
Transcend JetFlash 910 USB flash drive is fast, durable, and elegant
With cloud storage gaining in popularity, flash drives have fallen out of favor with many consumers. Maybe that's not such a bad thing, as USB flash drives are easy to lose and are susceptible to failure -- the cloud is arguably more safe and secure. With that said, there will always be a need for local storage, as sometimes you can't trust, say, company secrets, to the cloud. Hell, I used a USB flash drive for an operating system installation just yesterday -- they absolutely still have value.
It is hard to get excited about USB flash drives though, right? I mean, aren't they all the same? Actually, no! They can vary on things like build quality and performance. That's why the new Transcend JetFlash 910 USB flash drive piqued my interest. Not only are both read and write speeds very impressive, but the build quality looks great too -- it features an elegant aluminum body.

How the cloud can help enterprises break free from vendor lock-in [Q&A]
In the IT industry, software vendors naturally focus their efforts on developing easier ways to onboard new customers and provide unique functionality on their platforms, but they rarely devote development cycles to making it easy to export workloads. As a result, it can be difficult to extract workloads and move between competing platforms. This is commonly referred to as 'vendor lock-in' and is especially concerning with databases and enterprise applications.
But, according to Chris Patterson, senior director of product management at Navisite, an RDX company, cloud computing offers an unusual opportunity for companies to break free from vendor lock-in. He believes cloud migration could alter the status quo, because when organizations decide to migrate their databases to the cloud, it also creates an opportunity to change to new alternatives, such as Amazon Aurora and Azure SQL.

How censorship in Silicon Valley is killing free speech
As the role of Silicon Valley further permeates into the vast expanses of our daily lives, so does the spotlight on the decisions it makes regarding who can use their platforms and in what manner. There's no denying that, as private companies, these entities have a legal right to uphold policies which ensure fair and equitable access for their users.
But there's one particular arena that these tech supergiants are wading in which is getting increasingly murky, and ultimately, quite troubling. I'm referring to their insistence on setting the goalposts for protected and censored "free speech," if that term can even be considered as having its structural integrity still intact.

Web-based Outlook will support email aliases soon
Microsoft plans to introduce a new feature to its Outlook on the Web service that provides users with the option to use email aliases when sending messages.
The company added the new feature to the Microsoft 365 Roadmap and lists it as 'under development' currently.

