
Kodi 19 'Matrix' with Python 3 now available to download, but be warned
As well as rolling out a new build for Kodi 18 'Leia', the popular home theater developer has made a major change to its next big release -- Kodi 19 'Matrix'.
Python 2 is set to hit its end of life on January 1 2020, and in preparation for this, the Kodi Foundation has taken the step of switching to the Python 3 interpreter for all Python-based add-ons.

Poor security habits leave Americans vulnerable to fraud
Despite high profile data breaches in 2019 and 33 percent of respondents having been a victim of fraud or identity theft, when asked if they update or change passwords following a data breach at a firm they deal with, 28 percent say only sometimes and nine percent say they don't update their passwords at all.
This is one of the findings of a Shred-it report for International Fraud Awareness Week which highlights the need for improvements in both digital and physical security.

Kodi 18.5 'Leia' available to download now! [Updated]
It’s been a couple of months since the Kodi Foundation released a new version of its hugely popular home theater software.
After spending some time in the pre-release section, Kodi 18.5 is now finally deemed ready for all.

Debian 10.2 'Buster' Linux distro released with many security updates and bugfixes
Debian is a great Linux distribution in its own right, but also, it serves as a solid base for many other distros. That's why when a new version of Debian is released, it has a huge impact across the Linux community.
Today, you can download the newest version of Debian 10 "Buster." Debian 10.2 is the latest and greatest, but it is hardly exciting. To be fair though, Debian point releases shouldn't really be seen as a source for new features. Instead, you should expect security updates and bugfixes. And this time, with version 10.2, we get many of them. In addition, Firefox ESR (Extended Support Release) is being dropped from the ARMEL variant of Debian, but that really shouldn't have any impact on desktop users.

Database containing details of nearly half a million gamers exposed in security lapse
Wizards of the Coast -- publisher of, among other titles, Magic: The Gathering -- has confirmed a security incident that exposed information relating to 452,634 players.
The company left a backup database containing gamer information in a public Amazon Web Services storage bucket where it was accessible from early September. Specifically, the database was used to house data relating to the game's online portal, Magic: The Gathering Arena.

Microsoft is blocking the Windows 10 November 2019 Update on systems with certain Realtek Bluetooth drivers
Some drivers for Realtek Bluetooth radios are casing compatibility issues with Windows 10 November 2019 Update, leading Microsoft to block the update on affected systems.
Anyone with an outdated version of the Realtek Bluetooth driver will be greeted by a message informing them: "Realtek Bluetooth: Your PC has a driver or service that isn't ready for this version of Windows 10". Updating Windows 10 to the latest version is blocked until users follow the steps set out by Microsoft.

Microsoft is killing off Cortana for some users
Microsoft has quietly confirmed the rumors that it is planning to discontinue its Cortana digital assistant for some users. Starting next year, the company will no longer support Cortana on either iOS or Android in certain markets.
While Microsoft is yet to confirm which countries will be affected, the UK, Canada and Australia are known to be on the list. The change means that there will be no Cortana mobile app, and integration will be removed from the Microsoft Launcher.

Microsoft releases Windows 10 20H1 Build 19025
Three days ago, Microsoft rolled out new Windows 10 20H1 Builds for the Fast and Slow rings, and made the Windows 10 November 2019 Update available for non-Insiders.
Today, Fast ring Insiders get another yet release -- Build 19025.

How synthetic data can unlock and help monetize information [Q&A]
Big data offers major opportunities for many industries. But in areas like finance where personal information is involved using the information raises worries about privacy.
One solution to that is to anonymize the information in some way. To discover more about how this works we spoke to Randy Koch the CEO of ARM Insight, a company pioneering the use of synthetic data and assisting more than 1,000 financial institutions to monetize their data safely.

