
Privacy: Cloudflare brings its DNS switching tool 1.1.1.1 to iOS and Android
Cloudflare has just made it a whole lot easier to hide your mobile browsing from your ISP -- and access content that might otherwise be unavailable. The company has launched a 1.1.1.1 app for smartphone users, making it incredibly easy to switch between DNS services with a couple of taps; what amounts to a free VPN tool.
Earlier in the year, Cloudflare launched its 1.1.1.1 DNS service to bring privacy and speed, but it was a little off-putting to users unfamiliar with tinkering with such settings. With the launch of 1.1.1.1 for iOS and Android, the process is much, much simpler -- and the app and the service itself are free.

95 percent of IT security professionals underestimate phishing risks
A new survey of cybersecurity decision-makers shows that most companies lack adequate safeguards against phishing threats and many don't fully understand the risks or how widespread the threat is.
The survey from phishing site detection company SlashNext reveals that 95 percent of respondents underestimate how frequently phishing is used at the start of attacks to successfully breach enterprise networks.

Number of data breaches falls but 2018 is still set to be the second worst year on record
In the final quarter of 2018, the number of reported breaches is down by eight percent and the number of exposed records is down around 49 percent, from seven billion in 2017.
The latest Data Breach QuickView report from Risk Based Security shows that seven breaches exposed 100 million or more records with the 10 largest breaches accounting for 84.5 percent of the records exposed this year to date.

Exploit developer discovers security vulnerability in VirtualBox and publishes a full guide to exploiting it
A security researcher has not only discovered a vulnerability in the virtualization tool VirtualBox, but has released details of the exploit and a step-by-step guide to the zero-day vulnerability.
Russian exploit developer Sergey Zelenyuk found a way to break out of VirtualBox's virtual environment and he chose to go public with the vulnerability because of his displeasure at the "contemporary state of infosec, especially of security research and bug bounty". Having told Oracle about the problem, he also tired of the "delusion of grandeur and marketing bullshit" he experienced in the infosec community.

Continuous authentication helps boost behavioral analytics
In a move to better protect accounts, banks, retailers and service providers are increasingly looking to methods of authentication beyond the password.
Behavioral analytics specialist BehavioSec is launching an updated version of its platform, allowing it to detect the suspicious use of attack obfuscation techniques, including the use of VPNs and TOR-routed traffic during login attempts and sessions.

Enterprises face more than 100 critical vulnerabilities per day
Enterprises identify 870 unique vulnerabilities on their systems every day, on average. Of those, more than 100 are rated as critical on the common vulnerability scoring system (CVSS) according to a new report.
The Vulnerability Intelligence Report from cyber risk company Tenable is based on analysis of anonymized data from 900,000 vulnerability assessments across 2,100 enterprises.

Apricorn Aegis Secure Key 3NX: An ultra-secure 256-bit AES XTS hardware-encrypted USB flash drive [Review]
Storing files in the cloud means they are easily accessible from anywhere, but if you have private data that you can’t afford to fall into the wrong hands, this might not be the best option for you, especially given the number of data breaches we see on a regular basis.
An alternative option is to carry those files with you on a USB flash drive, protecting them with encryption. While software encryption methods are better than nothing, a hardware encrypted solution, like the Aegis Secure Key 3NX, is a much more advisable choice.

Consumers still reuse passwords despite knowing the risks
Despite almost half of US consumers (49 percent) believing their security habits make them vulnerable to information fraud or identity theft, 51 percent admit to reusing passwords and PINs across multiple accounts.
According to a new fraud awareness survey by information destruction company Shred-it, 39 percent of consumers have been a victim of fraud or identity theft, and 27 percent admit that they don't know how to find out if they've become a victim.

Pssst... Wanna buy a digital identity? Only $50
Ever wondered how much your life might be worth? If we're talking about the digital world then the answer might be, 'not very much.'
Cybercriminals could sell your complete digital life, including social media accounts, banking details, app data, gaming accounts, and even remote access to servers or desktops, for as little as $50.
Exploit developers claim 'we just broke Edge'
Security researchers claim to have unearthed a zero-day vulnerability in Microsoft Edge. The remote code execution is due to be revealed with a proof-of concept.
Microsoft has not yet been informed about the details of the security issue, but exploit developers had been looking for a way to break Edge out of its sandbox -- and it would appear that this objective has now been achieved.

A new approach to data protection at the edge [Q&A]
Given the increase in both frequency and complexity of cyberattacks today, it's no surprise that security is coming to the forefront across industries.
While people often view cybersecurity as hackers trying to steal data, threats can impact more than just traditional data loss. With new technologies like edge computing emerging, we need to start thinking about protecting physical infrastructure in addition to data at the edge.
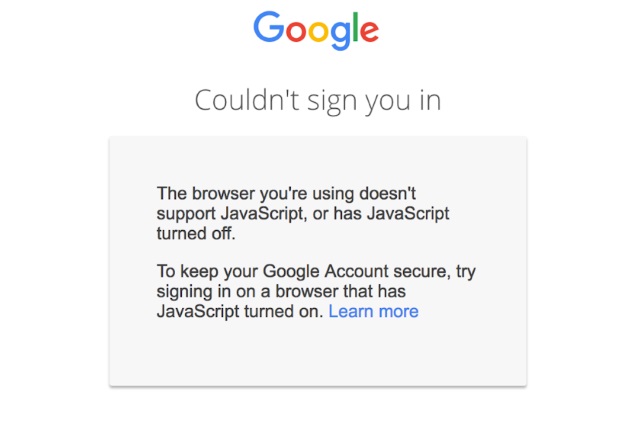
Now you need JavaScript enabled to log into your Google account securely
Google has made a change to its account sign in process that means you now have to have JavaScript enabled.
The change, which has been introduced for Cybersecurity Awareness Month, is part of a security process which Google says protects you "before you even sign in". While the vast majority of people will have JavaScript enabled, the new policy will still affect a number of users.

Microsoft and Amazon most impersonated in email attacks
Nearly two-thirds of all advanced email attacks used emails impersonating Microsoft or Amazon, according to new research by Agari, the email protection specialist.
Microsoft was impersonated in 36 percent of all display name impersonation attacks in the third quarter. Amazon was the second most commonly impersonated company, used in 27 percent of these attacks.

New monitoring tool checks the dark web for stolen credentials
Stolen login details are highly prized by cybercriminals, whether they are used to penetrate corporate networks or to make extortion emails look more convincing.
But often breached companies are slow to let users know their credentials have been stolen. This has begun to change in Europe thanks to GDPR, but in the US there is, as yet, no federal law regulating what companies must do if their users' information is stolen or compromised.

Cyberattacks on energy and utility companies increase
Attacks on infrastructure and energy companies are increasing, but they are occurring inside enterprise IT networks, not directly in the critical infrastructure, according to a new report.
AI powered attack detection specialist Vectra finds attackers typically gain a foothold in energy and utilities networks by staging malware and spear-phishing to steal administrative credentials.
