HP announces new PCs made for Windows 10

We're only weeks away from the official launch of Windows 10, or, as some people may think of it, Microsoft's correction to the problems of its last operating system. That means OEMs are busy readying products to push to market for the big day, and HP is among them.
The company is announcing an entire portfolio of computers that are designed to run this new operating system, though not all will ship with it.
Young people are all for equality in games

If game designers opt for a male protagonist thinking it would make it easier to tap into the predominantly male gaming audience, then they’re in for a nasty surprise.
A recent study conducted by Time has shown that most boys don’t really care which gender the main character is, as well as that they’re aware that women are underrepresented in video games.
Microsoft Power BI exits Preview -- will be generally available on July 24th
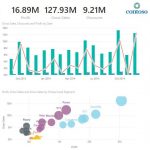
Data is the most important and valuable thing in the world. Diamonds and gold are just rocks in the ground by comparison. Want proof? Look at Google. Collecting information and storing data creates power and has huge value.
The problem with data, however, is that it only has value when it tells a story. In other words, you have to actually use the data you collect at some point. You can have giant SQL tables full of the secrets of the universe, but you need to be able to utilize and share it. Tableau is a popular visualization solution in the data analysis world, but it is clunky and confusing. Microsoft's solution, Power BI, looks much more promising and useful. Today, the company announces that it is exiting Preview and will be generally available on July 24th.
Leaked tool lets you download Windows Phone apps on a PC
Something that many Windows Phone users have been asking for is a little flexibility with how apps are downloaded and installed. One particular request is the ability to download apps using a PC rather than with a handset. A new tool leaked by a Microsoft employee makes this possible.
The appropriately-named Windows Phone Assistant is an official Microsoft tool that has been used internally. Nawzil released the software in response to a series of requests from people, granting greater control over apps. The leaked tool is available for anyone to download -- you just need to be running Windows Phone 8.1 GDR 2.
Hacking collectives target major firms for profit

Security researchers at Symantec have discovered that a number of well-known hacking collectives are actually highly trained independent groups targeting large corporations for financial gain.
The likes of Apple, Facebook and Twitter have all faced cyberattacks in the past and it is now thought that this is only viable if the information that is acquired is then sold or traded through some "financial market".
Twitter removes Vine ads that could trigger epileptic attacks

Twitter acted quickly to remove two Vines advertising the network's #DiscoverMusic campaign after warnings from an epilepsy charity. Epilepsy Action advised Twitter that the two ads could be dangerous to those suffering from photosensitive epilepsy.
The charity made a public appeal to Twitter in a tweet, and the company was fast to respond. Communications director Rachel Bremer thanked Epilepsy Action for drawing attention to the ads which were removed. The epilepsy charity was not alone in sending warnings to Twitter -- quite a few concerned tweeters got in touch with the company to point out the problem.
Create mobile-friendly websites with Mobirise

Mobirise is a free cross-platform WYSIWYG web designer which makes it easy to build mobile-friendly, Bootstrap 3-based websites.
The interface is stripped back, more like an app than a regular desktop program. There’s no complex menu system, no hidden right-click options, just a few buttons to click and panels to explore.
NSA releases network security tool -- will IT admins use it?

The NSA has released a network security tool that it claims is designed to help organizations "fortify their networks against cyber attacks". But, after being revealed to be spying on just about anyone it wants to, from US citizens to leaders of allied governments, while undermining major tech firms in the process, IT administrators will likely be very skeptical of adopting it.
Seemingly to put security concerns to rest, the security tool is made available through GitHub, making it easy for security researchers to analyze the code and find weaknesses -- of any kind -- that could put networks at risk.
App performance shapes consumer perception of retailers

A new survey reveals that shoppers are not forgiving of their favorite retailers or brands when their mobile apps aren't working as they should. According to the results 70 percent of consumers say the performance of a mobile app impacts their perception of the retailer.
The survey by application intelligence specialist AppDynamics spoke to 4,000 smartphone and tablet owners in the UK, US, France and Germany. It shows that 20 percent admit to making purchases on their phone while at work in front of their computer.
IBM research promises 50 percent improvement in processor performance

Moore's Law, the rule describing the steady growth of computing power, seems to have been under threat of late. But work by an alliance led by IBM research could see it safe for a few years yet.
Researchers have produced the first 7nm (nanometre -- one billionth of a meter) test chips. What does this mean? Current chips have components with a width of 14 or 20nm so a 7nm chip will allow many more components to be included.
Being proactive about security is the best defense against cyber attacks

Edinburgh council was the target of a cyberattack this week, and the details of more than 13,000 email addresses were stolen. The council was quick to issue a warning to all those who have an account with the authority, saying they might experience an increase in spam and phishing.
It said: "We are taking this incident very seriously. We have made sure that our service providers have reinforced the security of our website and we will continue to monitor security regularly".
AKVIS OilPaint turns ordinary pictures into works of art

Browse the "Effects" or "Filters" section of most image editors and you’ll often find tools which try to convert your pictures into sketches, oil paintings and more. But they’re usually basic, short on configuration options, and don’t deliver great results.
AKVIS OilPaint (and 64-bit) is a commercial tool for Windows and Mac which specializes in transforming your images into works of art. It’s expensive -- $49 to $89, depending on the license -- but the 10-day trial is full and unrestricted, so if you’re interested in the idea then there’s enough to justify the download.
HoloLens' field of vision isn't quite as impressive as you thought

Since Microsoft gave us a glimpse of its immersive HoloLens headset, there has been much pondering about just what to expect from the unit. Until we get an opportunity to go hands on with the new virtual reality cum augmented reality device, we're largely reliant on second hand information about what the experience of using HoloLens is like.
Microsoft has released new footage of HoloLens in action including an almost-first-person perspective that gives an idea of what it's like to wear. What's interesting to note is that, despite the promises of an immersive experience, the field of vision is rather smaller than many people will have expected.
How to protect yourself against ransomware

Regardless of whether you’ve been hit with ransomware or not, protecting your network from these types of attacks is now an integral part of any network security framework for both individuals and companies. Protecting yourself from intrusions and attacks requires securing your main layers of defense by utilizing Security Awareness Training and antivirus/anti-phishing software.
If you consider a computer network (even a simple one, like your home computer) to consist of a series of layers that any malware or virus needs to penetrate, the outermost layer would consist of your users themselves. After all, it takes a user’s interaction in order to initiate or allow a network intrusion. Only AFTER a user has clicked or visited a malicious link, will your secondary and tertiary layers (firewalls and antivirus) come into play. Thus, the very first layer you will need to harden is that of the human operator. It is only in recent years that the importance of this layer of security has come to be recognized. In the past, software has been relied upon as a catch-all for these types of situations. Software just by itself is not enough anymore, users must be trained to prevent such attacks from happening in the first place.
First look at iOS 9 and OS X 10.11 El Capitan public betas
Apple has released the first public betas of iOS 9 and OS X 10.11 El Capitan, allowing anyone with a compatible device -- iPhone and/or Mac -- to become a tester. Having signed up for the beta program last month, I immediately wanted to experience what is new in the upcoming versions of the two operating systems.
There is huge demand for the first public betas, proof being that Apple's servers were quickly overloaded during the first hours of availability. You can thank the media frenzy for this. Nonetheless, I have managed to install the iOS 9 and OS X 10.11 El Capitan public betas on my iPhone 6 Plus and 13-inch MacBook Air, respectively. And here are my first impressions.
Recent Headlines
Most Commented Stories
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.