Forget Windows 10, Windows 20 is the Microsoft operating system we need!
Windows 10 has had more than its share of issues over the years, with buggy updates causing a wide variety of problems for users. The May 2020 Update is nearly ready for release, and will no doubt bring with it another set of woes for many when it does arrive.
With Windows 7 no longer supported, Windows 10 is really the only game in town for those who want to use Microsoft’s OS. But perhaps we should be consigning it to the past and looking to the future with the gorgeous, and much more modern, Windows 20.

Read the Microsoft Edge Privacy Whitepaper here
Microsoft has published a whitepaper about privacy in its Edge browser. The paper goes someway to answer the questions user may have about the data Edge is collecting about users.
The company says that the whitepaper is an exercise in transparency which "explains how Microsoft Edge features and services work and how each may affect your privacy". Microsoft insists that it practices data collection minimization, and it uses the whitepaper to come clean about just what data the browser is gathering.
Windows Notepad returns to the Microsoft Store with new features
It's one of the most basic components of Windows, but also one of the most loved and most useful. Notepad has been with us for decades, and now it has found a new home in the Microsoft Store.
This is not the first time the app has appeared in the Microsoft Store. Originally announced in August last year, Notepad appeared for a while before vanishing. Now it's back, and it's better than ever with a host of new features.

What's new in Windows 10 May 2020 Update?
Microsoft is ready to unleash the next big feature update for Windows 10, so what do you have to look forward to? Known variously as the Windows 10 May 2020 Update, Windows 10 version 2004, and Windows 10 20H1, there are quite a number of changes.
While not quite as big an update a some feature releases, the Windows 10 May 2020 Update includes important updates to Cortana, Settings, Search, Virtual Desktops and Windows Subsystem for Linux (WSL) 2.

Fintech: Leak shows Google is working on a debit card to rival Apple Card
Leaked pictures suggest that Google is preparing to launch its own physical and virtual debit cards. TechCrunch cites multiple reliable sources in a report that gives a glimpse into Google's future fintech plans.
Images of not only the physical card itself but also screenshots of the Google Pay app with references to the virtual version of the card show off the design, as well as the spending tracking features that are in the pipeline.
Apple's new 'battery health management' feature improves MacBook battery life
The battery life of your MacBook is about to be extended thanks to a new feature Apple is adding to macOS Catalina 10.15.5. Called "battery health management", the feature reduces batteries' rate of chemical aging, helping to extend its lifespan.
Working much like the Optimized Battery Charging feature of iOS, battery health management measures battery usage and adjust the maximum charge level for improved life.

Apple Music on the web is no longer in beta -- including on Linux
My favorite streaming music service is Apple Music. As an iPhone user, this was a match made in heaven. As a regular desktop Linux user, however, this was very problematic. You see, for the longest time, you needed iTunes to listen to Apple Music on desktop. This wasn't a problem when using Windows 10 or macOS, but as soon as I signed into, say, Ubuntu, I was out of luck, as there is no iTunes for Linux.
Thankfully, late last year, Apple finally brought its streaming music service to the web. In other words, all you needed to listen to Apple Music was a compatible web browser. This meant that users of desktop Linux could finally listen to the streaming service by simply firing up a web browser, such as Firefox. Despite being a feature Spotify offered for many years, it was still a really big deal. The problem? Apple Music for the web was merely a beta. Today, this changes.

Get 'Web Coding & Development All-in-One For Dummies' ($25.99 value) FREE for a limited time
With more high-paying web development jobs opening every day, people with coding and web/app building skills are having no problems finding employment. If you’re a would-be developer looking to gain the know-how to build the interfaces, databases, and other features that run modern websites, web apps, and mobile apps, look no further. Web Coding & Development All-in-One For Dummies is your go-to interpreter for speaking the languages that handle those tasks.
Get started with a refresher on the rules of coding before diving into the languages that build interfaces, add interactivity to the web, or store and deliver data to sites. When you're ready, jump into guidance on how to put it all together to build a site or create an app.

MyFamilyTree 10 adds new interactive Fan chart view, introduces tool to resolve duplicates
Ahoy family historians! Chronoplex Software has released a landmark version of its free family history app for Windows users. My Family Tree 10.0, also available in 32-bit form, adds a brand-new interactive fan view that can also be used as a printable or shareable chart.
Other highlights include a new tool to resolve duplicate entries, various improvements to the user interface, a brand new progeny report and the ability to create placeholder entries in the tree for filling out later.
Plex releases media server app Dash, and Plexamp player for Windows, mobile, macOS and Linux
If the phrase "it really whips the llama's ass" means anything to you, you clearly remember the heady days of WinAmp. Now media server and management company Plex has come up with its own take on the classic software.
Called -- slightly uninspiringly -- Plexamp, the player is available for iOS, Android, macOS, Windows and Linux. The company has also released a new app for managing Plex media servers: Plex Dash. This is great news for Plex users, but there's a slight catch in both cases.

