
Microsoft slowly rolls out a button allowing Windows 10 users to refuse Windows 11
It is a drum that has almost been beaten to death, but the impending end of support for Windows 10 is not a story that is going to go away any time soon. Even when mid-October rolls around – the cut-off date – this is far from going to be the end of news, reminders, and more.
For now, however, there is some form of respite for Windows 10 users. Microsoft is rolling out a way to halt the constant pestering to upgrade to Windows 11. There is, of course, a catch.

Sam Altman wants to give everyone in the UK free access to ChatGPT Plus
The head and co-founder of OpenAI, Sam Altman, entered into discussions aimed at striking a deal to bring ChatGPT Plus to everyone in the UK at no cost to end users.
In a meeting between the UK’s technology secretary Peter Kyle and Altman, there was talk of granting UK residents access to a more advanced tier of ChatGPT as standard. The deal – while not definitely dead in the water – appears to have stalled, but the idea is an extremely interesting one.
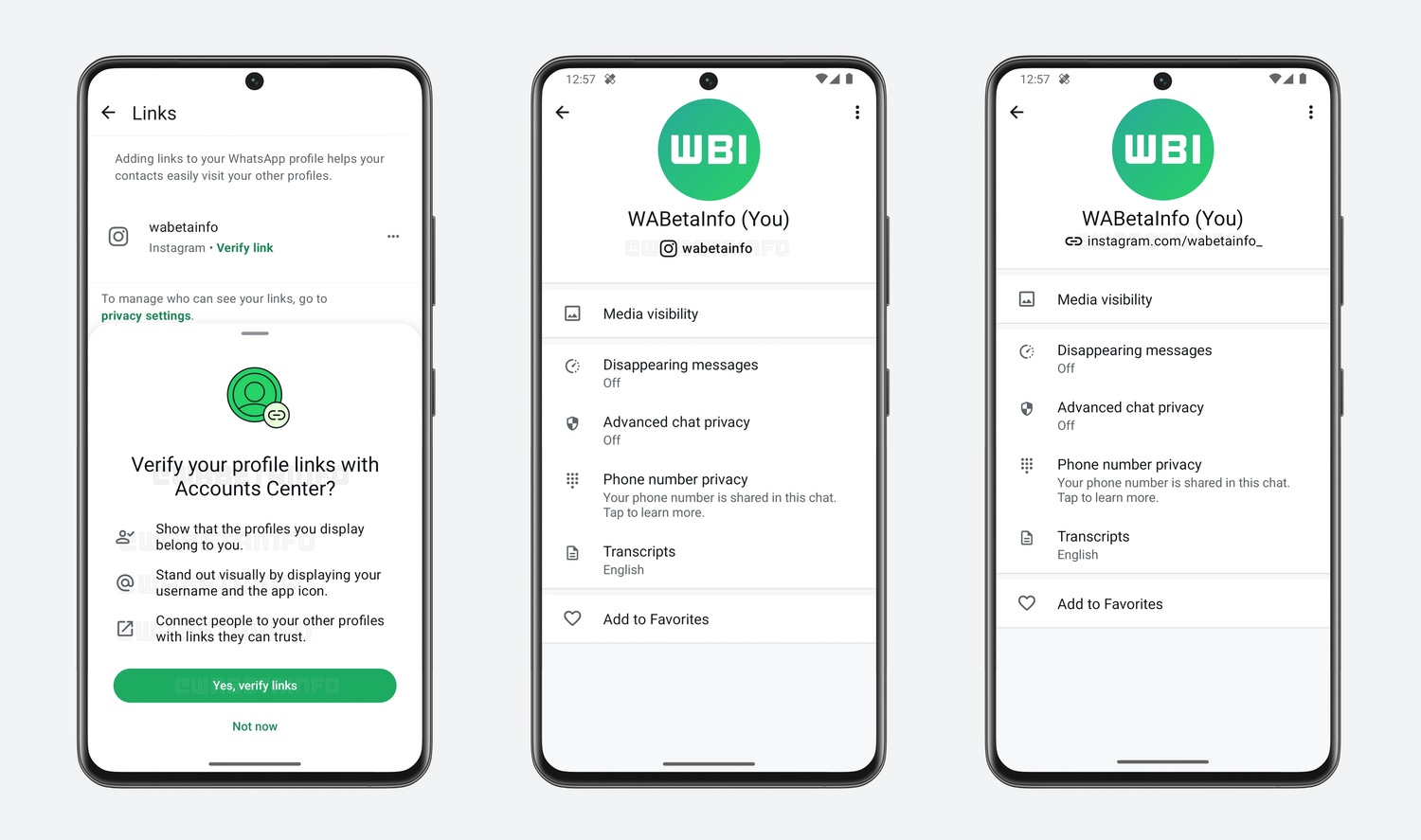
WhatsApp is working on Instagram profile verification
WhatsApp beta testers have access to a new option that allows them to link to a verified Instagram profile, complete with a special icon that others should recognize.
