Microsoft shares some of the design ideas behind Windows 11
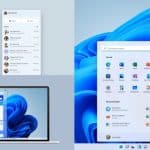
Windows 11 is almost upon us. While the look may not be radically different to Windows 10 -- evolution over revolution is a phrase you'll hear bandied around -- it is still different enough for the changes to be instantly noticeable.
You may be wondering just how and why Microsoft took the design decisions it did with Windows 11. To help sate this curiosity, the Microsoft Design team has given us a fascinating insight into the process and the philosophy that underpins everything.
Microsoft releases KB5004237 and KB5004245 to fix dozens of Windows 10 problems

Yesterday was Patch Tuesday, and as such Microsoft released updates to fix a batch of problems with Windows 10.
There are fixes for security issues as well as other niggles, including addressing the PrintNightmare vulnerability. KB5004237 is available for Windows 10 versions 2004, 20H2 and 21H1, while KB5004245 is just for version 1909.
Apple finally launches MagSafe Battery Pack for iPhone 12 line of smartphones

Apple's iPhone smartphones have historically offered very good battery life comparatively. In fact, in my experience, Apple's devices typically last a lot longer than many Android phones. This is despite Android phones often having larger batteries. Apple simply does a better job of optimizing its software. Not to mention, since the company designs its own hardware (including processors), Android-makers simply cant compete in this regard.
Even though Apple iPhone 12 battery life is reportedly great (except maybe for the mini model), the company has finally launched a MagSafe Battery Pack. This accessory is primarily designed for hardcore iPhone users that never put the device down. This battery attaches to the rear of the phone using magnets and extends its usage time. Just make sure to keep it away from your pacemaker!
Download Tails Linux 4.20, man

Hey, man. Want to know something totally far out? The privacy-focused Linux-based operating system, Tails, has achieved version 4.20. How groovy! If you aren't familiar, Tails is designed to run from an optical disk or USB drive and hide your browsing activity. It is particularly handy for journalists or computer users living in countries ruled by oppressive governments.
Version 4.20 of Tails receives several improvements. For instance, OnionShare has been updated to 2.2 and KeePassXC is now at 2.6.2. More importantly, the Tor Browser has been updated to 10.5.2 and the Linux kernel now sits at 5.10.46. Most significant, however, there are massive enhancements when connecting to a Tor network, including a new assistant.
The three industries experiencing a technological revolution

If I asked you to think of an industry that has been revolutionized by technology, you’d probably have no problem answering. In fact, the more difficult question might be naming an industry that hasn’t experienced digital transformation, particularly in the past year.
It’s clear that some industries are more technologically advanced than others. Naturally, technology businesses including Apple, Microsoft, and Google are leading the way. Media, financial services, and energy providers are some of the most digitized sectors. Some sectors, meanwhile, are still in their digital infancy. But that’s about to change. Here, we detail three sectors that are on the cusp of a digital revolution.
Using technology to boost engagement in video meetings

Since the shift to virtual and hybrid working, we’ve all experienced some form of video fatigue. Whether it be back to back video meetings discussing different topics or enduring a meeting that has lasted well over an hour, the era of virtual meetings can be challenging and as a result can lead to unengaged attendees.
While these challenges may be hard to overcome and are a common problem for all, there are a number of different tools and technologies that organizations can implement to have a positive impact on productivity and engagement during video meetings.
Security leaders want to give people more freedom -- but restrict it

A new survey of 200 enterprise IT and security leaders appears to uncover a fundamental paradox. 96 percent of respondents called for an expansion of IT freedom, while 91 percent say that enterprises also need to put more IT restrictions in place.
The study from OS isolation company Hysolate finds that in the post-COVID world businesses face demands to press for changes to IT security policies to simultaneously increase employee productivity while also enhancing the organization’s ability to ward off ransomware and other attacks.
Vertagear launches elegant gaming chair that is covered in beautiful Swarovski Crystals

When people think of PC gaming gear, they aren't likely to think of furniture. Instead, they probably conjure images in their heads of mice, keyboards, and controllers. But the gamer's computer and monitor need to sit upon a desk or table, right? And of course, the players themselves need to sit in a chair. So, yes, gamers do need furniture.
Believe it or not, gaming chairs are a things these days, providing extra comfort for long gameplay sessions. Not to mention, these chairs look cool, appealing to the style of gamers. One of the companies that makes such chairs, Vertagear, has a model called PL4500. And now, that chair is getting a special new variant. You see, Vertagear has partnered with Swarovski to emblazon the PL4500 with beautiful crystals. Très chic!
Insider breaches hit 94 percent of organizations

Insider data breaches have been experienced by 94 percent of organizations in the past year, according to a new survey of 500 IT leaders and 3,000 employees in the US and UK, from email security company Egress.
Human error is the top cause of serious incidents, according to 84 percent of IT leaders surveyed. However, respondents are more concerned about malicious insiders, with 28 percent saying that intentionally malicious behavior is their biggest fear.
Tweak the registry to make sure you're protected against the PrintNightmare Windows vulnerability

The accidental revelation of the PrintNightmare security vulnerability in Windows set off a chain of workarounds, third-party patches, official patches and problems with patches. But even after two weeks of back and forth, there are still steps you need to take to ensure that you're fully protected.
Microsoft recently updated its security advisory notice about the vulnerability to include additional details that system administrators should check. A quick visit to the registry is all it takes to ensure complete security.
Companies face more than 1,000 domain impersonations each year

Businesses are facing a wave of attacks using domains impersonating their company and brand names according to a new study.
The research from risk protection specialist Digital Shadows shows that in the last four months its clients experienced an average of 360 domain impersonations, amounting to over 1,100 per year.
Silicon Power PD60 USB-C enclosure turns any M.2 SSD into a portable storage drive

NVMe solid states are insanely fast and getting more affordable every day. It is for this reason that most consumers should opt for them when possible -- they put SATA variants to shame. Even if you don't need the extra performance of an NVMe SSD, the ever-lowering prices make them a no-brainer.
While most people probably think of NVMe SSDs as something to go inside a computer, they also make exceptional external drives -- when paired with an enclosure, that is. Today, Silicon Power launches its latest USB-C enclosure. Called "PD60," it is compatible with both NVMe and SATA M.2 SSDs.
New free tool helps map legacy identity systems

A number of on-premise identity systems from major suppliers including CA, Oracle and IBM are coming to the end of their lives and many businesses are looking to migrate to cloud alternatives.
But before migration can begin it's necessary to discover and catalog legacy identity systems. This is a largely manual process because there is no unified view of older environments that span multiple stakeholders, have evolved over a number of years, and can contain hidden complexities.
Security leaders struggle to guard against data loss

A new study from risk protection platform SafeGuard Cyber shows cybersecurity leaders understand what is needed for successful digital risk protection, but they are still struggling to provide it.
Lack of visibility (39 percent) is the biggest challenge for security leaders who aim to maintain security and compliance across all business communications.
Firefox 90 introduces background updates to Windows, tightens security elsewhere

After last month’s major redesign, you’d be forgiven for thinking Firefox might take it easy with its latest update. But while there are no standout features to rival version 89’s facelift, Firefox 90 sports some notable new features and improvements to make the update a noteworthy one.
The Windows build gets particular attention with this new release. Firefox 90 introduces a new about:third-party page to help users identify compatibility problems caused by third-party modules and apps.
Most Commented Stories
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.