
ADATA LEGEND 970 PCIe Gen5 x4 M.2 2280 SSD is actively cooled
ADATA Technology today launched the LEGEND 970 solid state drive. With a maximum sequential read/write speed of 10,000/10,000MB per second, the SSD is impressively fast.
Equipped with a PCIe Gen5 x4 transmission interface and NVMe 2.0 standard, the LEGEND 970 offers exceptional read/write speeds; twice the speed of its PCIe Gen4 counterparts, and six times faster than Gen3 SSDs. Its compatibility with the latest Intel and AMD platforms, SLC cache algorithm, and DRAM Cache Buffer, ensures high-level performance.

TP-Link releases Deco X55 Pro AX3000 Whole Home Wi-Fi 6 Mesh System
Today, TP-Link launches the Deco X55 Pro AX3000 Whole Home Mesh Wi-Fi 6 System. A notable feature is all three included access points have dual 2.5 Gigabit Ethernet ports. These ports can take advantage of the potential multi-gig speeds provided by the user's local ISP, offering ultra-fast wired connections.
The system also utilizes Wi-Fi 6 technology to deliver up to 3Gbps wireless speed. Thanks to its 160 MHz channel, the Deco X55 Pro performs 250 percent better than four-stream Wi-Fi 5 mesh systems, doubling both bandwidth and throughput.

Why you might not want to sign up for Threads
Mark Zuckerberg claims that some 30 million people have signed up for Meta's Threads app since its launch on Thursday.
You might be tempted to think, “He would say that,” but in the rush to join the new Twitter alternative are people overlooking the security and privacy implications of the app? Quite a few experts think so.
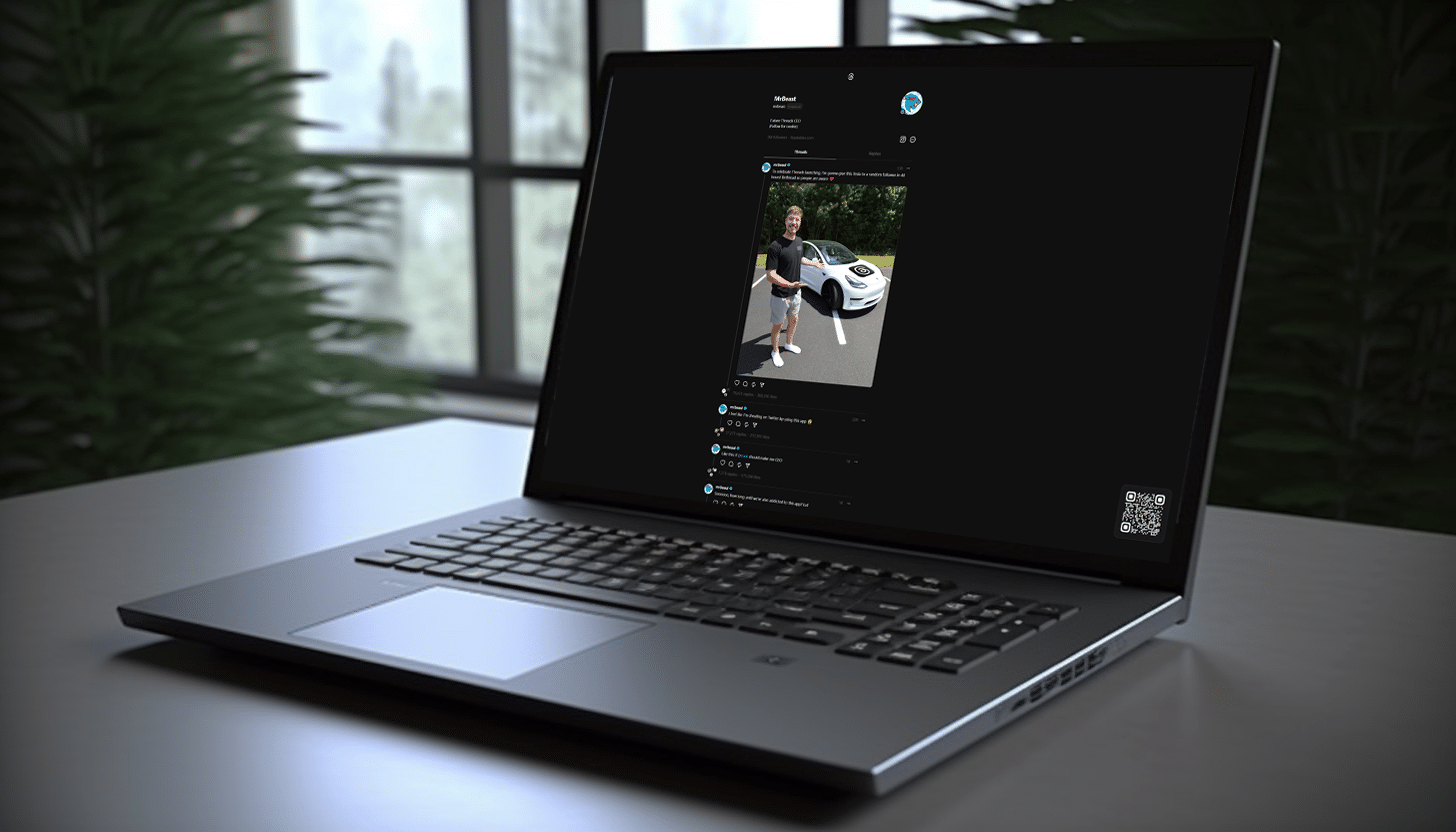
View your Threads (or anyone else's) on the web
Although it only launched a couple of days ago, Meta's new Twitter rival Threads is already a big success. It's lacking some important features at the moment, although they are coming, and not all of its capabilities are obvious.
For example, it's not clear how to add a second account to Threads, or how to switch between accounts, but it is possible.
Best Windows apps this week
Five-hundred-and-fifty in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft is making changes to the Windows 11 Start menu which will highlight its own apps in the operating system.

