Wikimedia secures connections with HTTPS encryption by default
There is a movement calling for the encryption of all web traffic. The cause of this could be laid at Edward Snowden's door, but there's no getting away from the fact that in recent years there is an increased interest in security and privacy. To this end, Wikimedia has announced that it is now using HTTPS to encrypt all of its traffic -- including that to Wikipedia.
We've already seen the US government embrace HTTPS, and companies like Google and Facebook are making it easier to control privacy settings. Apple has hit out at companies that fail to do enough to protect users' privacy, and Wiki media is taking the extra step of also implementing HSTS, just days after Microsoft announced that this would be supported by Internet Explorer 11 under Windows 7 and 8.1.

Amazon publishes opaque transparency report
Post-Snowden there is great interest in just what involvement the government has with technology firms. There are frequent requests from government agencies for information about users and the likes of Google, Snapchat, and even the NSA itself have all released transparency reports that reveal, in broad strokes, the number of requests for data they have received.
Amazon is the latest company to release a transparency report -- although the term really should be used in the loosest possible sense. The report includes scant details about the number of subpoenas, search warrants, court orders, and national security requests received in the first five months of 2015. The report is so vague as to be virtually meaningless.

Reddit starts killing off harassment subreddits
Reddit is both famous and infamous. It's a source of news, a platform for disseminating such delights as the pictures that came out of the Fappening, and home to the ever-interesting Ask Me Anything sessions. But like any social website, it also has problems. Like Facebook, Twitter, and other sites, there are issues with spam, trolling, and abuse. Reddit has a particular problem with sections that are dedicated to harassing and abusing groups of people.
Now the site is fighting back. It is taking a proactive approach and removing subreddits whose raisons d'être are the harassment of people. The cull initially sees the removal of five offending subreddits, but the Reddit team explains that only one with a sizeable userbase is affected -- r/fatpeoplehate.
Twitter's block lists make it easier to avoid trolls and spam
You don’t have to be following too many accounts on Twitter for it to become overwhelming; there is an incredible amount of data created every minute. To make things more manageable, lists make it possible to organize content into different categories so it can be quickly filtered. Today Twitter announces an extension of the lists concept that can be used to tackle spam and trolling.
It is now possible to not only create lists of accounts you would like to block (so you are invisible to them), but also share these block list with others. It's a technique that has already been implemented by some third party Twitter clients, but it is now officially supported. Privacy and abuse have long been issues for Twitter, and this is just the latest move to try to tackle the problem.

Apple hits Google where it hurts
I have some advice for the European Union Competition Commission: Lay off. You don't need to reign in the Google monopoly. Apple will correct the market around search and mobile. That's one of two related takeaways from Monday's WWDC 2015 keynote. iOS 9 and OS X El Capitan up Apple's push into search and proactively-delivered information in big ways. That is if delivery is as good as the company promises.
The other takeaway harkens back to what I told you last week about Tim Cook's piracy rant against unnamed Facebook and Google alongside the friggin U.S. government -- plural if thinking beyond the Feds: It's BS marketing. Apple prepares a major competitive assault against Big G, hitting where damage can be severe: Perception and profits. I cannot overstate Google's vulnerability, which ironically is where the search and information giant exploited Microsoft during this Century.

Internet users are powerless to protect their privacy, and they know it
A paper produced by a team at the University of Pennsylvania confirms something many people have probably thought true for some time: the notion that internet users are unhappy with the way their privacy is undermined by advertisers and online companies, yet feel there is nothing they can do about it.
While marketing companies like to present an image of customers who are happy to hand over personal information in return for certain benefits, the truth is rather different. Rather than dedicating time and energy to trying to stop personal data from being exploited, people are instead taking it on the chin and accepting it as part and parcel of modern, online life. It's just the way things are.

PayPal angers consumers with telemarketing agreement
Anyone who’s ever received an automated PPI spam phone call will know that receiving pre-recorded messages, often which have no relevance to you whatsoever, can be very annoying. In fact, unwanted telemarketing of any kind can be a real turn-off for consumers, which is why many people are disappointed by recent changes to PayPal’s terms of service.
The company website lists the new agreement clearly and suggests that customers could soon be receiving a lot more unsolicited calls and texts from not only PayPal, but its affiliated businesses too.

20,000 London police officers will wear body cameras
Police in London are about to be equipped with 20,000 cameras on their bodies, together with tablet computers, improved computer systems and 999 text messages.
No, of course a single police officer won’t be wearing all 20,000 of them.

Millions of US government workers’ records exposed by data breach
The US government has been hit by a massive data breach at the department which handles government employee records, the Office of Personnel Management (OPM). According to officials this has the potential to affect every federal agency.
The Reuters news agency says that it's been told by a US law enforcement source that a "foreign entity or government" was believed to be behind the attack. Suspicion has fallen on China although Chinese foreign ministry spokesman Hong Lei said the accusations were, "irresponsible and unscientific".

