
FOX News Digital blazes ahead, leaving NY Times and CNN in its dust!
FOX News Digital continues its triumphant march through the world of digital media, sealing its 10th consecutive month as the numero uno brand for multiplatform views in July 2023. According to Comscore, the numbers are a testament to the brand's consistency, with a striking 29 months of reigning supreme in multiplatform minutes.
In a month where CNN.com faced a decline of over 20 percent year-over-year in multiplatform minutes, FOX News Digital showcased its digital muscle. They ended July with a whopping 3 billion total multiplatform minutes, 1.7 billion total multiplatform views, and a staggering 83 million multiplatform unique visitors. When you break down the numbers, it equates to FOX News Digital delivering an impressive 3.2 average views per visit, marking their best month in this particular metric. Their mobile app didn't lag either, registering 5.9 million unique visitors.

Peter Stern shifts gears from Apple to Ford Motor Company
In a significant strategic maneuver, Ford Motor Company has announced the recruitment of Apple veteran, Peter Stern, to oversee its newly established Ford Integrated Services. This pivotal appointment signals Ford’s intensified focus on enhancing software-driven customer experiences across its Ford Blue, Model e, and Ford Pro platforms.
Peter Stern’s credentials are indisputable. Serving as vice president of Services at Apple for over six years, he played an instrumental role in the conception and execution of an array of Apple’s services, including Apple TV+, Apple News+, and Apple Arcade. His expertise in integrating hardware, software, and service offerings will be invaluable to Ford’s ambitious agenda.

Kingston launches IronKey Keypad 200C USB-C flash drive
Today, Kingston Technology unveils its latest product, the IronKey Keypad 200C. This USB Type-C drive is designed to seamlessly integrate robust security with user-friendly convenience. With this drive, users can now ensure top-notch data protection on their USB-C devices, entirely sidestepping the need for any additional adapters.
Richard Kanadjian, IronKey global business manager at Kingston, emphasized the heightened need for data protection. “As breaches due to Cloud penetrations or storage drive losses amplify, there’s a burgeoning demand for robust military-grade protection on hardware-encrypted drives,” he remarked. Kanadjian highlighted the unique position of the KP200C, joining the ranks with the Vault Privacy 50C, in facilitating cross-platform flexibility and effortless data access.

