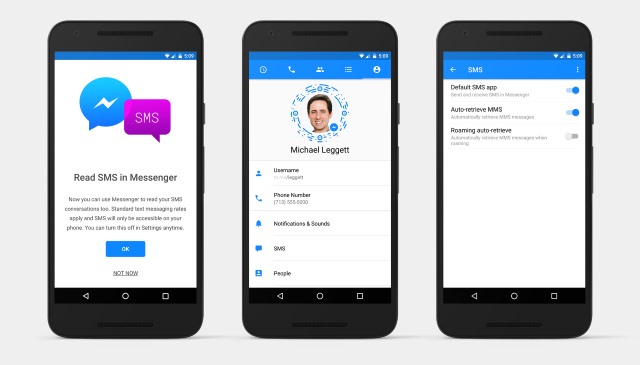
Facebook Messenger gets data-saving mode in beta, test it now
Little more than a week ago, Hurricane Matthew rolled up the southeastern US coast, wreaking havoc from Florida to North Carolina, with the latter seemingly getting the smallest hit, though it turned out the worst in the long run. My cousin, located there, was without power for some 48 hours and was forced to place his phone in power-saving mode. This eliminated Messenger and all information we received from him afterwards came from texts.
SMS, it seems, is fine in that mode, but Messenger was not -- he claimed he could see that he had messages, but he couldn't read them.

How to significantly improve Windows 10's wallpaper quality
You may be more than happy with your choice of Windows wallpaper, but what you may not know is it’s not as good as it could be.
I’m not saying the image itself isn’t great, but the problem is Windows 10 automatically compresses the picture to help system performance, and that reduces the overall wallpaper quality, quite considerably.

What you need to know about product lifecycle management
In any kind of production process, whether the end product is a washing machine or a piece of software, there are a number of stages to go through. From the initial idea, through design to manufacturing, service and support, and end of life and disposal, all products go through a similar lifecycle.
Product lifecycle management is about integrating the staff, data, processes and business systems that go to produce a product. This in turn provides a fund of information surrounding the creation of the product which can be used to streamline the development of future products. PLM software allows this to be done cost effectively across the entire lifecycle of a product.

Acer updates Chromebook 15 with 12-hour battery life -- $199 exclusively at Walmart
Chromebooks are not for everyone, but for many home users, it is absolute perfection. If you live in the web browser -- as many people do nowadays -- laptops running Google's Linux-based Chrome OS are a godsend because they are maintenance free. No need for confusing OS upgrades or anti-virus software. It just works, and it works well. Since they can now run Android apps too, they could become a serious threat to Microsoft and Windows 10.
One of the most attractive aspects of Chromebooks is price -- they are often quite affordable. Today, Acer refreshes its 15.6 inch Chromebook 15 with a mind-boggling 12 hours of battery life. Best of all? It starts at $199. Yes, this model will get Android app support in a future update too.

Germany tells Tesla to stop using 'misleading' Autopilot term
The German government has labeled Tesla's use of the Autopilot name to describe its assisted driving technology "misleading" and asked the US car maker to stop using it in advertisements. The system is not currently completely autonomous, as it requires driver supervision, based on SAE standards.
"In order to prevent misunderstanding and incorrect customers’ expectations, we demand that the misleading term 'autopilot' is no longer used in advertising the system", says German transport minister Alexander Dobrindt. "Autopilot is a pure driver assistance program, and not a highly automated vehicle that can be operated without constant attention of the driver".

MI5, MI6 and GCHQ secretly and illegally collected data about British citizens for over a decade
The surveillance activities of the NSA in the US, along with MI5, MI6 and GCHQ in the UK, have been known about for some time now, largely thanks to Edward Snowden. Now the Investigatory Powers Tribunal has ruled that for more than a decade, huge amounts of data were collected without adequate oversight, breaking privacy laws.
The tribunal also said that some instances of data collection failed to comply with the European Convention on Human Rights (ECHR). Privacy International, the group who brought the complaint against the spy agencies, said that this is a "highly significant judgment".

This map shows Wi-Fi information and passwords from airports around the world
Many years ago, I whiled away a long wait at a tiny airport by playing Snake on my Nokia phone. I literally did nothing for hours, except guide an ever-growing line around a small screen. These days, thankfully, there are much more entertaining diversions to be had on your phone.
Free airport Wi-Fi has been a godsend for many a traveler over the years, but it’s not without its problems -- you might need a password, and there could be restrictions in place to be aware of.

