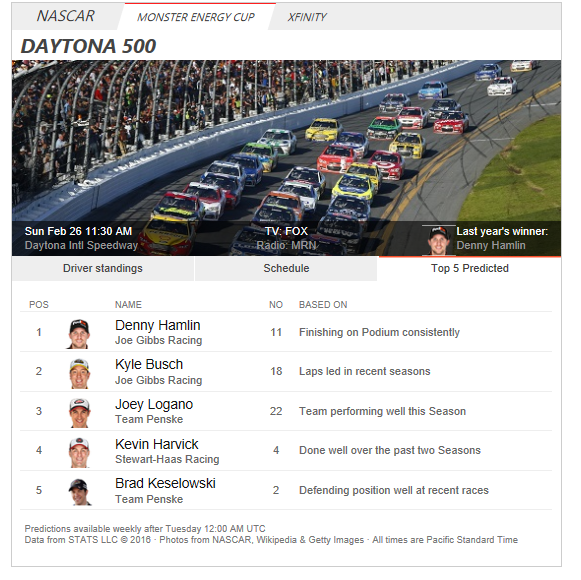
Microsoft's Bing says Denny Hamlin will win Daytona 500 -- do you agree, Nascar fans?
This weekend is the Daytona 500. I won't be watching. While I absolutely love cars, Nascar has never been my thing. Race cars going in a circle? Meh. Daytona USA for Sega Saturn is one of my favorite games of all time, however, but I digress.
Even though Nascar isn't for everyone, it is still very popular with many. Not only do people like to watch the event as spectators, but some folks like to gamble on it too. If you are planning to put some money on the race, Microsoft may have some useful information for you. The company's Bing Predicts division is saying Denny Hamlin will win the race. Actually, the Windows-maker has predicted the top 5 positions.

Windows 10 Insider Preview Build 15042 for PC and Build 15043 for Mobile arrive on the Fast ring
Like buses, you wait over a week for a new Windows 10 Insider Build… and then two come along at once.
In this case, there are two distinct builds -- Build 15042 for PC, and Build 15043 for Mobile. We’re edging ever close to the release of the Creators Update, and so while a lot of the changes in these releases are about squashing bugs and fixing issues, Microsoft has still managed to introduce some new features.

Most executives fear competition from disruptors
Almost two thirds (65 percent) of C-suite executives believe four in ten (40 percent) of today’s Fortune 500 companies won’t exist in 10 years’ time. This is according to new research from ChristianSteven Software, conducted by GITNS.
It is based on a poll of more than 500 C-suite executives across the United States and Europe. It also says that more than half (53 percent) of those surveyed say they fear competition from industry disruptors. Still, nine in ten (91 percent) say they are hopeful about the future of technology in their business.

Employees who embrace BYOD feel judged
There is a strange side-effect to the Bring Your Own Device initiative, and one that's slowing it down. Apparently, many employees refrain from bringing their own devices to work for the fear of being judged.
No, not because their devices are old or slow, but because others will think they're using them for personal instead of professional reasons.

Cloudbleed: Cloudflare leaks sensitive data, many major websites affected
Security researchers from Google's Project Zero have uncovered a critical bug in Cloudflare which allowed sensitive data -- like passwords, cookies and encryption keys -- from many hosted websites to leak online.
Patreon, Y Combinator, Medium, 4chan, Yelp, OKCupid, Zendesk, Uber and 23and Me are among the most-important affected websites. This security issue is so important that it is now being referred to as cloudbleed.

You'll be able to unlock any device running Windows 10 Creators Update with a Samsung phone
If you own a Samsung Galaxy smartphone, and run Windows 10, we’ve got some good news for you.
From April, which is when it’s anticipated that Microsoft will be rolling out the Windows 10 Creators Update, you’ll be able to unlock any Windows 10 device by using your phone… and that’s not all.
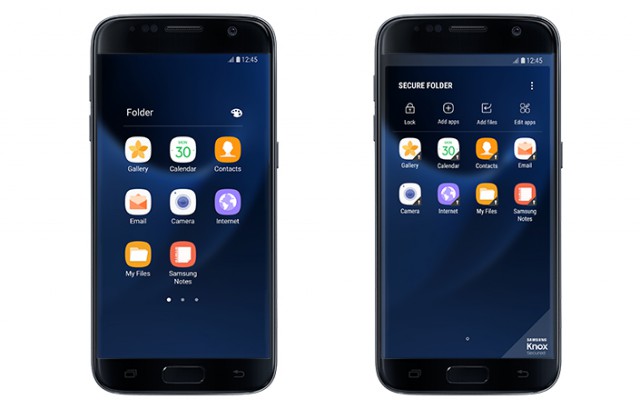
Samsung Secure Folder for Android safeguards your private data
If you want to secure your Galaxy smartphone, the first thing that you should do is set up a screen lock. But what if you want to go a bit further, and protect specific things on the device? Well, Samsung just released Secure Folder, which gives you a "private, encrypted space" to store sensitive data in.
Secure Folder is derived from Knox, the company's secure platform for business users, and can be seen as a consumer-focused iteration. It acts as a sandbox for apps and data and works with existing authentication options to keep them safe.