This ability is not necessarily something that will appeal to or interest all WhatsApp users, but it is certainly something that has value for some types of user. Creators are among those who are likely to welcome this addition, as are companies and brands looking to build trust and drive engagement.

xAI makes Grok 2.5 open source and plans the same for Grok 3
Many of the concerns about artificial intelligence can be overcome through transparency. And it is in the name of transparency that Elon Musk has announced the open sourcing of its Grok 2.5 model.
More than this, the AI firm will also make the Grok 3 model open source is around six months.
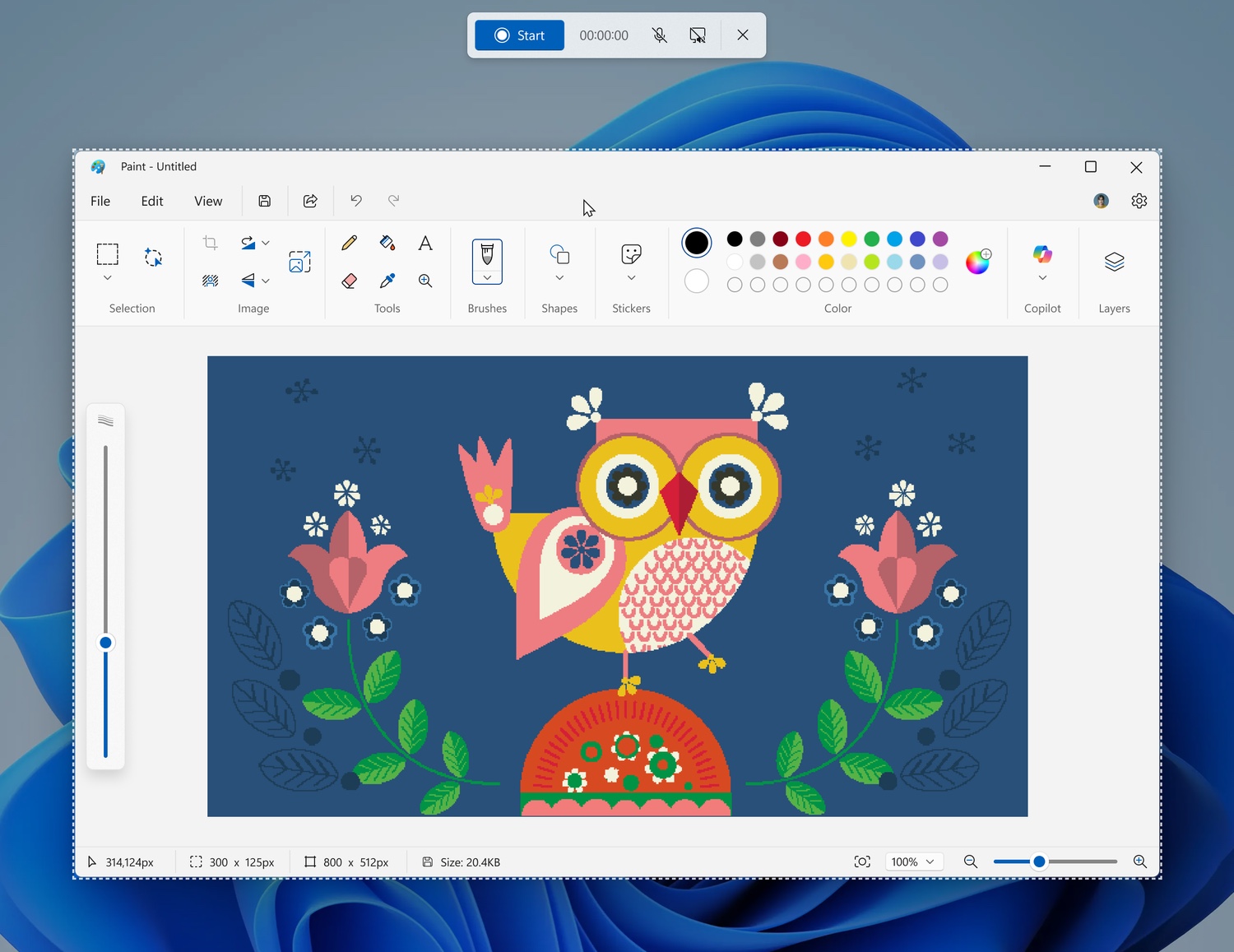
Snipping Tool gets a handy window recording mode
What started off as a simple screen-grabbing tool has evolved into something powerful and impressive. The Snipping Tool goes from strength to strength, and for Windows Insiders Microsoft has a new option to play with.
