Microsoft announces that third-party widgets are coming to Windows 11 this year
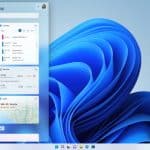
At its Build 2022 event, Microsoft confirmed what we have heard rumored for some time -- that third-party widgets will soon be making their way to Windows 11.
Although the company has not given an exact date, it says that "later this year" it will be possible for developers to start building their own widgets. It is possible -- probable, even -- that this will be linked to the release of the Sun Valley 2 feature update for Windows 11 in the coming months.
Logitech launches MX Master 3S mouse and a pair of MX Mechanical keyboards

Logitech's MX Master wireless mice are very popular with consumers, but I am not a big fan. Don't get me wrong, these mice are very well-made, but they are a bit too big for my small hands. Not to mention, I find some of the extra bells-and-whistles like the clickable thumb rest and thumb scroll-wheel to be unnecessary and distracting. In other words, not everyone will enjoy using an MX Master mouse.
Today, Logitech launches its latest such mouse -- the MX Master 3S. As the name suggests, it is only a slight improvement over the existing MX Master 3; it apparently isn't worthy of an "MX Master 4" moniker. What makes the 3S better than the 3? Essentially, it has up to 90 percent quieter clicking and an improved 8,000 DPI optical sensor. In other words, if you already have an MX Master 3, upgrading to the S variant would be a bit silly.
Apple Music finally comes to Google's Waze

If you have ever driven a car and needed directions, there's a good chance you have tried Waze. The Google-owned service is very popular thanks to its crowdsourced traffic information -- any user can report traffic jams, police speed traps, and more. It really is a useful app that can reduce travel times.
One of the coolest features of Waze is the ability to integrate with music-streaming services, such as Spotify, so you don't have to exit the navigation app to interact with music controls. This isn't just for convenience, but for safety purposes too. Sadly, the wildly popular Apple Music has not been compatible with the aforementioned Waze feature, but today, this finally changes.
Elevation of privilege is the top Microsoft vulnerability category

A new report into Microsoft vulnerabilities shows 2021 saw a 47 percent decrease in critical vulnerabilities, marking the lowest ever total since the report began.
The 2022 Microsoft Vulnerabilities Report from BeyondTrust also reveals that for the second year running, elevation of privilege was the #1 vulnerability category, accounting for 49 percent of all vulnerabilities.
Growing complexity leads enterprises to look for new service providers

A new study from CloudBolt Software reveals that 80 percent of enterprises are so frustrated with their existing cloud-oriented provider they are actively looking for a replacement within the next twelve months.
At the core of this dissatisfaction with CSPs and MSPs is the growing complexity of multi-cloud environments, and a widening skills gap among both enterprises and service providers.
Two-thirds of data breaches at UK legal firms caused by insiders

New analysis of data breaches in the UK legal sector reveals that 68 percent were caused by insiders.
Analysis by secure cloud platform NetDocuments of data from the Information Commissioner's Office (ICO) reveals evidence of a 'Great Exfiltration' where employees are leaving their jobs and taking their company's data with them.
How secure is your supply chain?

Supply chains are fast becoming one of the top targets for cyber criminals, so when it comes to supply chain risk management, organizations in every industry need to start paying more attention.
While the vast majority of business leaders recognize that cybersecurity is now a key priority, the UK’s Department for Digital, Culture, Media and Sport (DCMS) recently noted that in too many instances, actions aren’t keeping up with intentions. In fact, nearly a third of UK companies admitted they aren’t currently taking any preventative action at all.
Kingston VP80ES IronKey Vault Privacy 80 is an encrypted USB-C SSD with touchscreen

