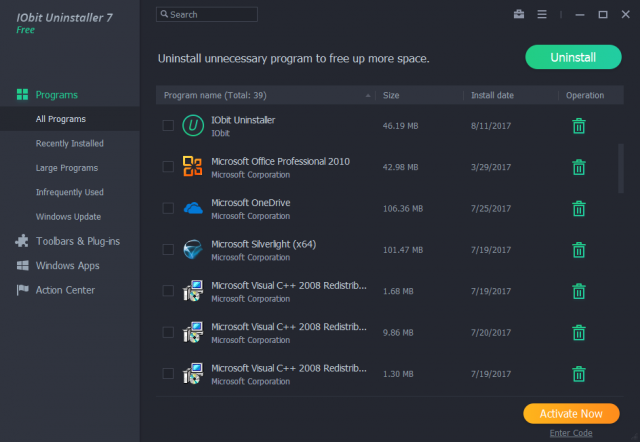
Remove stubborn apps, plugins and bundleware using IObit Uninstaller 7
Whilst dealing with malicious software is an ongoing issue, people overlook problematic software, downright stubborn applications and unwanted bundleware that can be difficult to fully remove from your system.
We can’t tell you how many people install security software, uninstall using Add/Remove Programs only to find new security won’t install as the previous suite wasn’t fully removed.
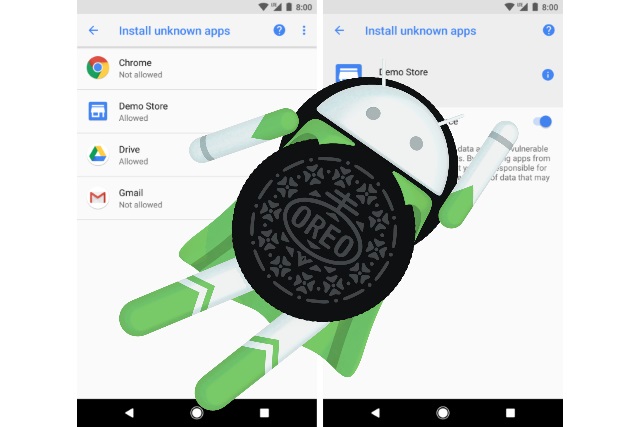
With Android Oreo, Google is stepping up app security
App security is undeniably an issue for Android users, particularly those who choose to install apps from outside of Google Play. Even apps that are housed in the main store are not immune to security issues, but those from other sources are rather more risky.
With Android O, Google has ditched "Allow unknown sources" -- the setting that could be toggled to allow for the installation of non-Play apps. Instead, there is a new "Install unknown apps" permission, and Google thinks this offers more control and greater security.

Google to reveal Titan security chip for cloud services
In an effort to better compete against Amazon and Microsoft in the cloud computing space, Google will this week reveal the technical details of its new Titan computer chip designed to protected the data centers powering its cloud services.
Apparently the chip is the size of a small stud earring and the search company has already installed it in many of the servers and network cards that comprise its own massive data centers. Titan scans network hardware to detect if any unauthorized changes have been made and if so the chip will prevent it from booting up.

Privacy: Mozilla to test opt-out telemetry collection in Firefox
Plex recently caused controversy by changing its privacy policy so users could not opt out of data collection -- although the company backed down after assessing the level of concern it raised. Now Mozilla looks set to raise the hackles of privacy advocates as well.
Mozilla engineers working on the Firefox web browser are concerned that the current opt-in system of data collection does not allow for the collection of unbiased data about which websites users visit and so on. As such a test period of telemetry which is opt-out is planned.

Microsoft releases Windows 10 Insider Preview Build 16273 and things are getting very confusing
The star of today is undoubtedly Galaxy Note8, but Samsung's new smartphone is not the only thing to get excited about. For those enrolled in Microsoft's Insiders program, there is a new Windows 10 build to install.
Microsoft just pushed out Preview Build 16273. This is just one day after releasing a new Windows Server Insider build. While the server build had literally zero new features, the new Windows 10 build does have some; there is a new font and emoji notifications. Unfortunately, the Insiders Program is getting quite confusing. Dona Sarkar tries to explain it all, but you might be left with smoke coming out of your ears. What was once a fun way to test early builds of Windows is beginning to get very convoluted.

Galaxy Note8 hands-on first impressions -- Samsung pulls no boners
Earlier today, I took a journey to New York City to attend Samsung's Unpacked 2017 press event. I expected to see the Galaxy Note8 unveiled, and unsurprisingly it was. Sadly, the press event was sort of ruined as the company released all of the device details online just as the presentation began. Oh well. Such is life.
Let's be honest though, due to leaks, there weren't many surprises to be had anyway. Still, I expected to be impressed by the new phone, and I am happy to say that I was not disappointed. I got the opportunity to have some hands-on time with the Galaxy Note8 and I can say that Samsung has seemingly done everything right. In other words, Samsung has not pulled a single boner. Did it blow me away? No, but it still seems to be a solid evolutionary device.