The feature is an expansion of Snipping Tool’s screen recording capabilities, this time making it possible to limit recording to a specific window.
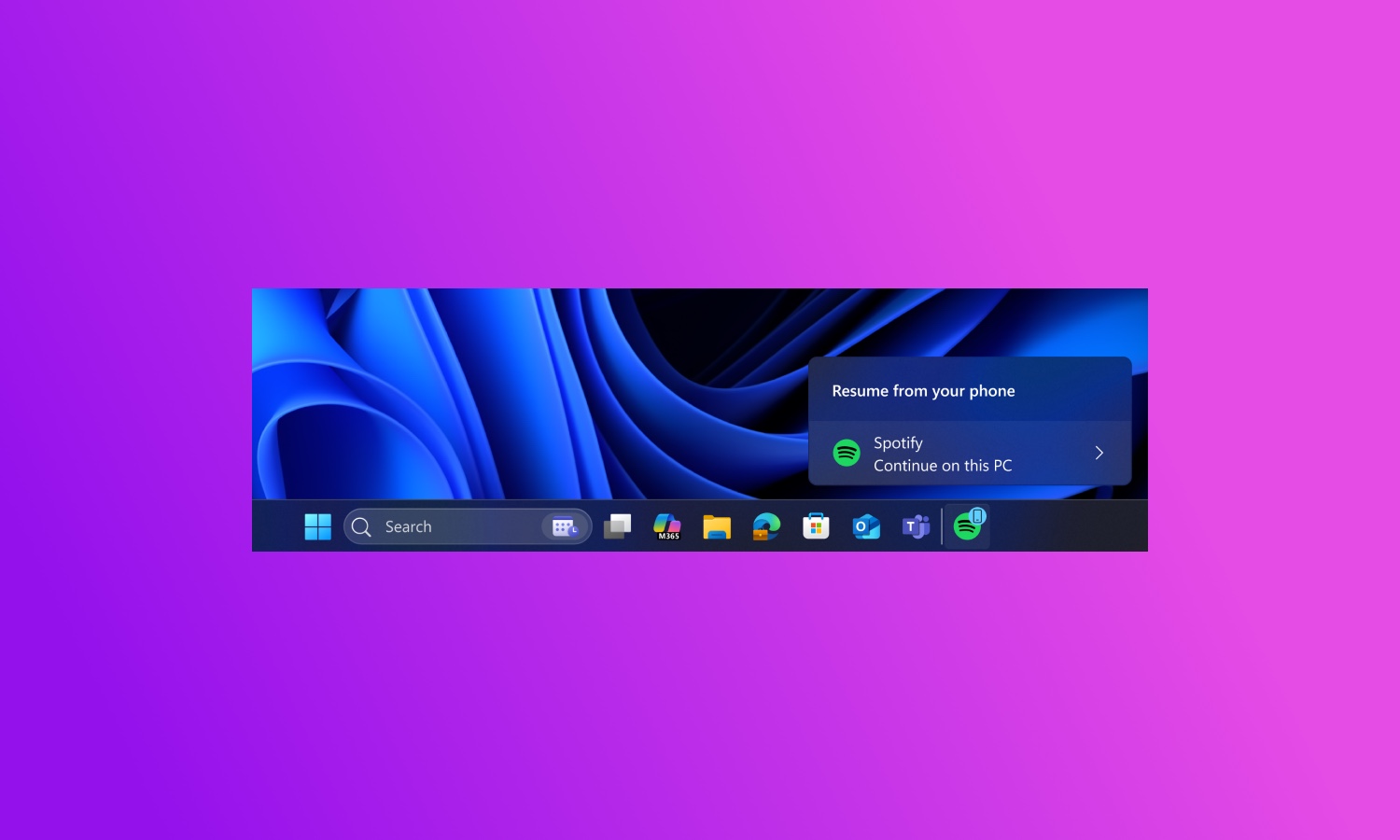
Microsoft adds ability to resume apps from Android phone on Windows 11
Microsoft has been slowly showing more and more love towards Android and its interoperability with Windows 11. This is something that is abundantly clear in the latest builds of Windows 11 released to Insiders on the Dev and Beta channels.
