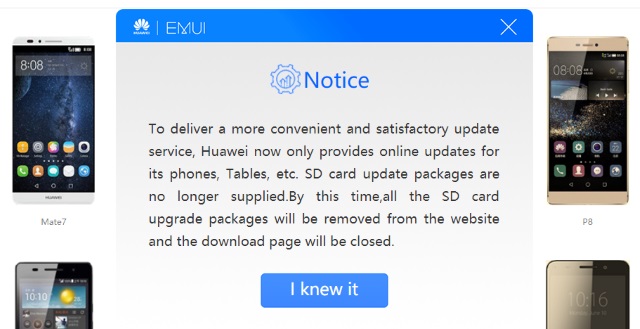
Want to download Huawei EMUI images? Tough... they've vanished!
Out of the blue, and without a proper explanation, Huawei has pulled EMUI images from its websites. Anyone looking for a ROM for their smartphone is now out of luck.
Although the Chinese company makes reference to wanting to give users a "more convenient and satisfactory update service," it's not really clear what this means in practice. The images could appear on a new dedicated site, but for the moment Huawei is remaining tight-lipped about what's going on.

New blood needed to solve the cyber security skills crisis
Senior figures in IT security see enticing staff from non-IT backgrounds and encouraging young people into the industry as vital to addressing the cyber security skills shortage.
A new study commissioned by MWR InfoSecurity and carried out by security discussion and networking group RANT shows respondents feel the core skills needed in cyber security are curiosity (46 percent) or on-the-job experience (34 percent), with no respondents saying a university IT degree is crucial.

How to disable a touchpad on a Chromebook
Using a Chromebook and having problems? You aren't the only one. In the middle of typing, your cursor can jump to the center of another sentence or jumble all of your words. It's not only annoying, it can get confusing to fix. What you need to do is disable the touchpad.
On some Windows PCs there's a simple solution that involves pressing a key at the top. That isn't the case with Chrome OS. It can be done, it just takes a bit more work to accomplish the goal.

Apple Music Festival is cancelled indefinitely
The Apple Music Festival -- formerly known as the iTunes Festival -- has been cancelled. The termination of the festival comes after a decade-long run which has seen performances from artists such as Oasis, Adele, Ed Sheeran, Coldplay, Lady Gaga and Elton John.
Once a month-long event, the Apple Music Festival shrank down to just a 10-nighter in recent years. Apple -- due to launch the iPhone 8 next week -- is unlikely to completely pull out of the music scene, having recently been involved in the sponsorship of shows by Lana Del Rey and Arcade Fire.

Official Plex for Kodi addon now available to everyone -- with and without a Plex Pass
It has been hard to escape talk of Kodi recently. The media center software has caused a great deal of controversy due to the number of addons that can be used to access illegal content. Most recently, the software hit the headlines after legal intervention lead to the withdrawal of the unofficial MK Plex addon that allowed for access to Plex through Kodi free of charge.
But now there's no need to turn to the dark side to get your Plex fix in Kodi if you haven’t paid for a Plex Pass subscription. The official Plex for Kodi addon is now available, and most features are available without the need to pay anything.

HPE offloads software division to Micro Focus
HPE has finalized the sale of its software division, bringing to an end one of the company's most traumatic periods.
The technology giant has confirmed the spin off of its software business in a deal with British firm Micro Focus which is valued at around $8.8 billion.

Apple launches premium Beats Studio3 Wireless headphones with W1 Bluetooth chip
Happy Labor Day, dear BetaNews readers! I hope you are off from work today, spending time with family and barbecuing some food on the grill. If you are working, as some folks have to do on holidays, I salute you. I just got home from a baseball game, where my beloved Mets beat the Phillies. America's pastime is a great way to celebrate today's holiday.
Another great way to celebrate? Listening to some rocking tunes! Whether playing some Lynyrd Skynyrd in the backyard on some speakers, or curled up on the couch with the latest from Lil Uzi Vert on some headphones, music can enhance the experience -- as long as you have some decent equipment, that is. Today, Apple launches a new set of wireless cans from its Beats by Dr. Dre subsidiary. The "Beats Studio3 Wireless," as they are called, look beautiful, but more importantly, they should sound exceptional.

Microsoft at the forefront of enterprise SaaS market
Enterprise SaaS market has seen growth of almost a third (31 percent) compared to last year.
That's according to the latest research from Synergy Research Group.

Juniper buys security startup Cyphort
Juniper Networks has announced plans to acquire security analytics software firm Cyphort.
By acquiring Cyphort, Juniper will have access to its open-architecture platform that features a machine learning powered analytics engine that is capable of integrating with existing security tools to aid companies in detecting threats that have been missed by their first-line of security.

Will my phone get Android 8.0 Oreo?
If there's one thing that the release of a new version of Android highlights, it's Android's fragmentation problem. While iPhone users can be sure of receiving iOS upgrades for a number of years, it's more of a gamble when it comes to Google's mobile operating system.
The number of handsets that will receive an Oreo upgrade is relatively small, so the chances are that the answer to the question posed in the headline is "no". That said, there are many phones that will get the update to Android 8.0 -- so here's the list.

Leaked Service Eligibility Guidelines show how Apple decides whether to repair or replace iPhones
What are the chances of getting a new iPhone if your handset develops some sort of fault? If you take a damaged or troublesome iPhone into an Apple store, you might be told you're eligible for a repair, or you might walk out with a completely new phone. A newly leaked document shows how Apple decides what treatment you receive.
A document known as the "Visual/Mechanical Inspection Guide" has been leaked to Dropbox, and it shows how Apple technicians choose between offering in-warranty repair, out-of-warranty repair, or a replacement phone.

Lenovo's new ThinkPad A laptops come with AMD Ryzen Pro chips
Lenovo has revealed details of an all-new build of its enterprise-focused ThinkPad notebook products.
Scheduled to mark the 25th anniversary of its iconic ThinkPad line, the two new A-series products will be the first notebooks to feature AMD hardware. Specifically, this means the chipmaker's all-new Ryzen Pro processors, which were shown off at an event in New York this week.
YouTube ripping site YouTube-MP3 to close after record label lawsuit
YouTube-mp3.org -- "the easiest online service for converting videos to mp3" -- is closing down. The ripping site faced action from numerous record labels, but it has now come to an arrangement with the RIAA.
The site is one of many that make it possible to convert YouTube videos into MP3 format, but it has piqued the interest of copyright lawyers. Millions of users meant the site was able to rake in ad revenue -- something the RIAA and record labels were less than happy about. An arrangement with the RIAA means YouTube-MP3 will close, leaving users looking for another site to cater for their YouTube ripping needs.

47 percent of UK teens have been cyber bullied
According to a new study of 1,000 UK teenagers, 47 percent have been cyber bullied with 70 percent experiencing it on social media and Facebook being the most common platform.
The survey by McAfee reveals part of the problem appears to be that teens are not getting proper guidance at home or at school about staying safe online.

Facebook has mapped the location of millions of people down to 5-meter accuracy
If you've ever thought that Facebook knows a little too much about you, here's something that's going to do nothing to dislodge that fear from your mind. Using a combination of government census information and data from satellites, the social networking giant has mapped the location of people in 23 countries around the world.
In all, Facebook knows where millions of people live down to an accuracy of 5 meters. All of this has been made possible by a mapping technology developed by Facebook to help it see how people are distributed across the globe to determine how best to supply internet to different parts of the world.


