
T-Mobile launches pre-orders of the Samsung Galaxy S7, adds bonuses
Samsung has recently unveiled its latest smartphone, the Galaxy S7, a follow-up in the same line the company has been producing for years now. Regardless of what you think of it, it's sure to be popular, and getting widespread adoption requires carriers to be on board.
One such carrier, T-Mobile, is trying to sweeten the deal in an effort to grab more customers. This involves the handing out of bonuses and there are several to be had if you pre-order this latest handset.

How to improve security in a BYOD enterprise environment
For most of us, our mobile and personal devices have become extensions of our lives and even bodies. Most of us carry our smartphones with us all the time, and when we can’t find them, we feel lost.
We are essentially always on, always connected to the Internet. This notion of anytime, anywhere access has extended not only to our personal lives but also our professional.

Five not so obvious things you can expect at MWC 2016
At Mobile World Congress (MWC) tides will start to turn. There won’t be an overnight revolution powered by shiny new gadgets, but technologies we’ve seen evolving over recent years will start to demonstrate their real potential.
We expect to see five major technology themes come to the fore in Barcelona this year:

Opera claims you're using 30 percent of your mobile data on background apps
Mobile data these days comes at a premium. Carriers charge what could be considered ridiculous amounts for it and many customers burn through it. Unless you're predominantly on Wi-Fi then you're likely wondering where all of that data is going.
The answer, of course, is background apps -- programs that run all the time without the user realizing it. These can eat up tremendous amounts of a monthly allotment.

Mobile operator Three to block ads at the network level
Ad blocking has been going on for years, but it’s risen in popularity a lot lately, thanks in part to Apple allowing ad blockers into the App Store. Popular content blocker Adblock Plus has been having conversations with advertisers recently too and is looking to discover just why people block ads on the web.
In an interesting move, mobile network operator Three has announced that it will be using ad blocking technology created by Israeli startup Shine to block adverts on a network level.
Twitter makes it easier to annoy your followers with GIFs
GIFs are, sadly, here to stay. We've come a (relatively) long way since the days of animated GIF adverts that adorned countless web pages through the 90s, but the animated image format is still highly divisive -- and I'm not just talking about whether it is pronounced with a hard or soft G sound.
Some people loathe GIFs with a passion that knows no bounds, while for others they are the perfect means of communication. If you fall into the latter camp, Twitter has some good news for you -- a 'GIF search' button is making its way to the web, as well as the iOS and Android apps.

Canonical announces premium Linux-powered Meizu PRO 5 Ubuntu Edition smartphone
While I love iOS when it comes to mobile devices, Linux is my true love on the desktop. Android used to be my choice for mobile, but I jumped ship due to scary exploits and untimely (or nonexistent) OS updates. Linux should be synonymous with security, but Google's mobile OS has tainted that, sending me into Apple's loving arms.
Luckily, Google is not the only Linux player with mobile -- Canonical is still moving ahead with Ubuntu. True, it is a long shot to ever meet or exceed iOS or Android in market share, but fans of Linux and other open source software should pay attention. Today, Canonical announces the Meizu PRO 5 Ubuntu Edition -- a premium and luxurious smartphone.

What you need to know about biometric security
Generally speaking, biometrics refers to the measure or statistical analysis of a person’s physical or biological characteristics. However, increasingly the term is being defined more narrowly, at least in a business context, to refer to biometric security.
Although passwords can be guessed and network vulnerabilities exploited, overcoming biometric security protocols is significantly more challenging. For example, how would a cybercriminal go about duplicating a fingerprint or an iris scan? As a result, the unique aspects that make up our physical features are increasingly being utilized for authentication methods by businesses all over the world.

Kids and handheld tech -- to have and to 'PLEASE hold'
Technology to previous generations involved radio, TV, record players and perhaps even 8-track tape players, but today's youth have smartphones and tablets and are connected all of the time. Messaging apps have replaced phone calls and social interaction takes place via the internet.
On the heels of the gift-giving season, which likely featured a few iPads and the like, Logitech has looked into the prospect of young children with these devices. The survey includes both US and UK parents.
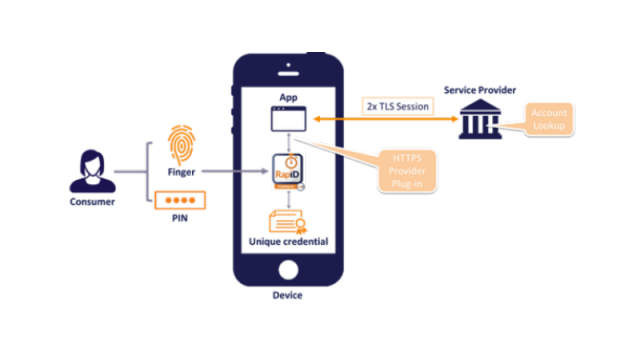
Security solution RapID wants to kill the password
At a time where cyber security is infiltrating the consciousness of consumers and businesses alike, finding the right balance between security and convenience has never been more important.
To that end, digital identity and credentials firm Intercede has launched RapID, a new security solution that delivers password and token free access to cloud services from mobile applications.

Installing apps at the weekend? You're probably using iOS
Companies looking to market to mobile users rely on being able to reach users at the times and places when they're most receptive.
A new report from mobile advertising company AppsFlyer looks at the behavior of app users and how it differs between operating systems and around the world.

Majority of UK shoppers prefer mobile devices
Shopping via mobile phones is now the default in the UK, a new research by market intelligence company SimilarWeb suggests.
According to the research, 64.54 percent of all website visits, by UK shoppers to retailers, was made via a mobile device this year. With these figures, the UK has now surpassed the US (55 percent), Germany (43 percent) and France (35 percent). It is still, however, lagging behind India, a country with 65 percent of mobile shoppers.

Facebook irks devs by shutting Parse mobile development platform
Facebook is closing down Parse, its mobile development platform, just three years after acquiring it for $85 million. The shutdown comes as something of a surprise as it is not long since Facebook was talking about using Parse to make giant steps into the Internet of Things.
But it seems that Facebook's IoT future is going to be one that is Parse-free. The shutdown will take place over the course of the next year, but starts with immediate effect. As of right now Parse is in wind-down mode, and will be fully shuttered by January 28, 2017. Believed to power tens of thousands of mobile apps, the killing of Parse will see Facebook diverting funds to other ventures.

What you need to know about mobile device management
The way in which we work has changed significantly in recent times. It was not that long ago that your standard office job meant being tethered to your desk from nine to five, glued to your PC screen. The rise of smartphones and web apps, however, have disrupted these traditional ways of working, granting employees more freedom than ever before. But this new mobile workforce also poses challenges for the modern business, particularly regarding security.
Of course, organizations cannot afford to restrict workplace mobility, as this would see them overtaken by a more flexible and innovative competitor. Therefore, businesses are tasked with enabling mobility without introducing vulnerabilities into the workplace -- which is where mobile device management comes in.

Where's my phone? A couple in Atlanta don't have it
Smartphones are a hot commodity, meaning thieves want them, but they are also relatively small and easily lost or forgotten. There's an app for that. Well, several apps in fact. Creating ways to find misplaced or stolen phones has become a cottage industry, but these products have limitations.
Locating a device isn't an exact science. It's more just narrowing down an area and then making it a guessing game through triangulation via cell towers -- although using GPS works rather better.
