Punycode: The invisible cyber threat hiding in plain sight

The internet was conceived to connect the world, and internationalized domain names (IDNs) have certainly helped make that vision a reality. By allowing non-ASCII characters in web addresses, they’ve been pivotal in improving both accessibility and inclusivity.
As with any technological breakthrough, cybercriminals have found a way to turn innovation into exploitation. By using Punycode, a system for encoding IDNs, attackers have been able to create their own deceptive domains to mimic trusted brands and evade traditional security defenses to fool even the most wary users.
Microsoft is pushing a security update to Windows 11 that breaks File Explorer
The last round of security updates saw Microsoft release the KB5051987 update for Windows 11. As this patch addresses a number of security issues with the operating system, it is a mandatory update that will be automatically installed for most people.
As we’ve seen time and time again, the automatic installation of security updates is a good thing... until it isn’t. And with the KB5051987 update, there are numerous problems that raise the question of whether it is advisable to have Microsoft pushing out obligatory patches that can wreak havoc.
Why it's time to guarantee resilience in our critical software

Software has become central to our daily lives, with nearly every major company relying on it to operate. We are all increasingly dependent on fault free software for almost everything we do -- whether it’s ensuring trains run on time, accessing websites or using online banking.
Software has evolved into a form of digital public infrastructure, just as vital as physical infrastructure like roads and utilities. Yet, despite its critical role, software largely goes unmonitored and unregulated.
What startups can learn from special forces strategy

On the battlefield and in the trenches of entrepreneurship, victory comes to those who dare to think unconventionally and act with precision. As a former Green Beret, I've seen firsthand how the principles of unconventional warfare can translate into the business arena. Both demand team building, strategic thinking, and adaptability in dynamic environments.
Let's break down the seven-phase model of unconventional warfare and see how it can guide a startup from its inception to market dominance.
Unpatched software: The silent gateway to cyber attacks and how AI-driven solutions can close the gap

Modern enterprises are under fire from all angles. Attackers have become increasingly sophisticated and persistent in how they target enterprise data and systems. But as the threat landscape has evolved and become more complex, one tried and true method for malicious attackers stands out as a weak point for nearly every enterprise attack surface: outdated software. As much as patch management has advanced in recent years, the fact remains that most organizations struggle to deploy patches consistently and effectively, and that leaves systems exposed to cyber attacks.
Cybercriminals have become quite adept at exploiting unpatched software, using it as an easy entry point into enterprise networks. Malicious actors have developed an incredibly sophisticated understanding of where enterprise weak points are. In fact, most criminal operators have a deeper understanding of enterprise attack surfaces than the security teams tasked with defending them. Enterprise networks often consist of hundreds of thousands of IT assets, and every single unpatched instance represents an opportunity for attackers to compromise data and operations.
Microsoft is dropping the privacy protection VPN feature from Microsoft Defender really soon -- unless you pay up

Microsoft has very quietly announced that the VPN feature of its Microsoft Defender security tool is going away for anyone unwilling to part with money.
In a support document entitled “End of support-Privacy protection (VPN) in Microsoft Defender for individuals”, the company gives very short notice for the dropping of the free tool. When the end of February rolls around, the VPN feature will only be available to users paying for a Microsoft 365 Personal or Family subscription. What does all of this mean?
Google is making it easier to find a safe and reliable VPN
Take a browse through an app store and you will find that there is no shortage of VPN tools to choose from. But which can you trust?
One of the reasons for using a VPN in the first place is to help keep data safe -- but some tools leak information in ways that run completely counter to this. So how do you know which one you should be using? Google has come up with a new way to help guide users towards the safest options,
Google launches Identity Check, a new location-based security feature, and completes roll-out of AI-powered theft detection
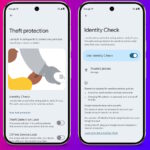
Theft of mobile devices is a crime that is not going away any time soon. Phones are now completely central to so many aspects of life, and the theft (or loss) is about much more than the monetary value of the device itself. There is great potential for a thief to gain access to a wealth of information via a stolen phone.
This is why the security of mobile devices is so important, and it is why Google is taking steps to limit the impact of theft. A new feature that is starting to roll out is Identity Check, which requires the use of biometric authentication whenever your device is in an unknown or untrusted location. The company is also harnessing the power of artificial intelligence for good, using AI-powered tools to detect thefts.
If you sign into your Microsoft account on a public or shared computer, you need to know this

Microsoft has quietly announced a significant change to the sign in/out process for Microsoft accounts. The change could have massive security implications for many people.
As of next month, when you sign into your Microsoft account, you will remain signed in until you opt to sign out manually. At the moment the (arguably more secure) approach sees users signed out automatically after a period of inactivity, helping to protect anyone using a public computer.
7-Zip users need to take action right now to address a serious security flaw

If you are a 7-Zip user, you need to be aware of a serious Mark-of-the-Web bypass vulnerability. The security hole is not new, having been reported way back in October 2024, but details have only just been released about it, and a fix has only just been produced.
Unlike many security fixes, however, 7-Zip users will need to be proactive in securing their software. Here’s what you need to know.
Microsoft’s latest Windows security fixes may not install alongside Citrix software -- but there is a workaround

The recently released security updates for Windows 10 and Windows 11 are proving problematic for some people. Microsoft has acknowledged issues with the KB5049981 and KB5050009 updates on systems with “certain Citrix components installed”.
With Windows 10 breathing its last, users will be keen to grab all available security updates before Microsoft abandons it later in the year, so it is good that while there is not yet a proper fix for the problem, a workaround is available.
Data privacy in 2025: The resurgence of biometric security, a fleeting forecast for federal data privacy regulations, and the return of the wild west of AI

The transition from 2024 to 2025 brings a lot of uncertainty, speculation, and hopefully some optimism for the world of data privacy.
As technology continued to innovate, securing data grew more complex and consumers grew more concerned over how their information was being used. Regulatory changes are coming soon, with several states providing their own data privacy standards in anticipation of a shifting focus within the U.S. federal government, creating an important inflection point to set the tone for the future of data privacy and security.
Microsoft confirms strange ‘some settings are managed by your administrator’ BitLocker error

If you’ve got BitLocker enabled on your computer and you’re seeing unexpected error messages, you can take some comfort in knowing that you are not alone -- and also that Microsoft is aware of the issue.
The problem affects some systems with TPMs (Trusted Platform Module), and it results in a message being displayed that reads: “For your security, some settings are managed by your administrator”.
Microsoft will forcibly install the new Outlook app on Windows 10 in February
While making much of the end of support for Windows 10, practically begging users to move on to Windows 11, Microsoft is sending out some confusing signals. The company has announced that the new Outlook for Windows will be forcibly installed on the aging operating system.
Somewhat unusually, the app will be pushed out as part of February’s security updates. This is likely to lead to mixed reactions; some people will be unhappy at having software installed against their will, while others will be pleased to get something new and more secure.
Apple defends Siri, saying the data it collects is never used for advertising, never sold, and never used for profiling

Having agreed to pay out $95 million to settle a lawsuit alleging Siri recorded private conversations without consent, Apple has doubled down on its assertion that it has done nothing wrong.
In a statement entitled “Our longstanding privacy commitment with Siri”, the company stresses it is committed to protecting user privacy. Referring specifically to Siri as “the most private digital assistant”, Apple insists that it “has never used Siri data to build marketing profiles, never made it available for advertising, and never sold it to anyone for any purpose”.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.