
The impact of open source on security [Q&A]
Open source software is commonly used to save time as it means developers don't end up repeating the same things over and over.
One of the key things about open source is that the source code is open to examination by everyone, In security terms this means it’s open to both the attackers and defenders.

60 percent of organizations expect to suffer attacks by email
Email is still a favorite attack route for cyber criminals a new study reveals, 77 percent of respondents say they have or are actively rolling out a cyber resilience strategy, yet an astounding 60 percent of respondents believe it is inevitable or likely they will suffer from an email-borne attack in the coming year.
Respondents to the Mimecast survey of more than 1,000 IT decision makers cite other worries as data loss (31 percent), a decrease in employee productivity (31 percent) and business downtime (29 percent) due to a lack of cyber resilience preparedness.

Executives believe their companies will benefit from 'continuous intelligence'
New data released today by Sumo Logic highlights increasing demand for a new category of software called 'continuous intelligence' among C-level executives.
Continuous intelligence allows organizations to more rapidly deliver reliable applications and digital services, protect against modern security threats, and consistently optimize their business processes in real time.

Vectra integrates threat detection with Microsoft security
Network threat detection and response company Vectra AI is announcing deep product integration with Microsoft Defender Advanced Threat Protection (ATP) and Microsoft Azure Sentinel to allow enterprises to better protect their networks.
Vectra has also been invited to become a member of The Microsoft Intelligent Security Association, an ecosystem of independent software vendors purpose-built to defend against increasing cyber threats.

Security priorities change as businesses adapt to 'new normal'
A new study from Check Point looks at how organizations have managed their cyber-security during the recent lockdowns and also their security priorities and concerns over the coming months as they move to the 'new normal.'
Over 86 percent of respondents say their biggest IT challenge during the pandemic was moving to mass remote working, and the biggest security concern (62 percent) was maintaining VPN capacity for staff.

Remote working and obsolete devices increase security risks
The move to cloud applications is leading many businesses to slow down investment in their in-house networks. This combined with a surge in home working is putting a strain on network security and infrastructures.
A new study from technology services company NTT Ltd finds 45.6 percent of organizations' network assets in Europe are aging or obsolete, as a weighted average, representing a huge surge on 2017, when this figure was just 12 percent.

You will soon be able to request Twitter verification
The coveted blue tick of verification is the goal of many Twitter users, and for a very long time the social media company has closed off the request system that existed.
Having used a secretive system to determine whether an account is deemed worthy of being verified or not, Twitter is now going to bring a "Request verification" option into its apps. The feature is currently undergoing development, but Twitter confirms that there is a new system in the works.

Kaspersky launches free online talks to spread cybersecurity knowledge
Kaspersky has announced that it's launching a series of online talks, created to present knowledge and the latest cybersecurity findings, freely accessible to anyone with an internet connection.
Titled 'GReAT Ideas. Powered by SAS' the events will be hosted by Kaspersky's Global Research and Analysis Team (GReAT), which works to uncover APTs, cyber-espionage campaigns, major malware, ransomware, and underground cybercriminal trends around the world.

Open source vulnerabilities doubled in 2019
Open source code allows developers to quickly integrate new capabilities into applications without having to reinvent the wheel, but it doesn't come without hazards.
A new report from RiskSense provides in-depth findings on vulnerabilities in leading open source software (OSS), including the most weaponized weaknesses, which software is most at risk, and the top types of attacks.
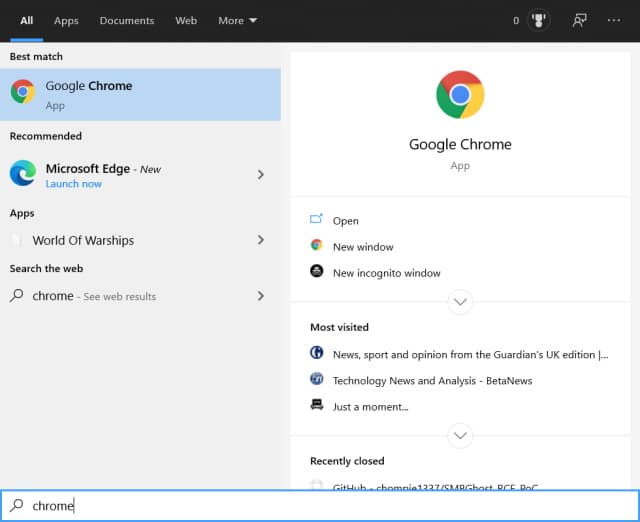
Microsoft is showing ads for Edge in the Windows 10 Start menu if you search for rival browsers
Microsoft is certainly no stranger to using Windows 10 to promote its own software; there have been numerous instances of the company advertising products within the operating system.
Now, if you use the Start menu to search for a web browser such as Firefox or Chrome, you'll see an ad recommending Microsoft Edge. While with previous in-Windows ads there have been simple steps you can take to avoid or disable them, this time around it seems there is nothing you can do about it.

Google CEO Sundar Pichai delivers ‘You Will Prevail’ commencement speech to the Class of 2020 on YouTube
Graduation ceremonies and associated commencement speeches are generally very boring. Graduating students and their families sit through them out of obligation, but for the most part, no one really wants to be there. This year, because of COVID-19, these ceremonies are largely canceled across the USA. Even though people are acting upset about that, they are probably secretly happy — you know it is true.
With planned commencement speeches being scratched, many people are instead delivering them online to a wider audience — anyone that is willing to watch and/or listen. Today, Google CEO Sundar Pichai delivers a virtual commencement speech to the Class of 2020 on YouTube.

Microsoft is now pushing out Chromium-based Edge to all Windows 10 users
It is a while since Microsoft adopted the Chromium engine for the new version of Edge, and reception to the browser has been broadly positive.
Until now, Microsoft has given Windows 10 users the choice between whether they what to use the new Chromium-based Edge, or stick with the old legacy version. But now that's changing. The company is pushing out the browser via Windows Update to Windows 10 versions 1803, 1809, 1903, 1909, and 2004 -- and it is not possible to keep using old Edge, however much you want to.

Apple has a new open source project to help improve password security
Apple has launched a new open source project designed to promote collaboration between the developers of password management software to help improve security for users.
The Password Manager Resources project has been created to make it easier for the developers of password managers to work together to ensure interoperability with websites, and to create a better experience for users. The aim is to integrate the strong password generating capabilities of the iCloud Keychain platform into password management apps.

How to free up disk space after installing Windows 10 May 2020 Update
With Windows 10 May 2020 Update now available, many people are rushing to install it. We already know that the update contains various bugs and problems, but even if you've had a problem-free installation, you may be surprised at just how much disk space you've lost.
This is particularly true for anyone with an SSD, which tend to be smaller, but there are steps you can take to claim back this space and free up several gigabytes. Here's what you need to know.

More tech companies issue statements about George Floyd's death and the continuing protests
Obviously, unless you've just returned from hiking the Appalachian Trail, you know the current events in the world. If you haven’t been absent from society then the news has been hard to avoid.
Now two more tech companies have added their voices to the incident in Minneapolis that involved four law enforcement officers and one citizen, George Floyd, and resulted in his death. Protests, some peaceful others violent, have broken out in cities across the US, including in small towns not accustomed to such events. They have even somewhat spread to other parts of the world, including London and Paris.