How to install GIMP on Linux Mint 19.3 Tricia
Linux Mint is a great operating system, but with the most recent version (19.3 "Tricia"), there was some shocking news -- GIMP (GNU Image Manipulation Program) was being removed! Crazy, right? I mean, of all of the great software available for Linux, GIMP is one of the best. It is an essential image editing tool that rivals Adobe Photoshop.
So, why did Linux Mint remove it as a pre-installed program? The developers thought the software was too advanced for newer Linux users. While I think that is a bit of nonsense, I can understand why the Mint developers would want to cater to beginners. Thankfully, it is totally easy to install GIMP on a new Linux Mint 19.3 installation.
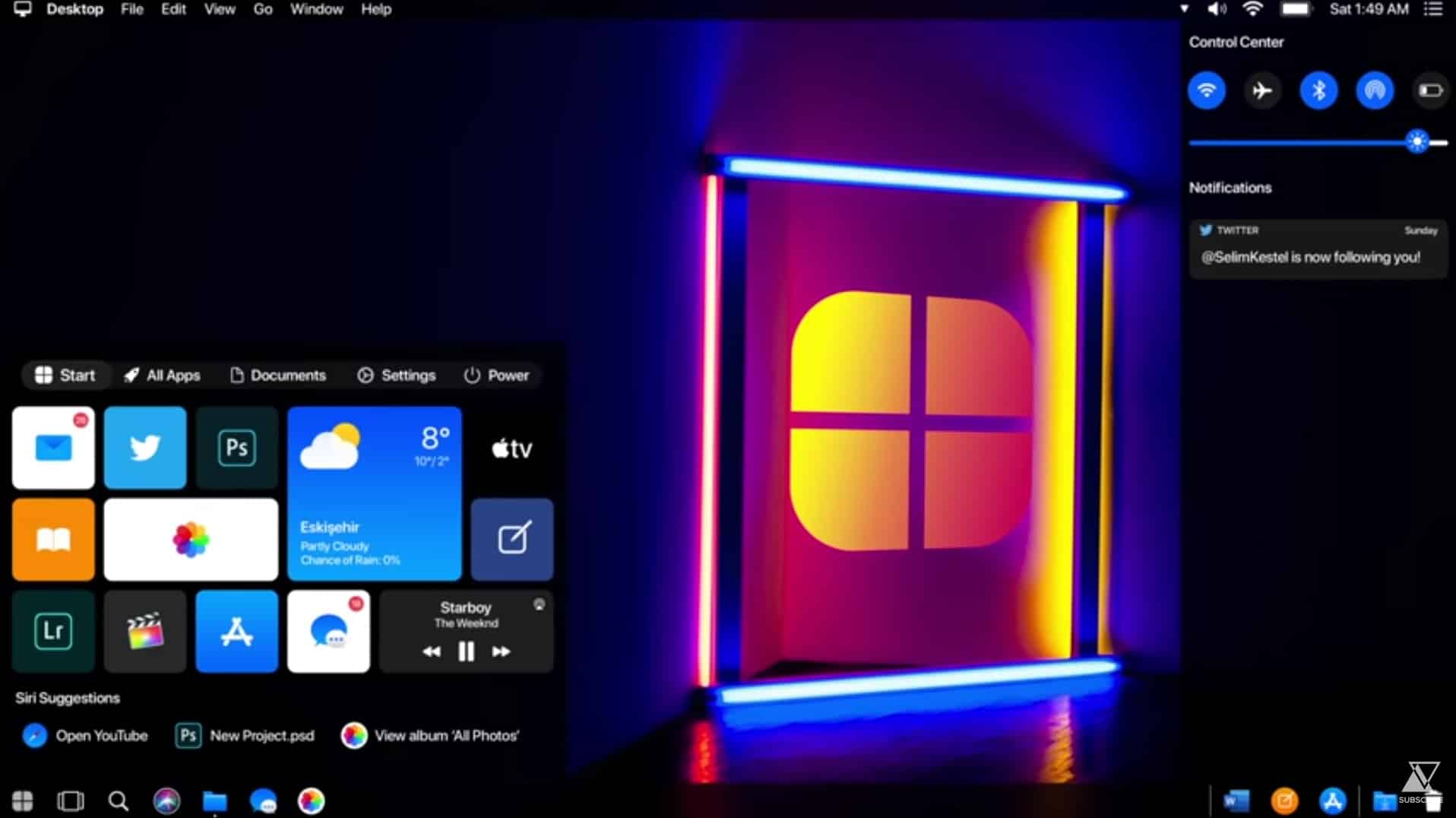
Sorry Microsoft, Apple's Windows 10 is the operating system we really want!
Apple has a reputation for producing stylish and elegantly designed hardware and software products. Microsoft, well, not so much.
Windows 10 under Microsoft’s control isn’t a bad looking operating system, but even after all these years it still doesn’t feel quite finished, with elements of the old design cropping up in various places. If you’ve ever wondered what Windows 10 would look like if Apple was developing it, we have the answer.

Beta insights show WhatsApp's Disappearing Messages feature is probably not what you think
When app hackers discovered references to Disappearing Messages in beta versions of WhatsApp, it was -- understandably -- assumed that this was going to develop into a self-destructing messages feature. But when the same option was renamed to the less-exciting Delete Messages, the name didn't really tally.
Further details shared by WABetaInfo about the latest beta of the WhatsApp app for iOS shows that the feature is very much not what people were expecting... or hoping. Oh, and if you were hoping for a Dark Mode option, you're going to have to wait a bit longer.
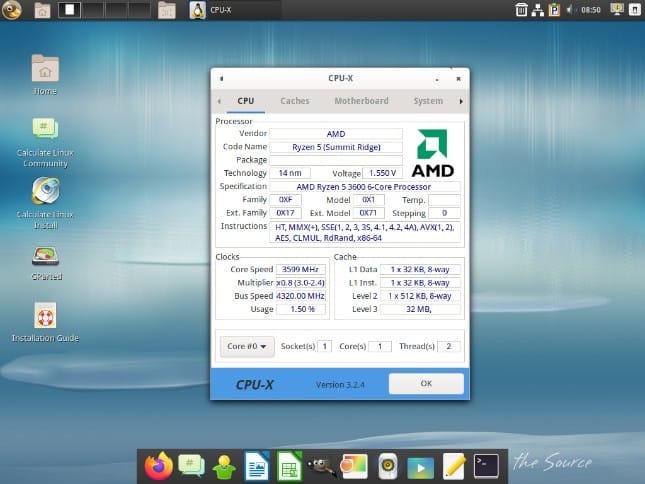
Gentoo-based Calculate Linux 20 now available for download
With 2019 almost over, we turn our sights to a new decade with 2020. Soon we will celebrate the new year by partying, eating good food, and watching the Times Square Ball drop on TV. Sadly, Dick Clark is dead, but his legacy lives on through Ryan Seacrest.
But what if you want to celebrate 2020 in a more... nerdier way? Well, I have some good news. Calculate Linux 20 is now available for download! Yes, the Gentoo-based operating system is ready to be installed on your computer. Since it is version 20, that makes it perfect for ringing in 2020.

