
Home tech gifts: Which products are topping consumer wish lists?
Our ongoing obsession with electronics shows no sign of cooling off, but consumers are showing an increased interest in connected devices, according to CES trends, market research from Parks Associates, and Amazon Wish List rankings. While gaming and mobile devices continue to be favorite gift items, many consumers are just beginning to embrace the idea of a smart home. As they do, smart and connected products are seeing a rise in popularity. Some consumers shop independently for smart products, while others seek to purchase easy-bundled solutions from home security companies and ISPs.
As consumers are creating wish lists for housewarming presents, wedding gifts, and holiday surprises, here are some items that are emerging as trends this season.

A guide for mastering endpoint management
Unified Endpoint Management (UEM) has emerged over the last couple of years as a new approach to help IT teams better manage a growing number of devices in an increasingly distributed work environment, by uniting traditional endpoint management and mobile device management (MDM). Yet successfully integrating the two commonly disparate approaches is easier said than done. In fact, many teams find themselves overwhelmed by the thought of figuring out where to even begin marrying both approaches, resulting in continued separate workflows and lingering inefficiencies.
For the modern enterprise looking to maintain both its security posture and digital relevancy, however, the impact of resisting UEM extends well beyond a missed opportunity for IT workflow optimization. By not deploying an effective UEM strategy, an organization is missing a critical step to comprehensively and uniformly securing its entire IT environment -- which includes an ever-growing web of network connected devices, including desktop computers, laptops, smartphones and tablets, as well as printers, projectors, BYOD devices, gateways and Internet of Things devices -- all of which are essential to employees’ daily work and, ultimately, business continuity and growth. For organizations looking to unite endpoint management and MDM workflows to optimize efficiency, security and digital enablement UEM has to offer, here are some key tips to keep in mind.

9th anniversary of Bitcoin: Is the war between cryptocurrencies and governments over?
The global real estate market is worth $217 trillion, and one-third of income-generating real estate transactions are cross-border. But cross-border real estate transactions are notoriously complicated and rife with delays and impediments inherent to antiquated property rights registrations systems. However, an American’s purchase of $60,000 apartment in Kiev may change everything.
In September, TechCrunch founder Michael Arrington remotely purchased a $60,000 apartment in Kiev in a deal that will change real estate forever.

Ethereum wallet vulnerability freezes hundreds of millions of dollars
Ethereum is a hugely promising blockchain technology which has really taken off this year, thanks in no small part to the backing of major companies like Microsoft, Intel and Cisco. It is also super valuable as a cryptocurrency, being worth around $28 billion, and a great platform for ICOs (Initial Coin Offerings).
So, many startups are now turning to Ethereum to raise money, and the way that they are doing it is through smart contracts. Only problem is, they are not bullet-proof, as a newly-uncovered vulnerability in a popular wallet puts hundreds of millions of dollars at risk.

Amazon makes Fire TV Stick available in over 100 countries
Not long after releasing the original Amazon Fire TV as a small set-top box, Amazon shrunk its player down into stick form. It's a small dongle that plugs directly into an HDMI port on your TV or monitor, or even an HDMI switch if you'd like to easily move between sources.
Now the retail giant is opening up the market for the Fire TV Stick to people around the globe, bringing entertainment to everyone.
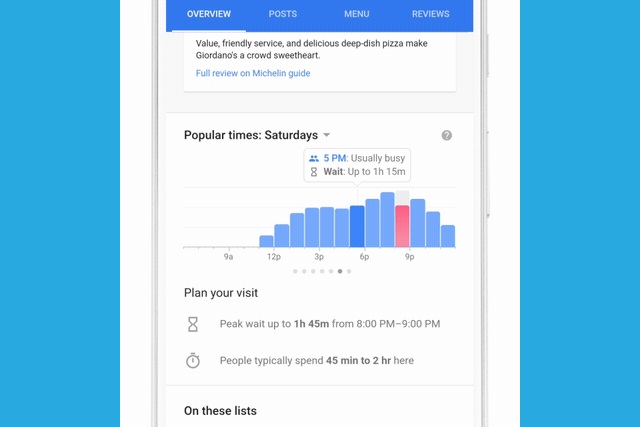
Google adds restaurant wait times to Search and Maps
Search for a restaurant using Google, and you're already told the times of day at which a particular place is busiest. But Google is about to make this information even more useful.
The fact that a restaurant is busy at 3PM on a Thursday afternoon doesn't necessarily mean you'll have to wait ages for service -- there may be more staff working, for instance. A new update to Google Search -- and Maps is to follow -- means you'll be able to see estimated wait times as well.

