
Cloning voices: The opportunities, threats and needed safeguards
Microsoft recently made headlines by announcing it is working on a form of artificial intelligence (AI) called VALL-E that can clone voices from a three second audio clip. Imagine that now AI can have anyone’s voice say words without that individual actually speaking! Even more recently, Samsung announced that its software assistant, Bixby, can now clone users’ voices to answer calls. Specifically, Bixby now lets English speakers answer calls by typing a message which Bixby converts to audio and relays to the caller on their behalf.
Technologies like VALL-E and Bixby are bringing voice cloning to reality and have the potential to be industry game changers. The term voice cloning refers to the ability to use AI to build a digital copy of a person’s unique voice, including speech patterns, accents and voice inflection, by training an algorithm with a sample of a person’s speech. Once a voice model is created, plain text is all that’s needed to synthesize a person’s speech, capturing and mimicking the sound of an individual. In fact, many different types of voice cloning companies are now launching, making this technology much more accessible.
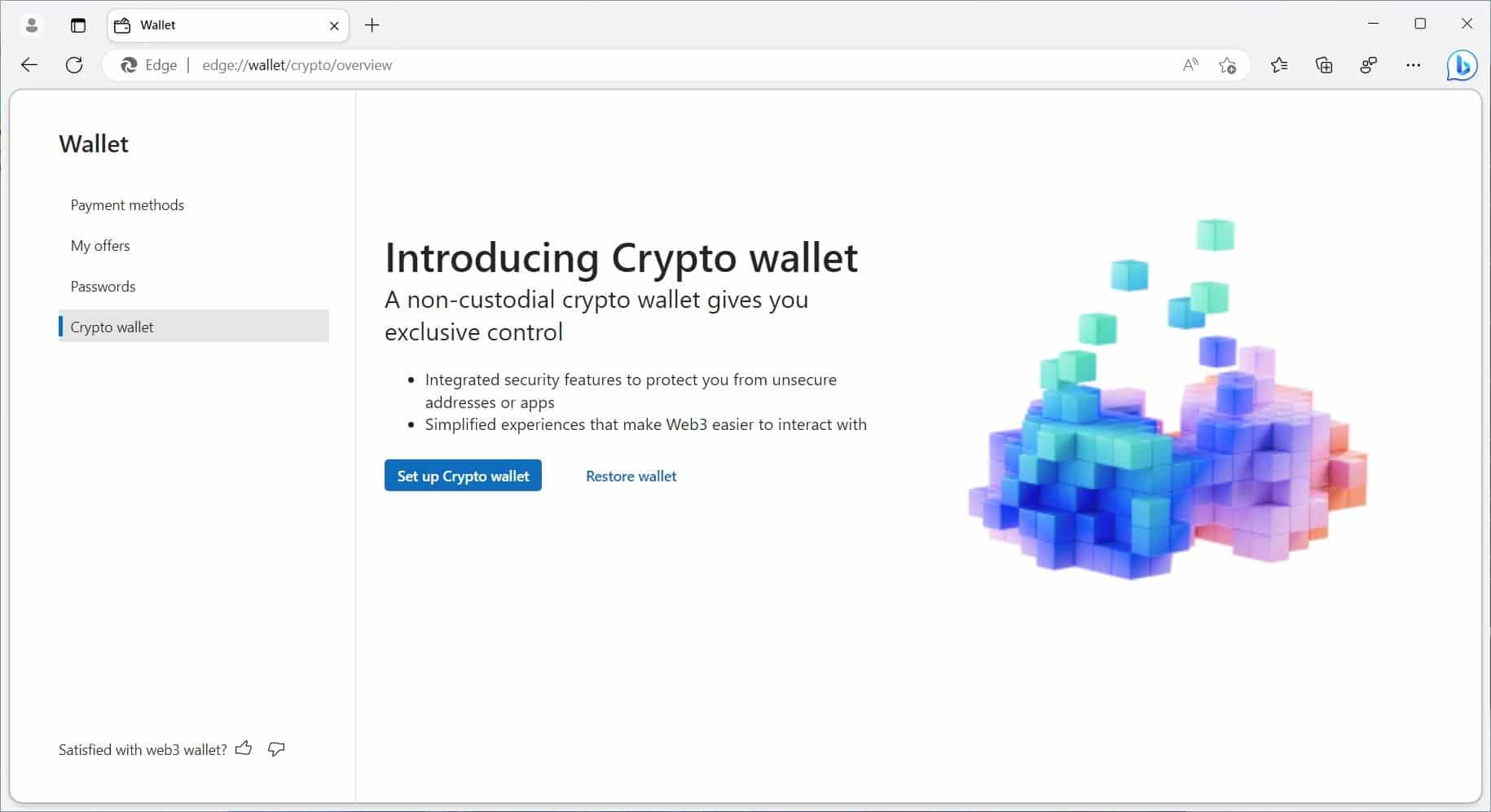
Microsoft Edge is getting an integrated crypto wallet
Microsoft is working to bring a cryptocurrency wallet feature to its Edge browser.
Known simply as "Crypto wallet" the feature is currently undergoing development and is being trialed on a test group of unknown size. Microsoft highlights the benefits of having the non-custodial wallet embedded in Edge, eliminating the need for a browser extension.

