Microsoft to make Sysmon a native Windows 11 tool

Windows 11 power users will be pleased to learn that Microsoft is planning to bring the Sysmon (System Monitor) tool to Windows as a native utility. Usually part of the Sysinternals suite of utilities, Sysmon will be integrated into not only Windows 11, but also Windows Server 2025 starting next year.
The announcement was made not by Microsoft, but by Sysinternals creator Mark Russinovich. He says that by integrating the Sysmon utility into Windows, administrators will simplify deployment and bring additional functionality.
Google to use Android developer verification to allow safe app sideloading

Like Apple, Google has gradually made it more difficult to install apps from outside its own store. But the company is aware that neither users nor developers necessarily want to be tied to just the Play Store – this is why it has come up with the Android developer verification program.
The idea is that Google will check and verify developers so the users know they can be trusted. Now the company has an update based on early feedback it has received.
Microsoft is killing off Defender Application Guard for Office

More than a year-and-a-half after announcing its retirement, Microsoft has revealed its plans to fully remove Defender Application Guard from Office.
The journey has been a long a slow one for the this security feature which isolates untrusted Office documents in a virtualized contained. Deprecation was first announced way back in November 2023, and the process of complete removal will not be finished until the end of 2027.
ESET brings its ransomware protection to home and small business users

ESET has added new ransomware recovery and scam protection capabilities to its consumer and small business products. The security firm's latest offerings, ESET HOME Security and ESET Small Business Security, bring its enterprise-grade Ransomware Remediation feature to homes and small offices for the first time.
Ransomware incidents remain among the most damaging forms of cybercrime worldwide. ESET’s Ransomware Remediation system automatically creates encrypted backups when a threat is detected, so that users can restore any affected files once the attack has been neutralized, hopefully minimizing downtime and data loss.
Get ready to reserve your WhatsApp username
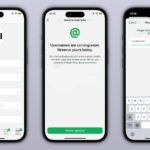
It has been known for a little while that Meta has been working on a username system for WhatsApp. The popular messaging app is slightly unusual in not offering people a way to choose a username, but this is going to change at some point in the future.
Recent beta builds of the iOS and Android apps show that work is gathering paced, and the most recent development is a username reservation system. This will serve as a way for users to try to pre-select their preferred username even before the username system rolls out to everyone.
Mozilla commits to updating Firefox on Windows 10

Microsoft may have all but abandoned Windows 10, but this is not true of its users. There are still millions of Windows 10 systems in use around the world, causing security concerns for many. But not all software developers are turning their backs on Windows 10 – Mozilla included.
The company has announced that “Firefox will continue to support Windows 10 for the foreseeable future”.
Microsoft restrains IE Mode access in Edge because of abuse

The impact of Internet Explorer is still being felt years after the world moved on from the web browser. Microsoft has announced that it is “Restraining IE Mode Access” in Microsoft Edge, citing concerns about exploitation of 0day vulnerabilities in Internet Explorer’s JavaScript engine.
That Internet Explorer continues to live on in Edge remains astonishing to many, but it has been retained for compatibility issues. Nonetheless, Microsoft is now taking steps to plug holes that have enabled threat actors to gain access to devices.
Apple doubles its top bug bounty payout to $2 million

Five years after it was launched, Apple has announced major changes to its bug bounty program. The Apple Security Bounty program is entering what the company describes as a “new chapter”, and the headline change is a massive boost to the payments made for the discovery of the most serious types of security issues.
In addition to this and other changes, Apple also reveals that it has paid out over $35 million to more than 800 security researchers since the scheme launched in 2020. The company points out that many of these payouts were for $500,000. But the focus here is what is happening in the future.
SonicWall warns its cloud backup service users to reset credential after security incident
Following a previously acknowledged security breach last month, SonicWall has published an updated bulletin to customers having investigated the incident. The company says that it is now aware that an “unauthorized party accessed firewall configuration backup files for all customers who have used SonicWall’s cloud backup service”.
SonicWall has also published an extensive document to help customers with “containment, remediation and monitoring”. This includes advising everyone to reset various passwords.
Malwarebytes shifts to people-based protection with new security plans

Malwarebytes has introduced a new range of security packages designed to protect individuals and families based on the number of people in a household rather than the number of devices.
Malwarebytes says its research shows most users now own at least two devices, often including a smartphone, increasing the number of potential entry points for cybercriminals.
Microsoft and Valve issue warning to gamers about Unity vulnerability

Both Microsoft and Valve have issued warnings about flaws in the Unity engine that could expose gamers to attack. A new version of Steam has been released to plug the security hole as well.
Tracked as CVE-2025-59489, the Unity Gaming Engine Editor vulnerability has a severity rating of 8.4. The nature of Unity is such that the flaw affects multiple platforms – Windows, Linux, macOS and Android. There is good news for some, however; Xbox consoles, Xbox Cloud Gaming, iOS and HoloLens all remain unaffected.
The Red Hat data breach is worse than first thought

The situation regarding Red Hat’s recent data breach is worsening – both for the company and for its customers. With GitLab instances belonging to the company having been breached by the Crimson Collective, hundreds of gigabytes of data were stolen.
Now the data breach has transformed into a demand for ransom – perhaps predictably. Interestingly, though, the extortion is not being perpetrated by the Crimson Collective, but by ShinyHunters.
Oracle releases emergency patch to address Cl0p data theft attacks in E-Business Suite

Oracle has released an emergency patch and an urgent security warning about a 0-day vulnerability in Oracle E-Business Suite.
Tracked as CVE-2025-61882, the security flaw has a severity rating of 9.8 and is described as an “easily exploitable vulnerability”. Oracle warns that the vulnerability is “remotely exploitable without authentication”, going some way to explaining why it is seen as being so serious an issue.
Discord admits customer data theft after third-party security breach

The personal data of Discord users has been exposed after a third-party customer service provider suffered a data breach.
Hackers were able to obtain support tickets from an unnamed company used by Discord to provide support. From this, they were then able to gain access to data including names and government-issued IDs.
Perplexity releases AI web browser, Comet, for free; security warnings follow

Perplexity is the latest company to release an AI-powered web browser. Comet is available free of charge for Windows and macOS, and it is looking to compete with the likes of Opera’s Neon.
Comet is not brand new. It launches in July to a limited audience, but now its AI powers are being made available to everyone. But while there is much excitement from Perplexity about the launch, and excitement from users, there is also a warning from security experts.
Recent Headlines
Most Commented Stories
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.