
With Chrome 80, Google is making website notifications STFU
When Mozilla released Firefox 72 yesterday, users were happy to find that the company had tamed the popup messages that ask whether a website should be allowed to send notifications. Now, with Chrome 80, Google has done the same.
Google notes that while the option to receive notifications from sites can be useful, they are "also a common complaint as many websites request the notification permission on first visit rather than at contextually relevant moments in the user's journey". But rejoice, for there is a solution!

Google's Project Zero is testing new vulnerability disclosure procedures
The vulnerability-finding Project Zero has found Google on the end of both criticism and praise, but there has long been concern about the policy of being very quick to reveal details of vulnerabilities that have been discovered.
Previously Project Zero has given software developers a 90-day window of opportunity to fix bugs before it goes public. Details of vulnerabilities would also be published as soon as a fix was released. For 2020, Google is trying something new. The company will wait a full 90 days before disclosing a vulnerability, regardless of when the bug is fixed.
TiKTok vulnerabilities could allow hackers access to personal data
Multiple vulnerabilities in the popular TikTok video-sharing app and its back end could have allowed attackers to manipulate content on user accounts, and even extract confidential personal information.
Researchers at Check Point have found that an attacker could send a spoofed SMS message to a user containing a malicious link. If the user clicked on the link, the attacker was able to access the user's TikTok account and manipulate its content by deleting videos, uploading unauthorized videos, and making private or 'hidden' videos public.

Satechi's AirPower-like Trio Wireless Charging Pad can simultaneously charge your iPhone, Apple Watch, and AirPods
Remember the Apple AirPower? If not, that is totally understandable. After all, the product never actually saw release. Please know, it was Apple's planned Qi wireless charging mat that could charge multiple devices at once. For whatever reason, the iPhone-maker canceled the product before it reached the public, saying it was not up to Apple's quality standards.
Impressively, popular accessory-maker Satechi has managed to do what Apple couldn't. You see, today, Satechi releases the Trio Wireless Charging Pad, which is capable of charging your iPhone, Apple Watch, and AirPods at the same time. This is with a single USB-C cable. Wow. Of course, since it uses the Qi wireless charging standard, it can charge non-Apple devices too, such as an Android phone.

Get 'Kali Linux -- An Ethical Hacker's Cookbook, 2nd Edition' ($44.99 value) FREE for a limited time
Many organizations have been affected by recent cyber events. At the current rate of hacking, it has become more important than ever to pentest your environment in order to ensure advanced-level security.
Kali Linux -- An Ethical Hacker's Cookbook from Packt Publishing is packed with practical recipes that will get you off to a strong start by introducing you to the installation and configuration of Kali Linux, which will help you to perform your tests.

Firefox 72 improves site notifications tool, rolls out picture-in-picture video to Mac and Linux
Mozilla has released Firefox 72.0 for desktop, along with Firefox for Android 68.4 and Firefox ESR 68.4.0.
Mac and Linux users gain the picture-in-picture video feature introduced for Windows in Firefox 71. Fingerprinting scripts are now blocked as standard with this new release, while intrusive pop-up notifications from websites have been confined to the Address Bar to prevent disruption when browsing.

Four surprising things we learned in 2019 about startups and sexual offenses
So far this century, one tech startup after another has reshaped the way that we live. Facebook transformed social interaction. Uber changed how we get around. Tinder changed how we date. While these companies have been highly forward-thinking, they have also persistently struggled to solve crucial challenges regarding background checks and user safety.
2019 brought many of these issues into the limelight. Here are four of the most surprising things we learned about startups and sexual offenses in 2019.

ARRIS unveils Wi-Fi 6 Tri-Band AX6600 Mesh SURFboard mAX System
Well, folks, with 2020, the Wi-Fi 6 (802.11ax) revolution is truly here. At this point, no one should be buying an 802.11ac router, After all, you can score a nice Wi-Fi 6 router for under $100. Of course, for many larger homes, a single router simply isn't enough. Instead, mesh systems are all the rage these days. If you aren't familiar, mesh is when two or more access points are used together for a single network. Basically, it should give you better Wi-Fi range without needing to mess around with extenders other other clunky add-ons.
Today, ARRIS unveils its latest mesh system, and it uses the aforementioned Wi-Fi 6. The AX6600 Mesh SURFboard mAX System is tri-band and features up to 5500 square feet of Wi-Fi coverage. It features a Quad-core ARM-A7 Cortex processor and has optional Amazon Alexa support. Each access point features two Gigabit Ethernet ports -- one wan and one wan/lan. This means the unit that connects to the modem will only be able to connect to one other hardwired device, but the second unit can connect to two.