The latest feature to start rolling out is the ability to seamlessly resume apps from Android phones on PC. This is not something that works with all apps – indeed, it is not something you would want or need to work with all apps – but it is an interesting feature which has a lot of potential. For now, however, it is starting small.
Google Drive simplifies video editing
Google Drive is home to every type of file imaginable, and a decent proportion of those files are videos. It is with this in mind that Google has decided to make it easier to edit videos which have been uploaded to its cloud storage service.
Rather than adding video editing tools directly into Google Drive, the company is instead making it easier to access the option to do so using Google Vids.
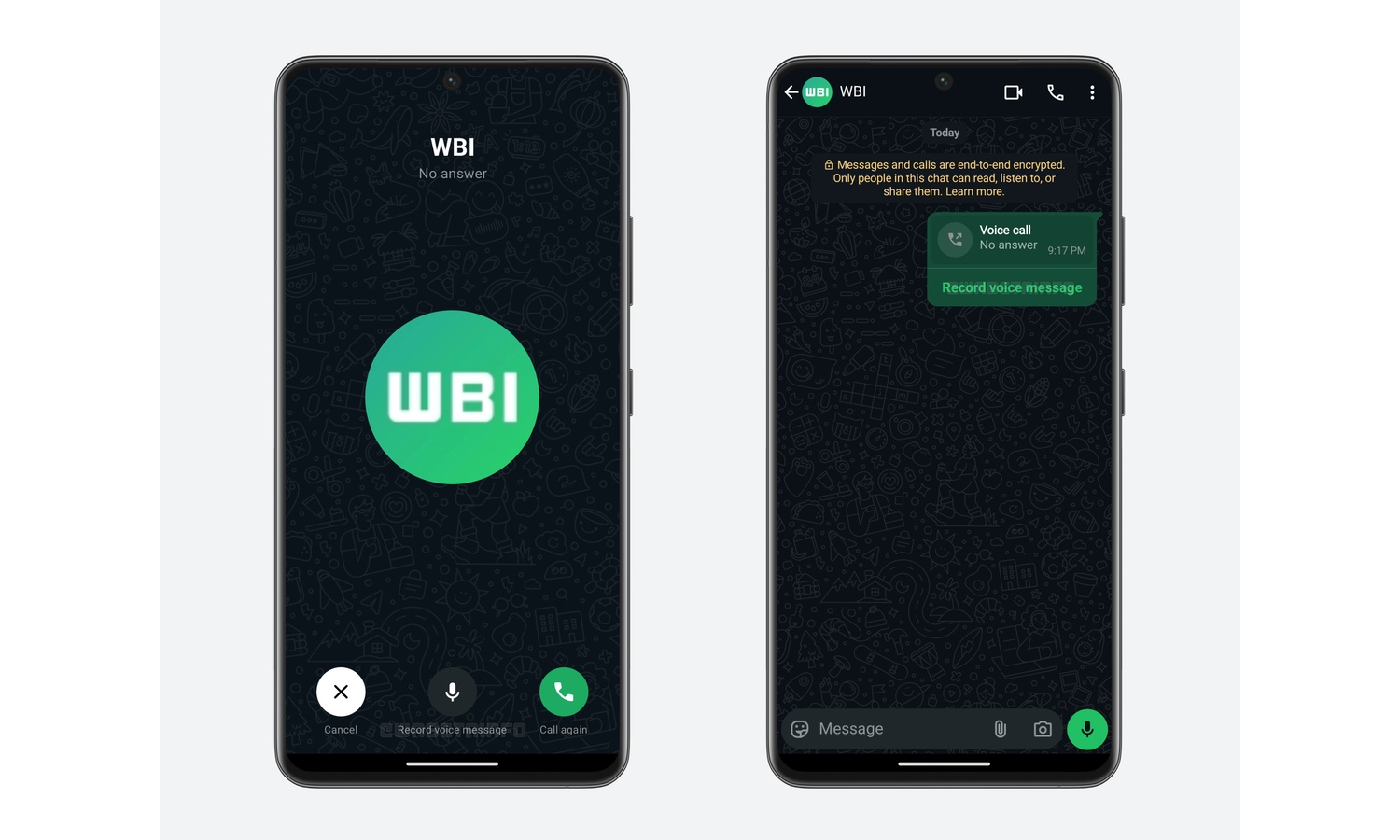
WhatsApp is testing an 'answerphone' for missed calls
WhatsApp would like you to leave a message after the beep. In what feels like a blast from the past, Meta is testing what equates to an answerphone service in WhatsApp.
Currently undergoing beta testing with a limited number of users, the feature seeks to encourage conversation and connectivity. You have almost certainly been notified of a missed WhatsApp call on your phone, but how many times has the person who called followed up with a text message? Probably not often, and this is something WhatsApps is looking to address.

US government to acquire nearly 10% stake in Intel as part of President Trump's plan to boost American chip manufacturing
Intel has confirmed widely reported plans that it intends to sell nearly 10 percent of its shares to the U.S. government under a new $8.9 billion agreement with the Trump administration aimed at expanding American semiconductor production.
The deal gives the American government a direct equity stake in the struggling iconic chipmaker, and comes as part of President Trump’s much publicized push to strengthen domestic manufacturing.

First release of Kodi 22 'Piers' is available to download NOW
