
Insiders miss out as Microsoft keeps its cards close to its chest in build up to Windows 11 announcements
Will it be Windows 11, Windows 365, WindowsOS or simply "Windows" that Microsoft reveals later this month as the successor to Windows 10? There's money being wagered on Windows 11, but we'll just have to hold out to see not only what the name is going to be, but also what the operating system has in terms of new features, tools and aesthetics.
Ordinarily jumping on the latest Insider builds of Windows gives a great way to see into the future. Eager users can try out preview builds ahead of the official update releases, but sadly this will not be the case ahead of the next major version of Windows.
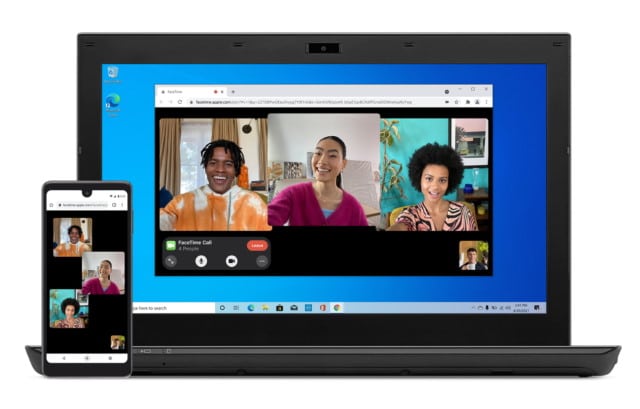
FaceTime on Windows, FaceTime on Android: it's happening
At the WWDC 2021 keynote yesterday there was quite a lot to take in, with Apple revealing details of iOS 15 and macOS Monterey. But there were other big reveals too, including the news that using FaceTime will soon be possible on non-Apple platforms.
In what many will see as something of a surprise move, Apple announced that FaceTime is coming to web browsers. This means that it will be possible to FaceTime from Windows and FaceTime from Android. No specific mention was made of Linux, but with a browser-based version of FaceTime in the pipeline, there's no reason to think this won't be possible.

Apple steals Microsoft's Windows 11 thunder with macOS Monterey unveil
Today at WWDC 2021, the folks at Apple talked. I mean, they talked a lot. Like, for nearly two hours, various Apple employees highlighted the company's plans for the future, including iOS 15 and iPadOS 15. While consumers are probably most excited about Apple's aforementioned mobile operating systems, other people (such as yours truly), are more intrigued by the newest version of the desktop OS. Called "Monterey," this once again looks to be the best macOS ever.
Despite Apple switching to its own ARM-based processors for the newest Mac computers, macOS Monterey will be compatible with Intel-based machines too. Notably, Shortcuts from iOS and iPadOS will be coming to Monterey. While Automator is still supported, it is unofficially on death-watch. Most interestingly, Apple is making it easier to work between iPhone, iPad, and Mac -- you can now do AirPlay to Mac and share your mouse and keyboard between devices with Universal Control.

