
Why now is time to build sustainable accessibility into organizational culture
Accessibility is increasingly recognized as an important part of how organizations deliver value across a number of industries, and rightly so. It goes beyond meeting legal requirements to improve user experience, promote inclusion, and build better services for all. Yet, despite the growing awareness, some organizations still see integrating accessibility into its processes as an isolated effort or something to be 'checked off' near the end of a project, prompted by upcoming regulation, user complaints, or reputational risk.
This reactive approach may satisfy compliance needs in the short-term, but it does little to build lasting, meaningful inclusion. Meaningful progress happens when accessibility is embedded into an organization’s everyday mindset and operations. In short, accessibility must become a fundamental element, not an afterthought. Adding accessibility to everyday practices instead of reserving it for emergencies allows companies to develop better products, rely on stronger teams, and be more resilient.

Get your hands on the new Windows Share feature and try out Click To Do enhancements with the KB5058499 update for Windows 11
Microsoft has released a preview version of the KB5058499 update for Windows 11, adding a host of new features to the operating system -- many of them, predictably, AI-oriented.
The biggest additions are updates to Click To Do, as well as the rollout of the new Windows Share feature. There is also “Cross device resume” to allow for seamless device migration when using OneDrive files, and much more.

The launch of Windows Backup for Organizations sees Microsoft making it easier to move to Windows 11
The end of support for Windows 10 is fast approaching, as Microsoft is only too eager to keep reminding us. This is important for all users of Windows 10, but particularly for organizations that need to ensure security.
Microsoft has just launched Windows Backup for Organizations, and this can be seen as one of the ways in which the company is encouraging migration to Windows 11. It is an Entra-based way to backup and restore Windows settings, and it's now available in a limited public preview.

Less than eight percent of top domains implement the toughest DMARC protection
New research from EasyDMARC reveals that just 7.7 percent of the world's top 1.8 million email domains are fully protected against phishing and spoofing, having implemented the most stringent DMARC policy.
While this configuration, known as 'p=reject', actively blocks malicious emails from reaching inboxes, many businesses have only adopted the passive monitoring setting known as 'p=none', which passively monitors inboxes for threats without intercepting them. This means it doesn't block fraudulent emails or provide full visibility into authentication failures.

Microsoft super-charges Windows Update so it can keep all of your apps up to date
Microsoft has launched a preview version of the Windows Update orchestration platform. This is an update to Windows Update itself which opens it up for use by third-party developers.
This means that Windows Update could soon be able to update not only Windows, but also drivers, and third-party apps. So broad is the scope of what Microsoft is working on that it feels as though Windows Update will soon be a misnomer, and a rebranding may be in order.

Elon Musk quietly kills encrypted DMs on X and you should be furious
X, the social platform formerly known as Twitter, just yanked one of its most important privacy features. In a quiet and deeply troubling move, the company announced it is pausing end-to-end encrypted direct messages. Worst of all, there is no clear timeline or meaningful explanation.
According to a post from the official engineering account, encrypted DMs are being temporarily suspended while the team works on improvements. But here’s the kicker: users can still send and receive DMs, they just won’t be encrypted anymore. In other words, your messages are now visible to anyone at X with the right level of access. Hell, this potentially makes them more accessible to hackers too!

TUXEDO Stellaris 16 Gen7 is a Linux laptop with desktop power and optional water cooling
If you’ve been hunting for a laptop that offers hardcore power without ditching portability, the new Stellaris 16 Gen7 from TUXEDO Computers might be your dream machine. This thing is built like a tank, runs Linux out of the box, and somehow manages to blend high-end desktop performance into a notebook form factor.
At the center of it all is Intel’s Core Ultra 9 275HX processor. It has 24 cores and can hit 5.4GHz, which means it handles everything from gaming and compiling code to editing massive videos without flinching. Even better, it uses way less power than its predecessor. You can fine-tune how it behaves using TUXEDO’s own Control Center, letting you decide how loud or fast it should run depending on what you’re doing.

Confidence in software supply chain security at odds with actual readiness
New research finds that 32 percent of security professionals think they can deliver zero-vulnerability software despite rising threats and compliance regulations. 68 percent are more realistic, noting they feel uncertain about achieving this near-impossible outcome.
The study from Lineaje, carried out among RSA attendees, also shows that while software bill of material (SBOM) regulations and guidelines continue to increase, organizations vary in their level of adoption.

How safe are your browser extensions? New free database helps you find out
Not all browser extensions are created equal, and just because one is available in a high-profile store doesn't mean it's safe. Stores may do simple verifications to check for obvious red flags, but it's not part of their workflow to investigate deeper indicators of suspicious or malicious behavior.
ExtensionPedia, a new database developed by LayerX, changes that by providing individuals and businesses with detailed risk analyses on over 200,000 extensions to distinguish between safe, risky and malicious tools.

Apple brings Self Service Repair to iPad
Apple is now letting iPad users fix their own devices with official parts and tools, expanding its Self Service Repair program to include the iPad Air (M2 and newer), iPad Pro (M4), iPad mini (A17 Pro), and iPad (A16). Starting tomorrow, do-it-yourselfers can access the same components and instructions used at Apple Stores and authorized repair shops, including batteries, displays, cameras, and charging ports.
The move comes as right to repair legislation gains traction worldwide. Apple seems to be trying to stay ahead of government pressure while maintaining strict control over how its products are repaired. Still, giving consumers and independent shops broader access to genuine Apple parts marks a shift for a company long criticized for its tightly locked repair system.

New platform offers secure development for the AI era
According to recent projections from Gartner, by 2028 90 percent of enterprise software engineers will use AI code assistants, up from less than 14 percent in early 2024. But relying on AI in development roles also introduces risks.
Snyk is launching a new AI-native agentic platform specifically built to secure and govern software development in the AI Era.

