
The race against hackers to secure EV cyber-grid
The electric vehicle (EV) revolution is here. After decades of hype, EVs are finally starting to get their day in the sun. In the last ten years, plug-in hybrid electric vehicles have grown from 16,000 to over 2 million vehicles, and auto executives expect over 50 percent of US vehicles to be all-electric by 2030.
It is not hard to see why experts make such an optimistic prediction. In addition to the growing fleet of EVs, the Bipartisan Infrastructure Deal signed earlier this year will include $7.5 billion to help plan and build an extensive network of EV charging stations across the country, a task critical to ensuring full adoption of the technology. It took decades for the current network of gas stations to stretch from one end of the U.S. to the other, and a similar process is now underway for EV charging stations. An infrastructure project of this size requires thorough planning and significant investment, after all.

How technology can inspire teamwork and collaboration
The way we work is always evolving, and it makes sense that where and how we work would also change. Office working isn't for everyone and there is a lot more to consider than only your morning commute.
Enter collaborative technologies and with them, a boom in users per day by the millions. Companies are becoming more flexible and accessible to their employees and partners. It has become clear that maintaining an enjoyable working environment is crucial, even when workers are not sat within reach of each other.
The best free alternatives to Zoom -- with no time limits
For a while, Zoom was the darling of the video conferencing world, but a series of privacy and security issues -- although ultimately resolved -- knocked confidence in the platform. Many users hung on, though, with the free tier proving particularly popular.
But Zoom's recent, quiet announcement that one-on-one meetings are going to be subject to a 40-minute limit from May 2 means that a new batch of users is looking to jump ship and is on the lookout for a replacement. To help out, we've collected together a list of the best free Zoom alternatives that do not have a time limit on meetings (or at least not one that will impact on most usage scenarios).

Microsoft releases Windows 11 Build 22610 with new group policies and loads of fixes
There was no new build for Windows Insiders in the Dev Channel last week, and it looked as if we might not get one this week either, but at the death Microsoft releases a new build in time for the weekend.
Build 22610 introduces some new group policies for IT administrators, an update to the Family Safety Widget, and a large number of new fixes. However, it also introduces two known issues to be aware of.

Steam snap now available for Linux gamers
Today we get some very exciting news for the Linux gaming community. And yes, smart aleck, people do play video games on Linux these days. What is the big news? Canonical has released an early-access snap version of Steam for Ubuntu and other compatible Linux-based operating systems!
What exactly does this mean? Well, Canonical is aiming to make it even easier to get Steam up-and-running on Linux. Gamers will be able to install Valve's software from the snap store for a more elegant experience.

How has UK tech evolved to achieve such landmark success?
The past decade has been a period of sustained growth for the UK tech sector. But it has also seen the industry evolve remarkably -- something that has been apparent to those working within it.
It was reported only last month the sector had surpassed a milestone $1 trillion valuation, becoming only the third country to do so behind rival giants China and the US. Naturally, this puts the UK at the top of Europe’s digital food chain.
Best Windows apps this week
Four-hundred-eighty-eight in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Adoption of Windows 11 appears to have slowed down in the past two months according to recent usage statistics by third-parties.

The changing role of the CISO [Q&A]
Digital transformation, a shift to hybrid and remote working, and increasing regulatory pressure have seen major changes to the enterprise IT landscape in recent years.
CISOs have been at the heart of this, facing new challenges and taking on additional responsibilities. We spoke to Ben Smith, field CTO of NetWitness, to discuss these changes and find out what makes a good, or bad, CISO.

KB5012643 update is causing screen flickering for some Windows 11 users
Installing updates for Windows can often be something of a gamble, but this is particularly true when we're talking about the preview versions Microsoft makes available ahead of the monthly Patch Tuesday releases.
The latest problematic patch is the recently released KB5012643 update for Windows 11. Due for a wider release in May, Microsoft has already made a preview version available for those who like to get updated as soon as possible. But some people who have installed the update are reporting problems with flickering screens.

PATRIOT VIPER VENOM DDR5 6200MHz 32GB desktop RAM kits now available with and without RGB
When you are a computer-builder, there are peaks and valleys when it comes to excitement about PC components. What do I mean by this? Well, sometimes you are building machines with cutting edge parts as an early adopter, while other times you are using ho-hum components that have been around a while. For instance, we have been using DDR4 memory for about seven years now. It is time to move on.
Thankfully, the age of DDR5 is finally here. After dealing with DDR4 for so many years now, we will soon see many PCs with DDR5 memory inside. One of the companies leading this industry shift is PATRIOT, and today, that company begins selling the 6200MHz variants of its VIPER VENOM DDR5 32GB (16GB x2) RAM kits.

