What you need to know about Hadoop

Unless you’ve been hiding away from the world of computing for the last few years, you’ll have come across Hadoop.
Apache Hadoop, to give it its full name, is an open source framework designed to handle the storage and processing of large amounts of data using low-cost commodity hardware. Since its initial release in 2011, it has become one of the most popular platforms for handling big data.
The new Google Play Music rolls out to Android, iOS and the web
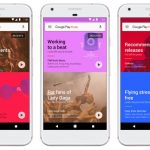
Starting today, Google is rolling out an updated version of Google Play Music, its streaming music service. The company says that the update sees the use of machine learning to create contextual playlists based on where listeners are and what they are doing.
The latest version of Google Play Music is more "assistive" than ever, with Google making much of the personalized playlists it is able to automatically create.
How to restart your graphics driver instantly with a key combination
Generate soothing ambient soundscapes with Halotea Free

If you like some background noise while working on your PC then it can be tempting to play music, stream video, maybe just turn on the TV. But that can be distracting, and you might not get as much work done as you’d hoped.
Halotea Free generates ambient soundscapes instead -- birdsong, rain, white noise -- which help you tune out distractions and concentrate on whatever you’re doing.
Hillary Clinton blames FBI email investigation for her election loss to Donald Trump

Donald Trump said in no uncertain terms that he believed the US election was rigged. If he had lost, he would have almost certainly contested the result, making claims of vote influencing, media bias and who knows what else.
But the reality is that Trump won, and this means that it is Hillary Clinton who is left pointing the finger of blame for losing. Unsurprisingly, it's the FBI that finds itself named as being responsible, with Clinton referring to letters from FBI director James Comey relating to the investigation into her use of a personal email server as the reason for her loss.
Mark Zuckerberg denies Facebook influenced the US election, and vows to tackle fake news

In the wake of the election of Donald Trump as Barack Obama's successor as president of America, Mark Zuckerberg has spoken out to deny claims that Facebook in any way influenced the result of the US election.
Criticism of Facebook has taken various forms. One of the key complaints is that its news algorithms serve to create an echo chamber, exaggerating the already-present confirmation bias effect. But there are also concerns that fake news is a serious problem on the platform.
New emoji revealed: breastfeeding, vomiting, and naked sauna users

The emoji lexicon is one that continues to grow month after month, year after year. Once little more than a collection of smiley faces and a few symbols, there are now emoji representing just about everything imaginable -- and they're even considered works of art.
At the moment, Unicode is considering which of a number of proposed new emoji should be added to the collection in 2017. Included in the list of proposals are a swearing face, a vomiting face, an exploding head, emo hair, a breastfeeding mother, a hajib wearer and a couple of naked sauna users.
Furious Kaspersky is 'disappointed and dismayed' with Microsoft

Claims of anti-competitive behavior are incredibly common in the world of tech; Google finds itself on the defensive on just about a weekly basis. Microsoft is certainly no stranger to accusations of anti-competitiveness, most notably for bundling Internet Explorer in older versions of Windows. But now it's Microsoft's approach to security that's in the firing line.
Eugene Kaspersky (yes, that one: the Russian security expert and CEO of Kaspersky Lab) has fired a vitriolic tirade at Microsoft in which he complains about how Windows Defender works in Windows 10. Windows 10 has been lambasted for many reasons since it launched, and things are not really improving as we near the launch of Windows 10 Creators Update. Kaspersky is so furious about the way in which Defender operates that he has written a lengthy and bitter blog post entitled: "That's It. I've Had Enough!"
Facebook's Mark Zuckerberg is dead... maybe you are too

A "terrible error" has been blamed for the accidental virtual killing of a number of Facebook users, including none other than Mark Zuckerberg. Thousands of users of the social network logged into their accounts to find out they were dead after Facebook experienced a strange bug.
The accounts of many people were memorialized as friends were invited to "remember and celebrate" the lives of the "deceased". The mistake led to Facebook users having to reassure friends and family that they were OK and remained alive and kicking.
Employees want flexibile hours more than a company car

It's been a while since remote working became a reality, but this latest survey into the matter showed that it is now becoming the norm. As a matter of fact, employees would rather have flexible hours and the possibility of mobile working than a company car, according to BT.
A total of 1,500 workers in the UK, Germany, France and Spain were polled for the report, and 67 percent confirm the claim regarding the car. For 76 percent, flexible working is one of the top three priorities in their company. But mobile working is far from perfect -- current technology sometimes makes it hard to get a hold of people, which delays crucial decisions. Also, sometimes it's hard to access documents and files.
Tech Deals: Get a Dell Inspiron 17 5000 17.3" laptop for just $609, plus fantastic bargains on Xbox One, PS4, and more

Black Friday and Cyber Monday are fast approaching, but you don’t have to wait for those big shopping days to pick up a bargain.
Courtesy of our partners at TechBargains, we have a selection of great deals to share with you right now, including a massive saving on a Dell Inspiron 17 5000 series laptop, a Dell PowerEdge T130 desktop, and a 55" Vizio M-Series 4K UltraHD LED Smart HDTV with HDR and a $250 Dell Gift Card. Plus we’ve great deals on games consoles, top games, and Amazon devices too.
Google updates its site verification process to flag 'repeat offenders'

Google has decided to rework the way it classifies dangerous and harmful sites in an effort to better protect users from being infected by malware.
The search engine has tried to protect its users for a number of years by displaying a warning when a link appears that could lead them to an unsafe site trying to infect their systems with malware or trying to obtain their personal information through phishing.
Why letting attackers inside your network is the smartest thing you can do [Q&A]

Organizations waste millions of dollars trying to keep hackers away from sensitive information using outdated perimeter-based security technologies. The result is obvious: it isn’t working.
Percipient Networks’ CTO Todd O’Boyle has counterintuitive advice for businesses when discussing what to do about hackers: let them in your corporate network. I spoke to Todd, and he explained why that advice is more sound that you might think.
Why choosing authorization over authentication will kill your enterprise

Today, the majority of enterprises rely on employee authorization by means of keycards or passcodes. While this form of security is convenient, these methods don’t truly authenticate nor verify the identity of the person at the time and place of an access request. We’ve all seen how usernames and passwords can be easily stolen. When this inevitably occurs within an organization, that factor becomes useless and will allow an attacker to gain access to everything the employee was authorized for.
Employee authorization based on a single paradigm is highly flawed because it could easily be lost, stolen or duplicated. If you are relying on only one vector for authentication, then there will only need to be one point of failure. Outside of the increased risk of becoming victimized by a data breach, enterprises that rely on these single paradigm authorizations are opening themselves up to the potential of fraud, lawsuits and damaged reputation and relationships with both internal and external stakeholders.
The five most common social engineering attacks

However much technology you throw at protecting your organization's systems the weakest link is still the person sitting in front of the endpoint.
No surprise then that social engineering is increasingly the attacker's weapon of choice for gaining access to sensitive systems. Security rating and risk monitoring company SecurityScorecard has put together an infographic showing the five most common attacks and their impact on enterprises.
Most Commented Stories
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.