Meta faces criticism for poor accessibility features in Threads
Social platform Threads may only be a couple of days old, but it has already amassed millions of users. While Meta might be celebrating the popularity of its new Twitter rival, the company is also facing criticism from various quarters.
Huge privacy concerns mean that Threads not available in the European Union -- not officially, at least. But there are also complaints that the app has been rushed and feels unfinished. Released in Disability Pride month, one of the biggest complaints leveled at Threads is that it lacks basic accessibility options and features.

Disrupting the phishing killchain with new defenses [Q&A]
Recent reports have shown that email is still the channel where enterprises are most vulnerable to attacks, in particular phishing.
But adding new browser-based layers of security protection can disrupt such killchains, for example by preventing phishing victims from accessing or engaging with spoofed sites. We spoke to Red Access co-founder and CTO Tal Dery to find out more.

Meta publishes Threads Dictionary to help newcomers decipher the jargon
For many people the release of Threads, Instagram's text-based conversation app, represents an alternative to Twitter -- a platform which is widely considered to have become more toxic and problematic under Elon Musk. But for an even larger number of people, Threads will be their first step into this type of social media.
Switching from Twitter, Mastodon or Bluesky to Threads -- or using them in conjunction with each other -- is painless, but for anyone who has never used such a platform, the language surrounding it can be slightly mystifying. And this is why Meta has released a Threads Dictionary to bring users up to speed.

Unveiling retail's success roadmap for the tech industry
Amidst the ever-evolving post-COVID-19 era, the tech industry has been met with unprecedented challenges such as budget constraints, mass layoffs, and the urgent need for adaptability. In the face of these uncertainties, tech companies can draw valuable insights from numerous retailers who demonstrated remarkable resilience during the pandemic. How did these retailers triumph amidst one of the most challenging periods in recent history? In this article, we explore key takeaways that hold immense potential to benefit the tech industry in the current economic landscape.
Retailers have demonstrated unwavering dedication to improving customer service, cultivating loyalty, and fostering trust, resulting in strong and enduring customer relationships. Tech companies can adopt a similar approach to enhance their customer service efforts, aiming for frictionless user experiences and delivering personalized recommendations. Embracing innovative channels like chatbots, virtual assistants, and social media platforms enables real-time support and fosters immediate engagement, nurturing long-lasting connections with customers.

Transcend UTE210T is a next-gen U.2 NVMe SSD tailored for AI and big data
M.2 solid state drives are very common, but U.2 NVMe SSDs? Not so much. And so, the announcement of such a drive can be an exciting affair. With that said, today, Transcend has done exactly that. Yes, the company has unveiled a new U.2 NVMe SSD. Called “UTE210T,” the 2.5-inch drive is specifically crafted for use in generative AI, high-performance computing (HPC), and big data analytics.
At the heart of the UTE210T lies the 112-layer 3D NAND flash, an 8-channel controller, and a PCIe Gen 4x4 interface. The combination of these elements make up an SSD that offers blazing-fast sequential R/W speeds of up to 7,200/6,500 MB/s. This, in turn, grants your systems low latency, minimal power consumption, and reliable performance.

The straightforward guide to digital transformation
Businesses must embrace a digital future for multiple reasons: to avoid falling behind competitors, to strengthen security and cut down on security breaches, and to remove the reliance on legacy software.
We know it is important, but where do you start with approaching digital transformation? In this handy guide, we explain and break down digital transformation, as well as offer tips to success with going digital and unlocking future success.

TUXEDO’s 5th generation Stellaris 17 is a hardcore Linux laptop
Today, TUXEDO launches the 5th generation of the Stellaris 17 -- a hardcore gaming and workstation notebook. The laptop is everything a cutting-edge, upper-tier gaming desktop PC should be, but in a compact, portable, and robust package.
The Linux laptop is a high-end desktop replacement encased in a premium chassis. The machine's remarkable power is made possible by NVIDIA RTX 40 graphics cards (with the option of up to the GeForce RTX 4090) and the top-tier Intel Core i9-13900HX CPU.

How to add and manage multiple accounts in Threads, Meta's new Twitter rival
Threads, Meta's Twitter alternative, is now live and already proving incredibly popular. It's very much a work in progress, with lots of features missing, but the developers are working hard at bringing these to the app.
One question I've seen asked quite a few times is how to add a second account to Threads, and it's definitely not as obvious as it could be. The process is easy enough though, just follow these steps.

Value of cybercrime equivalent to the third largest global economy
Whoever said 'crime doesn't pay' clearly did so before the advent of the internet. A new report shows that if cybercrime was a country it would be the third largest global economy, valued at $10.5 trillion by 2025. Some 33 billion records are estimated to be stolen in 2023 -- a huge increase of 175 percent from 2018.
The latest Cybercrime Statistics Report from Independent Advisor, shows that last year the cost to US businesses of an average cyberattack amounted to a huge $4.35 million. In addition, 83 percent of organisations got attacked more than once.
Microsoft releases PowerToys v0.71.0 with visual refresh, archive file preview and much more
It feels as though it has been a while since the last update for PowerToys, but Microsoft has now rectified this. The company has released PowerToys v0.71.0 which sees not only a large number of bug fixes, but also numerous tweaks, improvements and additions.
This is a hugely significant update that adds support for the previewing of archives in the Peek utility, as well as making it possible to use Registry Preview as the default tool for opening .reg files. PowerToys developers have really gone to town with this release; just about every module has been updated and there is an improved look that is more in line with the Windows 11 aesthetic.