Best Windows 10 apps this week
Two-hundred-and-twenty in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Windows Store in the past seven days.
As always, if I missed an app or game that has been released this week that you believe is particularly good, let me know in the comments below or notify me via email instead.

Dropbox releases open-source Slack bot
Dropbox is looking to tackle unauthorized access and other security incidents in the workplace with a chatbot. Called Securitybot, it that can automatically grab alerts from security monitoring tools and verify incidents with other employers.
The company says that through the use of the chatbot, which is open source, it will no longer be necessary to manually reach out to employees to verify access, every time someone enters a sensitive part of the system.

New DDoS capabilities uncovered in Necurs botnet
The Necurs botnet is one of the largest around at the moment and is principally known for sending spam including the Locky ransomware.
However, new research from BitSight's Anubis Labs has uncovered a new component being loaded in infected systems that allows it to use bots to enable proxy communications and perform DDoS attacks.
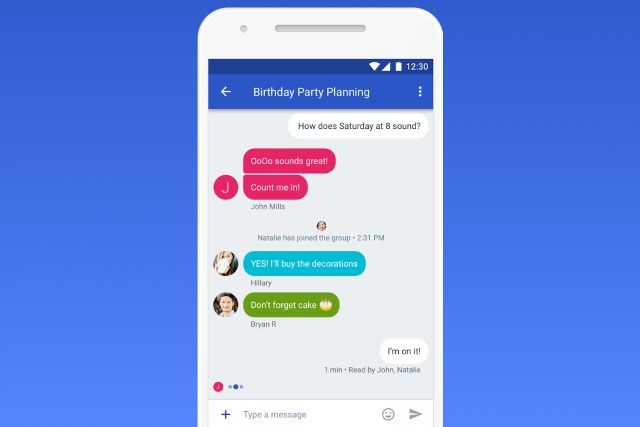
Google renames Messenger to Android Messages as the company pushes RCS
Just last week we were talking about Google's championing of RCS (Rich Communication Services), the successor to SMS. Now the company has renamed its Messenger app to Android Messages as it aims to become not just the default SMS app, but the default RCS app for Android users.
The name change also helps to better differentiate the app from others that had the same name -- such as Facebook Messenger, which is shortened to just Messenger on shortcuts. At the same time, the change is likely to cause a degree of confusion thanks to the sheer number of messaging apps Google now has.

Public cloud services market will reach $246.8 billion in 2017
The global public cloud services market is expected to grow 18 percent this year, according to Gartner’s latest report. Totaling $246.8 billion (up from $209.2bn last year), the growth will mostly come from IaaS, which is expected to grow 36.8 percent and reach $34.6 billion.
The growth will also be fueled by SaaS (20.1 percent increase, to $46.3 billion).
Ubuntu Core Linux comes to i.MX6-powered IoT-friendly TS-4900 Computer On Module
One of the best things about the Linux kernel (and associated operating systems) is the ability to work on various hardware types, including ARM. Microsoft's operating systems, by comparison, are far more narrow. True, there is the lightweight Windows 10 IoT for ARM boards, but it is hardly a factor nowadays.
Today, Ubuntu Core comes to the i.MX6-based and ARM-powered TS-4900 Computer on Module. While Android and other Linux options were already available for the IoT-friendly CoM, Ubuntu Core is still a major win. Canonical's revolutionary snap packages should work beautifully here.

First Windows 10 Redstone 3 build sighted
Microsoft is currently working hard on the next big update to Windows 10, which it’s calling the Creators Update. This will be the second release on the Redstone branch (Redstone 1 being the Anniversary Update).
There is yet another release from the Redstone branch planned for later this year, and although Microsoft has yet to name it, work is already underway internally.

Organizations failing to address security pain points
Cyber-attacks against organizations in 2017 will continue to be as successful as they were last year, because organizations aren't addressing the pain points they had last year, a new report says.
Fujitsu's "Blind spots and security basics -- letting your guard down could cost you in 2017" report says that attacks over encrypted channels will continue to be missed, due to the lack of SSL inspection capabilities.