Spam is still a key tool for hackers
Online criminals are keeping the faith with spam email campaigns, with more and more nuisance messages being sent today than ever before.
Figures from IBM have shown that spam email remains a key tool for hackers, with the volume of such messages increasing 400 per cent in the past year.

Fujitsu wants to sell its smartphone business
Fujitsu is preparing to sell off its mobile phone operations as the company faces increasing competition from its larger rivals in the mobile phone space.
Last February, the Japanese manufacturer decided to spin off both its mobile phone and PC businesses into separate companies in an effort to differentiate its offerings.

Ouch, that hurts! Verizon's new Unlimited plans throttle customers
I should have known better. Once burned is supposed to be twice as wary. Right? Disgruntled by pricing and other policies, in autumn 2015, I took my family from Verizon Wireless to T-Mobile, which cut our monthly bill by more than one-third. But in May of this year we made the trek back in part because data speed is so much faster from my apartment than it is with Magenta. Better Red than dead, eh? Wrong. Oh, dumbass me. Un-carrier's aggressive pricing, and Verizon's first-ever quarterly loss of post-paid subscribers, compelled the nation's largest carrier to respond—by, starting in February, to offer comparable unlimited plan that for my family of five lines would cost just $20 more a month while delivering superior, speedy service. But what Red gave, it now takes away. I regret the decision.
Today's unlimited cellular service plan changes suck some of the most important value from all that extra bandwidth. What good is having something you can't use? Henceforth, Verizon will offer two consumer options—one (Go Unlimited) that throttles streaming video to 480p on smartphones and costlier option Beyond Unlimited that reduces quality to 720p. Go is essentially priced the same as the older unlimited plan, and it takes away even more: Tethering (e.g. Mobile Hotspot) is capped at 600kbps. There's no 4G LTE for you, baby!

DDoS attacks increase by 28 percent in Q2 2017
DDoS attacks are seeing a major rise as hackers seek more diverse threats, according to new research.
The latest State of the Internet/Security Report from Akamai reveals that the number of DDoS attacks increased by 28 percent in the second quarter of 2017, following three consecutive quarters of activity decline, as attacks from the PBot malware hit a new high.

Samsung announces Galaxy Note8 -- here's what you need to know
The Galaxy Note8 is the most important smartphone that Samsung launches this year. Its predecessor nearly killed the high-end series, which is why Samsung cannot afford to make any mistakes with its latest flagship: the Galaxy Note8 has to be great. No pressure there, right?
The good news is that the Galaxy Note8 does not disappoint: it has all the right features that you expect from a high-end smartphone and a clear edge over the Galaxy S8, which is unquestionably the best smartphone Samsung sells today.

AI-powered analytics unlock commercial relationship data
Details of the deals that a business has with other organizations are usually locked up in contracts or other documents such that valuable information is either not readily available or easily overlooked.
California-based Pramata is launching a suite of analytic applications that can identify critical information in existing contracts and combine it with data from business systems such as CRM and billing to benefit commercial relationships.

What is Google Chrome Enterprise?
Chromebooks are gaining traction because they are simple, easy to use and offer great value. For consumers, they can be fantastic options. For enterprises, however, Chrome OS needs to go the extra mile in order to become more attractive.
Google is well aware of the longer list of needs that enterprises have, as compared to consumers, which is why it has introduced a new plan, called Chrome Enterprise, that adds a whole host of new features designed specifically with business customers in mind.

New portal helps developers integrate payment solutions
One of the keys to monetizing apps is to have an effective and easy to use payments solution built in. Payment solutions company Qualpay is aiming to make this process easier by offering a portal to make the selection of systems easier.
Qualpay for Developers allows developers looking for easy-to-implement payment APIs to use the portal to evaluate and deploy multiple payment solutions or work with Qualpay to tailor the platform for specific environments.

Microsoft will never again sneakily force Windows downloads on users
There have been various controversies with Windows 10, from issues with privacy and telemetry, to ads and forced upgrades. Following a court case, Microsoft has vowed to never force upgrade files onto users again.
Windows users in Germany were particularly unimpressed when Microsoft forcibly downloaded many gigabytes of files to upgrade from Windows 7 and 8 to Windows 10. Having held out for 18 months, and losing its case twice, Microsoft has finally agreed to stop its nefarious tactics.


