Microsoft releases Windows 11 update with revamped Start menu, printer fixes, and new Copilot button remapping

Microsoft has released the KB5044380 update for Windows 11, a preview version of the update that will roll out to everyone next Patch Tuesday. There is quite a lot to be found in this particular release including the previously announced ability to remap the Copilot key on a keyboard if you don’t like its default function.
As this is a preview update there are no security fixes, but problems with multi-function printers, Microsoft Teams, and high battery usage have all been addressed. There are numerous tweaks, fixes and additions that are available immediately to anyone installing the KB5044380 update, but there are also some that are subject to a more gradual rollout.
McAfee and Yahoo News partner to introduce AI-powered deepfake image detection

McAfee has announced a new partnership with Yahoo News, integrating its AI-powered deepfake image detection technology into the platform’s content quality system. This collaboration is designed to help Yahoo News quickly identify images that may have been created or modified using AI, with the goal of maintaining credibility and ensuring that content meets editorial standards.
McAfee’s deepfake image detection tool will flag AI-generated images, which are then reviewed by the Yahoo News editorial standards team. The integration provides a scalable and efficient method to detect manipulated content, offering additional resources to ensure that Yahoo News continues to deliver trusted journalism. This detection is currently being applied to content in the U.S. only.
Third-party JavaScript tags put security at risk

While businesses understand that third-party JavaScript tags collect information, only 13 percent are confident they understand what information they collect and only 26 percent are aware that tags can leak their private user data to other organizations.
A new report from the Jscrambler platform for client-side protection, with research conducted by Dimensional Research, shows 97 percent of respondents say they know that third-party tags collect sensitive or private information regularly.
Employees lack fundamental security awareness

Many executives are concerned about their employees' level of cyber risk awareness, with a new survey showing that 70 percent believe their employees lack critical cybersecurity knowledge, up from 56 percent in 2023.
The study, of 1,850 executives across 29 countries, from Fortinet also shows that over 60 percent of respondents expect more employees to fall victim to attacks in which cybercriminals use AI.
Majority of SaaS applications and AI tools are unmanaged

A new report reveals that 90 percent of SaaS applications and 91 percent of AI tools within enterprises remain unmanaged, suggesting a widespread vulnerability that continues to grow.
The study from Grip Security highlights the limitations of traditional security strategies in combating 'SaaS risk creep' the number of SaaS applications used in an enterprise increased by 40 percent over the last two years.
Save $35! Get 'Human Hacked: My Life and Lessons as the World's First Augmented Ethical Hacker' for FREE

Discover the future of cybersecurity through the eyes of the world's first augmented ethical hacker. In Human Hacked: My Life and Lessons as the World's First Augmented Ethical Hacker by Len Noe, a pioneering cyborg with ten microchips implanted in his body, you'll find a startlingly insightful take on the fusion of biology and technology. The author provides a groundbreaking discussion of bio-implants, cybersecurity threats, and defenses.
Human Hacked offers a comprehensive guide to understanding an existing threat that is virtually unknown. How to implement personal and enterprise cybersecurity measures in an age where technology transcends human limits and any person you meet might be augmented. The book provides:
The CEO's digital playbook for 2025 [Q&A]

As we head towards the end of the year, the pace of challenges posed by technologies like AI shows no signs of letting up.
So what should CEOs be doing to ensure that their workforces are equipped to deal with the changes and ensure that their business remains competitive? We spoke to Mike Lee, general manager at AND Digital, to find out.
How to thrive in the era of minimal data deletion

