Why automation can help continuously validate security policies [Q&A]

Security professionals all know that they should test their security hardware and software periodically to make sure it's working as intended. Many normal IT activities have unintended consequences that cause security configurations to 'drift' over time and make the organization more vulnerable.
But testing is frequently postponed or ignored because it never becomes a high enough priority. We spoke to Song Pang, SVP of engineering at NetBrain, to find out how automation can be used to detect when security products or network traffic are no longer behaving as intended.
Google will start deleting inactive accounts and wiping out user data later this year

Google has announced an update to its inactive account policies that means some user accounts will be deleted before the end of the year.
The company says that accounts that have not been accessed for two years will be deleted starting in December. While the deletion of inactive accounts might seem fairly innocuous, there are serious implications for many people, such as those who have used Google cloud storage, or Gmail, as a means of backing up data and have had no reason to access their account since.
Microsoft is looking into slow VPN speed problems in Windows 11 caused by recent updates

The curse of the problematic Windows update may have struck again. Some users who installed the KB5025305 preview update or the KB5026372 update for Windows 11 are complaining about a significant slowdown in VPN speeds.
Microsoft says that it is looking into speed issues with L2TP/IPsec VPN connections in Windows 11. The company is yet to provide a fix, but there is a less than ideal workaround available in the meantime.
AI ethics and innovation for product development

AI ethics are a factor in responsible product development, innovation, company growth, and customer satisfaction. However, the review cycles to assess ethical standards in an environment of rapid innovation creates friction among teams. Companies often err on getting their latest AI product in front of customers to get early feedback.
But what if that feedback is so great and users want more? Now.
Dealing with data: What to do and where to store it

Today’s digitally-enabled organizations generate huge volumes of data that needs to be stored, maintained, and accessed. Indeed, it’s been estimated that globally, around 2.5 quintillion bytes of data is created every day. A figure that is escalating at a rapid rate as enterprises pursue big data analytics and IoT projects.
Added to which, the rising use of video, rich imaging, and AI applications means that much of this data is 'unstructured'. So much so that according to IDC as much as 80 percent of the world’s data will be unstructured by 2025. All of which adds further complexities into the equation when it comes to storing and preserving data so that it is accessible and available for analysis.
New AI-powered engine helps protect critical infrastructure

A new AI-based analysis and response engine designed to quickly address security gaps and resource limitations in mission critical operational infrastructure is being launched by Nozomi Networks.
Vantage IQ uses artificial intelligence (AI) and Machine Learning (ML) to help security teams by automating the time-consuming tasks associated with reviewing, correlating and prioritizing network, asset and alert data.
Selling Gen Z on Fintech

Technology is becoming a more significant part of the world with each passing year and the newest generation of consumers is growing up with digital tools in hand. With this comes a great opportunity for selling Gen Z on fintech.
"Fintech" is a portmanteau of the term "financial technology." It refers to any digital tools financial institutions offer that make managing finances convenient. Since the COVID-19 pandemic, using fintech tools has become the preferred way consumers manage their finances.
Enterprises have a worrying lack of visibility into APIs

Analysis of around a trillion API transactions spanning a range industries over the second half of 2022 by Cequence Security seeks to highlight the latest API threat trends plaguing organizations.
In the second half of 2022, approximately 45 billion search attempts were made for shadow APIs, marking a 900 percent increase from the five billion attempts made in the first half of the year.
EU approves Microsoft's multi-billion-dollar Activision Blizzard acquisition despite UK and US opposition

Just last month, the UK's Competition and Markets Authority (CMA) blocked the proposed acquisition of Activision Blizzard by Microsoft because of concerns about the impact on competition in the cloud gaming arena. In the US, the Federal Trade Commission is also seeking to block the deal
But now EU regulators have cleared the acquisition, subject to conditions. The European Commission will hold Microsoft to commitments it has made to ensure gamers in Europe will have the ability to stream all Activision Blizzard games for which they have a licence via any cloud game streaming services, as well as a corresponding free license to cloud game streaming service providers to allow EEA-based gamers to stream any Activision Blizzard's PC and console games.
Dark web market in infostealers is booming

A new report from the Secureworks Counter Threat Unit (CTU) uncovers a thriving market in infostealer logs that serves as a key enabler for some of the most damaging forms of cybercrime such as ransomware attacks.
On the 'Russian Market' site alone, the number of logs for sale increased by 150 percent in less than nine months, from two million on a single day in June 2022 to over five million on a single day in late February 2023.
WhatsApp introduces Chat Lock to protect sensitive messages
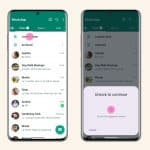
WhatsApp has long been one of the more secure messaging apps with mass appeal, largely thanks to end-to-end encryption. This has been boosted further by features such as disappearing messages, and now Meta has added Chat Lock.
The company says that the feature "lets you protect your most intimate conversations behind one more layer of security"; what this means in practice is that message can be password or fingerprint protected. But there is more to Chat Lock than this.
Microsoft is able to look inside your password protected zip files

Microsoft has been spotted scanning for malware within password protected zip files stored on its cloud services.
Security researcher Andrew Brandt was among those to notice that Microsoft appears to be bypassing passwords added to zip archives in order to check for malware. While the intentions of the company may be good, the practice raises serious questions about privacy and security.
Reality check: Time for rugged devices to get a security upgrade!

Let’s face it, the world is moving at an unprecedented pace. It has become imperative for all industries to evolve and adapt to the digital transformation wave. As the reliance on technology and devices to improve communication and collaboration in the industrial sector increases, mobile devices have been undergoing unbelievable transformations. One such device that is in the spotlight is the rugged handheld devices that are predominantly found in the supply chain, logistics and construction sectors.
For those who were of the notion that handheld devices are just rugged, tough hardware, it is worth taking the time to look at reports that suggest these devices are expected to witness a growth of $1.85bn in the next three years. The digits in billions indicate that it is no longer about having devices that can tough it out at extreme conditions but about revolutionizing a product to suit the dynamic working conditions and to not fade away in the digital transformation wave.
Is the future unified SASE?

Many organizations going through digital transformation are running into roadblocks as their networks become larger and more complex; with approximately 70 percent of companies failing to complete their digital transformation successfully.
The Secure Access Services Edge (SASE) framework has emerged as one of the most effective solutions for getting firms back on track. SASE solutions combine the Network as a Service (NaaS) component and Security as a Service (SaaS) component into a single cohesive solution.
Watch Windows 12 being installed
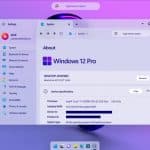
There's been a lot of talk about Windows 12, Microsoft's inevitable successor to Windows 11. Two months ago, my colleague Sofia Wyciślik-Wilson reported on Microsoft's plans for that future OS here.
We've also seen some hints about it tucked away in Windows 11.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.