The growing role of AI in healthcare: how devices are changing the game
Healthcare hinges on diagnostics, which is why doctors must accurately identify the illnesses they aim to treat to provide proper care for their patients. An incorrect diagnosis introduces the risk that treatment may be ineffective or harmful.
To diagnose properly, doctors rely on data by measuring key metrics and evaluating their implications based on experience, education, and best practices. The more data available to doctors, the more accurate their diagnoses can be.

Microsoft brings new features to older versions of Windows 11 with the KB5058502 update
It's the time of the month when Microsoft releases previews of next month's software updates, and for Windows 11 users there is the KB5058502 update preview.
Interestingly, this particular update is focused on older editions of Windows 11 -- specifically Windows 11 23H2, and the Enterprise and Education editions of Windows 11 22H2. And the update is significant; it brings not only bug fixes, but also a raft of new feature, including the almost inevitable selection of new Copilot-related bits and pieces.

The challenges and opportunities of generative AI [Q&A]
The promise of GenAI is undeniable, it offers transformative potential to streamline workflows, boost efficiencies, and deliver competitive advantage. Yet, for many organizations, the journey to implement AI is far from straightforward.
Obstacles typically fall into three categories: strategic, technological, and operational. We spoke with Dorian Selz, CEO and co-founder of Squirro, to explore these obstacles in more detail, as well as looking at some of the biggest misconceptions enterprises have when starting their GenAI journey.
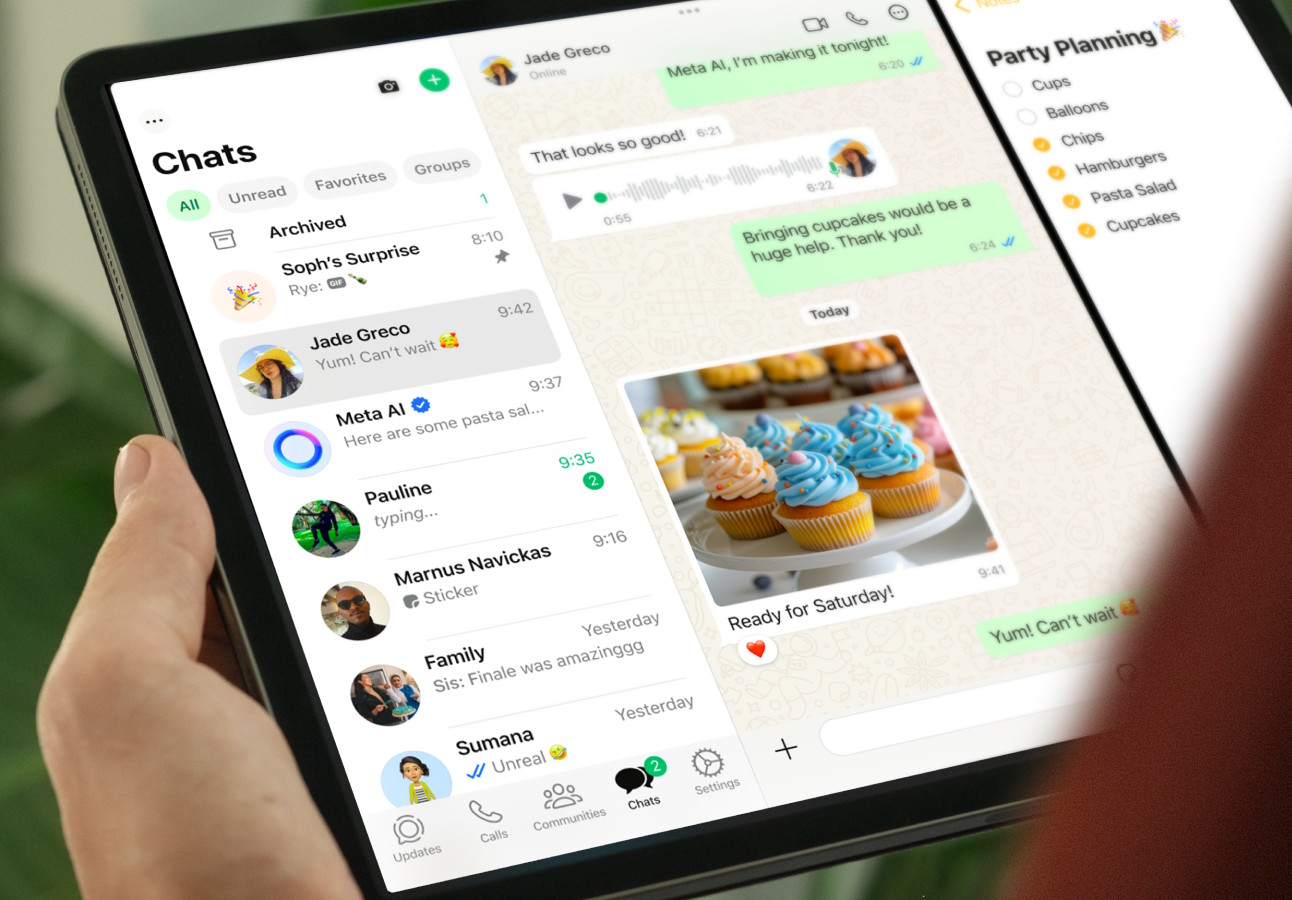
There is, at long, long last, a native WhatsApp app for iPad
Using WhatsApp on an iPad has long meant making a compromise or two. The reason is that there has simply not been a version of WhatsApp designed for Apple's tablet, forcing users to turn to WhatsApp Web in Safari.
After an incredibly long period of development, Meta has finally produced an iPad version of WhatsApp. So how does the iPadOS port of WhatsApp look?
