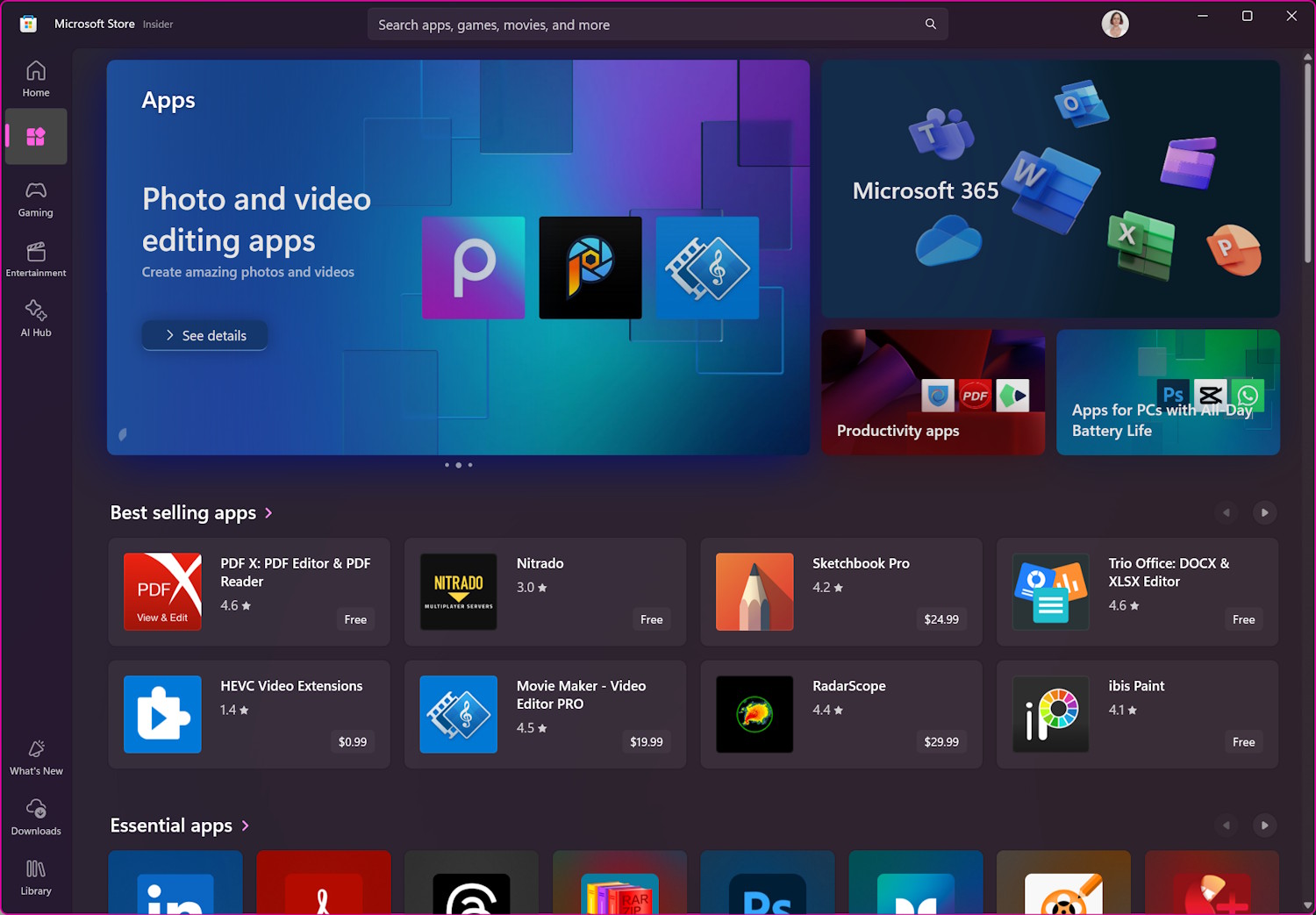
Major changes are coming to the Microsoft Store -- including the ability to update Win32 apps
Using an app store to keep installed apps up to date is something that the likes of Apple’s App Store and Google Play brought to the mainstream, and it eventually moved to the desktop. Until now, the Microsoft Store has been limited in its capabilities, but Microsoft has announced some huge changes.
Perhaps the biggest change is support for updating Win32 apps directly in Microsoft Store, which is something users have been asking for for some time. But there are other changes too, including zero onboarding fees for developers, and an expanded set of Health Report insights.