Western Digital shows off 8TB SanDisk portable SSD and 1TB Ultra Dual Drive Luxe USB flash drive
When you think of portable storage, SanDisk is a name that likely comes to mind. The brand (now owned by Western Digital) has long been producing quality memory cards and flash drives. Personally, when choosing an SD card for my camera, I always go with SanDisk. Sure, there are less expensive options, but I know from experience, when it comes to storing important family photos, you should never go cheap. SanDisk cards offer great performance, but more importantly, they are extremely reliable.
And now, at CES 2020, Western Digital is, of course, highlighting products from its SanDisk brand. There are two new offerings that are very impressive. One is just a prototype (for now), but it is certainly the more exciting of the pair -- an 8TB portable USB 3.1 gen 2 SSD. That's big capacity from such a small drive. Even smaller, however, is the Ultra Dual Drive Luxe USB 3.1 Gen 1 flash drive. This drive comes in capacities ranging from 32GB to a massive 1TB. It offers dual connectivity -- USB-A and USB-C.
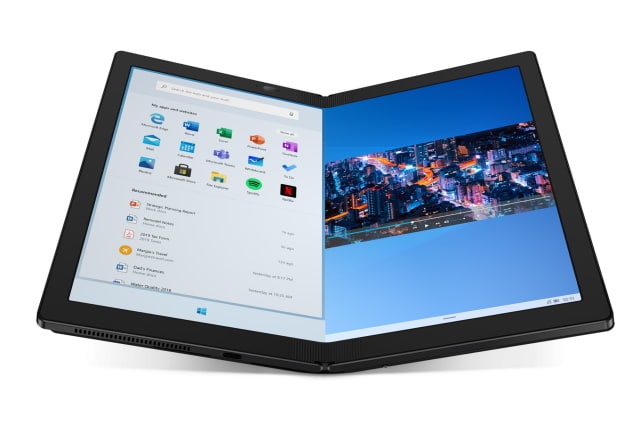
Lenovo's ThinkPad X1 Fold is 'the world's first foldable PC' with a hefty price tag
So far -- as Samsung will attest -- folding devices have been a bit of a disaster, but Lenovo thinks it has got things nailed with its ThinkPad X1 Fold which it officially revealed at CES.
Due for release in mid-2020, the "world's first foldable PC" features a 13.3-inch folded OLED and Lenovo says it delivers "laptop efficiency with smartphone portability". The device will initially ship with Windows 10, but a Windows 10X version will follow. A 5G version will also be available. Lenovo envisions its device being used in a variety of ways, but the only sticking point may be the price.
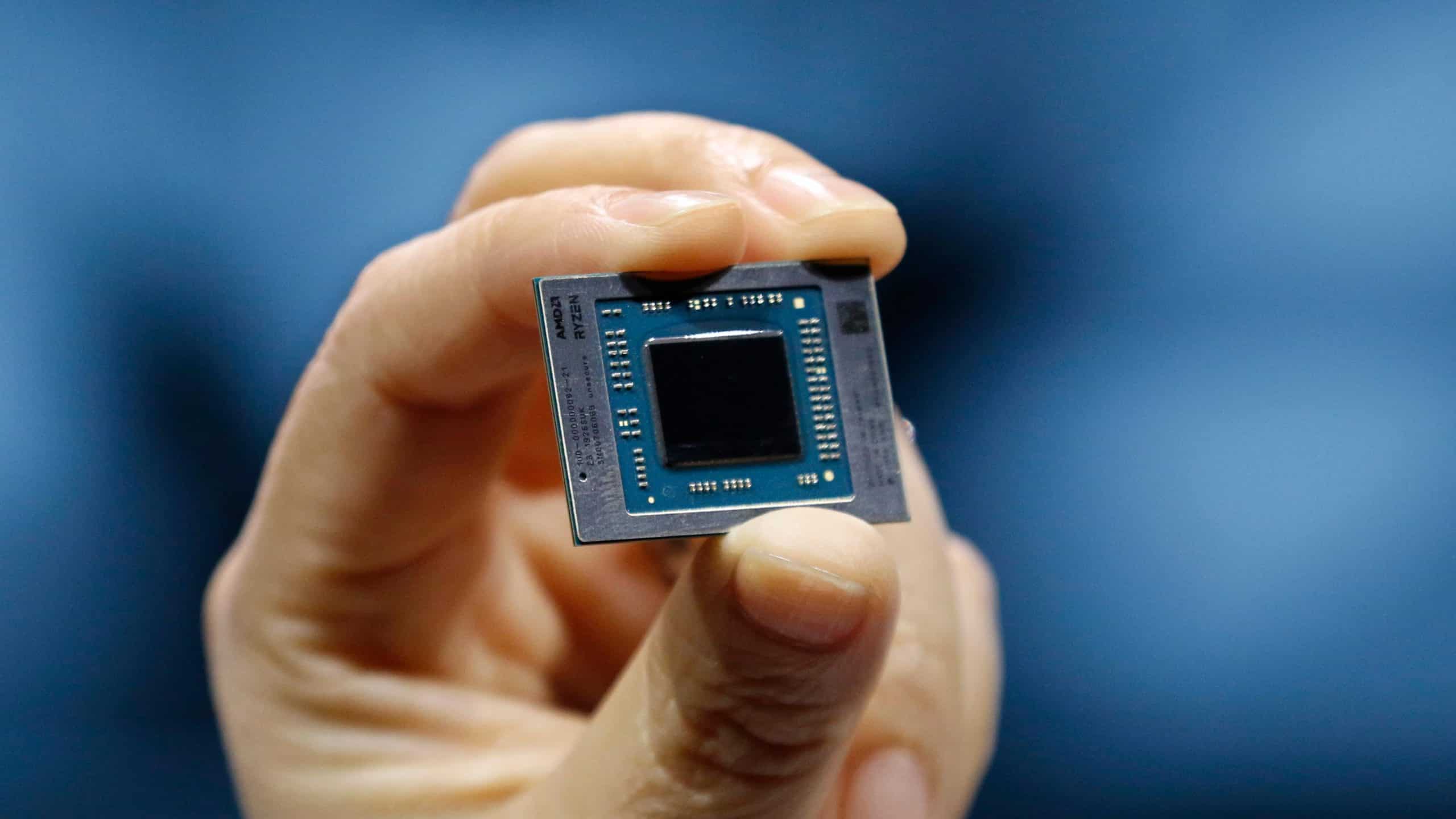
AMD unveils Ryzen 4000 Series mobile processors
AMD is most well known for its desktop processors, but the company does make mobile chips too. In fact, some of the best budget Windows 10 laptops are powered by AMD mobile processors. The company’s laptop chips are gaining more respect these days; case in point, Microsoft is finally selling an AMD-powered Surface.
Today, AMD unveils its latest mobile processors, and Intel should be very worried. These 4000 series chips should provide impressive multi-core performance. Road warriors in particular should appreciate the long battery life provided by the 15W variants. In addition to the new 4000 series processors, AMD is also announcing two new low-end Athlon 3000 chips for budget machines.

