
Microsoft HoloLens can run Windows apps in 3D
When Microsoft unveiled HoloLens a few months ago, it came as something of a surprise. It's essentially Google Glass meets virtual reality on steroids, throwing the users into a 3D world filled with holograms, all powered by Windows 10. Today at build 2015, Microsoft showed off some of HoleLens' capabilities.
Something that had been talked about when HoloLens first came to light was the possibility of running regular Windows 10 apps in HoloLens. In a demonstration, Microsoft showed how Windows 10 Universal apps can be used in 3D space, 'projected' onto floors, walls and other surfaces.
Microsoft's new browser -- Project Spartan changes to Microsoft Edge in Windows 10
Project Spartan -- the all new Web browser which Microsoft announced at an event in January -- now has a proper name. At its developer conference Build 2015, the Redmond, Washington-headquartered software company announces that it will be calling the new browser Microsoft Edge.
Microsoft Edge, which is a successor to the age old internet navigation tool -- and source of tons of jokes and memes -- Internet Explorer, is designed to surf on the waves of the modern Web. Interestingly, the company seems to be using the same moniker it used while christening the new rendering engine (EdgeHTML) that powers Edge.

Blame the dollar: PC prices rise, as features fall
Gartner predicts that currency devaluation will compel major computer manufacturers to reverse a longstanding trend. "PC vendors selling to Europe and Japan, where local currencies have fallen up to 20 percent since the start of 2015, have little choice than to raise prices to preserve profits" -- by as much as 10 percent, Ranjit Atwal, Gartner Research director, says in a statement earlier today.
Higher prices mean more consumers will do with leaner configurations, and many businesses will push back upgrades. All the while, PC makers will give customers less for more money. Atwal anticipates fewer features in new computers in affected markets and increased sales emphasis in "regions least affected by these currency effects".
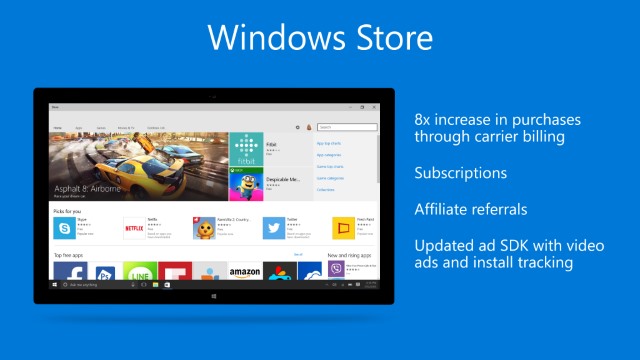
Windows Store to gain subscriptions and phone payments
Today at Build 2015, Microsoft revealed some exciting changes to the Windows Store -- not least that it will soon be much, much easier for iOS and Android app developers to convert their creations into Windows 10 apps. But this is far from the end of the story, and there are also important payment and subscription options on the horizon.
Microsoft is introducing support for in-app purchasing of subscriptions, providing developers with new ways to monetize their apps. To help make it easier for devs to get money from customers, the ability to pay for purchases with a mobile phone is also to be added.
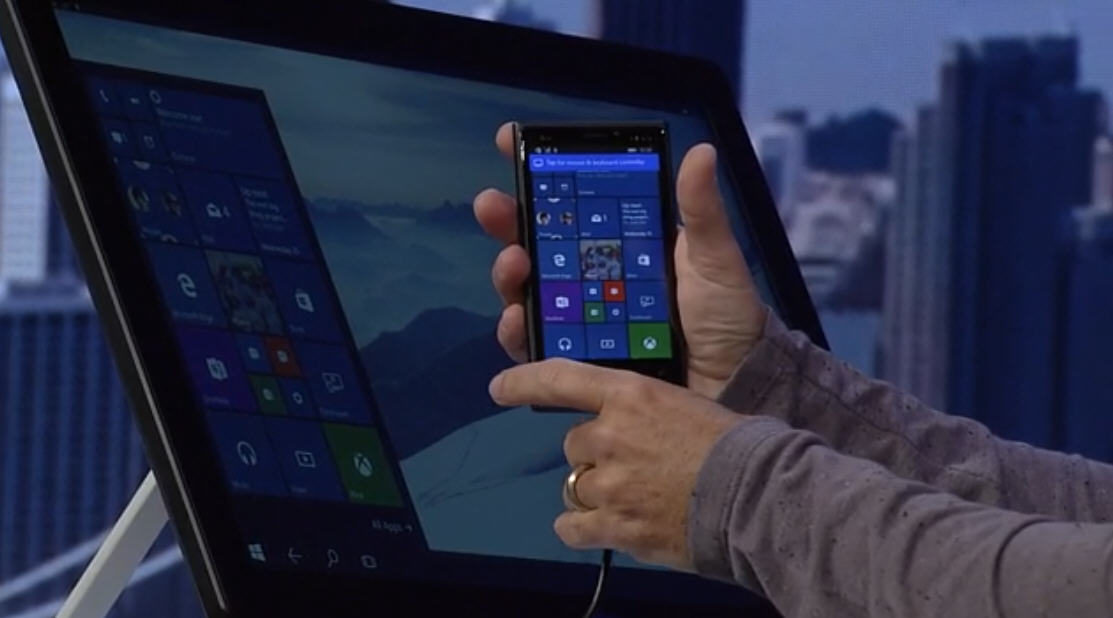
Windows 10 will turn your smartphone into a tiny PC
Smartphones are essentially pocket-sized computers, packed with processing power. However, Microsoft sees its devices as actually functioning as full-blown (if somewhat underpowered) PCs, once Windows 10 for phones arrives.
At the Build developer conference, the company showed how Continuum can transform a Windows Phone into a tiny Windows PC.