It’s been a whopping seven months since The Kodi Foundation rolled out Kodi 21.2 ‘Omega’, coming five months after the previous release.
The last build came with a raft of changes and improvements and was designed to keep things ticking along while the team worked on the next version of its popular home theater software -- Kodi 22 'Piers'.

Rokid takes on Meta with new AI-powered smart glasses
Rokid will unveil its newest wearable, the Rokid Glasses, at a launch event in New York City on August 26. The company says the device is the world’s lightest full-function AI and AR smart glasses, combining translation, navigation, transcription, and a first-person camera in an everyday design.
The glasses run on Qualcomm’s AR1 platform and include features such as real-time multilingual translation, live transcription, a teleprompter function, and object recognition. Rokid is also building around a developer ecosystem that already counts more than 15,000 developers in China, with plans to expand internationally.

Belkin's new UltraCharge collection brings faster Qi2 wireless charging to Apple iPhone and Android
Belkin has announced a new line of wireless chargers that use the new Qi2 25W standard. The UltraCharge series includes three products designed for different use cases, all capable of charging devices faster and more efficiently than earlier Qi models.
Qi2 is the newest wireless charging standard created by the Wireless Power Consortium. It allows speeds of up to 25W, greater energy efficiency, and better compatibility across devices from multiple brands.

Chinese smartphone maker vivo takes aim at Apple and Meta with its first mixed reality headset
vivo has entered the mixed reality market with the launch of its first headset, the vivo Vision Discovery Edition. The headset enters a field dominated by Meta, Apple, and other global players, but is the first mixed reality device from a Chinese smartphone maker.
The device has been in development for four years and vivo says it is for “everyday use” rather than short demos or niche applications.