Samsung Galaxy Chromebook is the elegant and powerful Chrome OS laptop the world has been waiting for
Google's Chrome OS has revolutionized desktop computing by stripping away the nonsense and allowing the user to focus on the task at hand. There is no clunky update system like Windows, nor is there the need for anti-malware software. Chromebooks just work, and they are very secure too. Best of all, they are often super affordable -- unlike Apple's overpriced MacBooks. While many folks can get by with web apps, the operating system also runs both Android apps and traditional desktop programs. If you haven't tried a Chromebook in a while, you will be surprised by just how great they are these days.
Today, Samsung announces a new premium Chrome OS convertible laptop that oozes elegance. The Galaxy Chromebook, as it is called, is just 9.9mm thin and features an aluminum chassis in either Fiesta Red or Mercury Gray colors. It has a built-in active stylus, 4K AMOLED display, and is powered by an Intel Core processor. It can even be configured with up to 16GB of RAM! It has the latest-and-greatest Wi-Fi 6 for connectivity plus two USB-C ports too. It even has a fingerprint reader -- a rarity for Chrome OS devices.

Apple is poised to dominate the media landscape -- here's why
There have been a lot of "media moves" in the mobile world recently, including the launch of Facebook News, Samsung’s "rebrand" of Bixby Home to Samsung Daily and more that demonstrate the battle for consumer attention on mobile devices is quickly heating up.
But Apple’s moves in both hardware, software, and media put them far ahead in making frictionless, seamless, and integrated media experiences. Apple’s hardware and software (already in the hands of millions) extends from the watch and the phone to the tablet and TV enabling cross-device media integrations (e.g., recommendations, control, etc.) that will transform the media landscape. Additionally, Apple already owns or has partnerships with streaming video, news publishers, game makers, and more, giving them the power, scale, and reach to dominate media.

Tensions between the US and Iran expected to lead to a Bitcoin surge
When news broke that the Iranian general Qassem Suleimani had been killed in a drone strike ordered by Donald Trump, the value of Bitcoin jumped by 5 percent.
With tensions between Iran and the US now at an all-time high, the price surge is expected to continue. This is the belief of Nigel Green, the CEO and founder of deVere Group, one of the world’s largest independent financial services and advisory organizations, who says that the cryptocurrency is increasingly seen as being as safe as gold.

Implications for CEOs who miss security targets [Q&A]
Increasingly IT security is seen as an issue for the entire organization. This means it's often included in business targets, but setting these in a meaningful way -- and being able to meet them -- is a major challenge .
We spoke to Joseph Carson, Chief Security Scientist and Advisory CISO at Thycotic, to find out more about the difficulties of setting and measuring the success of targets for security.