Microsoft's final attempt to save Windows Phone: Introduces support for Android apps, lures iOS devs
Microsoft has a four-fold plan to close Windows Phone’s infamous 'app-gap' problem. At its ongoing developer conference, Build 2015, the Redmond-based company announces that it is making it easier for developers to bring their apps to the Windows Phone platform.
The first way is to entice Web developers to wrap their sites into apps and release them on the Windows Store. The second -- arguably, the least exciting -- is to make Windows apps the traditional way -- using existing Win32, .NET WinForms and other Windows development technologies.

Microsoft aiming for 1 billion Windows 10 devices in 2-3 years
Windows 8.x is a massive failure for Microsoft, with a usage share that’s well below that of Windows XP.
With Windows 10, Microsoft is hoping to put the past behind it, and produce an operating system that isn’t overshadowed by older Windows versions.

Samsung fights for 'Avengers: Age of Galaxy S6'
Samsung is down but not out in the global smartphone shipments battle with top rival Apple. That is the conclusion from analysts at Juniper Research, which like Strategy Analytics released first quarter 2015 data today. Juniper sees sharp rebound from Galaxy S6 and S6 Edge, which "reception" is stronger than their predecessors.
Quarter-on-quarter, Samsung smartphone shipments -- 82 million units -- rose by 23 percent but fell 29 percent year over year. By comparison, annually, Apple shipments soared by 40 percent, to 61 million, largely lifted by China. The country's importance to the fruit-logo company cannot be overemphasized for either manufacturer. But Apple reaped the big crop, with shipments up 71 percent that generated $16.8 billion in revenue.

Heavens! Microsoft releases Visual Studio Code for Linux and Mac OS X (and Windows)
Satya Nadella’s Microsoft is a lot different from the Microsoft he took charge of from Steve Ballmer last year. It’s open, it’s bold, and it’s kicking. At the ongoing Build 2015 developer conference, the Redmond-based software mammoth announces the launch of Visual Studio Code, a cross-platform code editor for writing modern web and cloud apps. The interesting bit? In addition to Windows, the Visual Studio Code runs on Linux as well as Apple’s Mac OS X desktop platform. Also, it’s free and you can download a technical preview of it right here.
The full-fledged Visual Studio is still Windows-only, but with the new Code the company is opening up to other platforms. The idea is simple. A lot of people use Linux and Mac, so let’s make a development environment that could support their preferred platform.