Tim Cook is an opportunist
Nine years ago, a NPR interviewer asked me about Google and other U.S. companies censoring search results in China. The question was one of morality -- to which I gave answer she didn't expect. That response, or my recollection of it, is appropriate for rather ridiculous and self-serving statements that Apple CEO Tim Cook reportedly made two days ago.
"We believe that people have a fundamental right to privacy", Cook said, Matthew Panzarino reports for TechCrunch. "The American people demand it, the constitution demands it, morality demands it". Oh? What is moral? The answer I gave NPR in 2006 applies: There is no moral high ground in business. The high ground is quagmire, because all public companies -- Apple surely among them -- share a single, moral objective: Make profits for stockholders. Plain, pure, and simple.
Tim Cook lashes out at the government, Facebook and Google over privacy
We live in an age where people are more concerned about and more aware of privacy issues than ever before. Speaking at EPIC Champions of Freedom event in Washington, DC, Apple CEO Tim Cook criticized the government for seeking to implement backdoors into encryption techniques. He also hit out at Google and Facebook with their ad-dependant business models for infringing upon privacy.
He said that Apple wants to be different, saying: "We believe that people have a fundamental right to privacy. The American people demand it, the constitution demands it, morality demands it". Cook was at pains to stress that Apple should be viewed differently to other companies, assuring people that -- unlike others -- the company "doesn’t want your data".

USA Freedom Act passes unamended, limiting NSA surveillance after Snowden revelations
Today the US Senate passed the USA Freedom Act without amendments, signalling the start of the significant surveillance reform that has been called for since Edward Snowden blew the whistle on the agency's activities. It had already been determined that the bulk collection of phone metadata was illegal, and the expiry of Section 215 of the Patriot Act at the end of May brought this data collection to an end anyway.
The USA Freedom Act sets in concrete the end of the phone data collection program and is seen as a major victory for privacy advocates. It will come as good news to Snowden himself who will undoubtedly feel a sense of relief that his risk-taking paid off. The bill is still to be signed into law by President Obama, but this is now little more than a formality.

Facebook adds support for OpenPGP email encryption
Facebook can send out quite a lot of emails to its users in the course of an average day. Notifications can fly in thick and fast letting you know about friend requests, replies to your posts, messages from contacts, and the like, and it's possible -- nay likely -- that these will contain delicate personal information.
To help calm the fear of those with privacy concerns ("why are they using Facebook?", you might well ask) Facebook today announces the introduction of OpenPGP encryption support. This gives users the opportunity to protect communication from Facebook by encrypting it so it cannot be read by unauthorized parties.

Google makes it easier to control privacy and security settings
Taking a leaf out of Facebook's, er, book, Google today unveils a revamped privacy checkup page. Google and privacy are not words that belong in the same sentence for many people, but the search giant wants to change that. Users are invited to answer a series of simple questions to control how their data is stored, collected, and shared.
The company wants to place users back in control, and at the heart of today's announcement is the My Account page which is now central to configuring privacy settings. In the interests of transparency, Google has also set up a page dedicated to revealing how and why data is collected.
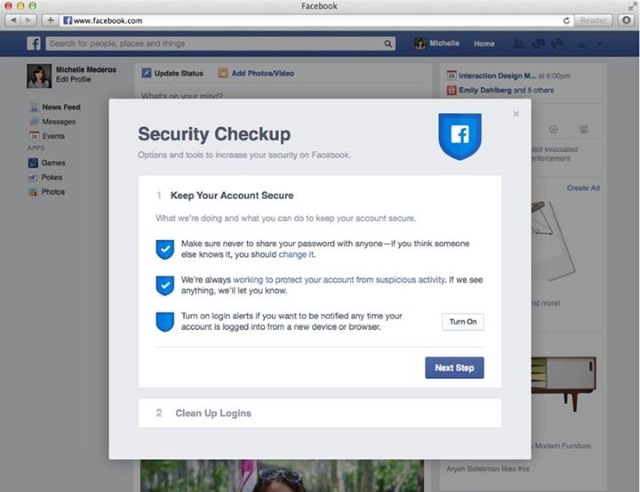
Facebook ups the ante with new Security Checkup tool
Security and Facebook are not words that generally sit well together. This is something that the social network is only too aware of, and in recent years has taken various steps to try to improve the security and privacy of individuals' accounts. The latest tool in its arsenal is the new Security Checkup.
At the moment the tool is not being made available to everyone, but those who have been chosen to test drive it will be able to use simple on-screen prompts to change their password, turn on login alerts, and clean up login sessions, all from one handy location.