You can join the Windows 10 Insider Program without a Microsoft Account (unofficially)
The Windows 10 Insider program has a few requirements but the most important ones are that users need to use a Microsoft Account to receive Insider builds and that data collecting needs to be set to full on the device.
Offline Insider Enroll is a command line script that enrolls Windows 10 devices in the Insider program even if no Microsoft Account is used. The requirement to set Telemetry to full is not changed, however.

Amazon again brags about record-breaking holiday shopping sales
Well, folks, Christmas 2019 is now in the rear view mirror. Hopefully you and your family had a wonderful holiday. Following Christmas, there is one big important tradition -- Amazon's bragging! Yes, every year, the online retailer loves to brag about its successful holiday shopping sales. They are always the best ever, of course, and this year, things are no different.
Yup, Amazon is claiming that it had record-breaking sales during the 2019 holiday shopping season. While the company doesn't share actual sales numbers, I actually don't doubt its claims. This year, when I went to brick-and-mortar stores on Black Friday (and the days after), the stores were clearly experiencing a huge drop in foot traffic. In other words, Amazon has seemingly continued its trend of cannibalizing traditional retailers, but this year, it seemed much more dramatic. Hell, I ended up doing 90 percent of my own Christmas shopping on Amazon and I don't even have Prime!

Twitter bans animated PNGs to avoid triggering people with photosensitive conditions
File under: "This is why we can't have nice things". To counter abuse by people seeking to trigger seizures in those with photosensitive epilepsy, Twitter has announced a ban on animated PNG images.
The company says that the fact that APNGs don't respect autoplay settings and pose a risk to some users. As such, the ability to post animated PNGs has been removed "for the safety of people with sensitivity to motion and flashing imagery, including those with epilepsy".

AI will create larger issues in 2020
Many predictions that we saw around artificial intelligence (AI) for 2019 leaned towards one extreme or the other -- ranging from the notion that AI will no longer be a thing to the idea that it’ll realize its full potential and completely change how industries work at a fundamental level. Advancing AI is going to be an incremental process and it’s unrealistic to think that the world will suddenly abandon it completely or exponentially accelerate its development in that area.
But in the security industry, we have still seen progress surrounding AI, as we’ve gotten better at using machine learning technology to identify and recognize behaviors to identify security anomalies. In most cases, security technology can now correlate the anomalous behavior with threat intelligence and contextual data from other systems. It can also leverage automated investigative actions to provide an analyst with a strong picture of something being bad or not with minimal human intervention.

Microsoft could be about to use the Windows Feature Experience Pack app to deliver non-core updates to Windows 10
Microsoft seems to have big things in store for Windows 10 in 2020, but it's not exactly clear what at the moment. A few people have recently noticed that after updating to Windows 10 version 19536 that there is a reference to something called Windows Feature Experience Pack under in the About section of System Settings.
But things get more intriguing. A dummy app from Microsoft called Windows Feature Experience Pack has been spotted in the Microsoft Store, leading to speculation that the company could start to deliver some Windows 10 updates via an app, keeping them separate from more major updates to the operating system.

You can track Santa Claus again this Christmas with Google
Santa Claus is absolutely real; he lives in the hearts and minds of all true believers of Christmas. Is it possible for one man to deliver gifts to every house in the world in one night? Under normal circumstances no, but Santa Claus is magic -- you must throw all logic and science out the window.
Need proof that Santa Claus is real? Every year, Google provides a way to track the jolly fat man as he makes his journey around the world. Yes, Google's official Santa Tracker is an annual tradition, and in 2019, it continues. As usual, the search giant delivers activities beyond mere tracking, such as an interactive Santa Village. This year, there is a holiday-themed bedtime story for kids called "Ollie Under the Sea." There is even a very cool augmented reality Santa Claus you can summon by searching for "Santa Search" on mobile and clicking the "3D" button.

Windows 7 users will still get updates to Microsoft Security Essentials when the OS is out of support
It's now mere weeks until Windows 7 is no longer supported by Microsoft. When January 14, 2020 rolls around, the end date for support will have been reached, and Microsoft is keen for people to upgrade to Windows 10 to avoid having insecure computers that don't receive updates.
But not all security updates are being dropped. Having previously said that Microsoft Security Essentials would no longer receive updates when Windows 7 support ends, the company has indicated that updates will in fact continue to be released.