The importance of data privacy in healthcare [Q&A]
Data is one of the biggest drivers of innovation in healthcare today. Almost everything in healthcare relies on having access to the right data from developing new drugs and medical equipment to allocating resources.
Making use of this data often requires sharing with other organizations and that presents challenges when it comes to keeping it secure. We spoke to Riddhiman Das, co-founder and CEO at TripleBlind, to learn how healthcare organizations are securing their data while still making it accessible.
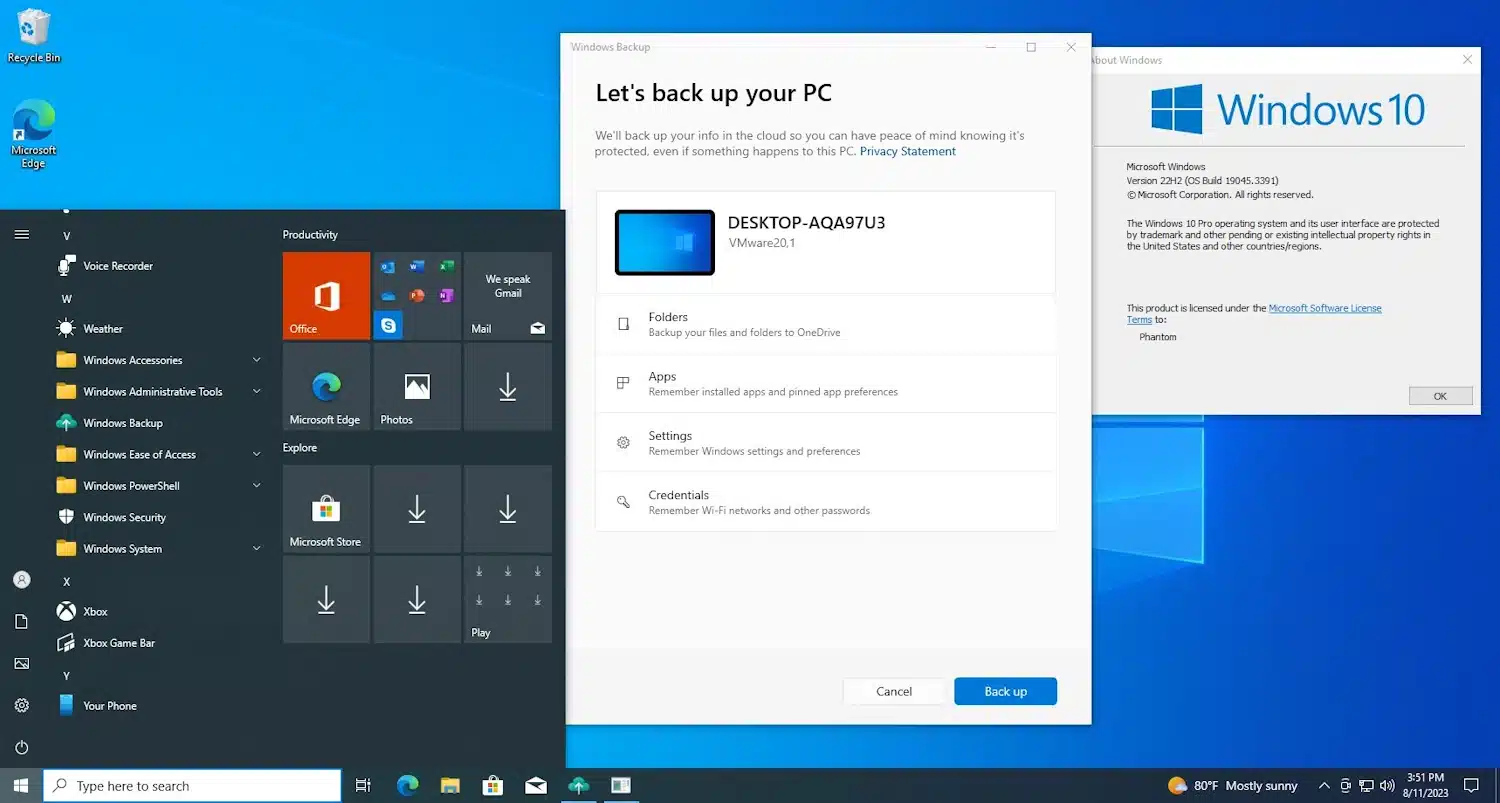
Microsoft is bringing Windows 11's new backup tool to Windows 10
A few months back, we learned of Microsoft's new Windows Backup app. At the time it was only made available to users of Windows 11 signed up as Insiders on the Dev channel.
Now this handy utility is making its way to Windows 10 as well. For now, it is included in the build pushed to the Release Preview Channel last week, but this means it won't be long until Window 10 users have access to an official backup tool from Microsoft which is about more than just safeguarding files.

Technology is a powerful tool for mitigating increasing business costs
Given rising inflation and a gloomy economic outlook for many companies in the UK, optimizing expenditures and cutting costs is essential to ensure the business continues to function effectively. It is imperative to maintain competitive performance, and controlling costs is often a critical step in obtaining robust business operations alongside operational efficiency.
Adopting the appropriate technology can drastically reduce the time invested in labour-intensive tasks, minimise human mistakes, and guarantee that projects are brought to fruition effectively, enabling a business to do more with less. As a result, your business will be better equipped to perform more proficiently, reduce expenses, and strengthen communication with customers and employees.

You're not already using zero trust authentication? Why?
Despite their weaknesses, many organizations continue to rely on a fundamentally flawed traditional security approach that exposes their systems, their data, their users, and their customers to significant risk. Yes, I’m talking here about passwords.
While password practices may have remained a security staple over the decades, the proliferation of digital services offers rich pickings for cybercriminals. Using various methods to gain access to digital accounts, cyber criminals typically target passwords to conduct an attack or account takeover. That’s because passwords are easy to steal and share.

