
Linux Mint 19 named 'Tara'
Unfortunately, 2017 was not the much-fabled year of the Linux desktop. Hell, that might not ever happen. With Windows 10 being such a disappointment for many, however, it is definitely a possibility. Maybe 2018 will be the year...
One such desktop operating system that consistently delights users is Linux Mint. Today, we get some information about the upcoming version 19. The biggest news is that it will be called "Tara." If you aren’t aware, the operating system is always named after a woman.

2017: Year of the data breach
Barely a week seemed to go by in 2017 without news of a new data breach exposing customer or commercial data.
But just how bad was it? File transfer specialist Ipswitch has put together an infographic looking at the year in breaches.
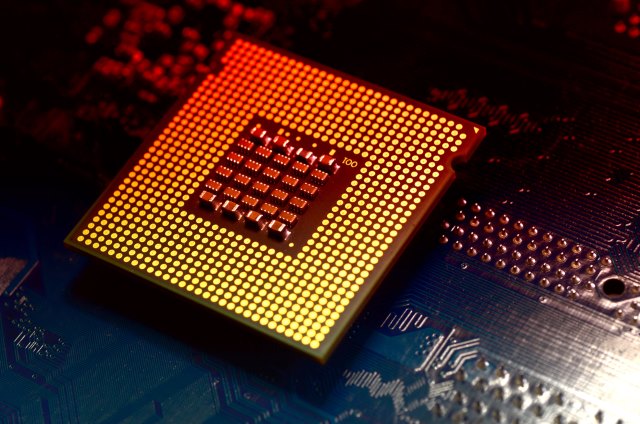
Intel chips have a huge security flaw, and the fix will slow down Windows and Linux machines
A design flaw has been discovered in Intel chips that will require major changes to be made to the Windows and Linux kernels. While patches are being worked on -- and in the case of Windows Insiders, have already rolled out -- users of both operating systems can expect to experience something of a performance hit. macOS machines running on Intel chips are also affected.
Intel is -- for the moment -- remaining tight-lipped about the specifics of the flaw that has been unearthed, but it is believed to affect processors produced in the past decade. Developers are currently estimating that systems could experience slow downs of between 5 and 30 percent.

Samsung CJ791 is world's first curved Thunderbolt 3 QLED display
Curved televisions are gimmicky and an overall bad idea. I bought a curved 4K TV a couple years ago, and while I do like it overall, it has a big negative -- it shows a lot of glare when the sun comes through the windows. Ultimately, the curved aspect doesn't seem to provide much (if any) value over a flat set when sitting on my couch.
Where curved displays are wonderful, however, is for computer monitors. When you are sitting closer to a display, such as at a desk, it provides a more immersive experience -- it is great. Today, Samsung unveils what it claims is the world's first curved Thunderbolt 3 QLED display. The 34-inch "CJ791," as it is called, features a 3440x1440 resolution, wide 21:9 aspect ratio, and four milliseconds response time.

Lindows rises from the grave! Freespire 3.0 and Linspire 7.0 Linux distros now available
About 16 years ago, a for-pay Linux distribution caused quite a stir all because of its name -- Lindows. Yes, someone actually thought kicking the billion dollar hornets nest that is Microsoft by playing off of the "Windows" name was a good idea. To be honest, from a marketing perspective, it was brilliant -- it got tons of free press. Microsoft eventually killed the Lindows name by use of money and the legal system, however. Ultimately, the Linux distro was renamed "Linspire." Comically, there was a Lindows Insiders program way before Windows Insiders!
After losing the Lindows name, the operating system largely fell out of the spotlight, and its 15 minutes of fame ended. After all, without the gimmicky name, it was hard to compete with free Linux distros. Not to mention, Richard Stallman famously denounced the OS for its non-free ways. The company eventually created a free version of its OS called Freespire, but by 2008, both projects were shut down by its then-owner, Xandros. Today, however, a new Linspire owner emerges -- PC/OpenSystems LLC. And yes, Lindows is rising from the grave -- as Freespire 3.0 and Linspire 7.0!

Hundreds of Android and iOS apps use your mic to check what TV shows you are watching
Advertisers are keen for their ads to be seen, that goes without saying. But it's more important to be seen by the right people, hence the explosion in targeted advertising. Social media is a great way to gather massive amounts of data about people and deliver ads accordingly, but some mobile games take things further.
There are a large number of games for both iOS and Android which include Alphonso software. This uses smartphones' microphones to record audio which is then used to determine which TV shows and commercials you're watching -- and then deliver targeted ads accordingly. Is this being done in secret? Not really. Details of the activities are included in Alphonso software's privacy policy.