IT leaders say Log4Shell was a wake-up call for cloud security
The Log4Shell vulnerability proved to be one of the major cybersecurity events of last year and its repercussions continue to rumble on.
Research from network security platform Valtix shows 95 percent of IT leaders say Log4Shell was a wake up call for cloud security, changing it permanently, and 87 percent feel less confident about their cloud security now than they did before the incident.
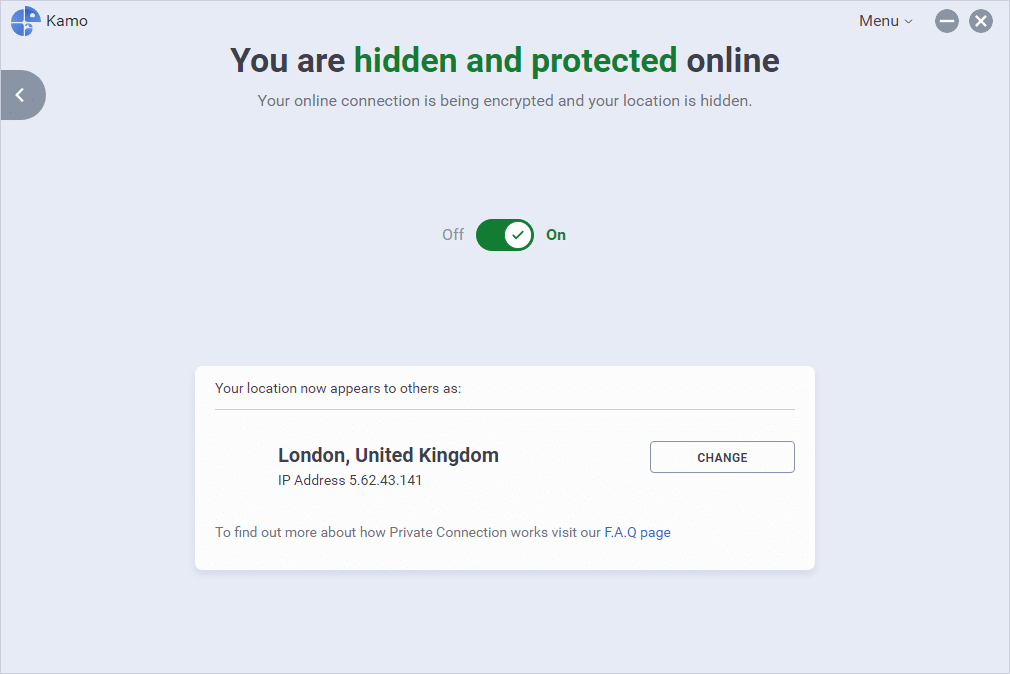
Kamo 4 adds VPN technology to block more online snoopers
Piriform Software, best-known for its CCleaner cleaning product for PCs and Macs, has released Kamo 4.0, a major new update to its Windows privacy tool.
Kamo 4.0, which blocks online trackers through a range of tools built into a single application, has added location masking through the implementation of a basic VPN, which masks the user’s IP address and exact geographic location via an encrypted connection through another server in their own country.

SEO techniques used to get users to trust phishing sites
Search engine optimization (SEO) is used to boost the ranking of websites by ensuring they offer quality content and a good user experience.
But new research from global threat intelligence firm Cybersixgill shows, perhaps not too surprisingly, that similar techniques are being exploited by threat actors to boost trust in their sites.

Get 'Linux for Networking Professionals' ($44.99 value) FREE for a limited time
As Linux continues to gain prominence, there has been a rise in network services being deployed on Linux for cost and flexibility reasons.
If you are a networking professional or an infrastructure engineer involved with networks, extensive knowledge of Linux networking is a must.
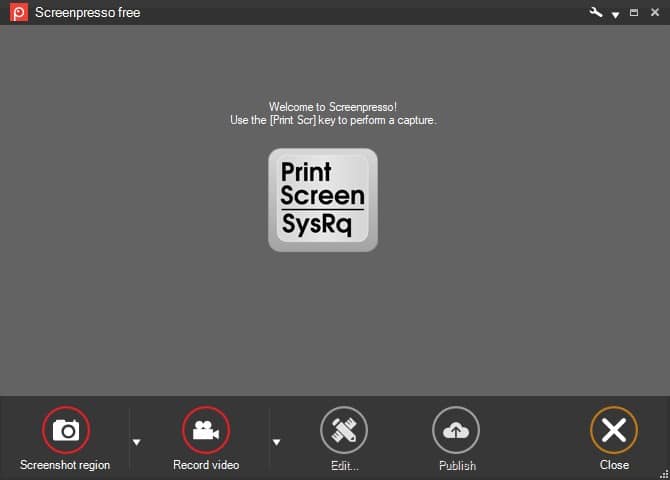
Screen grabbing utility Screenpresso 2.0 features improved video capture and better multi-monitor support
For some people, taking screen grabs is a simple matter of hitting Print Screen and pasting the contents of the clipboard into an image editor, while others with slightly greater needs may turn to Windows' Snipping Tool. While of these options are fine, they are both quite limited, and this is why the likes of Screenpresso remain important utilities.
For the uninitiated, Screenpresso is an advanced screen capture tool that makes it possible to take grabs of what you see on your screen -- but it includes a huge range of tools and options that make it stand out from the competition. The app can also be used to capture video footage, and with the release of Screenpresso 2.0.0 even more powerful special features help take your screen grabbing to the next level.