Public cloud and SaaS monitoring added to security operations platform
The use of SaaS applications and cloud infrastructure is becoming more widespread, but robust cyber security operations policies are often lacking for these environments.
The proliferation of these services has blurred the traditional security perimeter of the enterprise, creating a growing need to unify the security and operational policies of on-premises, SaaS and public cloud infrastructure to ensure visibility into systems and data.

Twitter blames a failure to take context into account for its block on LGBTQ searches
Over the weekend, users noticed that a number of search terms -- such as bisexual -- appeared to be blocked on Twitter. Having said "we've identified an error with search results for certain terms. We apologize for this. We’re working quickly to resolve & will update soon," Twitter has finally explained what happened.
Perhaps predictably there's -- assuming you believe Twitter -- nothing sinister going on. Instead, the company's latest policy changes, which took extra measures to block sexual content, meant that its automated systems were being rather heavy-handed in censoring certain content, completely failing to take context into consideration.

One in five security professionals still uses paper to manage privileged passwords
A new study from identity management company One Identity reveals a worrying level of mismanagement of privileged accounts.
The survey of over 900 IT security professionals carried out by Dimensional Research finds 18 percent of respondents admit to using paper-based logs, and 36 percent are using equally inadequate spreadsheets for tracking privileged accounts.

Threat intelligence platform adds analyst assessments to machine learning
Companies are increasingly turning to AI and machine learning solutions to combat cyber threats, but sometimes there is no substitute for the insight that comes with human analysis.
Threat intelligence specialist Recorded Future recognizes this and is expanding its platform to give security operations centers access to analyst-originated intelligence to offer relevant expert insights and analysis needed for operational improvements and targeted risk reduction.

The iPhone X has the best display of any smartphone
DisplayMate -- the display calibration and benchmarking firm -- has put the iPhone X through its paces and has come to the conclusion that it has the best smartphone display ever. This is an accolade that DisplayMate handed to the Samsung Galaxy S8 back in April, and with the iPhone X display having been supplied by Samsung, the new award is perhaps not a surprise.
While there have been some minor concerns about Apple's switch to an OLED panel, the move has definitely paid off. Apple is praised for the careful calibration it has put into the iPhone X's screen, causing DisplayMate to say: "the iPhone X is the most innovative and high performance smartphone display that we have ever tested."

New partner program lets service providers offer erasure as a service
One of the areas that can often be overlooked when companies are formulating data protection strategies is what happens to information at the end of its life.
It's important to dispose of unneeded information securely and data erasure specialist Blancco Technology Group is offering a new erasure as a service (EaaS) process. It's making this available through a partner program so that managed service providers can integrate it into their IT service offerings.

EFF: Twitter users have a First Amendment right not to be blocked by President Trump
The Electronic Frontier Foundation has told a court that Donald Trump's blocking of users who criticize him on Twitter is a violation of their First Amendment rights. The digital rights group says that people have a "constitutional right to receive government messages transmitted through social media and participate in the forums created by them."
The EFF argues that Trump's use of Twitter has become a hallmark of his presidency, and by blocking individuals he is denying them access to the policy details and other information he frequently disseminates through tweets.

Xbox One X celebration giveaway -- win a Microsoft console and free video game!
Today is Xbox One X release day, and we here at BetaNews are very excited. Microsoft has created the most powerful video game console of all time. Besides playing 4K video -- including UHD Blu-ray -- it can handle 4K gaming too. Yes, folks, you will finally be able to leverage that new 4K TV for incredible graphic detail.
To celebrate the Xbox One X release, we are giving away an Xbox One console. In fact, it is the exact console as seen in the video here. While it is "only" an original Xbox One, it is actually a fairly rare white variant. Despite not being the latest and greatest, it will be able to play all Xbox One games, albeit at a max of 1080p. It can also play Blu-ray and DVD discs. Wow!

Paradise Papers: details of Apple's tax arrangements revealed in leaked documents
The Paradise Papers -- a massive cache of documents leaked to newspapers and journalists -- reveal the tax avoidance strategies used by millionaires, billionaires and businesses around the world. The leaks comprise over 13 million documents, and it shows the financial structure and offshore accounts for many big-name companies.
Included in the list is Apple -- a company already known to have taken advantage of the "double Irish" tax loophole in Ireland to massively reduce its tax bill. The Paradise Papers show that Apple made use of another tax haven after it faced criticism for its exploitation of Irish taxes and a clampdown on the loophole.