The rise of first-party data: Why quality matters over quantity
For years, digital marketers have paid hand over fist in the digital gold rush for data. Instead of a tangible product, tech companies earn millions in revenue from the data they collect on previous, current and future digital consumers. But digital marketers seeking to gobble up as much data as they for their campaigns, while not stopping to consider the source of or methods used to collect it, are taking the wrong approach. The age-old mantra of "quality over quantity" has never been more relevant in online advertising, and marketers must quickly and fully embrace first-party data or risk their digital campaigns (and bottom lines) falling flat.
The primary reason to use first-party data over third party data from data marketplace platforms is simple: it’s better. Publishers, apps and ad platforms alike can gather first-party data directly from their audiences and customers, whether that data be purchases, app downloads, in-app actions, social media interactions, or subscriptions. This data comes directly from the source, making it as precise and accurate as possible. This is in stark contrast to third party data, which is aggregated from multiple platforms and combined into a larger data set where buyers generally do not know the exact sources of their data.

How, what, where, when, and why of experimentation
Every new feature starts as an idea. Not all ideas are good ideas. Therefore, not every new feature is a good idea. So how do you know which feature is a good idea and which one isn’t? You experiment.
The idea of experimenting on users or in production may sound scary and complicated, but it doesn’t have to be. The questions below shed some light on common questions surrounding experimentation and can help you determine if experimentation is right for you.

Amazon fights Microsoft's JEDI contract win in court over bias claims
When Microsoft was awarded the controversial $10 billion JEDI contract by the US Department of Defense, many people voiced surprise -- including rival bidder Amazon.
Now Jeff Bezos' company is heading to court, claiming that the process of choosing who to assign the contract to was biased. But these claims have been denied, with the Department of Defense saying there was no outside influence involved in the decision.
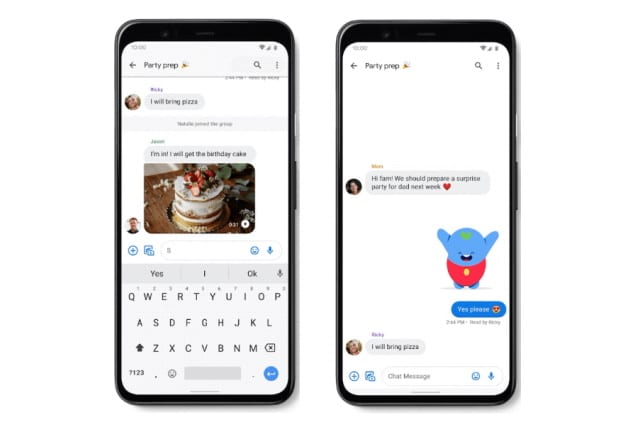
Google is rolling out RCS messaging to Android users in the US
The rollout of the successor to SMS is now underway in the US. Having brought RCS (Rich Communication Service) to the UK, Mexico and France, Google has started to deploy it in America.
The move comes as Google's frustration at carriers' apparent unwillingness to commit to RCS boiled over, leading the company to take the bull by the horns and start to push its own implementation of the standard.

MSI Cubi 5 should make an excellent mini Linux computer
If you want a basic Linux desktop, you can never go wrong with an all Intel-based mini computer -- such as that company's own NUC line. Things typically work without issue -- an Intel Wi-Fi card, for instance, shouldn't give you any headaches on Linux.
Intel is not the only game in town, however. Other companies manufacture and sell mini desktop computers too. Today, MSI unveils its latest, and it looks like a real winner. Called "Cubi 5," it comes with 10th gen Intel Comet Lake processors, USB-C, and supports Wi-Fi 6 (802.11ax).

Almost three quarters of retailers have been victims of cyberattack
Some 72 percent of retailers globally have experienced a cyberattack, with 61 percent experiencing one in the last year, yet 50 percent don't have a response plan in place to deal with data breaches.
This is among the findings of a new study carried out by the Ponemon Institute for Keeper Security, which also shows the average cyberattack on a retailer involving the loss of customer/employee data results in 7,772 individual records lost or stolen, with an average price tag of $1.9M from the disruption of normal operations.