Plextor launches M9Pe NVMe PCIe gaming SSD
It’s 2018, and there will likely be a lot of new hardware to excite and delight computer builders this year. In 2017, we saw solid state drives continue their climb in popularity -- a trend that will absolutely continue in the new year.
Today, Plextor launches a new solid state drive with a focus on gaming. The M9Pe series, as it is called, is an M.2 NVMe SSD drive that will be sold in capacities up to 1TB. It uses 64-layer 3D NAND Toshiba flash and the Marvell 88ss1093 controller.

OnePlus 5T receives Android 8.0 Oreo open beta
The OnePlus 5T is slated to receive Android Oreo early this year, but, until the update is deemed ready for prime time, users who want to sample the major changes can now give the first open beta a try.
The OxygenOS build targets more experienced users, as it's meant to be installed manually on the OnePlus 5T, and comes with a significant number of improvements for the launcher and system.

Steam: Windows 7 loses a large chunk of usage share, but is still well ahead of Windows 10
Depending on which analyst firm you believe, Windows 10 is either a whisker away from overtaking Windows 7 as the most popular desktop operating system, or still quite a distance off.
Steam’s monthly usage survey, which shows usage share from the gamers’ perspective, paints an entirely different picture however. It has consistently reported Windows 10 as the top operating system of choice, until recently, when Windows 7 roared into the top spot.

Privacy: Kodi's remote access could be used to spy on you
There's no denying the massive popularity of Kodi, and the streaming media center has become infamous as well as famous. While the negative press concerning the software tends to focus on the potential for piracy, there's also the question of privacy and security.
Kodi includes -- as does the likes of Plex -- a remote access feature. While wonderfully useful for when you're away from home, it also poses a security risk and represents a serious privacy concern if not correctly configured.
Samsung Galaxy Note8 handsets have a battery problem
Sound familiar? A Galaxy Note has a problem with its battery! Samsung has acknowledged that there is an issue with the battery of the Galaxy Note8 -- but unlike the Galaxy Note7, there's no risk of it catching fire or exploding this time around.
A number of Note8 owners have complained that their phones have essentially been bricked after they let the battery run flat. With the battery fully discharged, it has proved impossible to charge the phone again. The problem is mainly affecting Note8 owners in the US.

Ancient unpatched IOHIDeous vulnerability allows root access to macOS
Apple has a tendency to pride itself on security, but a researcher has released details of a macOS vulnerability that allows for complete system control by an unprivileged user.
A self-described "hobbyist hacker," Siguza, has published details of the exploit which is thought to have existed, undetected and unpatched for at least a decade. As well as details of the security flaw, Suguza has also published proof-of-concept code for the IOHIDeous vulnerability on GitHub.

StatCounter: Windows 10 STILL hasn't overtaken Windows 7
While NetMarketShare’s monthly usage share figures show there to still be a fairly significant gap between Windows 7 and Windows 10 (in the older OS’s favor), rival analyst firm StatCounter has long reported the battle for the top spot to be much, much tighter.
So close is the race in fact, that in October it looked as if Windows 10 would easily pass Windows 7 at some point in the following month. Surprisingly, that didn’t happen, although the gap did narrow. It seemed all but guaranteed that Windows 10 would claim pole position in December, but incredibly it didn’t.

NetMarketShare: Windows 10 still has quite some way to go to beat Windows 7's share
NetMarketShare reports on the state of the desktop operating system market on the first day of each month, and it has long shown Windows 10 to be lagging well behind Windows 7. However, tweaks to how the analyst firm records these numbers means the gap has closed recently.
The latest figures, for the final month of 2017, show Windows 10 growing and Windows 7 declining, but the difference in usage share hasn’t altered by much.

How to use Kodi to play classic video game ROMs -- Mario, Sonic, Zelda, and more!
As someone who was born in the 1980s, I experienced the golden age of video games. While the graphics were archaic by today's standards, the games were much more fun than the ones of today. People tend to forget that fun is the most important aspect of video games -- sound and graphics be damned. You bought a completed game and there were no updates, DLC or loot crates to be had. It was an amazing time.
Luckily, enjoying these classic games of yesteryear is very easy thanks to emulators. While the legality is a bit sketchy, you can download thousands of retro games (ROMs) and play them on your PC with near-flawless results. To make things even more convenient, the Kodi media center can now be used to play these ROMs. If you want to try this for yourself, I am happy to say you can do so immediately. The folks over at TVAddons have created a very useful guide.