Kodi 20 N's codename revealed, and you can install the first build of it now
Kodi 19 'Matrix' Final was released in February, followed by a bug fixing follow-up four weeks ago. If you’re already looking forward and wondering what the next iteration will bring we have news.
We can’t tell you what new features or changes to expect yet, but we can tell you what the next codename is.
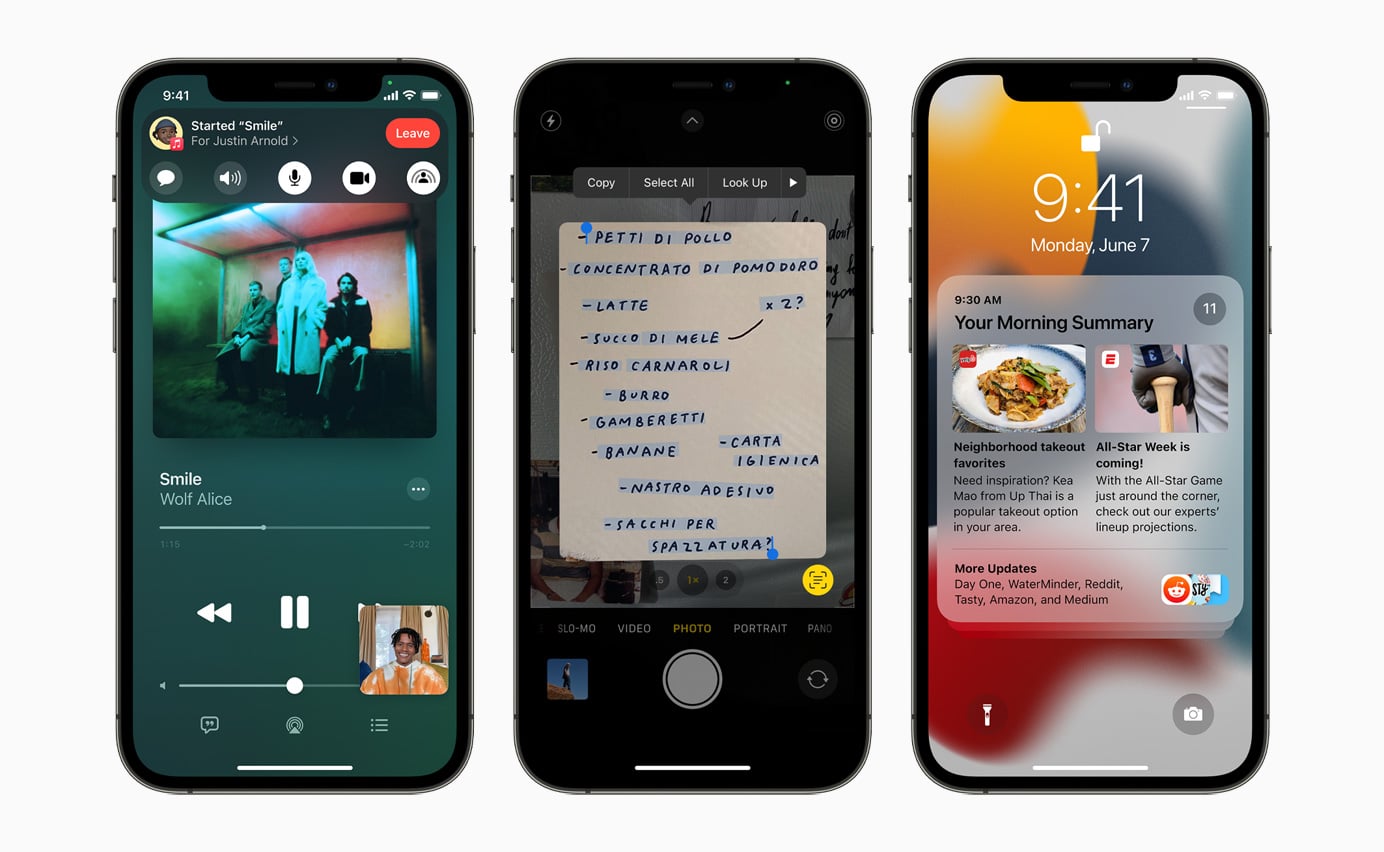
Apple iOS 15 promises loads of powerful new features
Apple’s WWDC started today and the tech giant had a lot of news covering iOS, iPadOS, macOS, watchOS and more.
For many non-developers, the big news is going to be the changes coming to the iPhone’s mobile operating system, and iOS 15 doesn’t disappoint.

Username and password breaches increase by 450 percent
A new report from identity specialist ForgeRock reveals a massive 450 percent surge in breaches containing usernames and passwords globally.
The report also finds that unauthorized access was the leading cause of breaches for the third consecutive year, increasing year-on-year for the past two years, and accounting for 43 percent of all breaches in 2020.
Watch Apple's WWDC 2021 keynote live here today
Today is a big day for Apple as it will be opening its yearly developer conference with a virtual keynote. As always there will be a lot of software news.
The focus will no doubt be on the latest versions of iOS, iPadOS, macOS and watchOS, but it’s likely new hardware will also be unveiled.