Google's open source 'Password Alert' protects your login credentials from phishing attacks
Google is life. Well, not really, but for some people it kind of is. For many of us, a Gmail account became a gateway to an entire Google lifestyle. One password logs us into numerous services, which is super convenient, but also quite scary. Over time, it is easy to let your guard down and fall for phishing sites that pretend to be a legit Google login. If your Google credentials are intercepted, you are going to have a bad time.
Today however, the search-giant releases an open source Chrome browser extension aimed to thwart these stinky phishing goons. Called "Password Alert", it will hopefully protect your credentials and keep the sun shining on planet Google.

Incentive launches Dropbox integration for secure file collaboration
Businesses often use different applications to create, store and share content. Whilst most enterprise collaboration tools allow for some sort of file sharing it can involve additional time and effort importing data.
The Incentive platform is now making sharing information easier by adding one-click integration with Dropbox cloud storage.
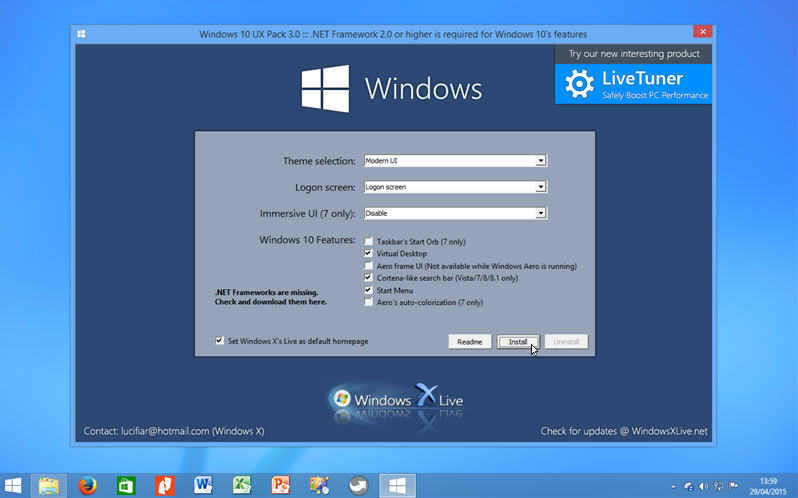
Windows 10 Transformation Pack 3.0 and Windows 10 UX Pack 3.0 arrive
WindowsX has released Windows 10 UX Pack 3.0 and Windows 10 Transformation Pack 3.0, new builds for its Windows skinning tools.
Each tool allows users to emulate the forthcoming Windows 10 user interface on PCs running older versions of Windows from XP upwards, the difference being that the UX Pack is less radical and promises not to touch any system files, making it easier and safer to use.

Hackers plunder $5 million from the account of Irish airline Ryanair
It's one thing to have your personal bank account hacked, you may lose a few dollars or worse a small fortune. However you would expect corporate accounts to have added security, preventing such a devastating event. That's clearly not the case. While we've seen point-of-sale systems hacked and customer data stolen, this time it was actually a company bank account that was robbed.
Irish airline Ryanair had its corporate account plundered by hackers to the tune of $5 million, or €4.6 million. The money apparently disappeared from accounts used to fund the fueling of the company's planes, not a cheap task and perfect for not immediately ringing alarm bells.

'You don't post pictures of us on Facebook -- I want a divorce!'
According to a new survey of 2,000 people in the UK, one in seven say they've contemplated divorce because of their partner's activity on social media.
Nearly a quarter also say they have at least one row a week with their partner because of social media use and 17 percent say they argue every day because of it.

Caddy is a hassle-free web server
Running your own local web server can make it easier to develop and test websites, but there’s one small obstacle to install first: you’ll have to find, download and install one, and figure out how to set it up.
Caddy is a simple but surprisingly capable server which cuts through the usual hassle and can handle simple sites with no configuration at all.



