
Samsung Galaxy S7 Active rugged Android phone comes to AT&T with massive battery
The summer is almost here, and I am so excited! Relaxing and having fun at the beach, pool, or my backyard are some of my favorite things. Unfortunately, water and sand are not good for electronics. While I absolutely adore my iPhone, I wouldn't dare bring it to the beach, or rest it on a table near a pool.
If you live a very active summer lifestyle, and cannot deal with owning a phone that you must treat gently (such as Apple's), a rugged such offering would be a wise choice. Today, Samsung announces that the all-new rugged Galaxy S7 Active is coming to AT&T as an exclusive. Best of all, it will be available just in time for the summer season.
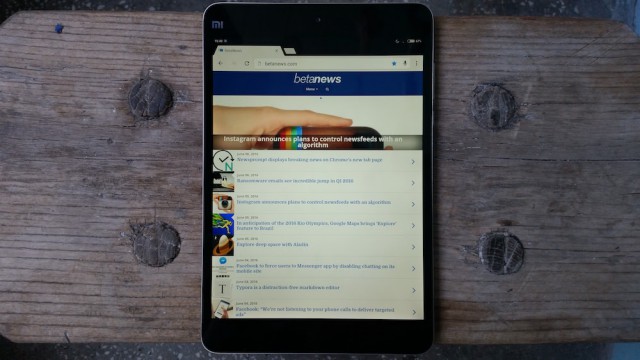
Xiaomi Mi Pad 2 is the small Android tablet you've been waiting for [Review]
There aren't many small Android tablets that can set your world on fire. The manufacturers that are still invested in this market no longer seem to be interested in producing smaller devices, as their attention is now either focused on larger slates or hybrid devices. So, if you are in the market for a small tablet that runs Android, you clearly aren't spoiled for choice.
This is why, after nearly three years on the market, the second-generation Nexus 7 is still my favorite. Google's last small slate got so many things right back in 2013 that I have been struggling to find an attractive replacement for it. But since Xiaomi introduced the Mi Pad 2, I have been wondering whether it is the successor that I have been waiting for so long. Given the opportunity to test it, I set upon to find out whether there truly is a small Android tablet to get excited about these days.

Microsoft has no plans to build a self-driving car
Microsoft won’t be building its own autonomous vehicle, but it will be present in the market, it was confirmed at a conference recently.
Speaking at the Converge Asia conference, Microsoft’s head of business development, Peggy Johnson, made these claims. Instead of building its own car, the company will team up with existing car makers and see to it that the devices get powered by Microsoft’s products.

Change.org petition seeks to have Microsoft investigated for 'malicious' Windows 10 upgrade practices
If you’re unhappy with the way Microsoft is forcing Windows 10 onto people who really don’t want it (including plenty of people who don’t even know what it is), then you’re not alone.
A new Change.org petition is seeking supporters in order to have the EFF (Electronic Frontier Foundation) investigate Microsoft for "malicious practices regarding Windows 10".
Self-driving vehicles can’t operate alone -- they haven't got the brains
It seems that the not so distant future will soon resemble a scene from I, Robot with everyone from car manufacturers to tech companies developing their own model so they can take a stake in an industry that is expected to be worth $2.81 billion by 2022.
While the prospect of a sci-fi fantasy becoming reality is whipping up excitement for many, the driving industry has been thrown into uncertainty with many predicting that fully automated vehicles will push millions into unemployment, but how realistic is this vision? Considering the current roadblocks ahead, it would appear that the idea of implementing automated only vehicles will soon be parked.

New solution simplifies time and task entry for project management
A recent survey from the Project Management Institute showed that inaccurate time and task management is a leading cause of project failure at least 28 percent of the time.
Project management software specialist Changepoint aims to address this with a new solution that team members can use to easily capture task and time data any time, anywhere, and on any device.

Newsprompt displays breaking news on Chrome’s new tab page
Newsprompt is a free Chrome extension which finds, sorts and displays 50+ of the latest news stories on your new tab page. The add-on scans 1,000+ top websites covering broad and niche categories, uses smart algorithms to remove any duplicates, and presents you with the results: a picture, headline, source and date per story.
Just skimming through the recent results will get you up-to-date in seconds. Click anything interesting and the source article opens in new tab.