The challenges of securing the modern enterprise [Q&A]
In recent months there have been many high profile attacks using ransomware and other techniques, against businesses.
But why has there been an apparent upsurge in attacks and what should enterprises be doing to keep them selves safe? We talked to Lynx Software Technologies' vice president of product management, Pavan Singh to find out.

Microsoft will manually review all submissions to the Windows Package Manager (Winget) repository
Last week's official release of the final build of the Linux-style Windows Package Manager by Microsoft was met with great excitement from the community. But the company seems to have only belatedly spotted an issue with its Store alternative.
The problem is that the Windows Package Manager Manifest Creator tool makes it incredibly simple to submit new package to the repository. This has results in complaints that "people are submitting bad or duplicate manifests without checking if the app already exists or not"; Microsoft has come up with a vey hands-on solution.

How to verify your Apple AirTag has the new anti-stalker firmware
Apple AirTag is a very cool, albeit expensive, product. If you aren't familiar, it is a little battery-powered disc that is designed to track belongings. You can buy an accessory to turn it into a keychain, for instance, and then track your keys. As another example, you can buy a luggage tag accessory so you can track your bags when traveling. It is the dependence on accessories that makes the AirTag so expensive.
The problem, you see, is that not only can it be used to track things, but people too. Yes, creepy stalkers can secretly hide one of these AirTags inside something that belongs to another person and then track them. If the person being tracked has an iPhone, however, it will detect such behavior and warn them if it notices an AirTag (that they don't own) moving around with them.

Majority of consumers don't trust 'big tech' with their data
Only a third of consumers trust 'big tech' companies more with their data compared to smaller, independent or local companies according to a new study from API management platform Axway.
The study of over 1,000 US adults finds 82 percent of consumers wish they knew what specific data companies have collected about them, and they have concerns that their online data may not be secure.

The role of Information Technology in elevating customer experience
"Exceptional service" has always been a key customer demand over the years. But customers today expect more -- a combination of customized insights, connected interactions and an agile approach in addition to exceptional customer service. Therefore, while focusing on customer experience, communication and connection become highly crucial.
The recent pandemic and the process of businesses overcoming it have further brought to the spotlight the need for customer experience backed by flexible technology support and exceptional customer satisfaction, especially during adverse times. Information Technology (IT) has a significant role in providing the exceptional service and connected experience customers have always demanded.

Get 'Work Your Money, Not Your Life' ($19.95 value) FREE for a limited time
Studies show that if you're like the majority of young professionals, you feel dissatisfied with your job, your finances, or your overall station in life. It can seem impossible to disentangle the work stuff, the money stuff, and the personal stuff, because they're all inextricably linked.
But the good news is, you don't have to go at it alone: Work Your Money, Not Your Life is your all-in-one guide to achieving both your career and financial goals so that you can get where you want to be.
In his debut book, Roger Ma, an award-winning financial planner and a publisher strategist at Google, offers secrets on how you can craft a meaningful career, gain financial comfort, and achieve a greater sense of purpose.
Best Windows 10 apps this week
Four-hundred-forty-one in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft plans to reveal "the most significant update of Windows over the past decade" on June 24. Rumors suggest it could be the next version of Windows. Whether it will be named Windows 11, just Windows, or something else remains to be seen though.

Why enterprises need to prepare for more insider threats [Q&A]
Insider threats are a growing problem. In its 2021 predictions, Forrester believes that insider incidents will be the cause of 33 percent of data breaches in 2021, up from 25 percent in 2020.
But what does this mean in practical terms for businesses and how can they protect themselves? We spoke to Anurag Kahol, CTO of cloud security specialist Bitglass, to find out.