According to the latest global estimates, up to 400 million terabytes of data are created every single day. However, unlike the past, where users were happy to delete data once they felt it was no longer required, today’s data rarely gets deleted anymore, which is creating a growing number of issues.
It has become a cliché to say, “data is the new oil”, but its value has never been higher. Companies across all industries now collect as much as they can from every customer and process, so it can be mined for valuable insights and/or sold to generate new revenue streams. But to extract greater value from data, you need to keep it. To keep it, you need space, security, and money. Consequently, organizations are increasingly looking for the best ways to store their data without breaking the bank (or damaging the environment, if they can help it). The question is, what’s the best way to go about doing this?
Adding contacts to WhatsApp just got a whole lot easier
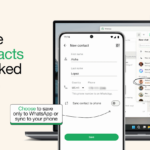
Managing WhatsApp contacts has proved to be a frustrating friction point for many users, and Meta has just announced that it is taking steps to simplify things.
As well as making it possible to add contacts via the web interface and Windows app, soon it will be possible to use linked devices -- not just your primary mobile -- to manage them. There are also new privacy controls including the option to create WhatsApp-only contacts to keep your main address book separate. And there is more on the horizon, with contact usernames being a particular highlight.
Belkin launches Connect USB-C 11-in-1 Pro GaN Dock with 150W power

Belkin has launched its new Connect USB-C 11-in-1 Pro GaN Dock. This compact docking station offers up to 150W of power, utilizing Gallium Nitride (GaN) technology to create a compact, efficient device.
The 11-in-1 dock includes a variety of ports, such as USB-A, USB-C, HDMI, Gigabit Ethernet, SD and MicroSD slots, and a 3.5mm audio jack. It supports up to three external displays, offering resolutions up to 4K at 60Hz, and can handle fast data transfers with speeds of up to 10Gbps.
Microsoft upgrades Xbox Wireless Headset with Dolby Atmos and better battery life

Microsoft has updated its Xbox Wireless Headset, bringing some nice enhancements for gamers looking to upgrade their audio experience. One of the most biggest changes is the addition of Dolby Atmos, a feature that aims to provide immersive, spatial audio for more precise sound in gaming environments. The updated headset also features improved battery life, now offering up to 20 hours of playtime, as well as Bluetooth 5.3 for better connectivity across devices.
The new model comes with support for Dolby Atmos, Windows Sonic, and DTS Headphone:X, offering a variety of spatial audio options. Microsoft says that this technology allows for clearer sound separation, making it easier to hear key details in games, whether it’s enemy footsteps or subtle environmental sounds.
Cloud attacks grow in cost and scale

A new report from Sysdig highlights the growing cost and scale of cloud attacks and the evolution of tactics being used by attackers.
Among the findings are that over $100,000 is lost per day to AI resource jacking. It hasn't taken long for threat actors to leverage stolen cloud access to exploit large language models (LLMs), as illustrated by an LLMjacking attack that left one victim on the hook for $30,000 in just three hours. Left unchecked, an LLMjacking operation can cost more than $100,000 per day.
TRIBIT launches StormBox Blast 2 Bluetooth speaker with 200W output

TRIBIT has unveiled its updated portable Bluetooth speaker, the StormBox Blast 2, featuring enhanced performance and new capabilities. This latest model offers a 200W output, an improved IP67 waterproof rating, and Bluetooth 5.4 connectivity. The speaker includes an 80W subwoofer, dual 45W mid-range drivers, and two 15W tweeters to deliver a full sound experience.
The StormBox Blast 2 also includes dynamic lighting that syncs to the music or can be customized through the TRIBIT app, providing a visual element to complement audio playback. This feature is designed for various settings such as parties or outdoor gatherings.
Google shows its commitment to Secure by Design

In an ever more interconnected world facing growing numbers of cyberattacks, it's critical to ensure that technology systems are resilient in order to keep people safe.
Google has announced that it's signed up to the CISA's Secure by Design pledge, a voluntary commitment to specific security goals.
Plugable introduces PS-10CC 10-port USB-C charger with intelligent power management

Plugable has announced its latest product, the PS-10CC, a 10-port USB-C charger featuring intelligent power allocation and priority-based charging. The new device is designed to address common charging issues such as limited outlets, cable clutter, and slow charging speeds, making it suitable for households, small businesses, and educational environments.
The PS-10CC uses real-time current sensing technology to distribute power across all 10 ports efficiently. By adjusting power output based on each connected device’s requirements, the charger can prioritize high-demand devices, such as laptops and smartphones, while ensuring other devices receive power as needed. Users can organize their devices based on importance, with the leftmost ports receiving power first.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.