Ransomware emails see incredible jump in Q1 2016
PhishMe, a security company providing anti-phishing solutions, has released a new report, analyzing the state of phishing attacks worldwide, and the numbers are staggering, though expected.
The first quarter of 2016, compared to the last quarter of 2015, has seen an incredible 789 percent jump in the number of phishing emails containing malicious code, mostly ransomware.

Instagram announces plans to control newsfeeds with an algorithm
People are possessive and precise about their social media. Any change that may be introduced will be scrutinized, criticized, bemoaned, and suffered -- something we've seen time and time again with changes made to Twitter and Facebook timelines. Now Instagram is going down a similar route and introducing algorithmic timelines.
While the move will disappoint -- even infuriate -- many Instagrammers, the announcement has not come completely out of the blue. Just a few weeks ago the social network started testing algorithm-powered timelines and it seems the tests went well. Starting next month, Instagram will ditch the reverse-chronological timeline in favor of one that shows the "moments you care about first".

In anticipation of the 2016 Rio Olympics, Google Maps brings 'Explore' feature to Brazil
The Olympic games are a time when the countries of the world should put aside their differences to engage in sport. Whether that actually happens, however, is debatable. While the athletes are surely capable of focusing on the competition, it can be hard for long-standing disagreements to be forgotten -- even temporarily -- by their home countries.
If you plan to visit Brazil for the Olympic games, and to focus on sport and having fun, Google has you covered. In anticipation of the 2016 Rio Olympics, the search giant is bringing the 'Explore' feature to Brazil Maps.

Explore deep space with Aladin
Aladin is an interactive sky atlas enabling users to visualize and explore a host of astronomical images and data. Or, if that sounds too complicated, you could just use it to look at gorgeous pictures of deep space. Which works for us.
As long as you have Java, there’s no setup required. Aladin is a single executable, and you can just download it and run on Windows, Linux and Mac.

Facebook to force users to Messenger app by disabling chatting on its mobile site
If you access Facebook on your phone, the chances are that you use the dedicated Facebook app -- but this is not necessarily the case. A lot of people prefer to make use of the mobile Facebook website, and the social network is making an aggressive change to the way messaging works that will force the use of the Messenger app.
Head to the messaging section of the mobile site today, and you'll be greeted by a large pre-emptive warning that reads: "Your conversations are moving to Messenger. Soon, you'll only be able to view your messages from Messenger". For now, you can continue to send messages through Facebook's mobile site, but this will end at some unknown date in the future. It's an aggressive tactic reminiscent of Microsoft's forcing of Windows 10 onto users.

Typora is a distraction-free markdown editor
Typora is a minimalist markdown editor for Windows and Mac. Markdown is a simple language which uses plain text formatting to create rich text documents, but you don’t need to understand any of that to get started.
Typora opens much like any other editor. Start typing and you can style text, copy and paste, find and replace, undo, open, print, save and more, with all the keyboard shortcuts you know already.
Facebook: "We're not listening to your phone calls to deliver targeted ads"
Facebook has issued a statement denying mounting rumors that the company uses smartphone microphones to listen in on private conversations. The allegations have circled for some time, but have most recently been voiced by Kelli Burns, a mass communication professor at the University of South Florida.
In her own testing, Professor Burns said that after discussing certain topics within earshot of her phone, she would then see ads relating to those topics on Facebook. Just like the OK, Google feature of Android, the Facebook app does have a feature that listens out for user input, but the company says this data is not stored and certainly not used for ads.

TeamViewer denies being hacked, blames users, and introduces new security measures
In the last couple of weeks there have been a huge number of reports from TeamViewer users that their computers have been hijacked. In addition to this, users of the remote access tool have complained of funds being extracted from PayPal and bank accounts. But TeamViewer insists that there has not been a security breach, instead shifting the blame to users.
The company says they are in the habit of reusing the same passwords for a number of apps and services. It suggests that recent high profile security breaches -- such as the password dumps from MySpace and LinkedIn -- have allowed cyber criminals to learn TeamViewer log in credentials. Despite laying the blame firmly at the feet of users, the company is introducing two new measures to help increase security.