Browser extensions are making a comeback in Firefox for Android
Mozilla has issued a notice to developers, saying that it is preparing to launch support for an open ecosystem of extensions on Firefox for Android.
Pointing out that the move will make Firefox the only major Android browser to support such an ecosystem for extensions, Mozilla says everything sound be in place before the end of the year. The change means that it should not be long before Firefox users with Android handsets are able to use more than just the handful of extensions that are currently available.
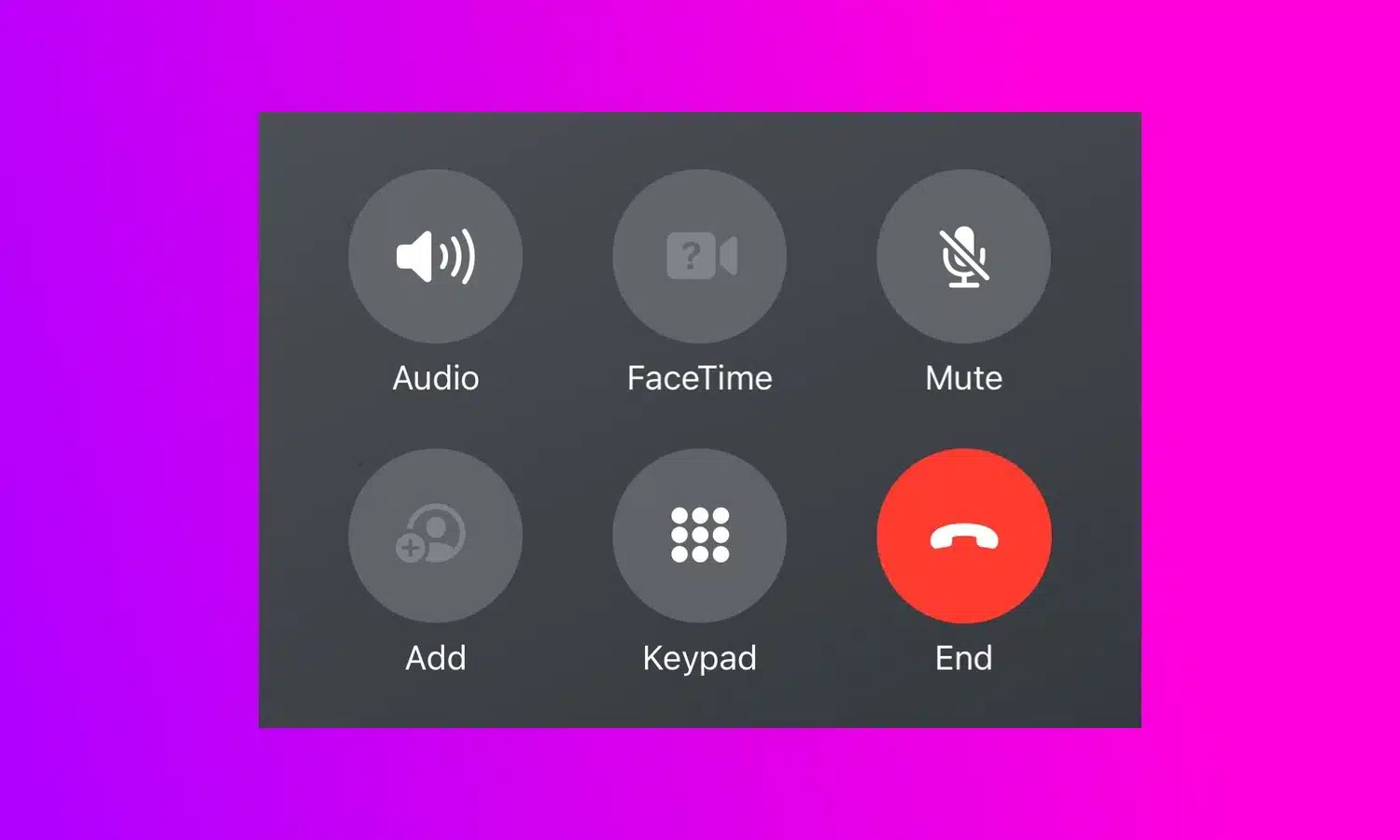
People are mad at Apple for a crazy change to the End Call button in iOS 17
Change is often divisive, and with a UI tweak in iOS 17 Apple is certainly dividing opinion. In the latest beta version of the iPhone operating system, the company has made the decision to move the End Call button.
Shifting the button from the center of the screen -- where it has resided for many, many years -- is causing confusion and wails of discontent from beta testers. Having becomes use to the button being in a central position for well over a decade, users are complaining that the new location is a problem for muscle memory.

Diagnostic fatigue is causing havoc on cyber efficiency
We can all agree that the effective detection and diagnosis of security threats is a fundamental component of cyber resilience. After all, you cannot protect yourself against what you can’t see, right? With organizations rapidly bolstering their security programs and allocating significant investments to advanced technologies to increase visibility into threats and exposures, many have made notable strides in their ability to expedite the detection of abnormal behavior within their environments. However, this hasn’t come without a cost.
Monitoring and threat analysis capabilities are deployed widely across most modern organization's technical infrastructure. Everything ranging from firewalls to email filtering and credential scanning. And the laundry list is proliferating as attackers leverage other weaknesses to spy on and steal data. This is where we begin to encounter challenges. Wading through these alerts, diagnostic analysis and remediation insights has caused a great deal of strain on cyber efficiency and security teams.