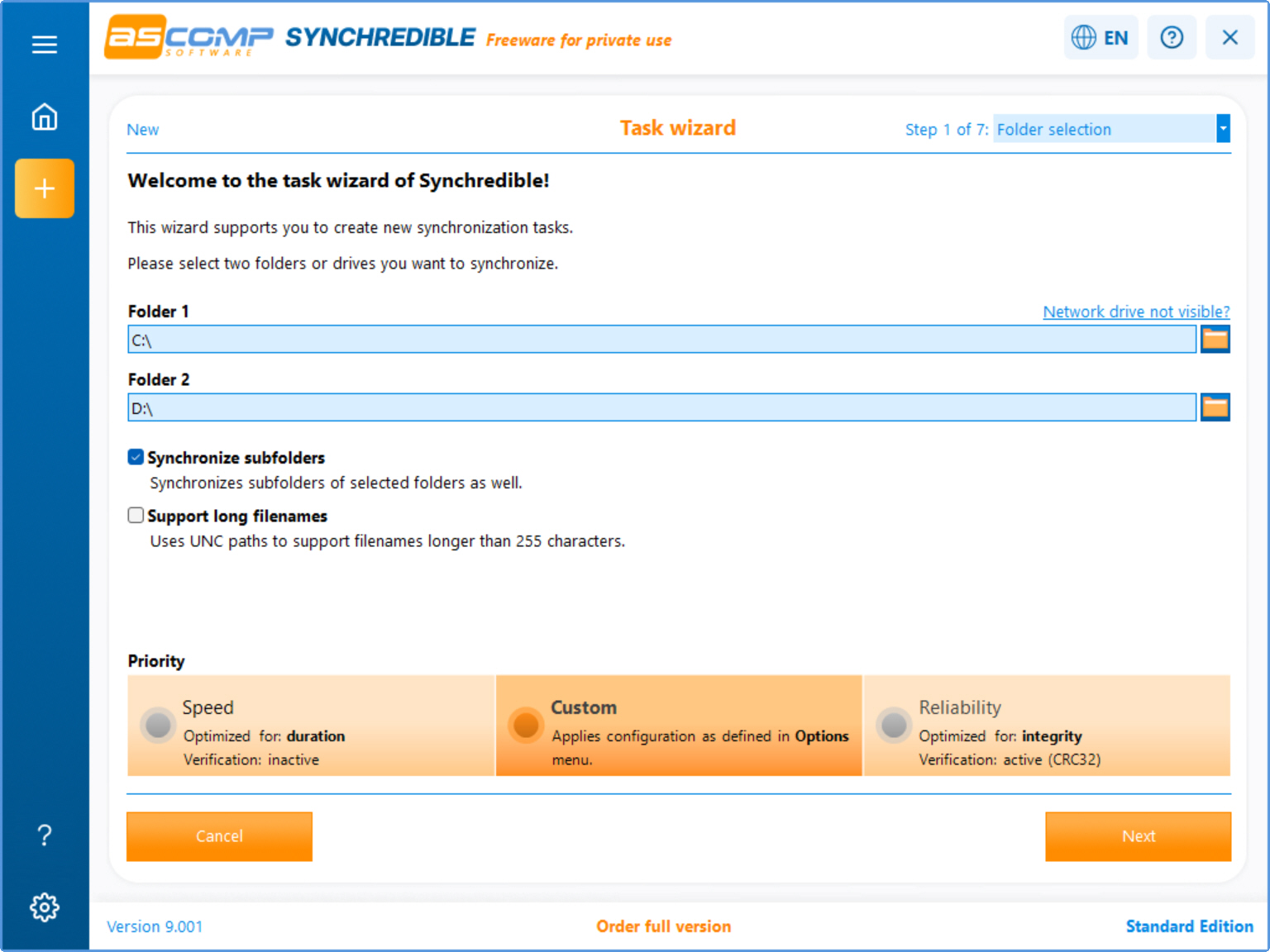
Free Windows backup and sync tool Synchredible 9 offers speed and design upgrades
Synchredible 9 is the latest version of the popular free Windows backup and synchronization tool that aims to make managing files and folders less of a chore.
The program has long been known for its flexible scheduling and detailed sync options, and this latest release brings a series of updates designed to improve speed, usability, and reliability.

Chatbots account for over 58 percent of all AI tool traffic
Over the year from August 2024 to July 2025 the top 10 AI chatbots collectively pulled in 55.88 billion visits, accounting for 58.8 percent of all AI tool traffic.
Within this group, ChatGPT is the undisputed leader, drawing 46.6 billion visits (up 106 percent year-on-year) and holding 48.36 percent of the entire AI tools market share.