Solid state drives don't just make wonderful internal boot drives for computers -- they're excellent for external storage too. Not only are they smaller than mechanical hard disk drives, but they use less power and are much faster as well. Quite frankly, if you are someone that needs to transport data on a portable drive, you'd be insane to still use a HDD with moving parts.
But what if you lose that external solid state drive? Well, if the content is unencrypted, your files could be exposed to the finder. This is particularly problematic for business users that are storing company secrets or private customer data. Thankfully, a new USB-C solid state drive from Kingston makes it super easy to encrypt and decrypt your data. You see, the VP80ES IronKey Vault Privacy 80 is a hardware-encrypted (FIPS 197 certified with XTS-AES 256-bit) SSD with a color touchscreen that allows you to enter a passcode, password, pin, or phrase.
Windows 11 Phone is everything a mobile operating system should be
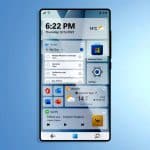
Microsoft certainly bet big on Windows 10 Mobile, even going so far as to buy phone giant Nokia in order to make its own handsets for it. While there was much to recommend the tiled mobile operating system, the combined might of iOS and Android proved too strong for the would-be rival. Windows 10 grew into a great operating system on PCs and tablets, but the company was forced to pull the plug on its mobile aspirations.
Windows 11 is slowly replacing Windows 10 (with the emphasis on 'slowly') but given the chance, would it fare any better on mobile than its predecessor did?
Why the voice network is a blind spot for security professionals [Q&A]

We're familiar with threats to data and data networks, but there's another part of corporate communication that's often overlooked yet represents an equally valid attack vector and equally high risks.
We spoke to Mutare CTO Roger Northrop to find out more about the risks voice networks present and why organizations need to take them seriously.
Silicon Power PCIe Gen 4x4 UD90 solid state drive is fast, but the SSD is also kind of slow

Are all PCIe 4.0 solid state drives fast? Absolutely. However, they aren't all the same speed. For instance, the Mushkin SSD we covered here can achieve read speeds up to 7,415MB/s -- that is really fast. A new SSD called "UD90" from Silicon Power, however, can only do up to 4,800MB/s.
Yes, folks, we have two M.2 drives, both with the same PCIe Gen 4x4 interface, but one is significantly faster than the other. In other words, the UD90 is rather slow as a PCIe Gen 4.0 drive... comparatively. And yet, compared to SATA-based solid state drives, the UD90 is actually incredibly fast.
The current state of intelligent automation adoption in cybersecurity

In the past year, research indicates that nearly a third of organizations have accelerated their plans to automate key security and IR processes, whilst another 85 percent plan on automating them in the next 12 months.
Despite the positivity of these statistics, many organizations struggle to change to a more automated process. This was highlighted at a recent webinar we held with a panel of senior cybersecurity experts from a multitude of sectors. The discussion revealed that, while most organizations are exploring automation, few have made significant progress and they attributed this to a combination of factors including needing an improved understanding of automation, increased help from vendors and a lack of good IT foundations.
Employee burnout: The financial impact to businesses and how to tackle it

Customers are always at the heart of a business. In fact, company owners, managers and their employees often go out of their way to please and satisfy every client’s needs. There is no hiding that this can be a tiring and demanding process, and it can eventually end up having a detrimental impact on a business' biggest asset: its employees.
Without adequate support and precautions, workers can face burnout. Not only will this put their physical and mental wellbeing to the test, but it can also conceal serious implications for the business itself. Stressed and unhappy employees can be more difficult to manage and -- in the long term -- could have pricey consequences on the company’s finances.
Four reasons you should go digital in your asset management

Managing assets is an important but laborious task. It can be difficult to track the location, condition or repair history of individual assets, and surveys are highly costly and time-consuming.
It’s likely your work is being doubled-up and digging out asset data requires you to locate the one CAFM super-user on your site, or you end up relying on pieces of paper, only to input the data at a later time.
How Fortune 1000s can get privileged access management right

Privileged access management is not a new concept to most IT and security leaders, but we’ve seen a surge in cyber incidents focused on exploiting privileged access that have renewed its importance. From the Windows Print Spooler vulnerability of 2021 to the Okta breach that impacted hundreds of companies earlier this year, attackers continue to gain access through vulnerable credentials and use that access to move laterally and cause trouble at rapid speeds for Fortune 1000 organizations. While breaches happen, it’s unfortunate when something as simple as privileged access management could have thwarted the attackers.
As geopolitical tensions continue to rise on the cybersecurity front, it’s clear no one is spared from cyberattacks. With that, it’s more critical than ever before for organizations to closely review current privileged access management policies and solutions. Here are some best practices to think about when deciding how to approach PAM properly and securely.
Most Commented Stories
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.