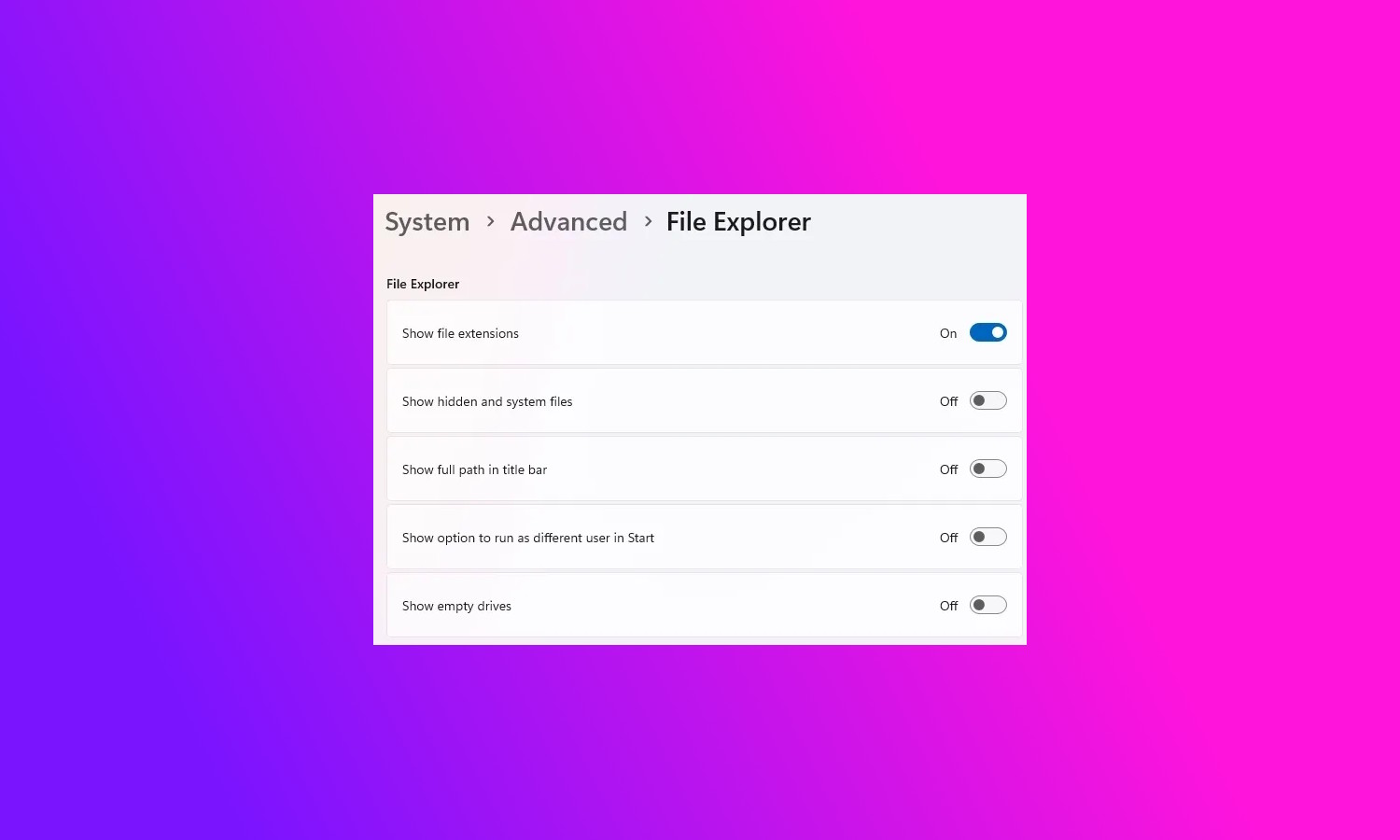
Microsoft is giving Windows 11 power users and developers new Advanced Windows Settings
Everyone likes to feel that they are in control of their computer, but the way the Settings app has been organized can make this hard. Acknowledging this, Microsoft had revealed new Advanced Windows Settings to allow for more configuration options.
The new Advanced section essentially replaces the For Developers section of Settings, but Microsoft says that it is now also aimed at power users. There are many options collected into one place that would otherwise be scattered, hidden or inaccessible.

Crucial unveils blazing fast T710 Gen5 SSD and massive 8TB X10 portable drive
Micron is making some serious noise at Computex 2025 with the launch of two new Crucial SSDs. The newly unveiled T710 Gen5 NVMe SSD and X10 Portable SSD offer the kind of speed and storage capacity that demanding users have been waiting for.
The T710 is an absolute beast. Crucial is claiming up to 14,900MB/s read speeds and 13,800MB/s write speeds, making it the fastest drive it’s ever released. Random performanceis off the charts, folks. We’re talking over 2 million IOPS. That kind of speed means faster game loading, snappier project rendering, and real-time responsiveness for complex tasks. There’s even an optional heatsink if you’re planning to push it hard.

Microsoft releases emergency patch for Windows 10 BitLocker recovery problems
The release of the KB5058379 update for Windows 10 earlier this month resulted in frustration for many Windows 10 users. People with devices with Intel Trusted Execution Technology (TXT) enabled on 10th generation or later Intel vPro processors were hit with BitLocker recovery problems.