Microsoft is bringing huge changes to app pinning and app defaults in Windows 11
Microsoft has unveiled plans for what it is referring to as "a principled approach to app pinning and app defaults in Windows". The company has outlined sweeping changes that are coming to Windows 11 that will give users greater control over their computers.
The updates mean that the pinning of apps to the Start menu, desktop and taskbar will respect user choices, and adjusting the default apps used to open specific file types will be much easier. Microsoft says that the changes -- which are due to hit the Dev Channel soon before making their way to everyone else -- will also benefit developers.
New platform aims to deliver consumer insights without compromising privacy
The online world means that there is more information available about individuals than ever before. At the same time, however, there's growing concern around tracking and privacy.
A new SaaS platform launched this week by Qudo uses 'zero-party' data shared by consumers in anonymous online surveys, rather than rely on first- and third-party data collected via cookies.

How to install Windows on a USB Flash Drive
Windows installations benefit from fast hard drives, and installing Windows on USB Flash Drives may sound counter-intuitive on first glance. While it is true that dedicated hard drives, especially Solid State Drives, are better suited for running Windows, USB Flash drive Windows installations offer some features that these dedicated installations don’t.
Installation on a USB drive makes the Windows installation portable. You can connect it to different PCs and use it on these, provided that booting from USB is supported. One downside is that this works best with PCs that have the same hardware. This solution has other benefits; it can be used to boot a copy of Windows on a PC it was created on, even if the main hard drive is no longer available.

Get 'Linux Bible, 10th Edition' (worth $36.00) for FREE
Linux Bible, 10th Edition is the ultimate hands-on Linux user guide, whether you're a true beginner or a more advanced user navigating recent changes. this updated tenth edition covers the latest versions of Red Hat Enterprise Linux (RHEL 8), Fedora 30, and Ubuntu 18.04 LTS.
It includes information on cloud computing, with new guidance on containerization, Ansible automation, and Kubernetes and OpenShift.

Best Windows apps this week
Five-hundred-and-thirty-four in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft unveiled Microsoft 365 Copilot yesterday, which "combines the power of large language models (LLMs) with business data and Microsoft 365 apps".

Microsoft is fixing a plethora of Windows 11 problems with the KB5023774 update
Ahead of next week's Patch Tuesday, Microsoft has released a preview of the upcoming KB5023774 update for Windows 11.
This is a non-security update, but it addresses a wide range of issues with Windows 11, including problems with Notepad, USB printer abnormalities, and bugs that were sending PowerPoint awry.

Poorly planned digitization makes it harder for customers to get support
Most businesses now offer their customers multiple means of getting in touch, with many providing online chatbots as a customer service channel.
But new research released by Twilio shows that without taking advantage of first-party data to understand their customers and personalize their approach, businesses are missing key opportunities to engage.

How IBM and AWS are driving innovation in the cloud [Q&A]
As we reported at the end of last year, IBM and AWS have extended their collaboration, making IBM software products available as Software-as-a-Service (SaaS) on the AWS Marketplace.
We spoke to Judah Bernstein, CTO, AWS strategic partnership at IBM, to find out more about how the collaboration works and what it means for customers and Ecosystem partners.

Get 'Teach Yourself VISUALLY Windows 11' (worth $19.00) for FREE
Teach Yourself VISUALLY Windows 11 collects all the resources you need to master the day-to-day use of Microsoft’s new operating system and delivers them in a single resource.
Fully illustrated, step-by-step instructions are combined with crystal-clear screenshots to walk you through the basic and advanced functions of Windows 11.

Twitter now shows how many times a tweet has been bookmarked
For fans of statistics, or anyone who has an idle curiosity, Twitter has introduced a new bookmark count feature. As well as making it possible for anyone to judge the interest an individual tweet has generated, the new analytics are useful for companies and individuals looking for a more accessible way to track interactions.
While there will be privacy concerns associated with this, Twitter assures users that "your Bookmarks are still private", promising that "we'll never display which accounts have added a Tweet to their Bookmarks".

Microsoft releases PowerShell scripts (KB5025175) to help address BitLocker vulnerability
Microsoft has published details of PowerShell scripts which the company has designed to help automate updating the Windows Recovery Environment (WinRE) to address a BitLocker security vulnerability.
The security feature bypass vulnerability affects both Windows 10 and Windows 11, and sample scripts are available for different editions of both versions of the operating system.

Impersonation attacks leverage Silicon Valley Bank collapse in new phishing campaign
As news of Silicon Valley Bank’s (SVB) collapse continues to dominate the headlines, cybercriminals are running phishing campaigns impersonating SVB and other financial institutions, including M-F-A and Bloomberg.
Responding quickly to the 24-hour news cycle, cybercriminals aim to leverage their victims’ potential distress over their financial situation to make them more susceptible to this type of attack.

YouTube TV gets yet another price hike
Right now, it feels like the US economy is in shambles. Tech companies are having huge layoffs, banks are failing, and inflation continues to eat away at people's savings accounts. Hell, many people can't even afford eggs anymore.
And now, YouTube TV is joining the inflation party with a new price hike. Sadly, Google has decided to increase the monthly cost of YouTube TV from $64.99 to $72.99. Thankfully, this jump in price isn't astronomical -- it is a mere 12 percent bump up. On a positive note, the 4K Plus add-on package is getting a price cut.