'Not a safe platform': India bans government officials from using Zoom -- but offers up some great security advice
The unrelenting criticism of Zoom continues, with India being the latest to slap an official ban on the video conferencing tool.
Voicing concerns that Zoom is "not a safe platform", the Indian Cyber Coordination Centre issued an advisory saying that the tool is "not for use by government offices/officials for official purpose". But the country recognizes that many people will want or need to continue using Zoom and the ministry of home affairs has issued a helpful guide to safe use of the service.

Free security analytics helps fight remote worker threats
We've seen many companies offering free software during the current crisis. Now security and risk analytics company Gurucul is launching two free services to help organizations protect themselves against cyberattacks that target their remote workers and third-party identities.
These deliver the Gurucul Unified Security and Risk Analytics platform as a cloud service with pre-configured and tuned algorithms that can detect unusual and high risk behavior patterns exhibited by remote workers as well as third party identities and devices.

Microsoft readies Windows 10 May 2020 Update (20H1) for release
We’re already halfway through April, so it should come as no surprise to you that the next big update for Windows 10, the May 2020 Update, is pretty much finished.
In preparation for its release, Microsoft has begun rolling it out to Insiders on the Release Preview ring for some last minute testing. The software giant believes that Build 19041.207 is the final flight, although that depends on whether Insiders find any major issues.

Samsung Galaxy Tab S6 Lite is a beautiful Android 10 tablet that comes with an S Pen
If you are an iPhone user, and you want a tablet, you should absolutely get an iPad. Why? Because not only do they share the same App Store (meaning you can often buy an app once and have it on both devices), but also, they can be linked so you get text messages and phone calls on the iPad. The problem? Most of the world uses Android smartphones -- not iPhone. Unfortunately, quality Android tablets are becoming increasingly more rare.
Thankfully, some companies are still making Android tablets consumers will actually want, and today, a new one is announced by Samsung. Called "Galaxy Tab S6 Lite," the tablet runs Android 10 and comes with an S Pen included. This device is designed with a focus on media consumption, so it has a big beautiful display and dual AKG-tuned speakers with Dolby Atmos 3D surround sound. It even comes with complimentary access to YouTube Premium for four months.
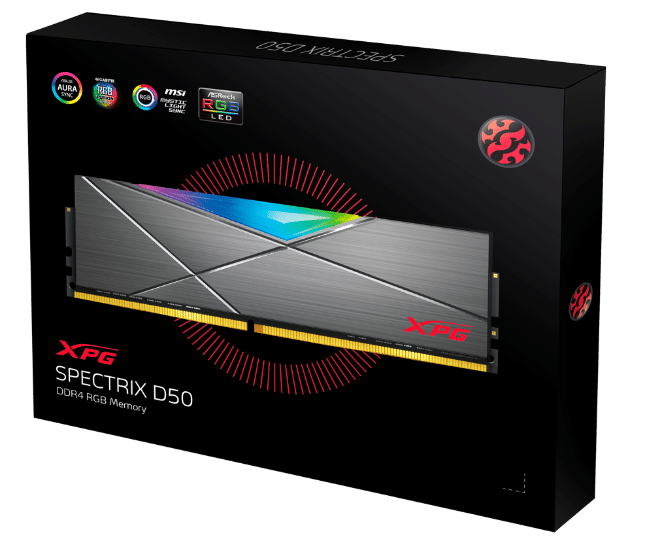
ADATA announces XPG SPECTRIX D50 DDR4 RGB gaming RAM
RGB lighting rules -- it's a fact. It has the ability to make a great product even better. True, some people decry the inclusion of RGB in so many products nowadays, but to them I say, either buy a different product or simply turn the lighting off! You see, many of these products allow you to turn off the lighting effects entirely, so there is really no downside.
Today, ADATA announces its latest memory, and yes, it features RGB lighting! Called "SPECTRIX D50," these DDR4 modules carry the company's XPG branding, meaning they are intended for gaming. With that said, even non-gamers can enjoy the performance and good looks of these sticks.
