
Just one percent of NHS trusts have migrated to Windows 10
Last year, the UK’s National Health Service was hit hard by the WannaCry/WannaCrypt ransomware attack that went on to infect computers around the world. The attack was so bad that Microsoft took the unprecedented step of patching Windows XP to try and stem the spread of the problem.
While it first believed that NHS computers running XP were the source of the issue, it turned out to be Windows 7 systems that were mostly to blame. PCs running Windows 10 were immune from the attack. You would have thought, having been through such a terrible experience, that the NHS would have taken steps to prevent it happening again, but it seems not.

Microsoft is killing off SMBv1 in Windows 10 to thwart the likes of WannaCry
From the fall, Microsoft is disabling SMBv1 in Windows 10. With the release of Windows 10 Fall Creators Update (or Redstone 3 if you prefer), the protocol that was exploited by the WannaCry ransomware will be no more.
The file sharing protocol was developed by Microsoft over two decades ago, and the company recognizes that the time has come for it to be retired. Internal builds of Windows 10 being tested by Microsoft already have SMBv1 disabled, and similar builds will make their way to Windows Insiders and the wider public in due course.

Microsoft includes Windows XP and Vista in June's Patch Tuesday updates
Last month Microsoft made the decision to issue a "highly unusual" patch for Windows XP. Despite the fact the operating system has not been supported for some time, the patch was released in an attempt to thwart the WannaCrypt ransomware attacks.
Now, in an even more unusual move, Microsoft has chosen to include Windows XP in this month's Patch Tuesday. Windows Vista is also included in this batch of security updates which Microsoft says should address the "elevated risk of cyberattacks by government organizations."

Microsoft: 'No known ransomware works against Windows 10 S'
When WannaCry was running rampant on older versions of Windows -- Windows 7 being the most at risk -- Windows 10 was unaffected. According to Microsoft, "no Windows 10 customers were known to be compromised by the recent WannaCry (WannaCrypt) global cyberattack."
That’s great news for anyone running the latest version of the OS, and the software giant says it is working to ensure Windows 10 remains safe from other future attacks. However, if you want to guarantee your safety from ransomware, then Microsoft points out there’s an even more secure option to consider -- Windows 10 S.

It's Windows 7 -- not Windows XP -- that's to blame for the spread of WannaCry ransomware
It’s been a week since the WannaCrypt/WannaCry ransomware cyber attacks began, and the repercussions are still being felt. It became clear quite early on that the ransomware was hitting older Windows systems hard (Windows 10 wasn’t affected), with a lot of talk focusing on the number of at-risk Windows XP systems still in service.
But here’s the interesting thing. Most of the affected systems -- over 98 percent -- were actually running Windows 7.
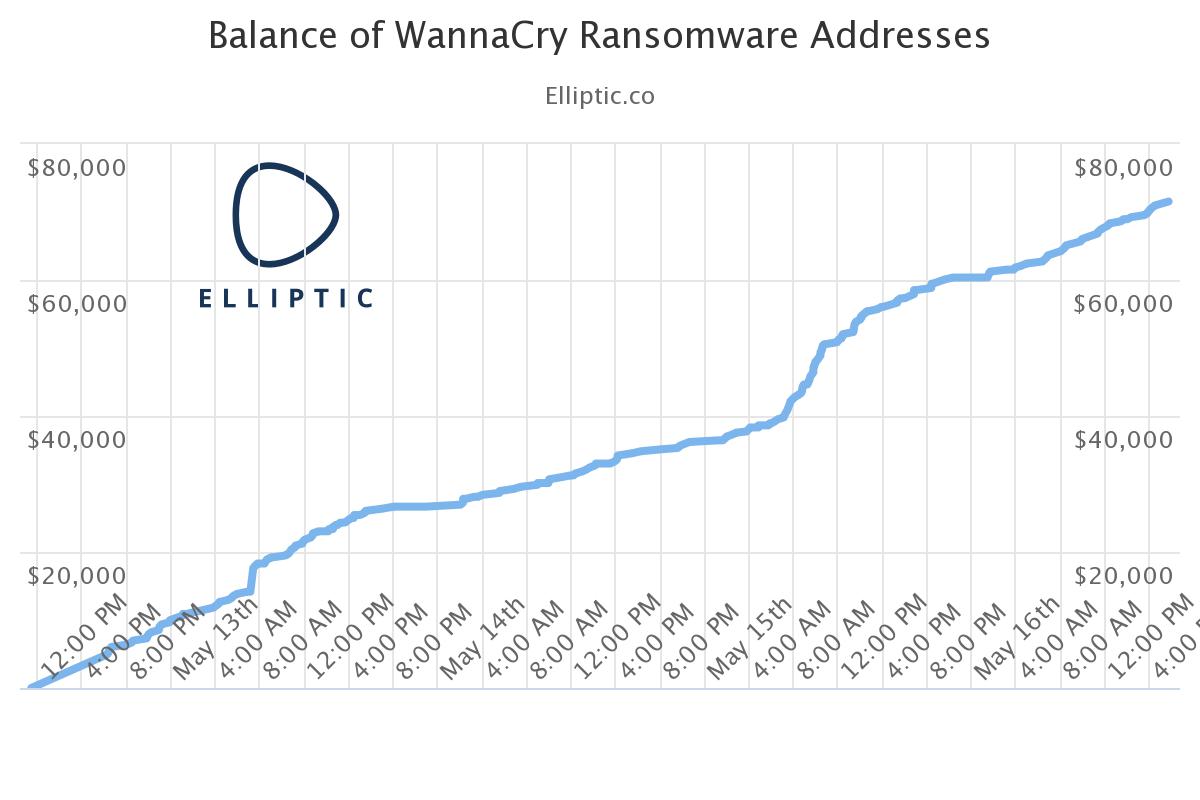
Watch how much money WannaCry generates in ransom -- in near real time
The WannaCry/WannaCrypt ransomware attack has hit businesses and individuals hard. It has now infected and locked over 300,000 computers across more than 150 countries.
It’s the most successful -- and damaging -- cyber attack in years, despite being rather poorly executed. If you’ve wondered how much money such an attack generates we have the answer -- and it’s not as much as you might think, given the scale.