How incentives are key to driving mobile wallet use
Mobile wallets are gaining in popularity, according to a new survey by loyalty platform Points almost 64 percent of consumers say they've used a mobile wallet in the past year.
However, some consumers are still reluctant to make mobile payments for a variety of reasons. 47 percent are concerned about security and privacy, 45 percent say that credit and debit cards and/or cash are enough, and 20 percent say it’s too complicated.

Microsoft introduces compliance guidance for Azure Government users
In an attempt to assuage concerns regarding how its cloud software and services designed for government agencies work, Microsoft has released new documentation for potential customers of Azure Government.
Microsoft Azure Government has already earned quite a few certifications acknowledging that it meets the strict requirements of the US federal government. However, for customers that believe this is not enough, the software giant has created its new Azure Blueprint program to help users use its cloud platform in a way that is compliant with government guidelines.

rclone syncs cloud storage files from the command line
Rclone is an open-source command line tool which enables copying and syncing data to and from a host of popular cloud storage providers.
Supported technologies include Google Drive, Amazon S3, Openstack Swift / Rackspace cloud files / Memset Memstore, Dropbox, Google Cloud Storage, Amazon Drive, Microsoft One Drive, Hubic, Backblaze B2, Yandex, and -- if all else fails - your local file system.

Microsoft predicts an 87 percent chance of Hillary Clinton winning the election
The United States presidential election is set to be held on November 8, 2016, and it’s going to be one of the more interesting in recent years, as the run up has already proved.
Both Hillary Clinton and Donald Trump are highly divisive candidates, with their fair share of bad publicity, but who will win the day? Microsoft thinks it knows, and is predicting a landslide for the Democratic nominee.

Facebook on the frontline: livestreaming Iraqi and Kurdish forces trying to wrestle Mosul from ISIS
When Facebook Live launched as a service available to everyone (after a celebrity-only debut) it didn’t take long for people's fears of terrible incidents being broadcast to come true. We've had celebrities livestreaming, we've had death, injuries and accidents livestreamed. What next? War.
Over in Iraq, the city of Mosul is currently under the control of ISIS. Iraqi and Kurdish military forces are in the process of attacking the city to regain control. What's unusual -- and particularly disturbing -- about this is that the whole event is being livestreamed on Facebook by Kurdish media group Rudaw -- complete with viewers' reactions in the form of cartoon emoji.

Netskope expands its Threat Protection product to cover ransomware
Ransomware is increasingly big business and more than 43 percent of malware types are used to deliver it. It can also be unwittingly spread via the use of cloud services.
To protect against the threat, cloud security company Netskope is adding ransomware detection and recovery capabilities to its Netskope Threat Protection product.

How to turn off Facebook live video notifications
It can be useful finding out when friends are broadcasting live on Facebook, but unfortunately -- depending on your friends, of course -- there is a good chance they won’t be broadcasting something so interesting you’ll want to drop whatever you’re doing to watch there and then.
Facebook will alert you when someone is live, but like any notification, you can disable this so you won’t be alerted when Dave takes a motorbike ride in the rain, or Ellie’s children perform an out-of-tune rendition of "Let it go" from Frozen.
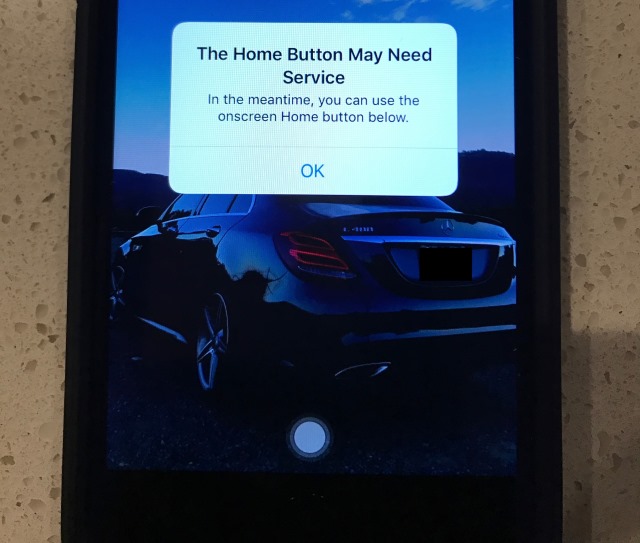
iOS 10 has a hidden onscreen Home button for iPhone 7 users
With the launch of the iPhone 7 and iPhone 7 Plus Apple not only removed the headphone jack, the company also replaced the mechanical home button with a static one. What was not revealed, however, is that iOS 10 also has a secret software Home button.
The feature is a safeguard built in should anything go wrong with your physical home button. Should this happen, the button problem will be detected and iOS 10 will offer up a temporary on-screen Home button to tide you over until you can get to the Genius Bar.


