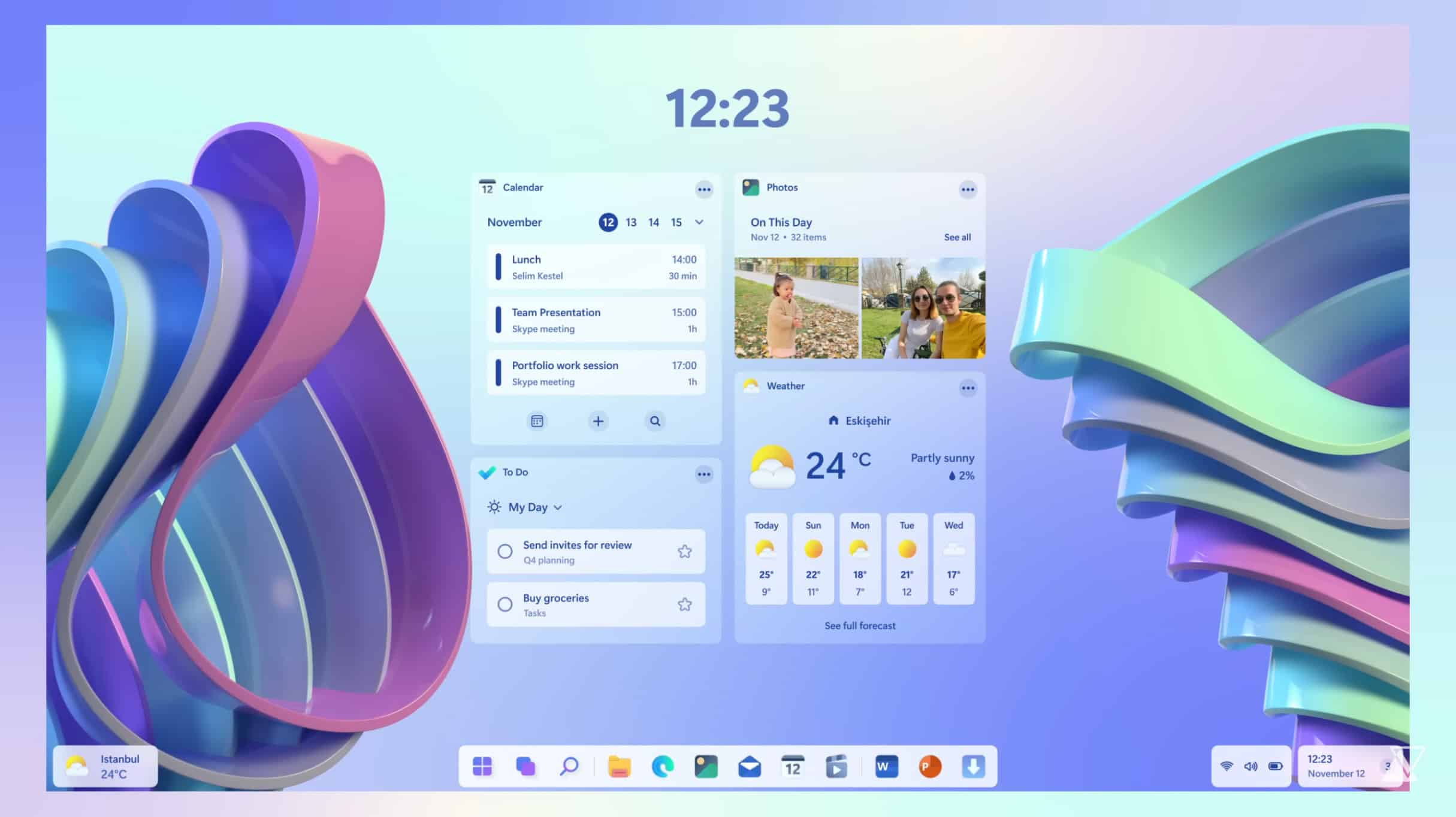
Adaptive wallpapers could bring the Windows 12 desktop to life
Although Windows 10 is the leading desktop operating system by some way, Microsoft will be praying that Windows 11 starts to gain more users throughout 2023.
While the new OS does have some features that set it apart from its predecessor, most notably a centered taskbar, for many users the differences don’t go for enough, and they’ll be hoping that Windows 12 will step things up significantly.

Platform engineering, SBOMs and off-the-shelf solutions -- development predictions for 2023
Developers are under more pressure than ever to deliver projects quickly, but at the same time applications and the supply chain need to be kept secure.
So, what things can we expect to see for development in 2023? Here are some expert views on the key trends.

Geopolitical threats, supply chain issues and phishing scams -- cybersecurity predictions for 2023
The cybersecurity world never stands still, with threats and the technology to combat them constantly evolving.
That makes predicting what might happen difficult, but we can still extrapolate current trends to get an indication of where things might be headed. Here are some expert predictions for cybersecurity in 2023.

Rebuilding trust between developers and security [Q&A]
The demands of modern business IT environments can often lead to friction between developers and security teams which can hamper the successful rollout of cloud security.
Developers want to deliver features as fast as possible and security teams want things to be as secure as possible, so there is constant conflict of interest. We spoke to David Hendri, CTO and co-founder of cloud security startup Solvo, to discover how to rebuild the trust between developers and security by creating a common language.

The missing piece in the MSP data security puzzle
In the dynamic world of Managed Service Providers (MSPs), it has become quite evident that the time has come for next generation Data Security Solutions, and that such a solution should be added to your technology stack.
For some time and becoming ever more frequent today, organizations and MSPs are facing major data security challenges that are likely to increase exponentially over the coming decade.