Is WannaCry linked to the Lazarus Group?
As last Friday's WannaCry (WannaCrypt) ransomware attack continues to cause ripples around the globe, links have emerged between the malware code and the infamous Lazarus Group.
Lazarus is the group responsible for attacks on the Bangladesh Central Bank last year, Sony Pictures Entertainment in 2014, and more financial attacks in at least 18 countries.

Symantec successfully blocks more than 21 million 'WannaCrypt' ransomware attempts
The 'WannaCrypt' ransomware has been a worldwide dilemma, impacting many countries. Luckily, the malware only impacts older versions of Microsoft's operating system -- Windows 10 is not vulnerable. Also immune to WannaCrypt is macOS and Linux distributions. Unfortunately, many people run older versions of Windows, but Microsoft has been very active in issuing patches for them -- including for the now-unsupported XP.
Patches aside, security software can protect vulnerable computers too. In fact, today, Symantec announces that it has successfully blocked almost 22 million WannaCrypt attacks. The company even leveraged machine learning in its fight against the ransomware.

Vladimir Putin says the WannaCrypt cyber-attack is nothing to do with Russia
With Russia being blamed for having a hand in fixing both the US and French elections, Russian President Vladimir Putin must be feeling at least a little smug that the WannaCrypt ransomware currently wreaking havoc around the world has nothing to do with his country.
Asked about the threat while at an international summit in Beijing, Putin said it was "worrisome" but that the United States, not Russia, was to blame.

Microsoft should be applauded for its response to the WannaCrypt crisis
I’ve certainly been highly critical of Microsoft in the past, particularly last year when the company began forcing Windows 10 on to users.
But in the past couple of days I have to admit that I’ve been impressed by the software giant’s response to the global WannaCrypt/WannaCry crisis, and not just in patching Windows XP.

Microsoft blames US Government for 'WannaCrypt' ransomware disaster
The "WannaCrypt" ransomware has proven to be a disaster globally. This malware will encrypt a user's files and then demand some Bitcoin ransom to decrypt them. While the amount being demanded is relatively low at $300 or $600, the scam can be modified for even larger amounts. Heck, even after the ransom is paid, there is no guarantee that the bad guys will follow through with the decryption, making it quite the gamble. As the ransomware has disrupted government agencies, medical services, and other critical computers, the ransom is being paid by some, as it can literally be the the difference between life and death -- surgeries and other procedures have been delayed.
While there are many directions in which you can point the finger of blame, Microsoft should absolutely not shoulder any of the responsibility. After all, the vulnerability that led to the disaster was patched back in March. It never even affected the most recent version of the operating system, Windows 10. The company has even since patched the archaic Windows XP! So who is to blame? Users and administrators that failed to keep their systems up to date are partially at fault. The biggest blame belongs to an unlikely party -- the US Government! You see, an agency of our own government -- the NSA -- knew about the exploit, and rather than alert Microsoft, it chose to stockpile it for intelligence purposes. Sadly, the exploit itself got leaked, and as a result, it landed into the hands of evildoers.

Microsoft patches Windows XP to fight the WannaCrypt ransomware attacks
Microsoft stopped supporting Windows XP back in 2014, but today it releases one more security update for the ancient OS.
The software giant is taking this "highly unusual" step to fight back against the WannaCrypt ransomware cyber attacks that have so far hit nearly 100 countries around the world. And XP is not the only unsupported system receiving this patch.