Getting colder -- cutting the risk of thermal attacks
Earlier this week we reported on a technique that could determine a password by listening to keystrokes. Just in case you weren't worried enough by that, today we learn of the risk of passwords being compromised by 'thermal attacks'.
These use heat-sensitive cameras to read the traces of fingerprints left on surfaces like smartphone screens, computer keyboards and PIN pads. Hackers can then use the relative intensity of heat traces across recently-touched surfaces to reconstruct users' passwords.
Best Windows apps this week
Five-hundred-and-fifty-five in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Soon, Windows 11 users will be able to uninstall the Cortana application. Microsoft announced the deprecation of the app, in favor of Windows Copilot and other AI-integrations, this week.

Storage challenges in a world of high-volume, unstructured data [Q&A]
The amount of data held by enterprises is growing at an alarming rate, yet it's often still being stored on 20-year-old technology.
Add to this a proliferation of different types of systems -- or even different storage platforms for specific use cases -- and you have greater complexity at a time when it’s hard to find new IT personnel.
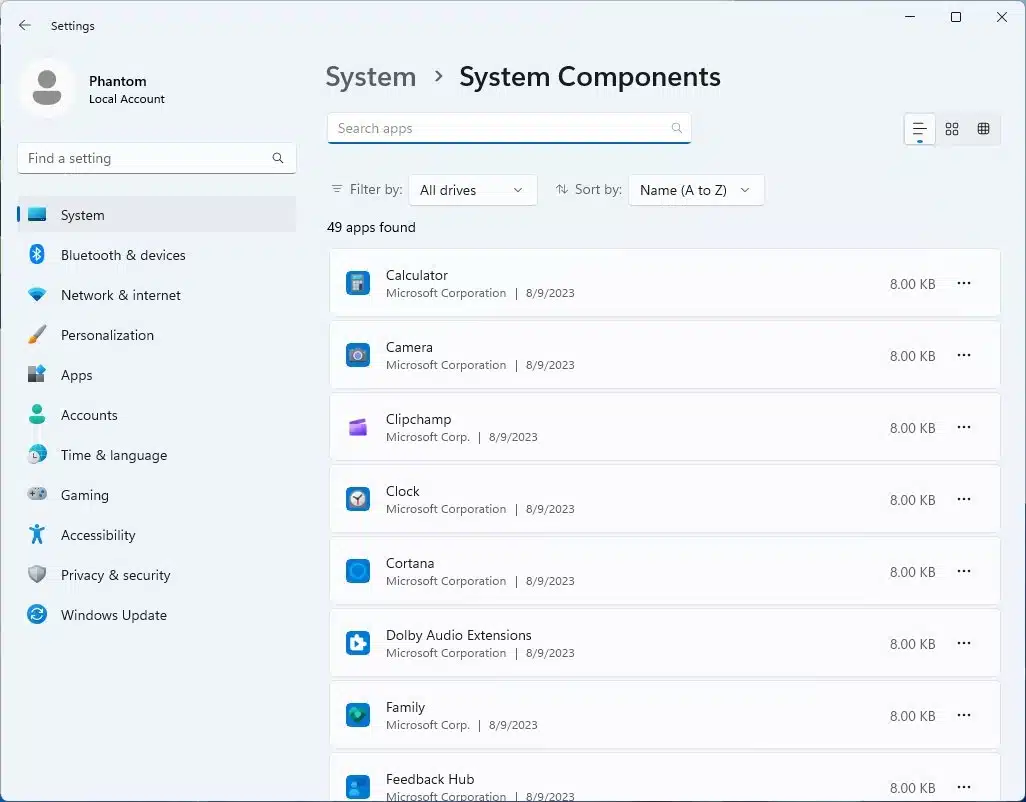
Microsoft adds a hidden System Components section to Windows 11 Settings
With the latest Canary build of Windows 11, Microsoft is at it again, hiding new features for anyone who knows where to look. In Windows 11 build 25926, it is a new section in the Settings app that has been secreted away.
Added with no announcement, and no mention in the release notes, a hidden System Components section in Settings can be enabled with the likes of ViVeTool or Microsoft’s own StagingTool. It provides a list of Windows 11's built-in apps and tools, and allows many to be uninstalled.

Turtle Beach brings Atom Mobile Game Controller to Apple iPhone
Get ready, iPhone gamers -- the future of mobile gaming is here, and it’s Atom-ic! You see, Turtle Beach has announced the Atom Mobile Game Controller, previously released for Android phones, is making its way to Apple iPhone next month.
The controller, available in a captivating Cobalt Blue hue, features a unique two-piece design. These ergonomic modules effortlessly attach to iPhone models ranging from 11 to the latest 14, making gaming seamless. And the best part? You can game away without bothering about removing those pesky phone cases.