It took Microsoft a little while to acknowledge the issue, but now the company has issued an out-of-band patch in the form of the KB5061768 update.
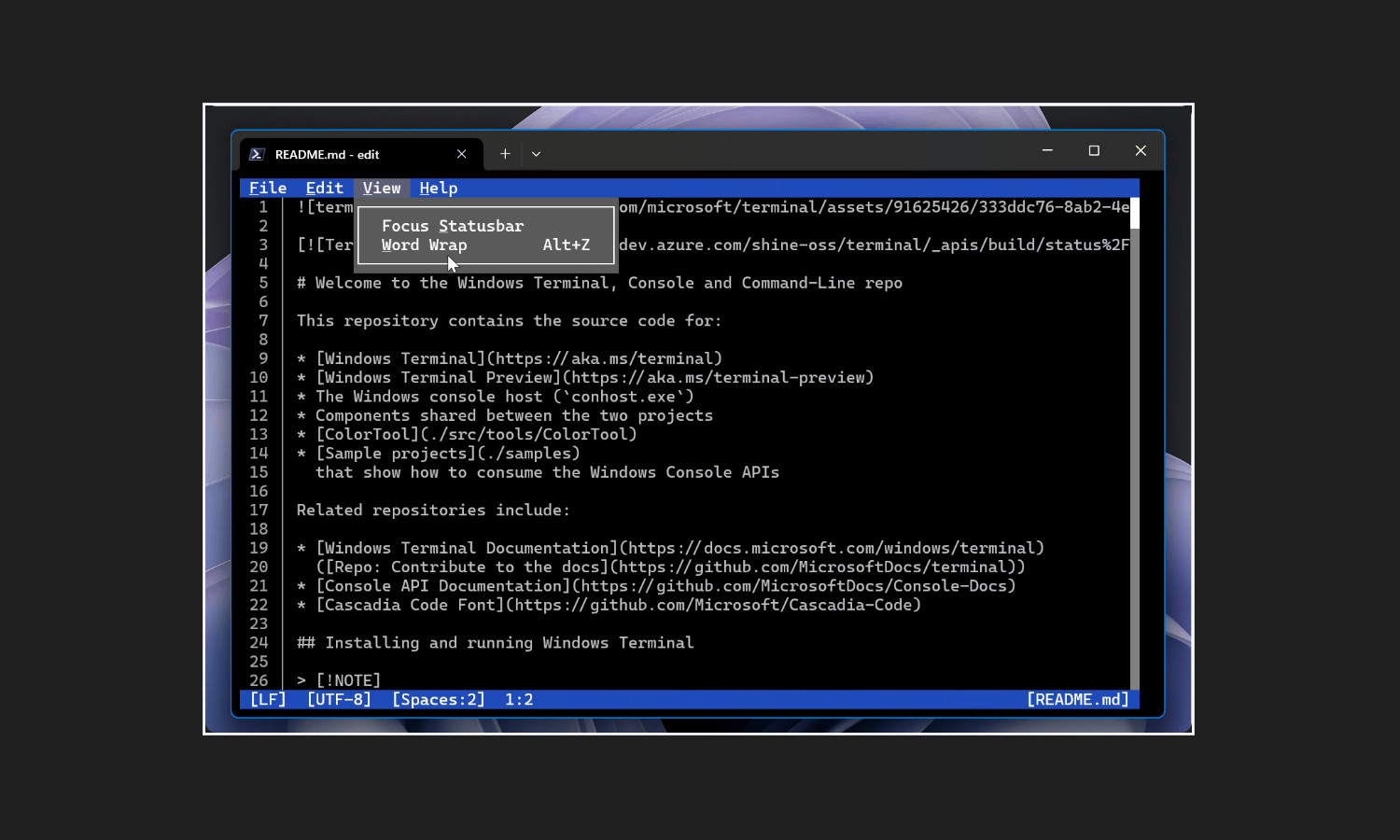
Microsoft launches Edit, its new open-source command line text editor
Microsoft Build is usually about cutting edge development, but sometimes there are nods to the past. And this is precisely what is happening with the company’s new text editor.
Named -- uninspiringly -- Edit, this text editor is not only open-source, but it is a command line tool. While clearly not something that will be of interest to the majority of Windows 11 users, it is something that has strong developer appeal.

MSI unveils new handhelds and laptops in massive Computex 2025 showcase
At Computex 2025, MSI definitely is not playing it safe. The company clearly came to Taipei ready to shake things up with fresh handheld gaming devices, artistic laptop designs, and a growing relationship with Mercedes-AMG. From lacquered laptops to performance-packed portables, MSI’s lineup is truly exciting.
The Prestige 13 AI+ Ukiyo-e Edition might be the most striking device on display. It features real Japanese Yamanaka lacquer, crafted in partnership with OKADAYA, and uses the famous “The Great Wave off Kanagawa” artwork as a design centerpiece.