Look back and look forward when walking into a new MDR relationship
The managed services market is bringing more and more providers into the mix, as an increasing number of organizations decide it makes fiscal and operational sense to outsource key functions, even those which traditionally have been considered especially critical, such as certain information security-oriented tasks. Perhaps the fastest-growing segment of service providers in this space is MDR -- managed detection and response.
The MDR concept is relatively young in the service provider space. MDR offerings are typically designed to augment your SOC (security operations center) function by providing detective and reactive tools and expertise. In some cases, it may even replace your tier one, or triage-level, security analysts, who are focused on reviewing and confirming the sometimes overwhelming flood of incoming security alerts.

Why proactive protection is key to effective cybersecurity
Compared to many industries, cybersecurity operates in a highly adversarial environment, with organizations investing huge levels of time, money and resources into defeating a range of determined threat actors. If that weren’t enough, security teams are pitted against highly motivated, well-organized criminal and nation-state groups who constantly shift tactics to gain the upper hand.
The result is that security teams are frequently inundated with alerts, false positives and negatives, which nevertheless, they are compelled to address rather than being allowed to concentrate on proactively securing their networks.

In 2023, organizations must prepare for a growing attack surface, the war for cyber skills, and the rise of unknown threats
In the world of cybersecurity, year after year we encounter new threats and challenges, and 2023 is going to be no different. Currently, organizations are dealing with a growing number of unknown cyber threats targeting on-premises systems, cloud infrastructure, and SaaS applications. Added to this, the skills shortage is worsening too, causing analysts to becoming overloaded and burnt-out. Combined, this is creating a perfect storm, leaving organizations more vulnerable to a breach in 2023.
So, what specifically do organizations need to be aware of? Here are four trends that will shake up the cyber landscape next year.

2023 predictions: Automation, right sizing cloud requirements, zero trust and the growing importance of AI observability
2022 was a year of extreme complexities. With the post-pandemic and Brexit fallout, cost of living rises and inflationary pressures, geo-political issues, ongoing climate crisis, supply chain shortages and growing cybersecurity and data security threats, it was undoubtably another unprecedented year.
In fact, ransomware set annual records again, with new ransomware strains emerging. Additionally, cloud adoption continued to grow, while the IT jobs market experienced significant skills shortages. As we look forward to the start of a new year, what trends are on the horizon in 2023 and what issues will organizations be grappling with?

Leaked: Microsoft is bringing tabs to more apps in Windows 11
Having revolutionized the way we browse the web, tabs made their way to File Explorer in Windows 11. Now, thanks to a premature -- and now-deleted -- tweet, we also know that Microsoft is looking to do the same with other apps.
A Microsoft employee shared a screenshot on Twitter that depicts an updated version of the Notepad app, complete with two open tabs. It is not known if the addition of tabs will come in the next Moment update for Windows 11, but it is something that is undergoing internal testing.

Twitter removes suicide prevention feature at Musk's request -- [UPDATED: it's back, with Musk claiming 'fake news']
Twitter has, without making an announcement, removed a feature that directed users towards suicide prevention services after searching for certain content.
The #ThereIsHelp feature was removed after Elon Musk issued an order to that effect. Sources familiar with the matter say that the removal is only temporary and that a revamped version will be launched in the future. But the social platform has been criticized not only for the timing -- Christmas is a tough time for many people -- but also for removing the existing support feature before having a replacement ready. [UPDATE -- the feature is now back. Despite the fact Twitter confirmed its removal, Musk used a series of tweets to denounce reports that it had temporarily been removed as 'fake news']

The final build of Kodi 19 'Matrix' arrives in time for Christmas, but it won't be coming to Google Play or the Microsoft Store
While Kodi 20 'Nexus' is nearing an official release, it’s not quite game over for Kodi 19 'Matrix' as the Kodi Foundation has just released version 19.5 and you can download it now.
This will be the final release for Matrix however -- all future Kodi releases will be for Nexus -- and this update won't be coming to Google Play or the Microsoft Store either, although there's a good reason for this.

Is AI the future of content marketing?
As technology advances, so does how we market our products and services. And with the rise of artificial intelligence (AI), businesses are beginning to explore how this innovative technology can be used to improve their marketing strategies.
AI offers several content marketing advantages, including personalizing content, targeting specific audiences, and optimizing campaigns. As more businesses adopt AI-powered content marketing, it is becoming increasingly clear that this technology is the future of content marketing. This article will explore the various ways in which AI is shaping the future of content marketing.

Celebrate the birth of Jesus Christ by installing Manjaro Linux 22.0 'Sikaris'
Tomorrow is one of the most important days of the year -- Jesus Christ's birthday! Also known as "Christmas," many people celebrate the holiday by giving gifts to friends and family. And of course, Santa Claus will be delivering many great presents to all the non-naughty children of the world too.
As an early Christmas gift, the Linux community is getting something very special today -- Manjaro 22.0! Code-named "Sikaris," this operating system is based on the excellent Arch Linux. If you love using a modern kernel, you will be happy to know Manjaro 22.0 comes with version 6.1. There are three desktop environments from which to choose -- GNOME (43), KDE Plasma (5.26), and Xfce (4.18).

The age-old question in 2023: How to deal with ransomware?
It has been a devastating year for organizations in the fight against ransomware, with the news this year being a revolving door of ransomware breaches. Research by Zscaler revealed that there had been an 80 percent increase in ransomware attacks year-over-year.
It’s not just an increase in the number of ransomware attacks but also the catastrophic impact they can have on businesses, employees, customers and the wider popular itself. Shockingly, the average cost of a ransomware attack is $4.54 million, and destructive attacks can increase this cost by over $430,000. So, as 2023 quickly approaches, what ransomware threats should we expect?



