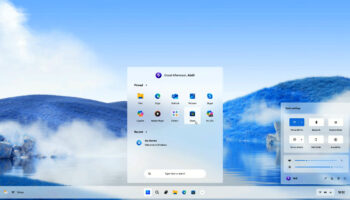
Taking enterprise security to the next level with two-factor authentication

Two-factor authentication (2FA) has been about for much longer than you think. For a decade or more we have been used to being issued with a card reader (in essence a hardware token device) to use with our bank card and Personal Identification Number (PIN) when looking to complete our internet banking transactions.
2FA technology has also, over the past years, been employed by seven of the ten largest social networking sites (including Facebook, Twitter and LinkedIn) as their authentication measure of choice.
Amazon unveils new hybrid drone prototype for 30-minute Prime Air deliveries

When you make an impulse purchase -- or you're just an impatient type -- time is of the essence. Next day delivery is far too slow, and same-day delivery has gradually spread to certain places. Some cities have the option of delivery within the hour, but Amazon is working on cutting this down to as little as 30 minutes with Prime Air.
As you would probably expect, these super-speedy deliveries will be facilitated by drones, and Amazon has unveiled a new prototype drone that blends elements of a helicopter with those of an airplane. Unlike other drones we’ve seen the Prime Air model is quite large, and is capable of carrying up to 5 pounds.
How to: Find your misplaced phone with Amazon Echo and IFTTT

Amazon just recently introduced support for IFTTT (If This Then That) to its Echo product. The company is pushing fairly hard to add functionality to its device. On a regular basis you will find a new addition at the top of the app when you fire it up on your phone or tablet.
With the introduction of IFTTT Triggers Alexa can now do even more. There are a number of recipes to choose from, but setting them up, in most cases, is pretty similar. Many involve your phone so be prepared to turn your number over, though neither entities have given reason for mistrust.
NSA stops bulk collection of phone metadata

The NSA's bulk surveillance and collection of phone data has come to an end. President Obama announced that the current surveillance program would stop by 11:59 pm EST Saturday, but this does not mean that phone surveillance has completely disappeared.
Instead of wide scale dredging of data, the NSA will now engage in more targeted surveillance programs -- something that privacy advocates have been calling for for some time. The scaling back of surveillance has not come out of the blue; it's became of a legal requirement earlier in the year that has now been implemented two and half years after Edward Snowden blew the whistle on NSA spying.
Google to work with Israel to censor Palestinian YouTube videos [UPDATED]

Coverage of any conflict is rarely free from bias, with propaganda being a staple tool. This certainly rings true of the war between Israel and Palestine, and Israeli Deputy Foreign Minister has engaged in talks with representatives of YouTube and Google with a view to censoring videos coming out of the region.
Tzipi Hotovely met with Google's Director of Public Policy, Jennifer Oztzistzki, and YouTube CEO Susan Wojcicki. On the agenda was discussion about how to censor Palestinian video footage deemed to be "inflammatory" or "inciting violence and terrorism" by Tel Aviv.
Holiday 2015 Gift Guide: Smartphones

If you're smartphone shopping this holiday and wondering what to buy, my primer can assist—with caveats. I focus solely on Androids that are higher end but affordable, and I ignore iPhones. No slight against Apple devices is intended. I figure that people who want an iPhone won't likely consider an alternative. Also: The differences aren't as pronounced. For example, the major benefit choosing 6s or 6s Plus over the two previous models is slightly lower price (3D Touch is an unnecessary gimmick). The major benefit picking 5s over the 6 or 6 Plus is again price but also smaller size.
Among Androids, differences abound—and many, such as older OS versions or custom UI skins, are carrier or manufacturer imposed. That's without considering the bloatware that either or both parties might impose. I intentionally focus on devices that offer the most value for price paid, which includes upfront or payment-plan purchased unlocked.
Amazon Echo introduces IFTTT trigger phrases

Amazon Echo continues to gain functionality, utilizing music apps like Pandora, TuneIn and Last.fm, as well as, of course, Amazon Prime music. There's also a growing list of home automation integration which allows customers to control devices by voice. You can even control your second-generation Fire TV -- first-generation is coming soon, or so Amazon has told me.
Now the company is introducing trigger phrases for IFTTT events and it also works into the home integration slant, though there can be other uses.
Is home automation in your future or are you using it now?

Home automation gets touted by some as the future, but it's really the now. A seemingly endless list of products are on the market and they allow the user to lock doors, turn lights on and off, open and close shades, there's even a crockpot that can be turned on and off from anywhere.
For a while now I have been controlling some lights with Amazon Echo. It's mostly good, but every once in a while the hub between Alexa and the bulbs needs to be reset. I've also been using the Mivatek Smart Plug to control another light. Therein lies the problem -- a lack of these things working together. Most are trying to, but the integration isn't there yet.
FSS ePub Reader silently installs adware?

FreeSmartSoft is the developer of a range of popular Windows freeware, including FSS Video Downloader, FSS Google Books Downloader, FSS ePub Reader and more.
You’ve installed one of their packages before? Then beware: we’ve discovered they have a mechanism that can silently install adware on a user’s PC.
Security breaches don't lead to a change in IT policy

A survey conducted by training company QA, reveals that eight out of ten (81 percent) UK IT decision makers experienced some sort of data or cyber security breach in their organization in 2015. Sixty-six percent said that the breach had led to a loss of data, 45 percent said that it had resulted in a loss of revenue, and 42 percent said that it had resulted in a PR nightmare for the business.
Despite this, however, less than a third (27 percent) plan to invest in cyber security technologies next year. It would also appear that not all organizations have learnt from their experience, with less than half (43 percent) of IT decision makers saying that the breach had not resulted in a change of policy and procedure.
VTech Learning Lodge hacked! Your child's identity could be at risk

When a company gets hacked, and its data is breached, it is hardly news anymore. What I mean is, it is so prevalent nowadays, that we are becoming desensitized to it. I personally received a letter regarding the OPM hack today -- yes, I am apparently a victim. If I can't trust the government to secure my data, who the hell can I trust?
Today, yet another company experiences a breach -- VTech. What makes this hack particularly devious and upsetting, is that children are impacted. Sadly, the company's "Learning Lodge", an online digital store for kids, has been compromised by evil-doers. Your child will now get a strong dose of reality -- nothing is safe online, and now their identities are at risk.
Samsung's first 128 GB DDR4 RAM modules for servers go into production

Samsung has announced that it is starting mass production of the industry’s first "through silicon via" (TSV) 128GB DDR4 memory modules for high-end enterprise and data centre servers.
This news follows on from its successful introduction of the 64GB 3D TSV DDR4 DRAM last year, which was an industry first.
Lenovo fixes two security vulnerabilities in its preloaded Windows tools

Lenovo has issued a patch which fixes vulnerabilities located in the software which comes preloaded with some of the laptops it sells.
The company recently released version 5.07.0019 of Lenovo System Update. This tool is made to keep the BIOS and drivers updated, previously called ThinkVantage System Update.
Act now and get a major discount on unlimited Amazon Cloud storage

I'm likely preaching to the choir when I say all data should be backed up, in fact it's best to have it in two places -- one local and one off site in case of disaster. Off-site can mean several things, but the increasingly popular choice is the cloud and there are many choices for that.
Now Amazon has an offer you may not be able to refuse. Get unlimited cloud storage space for a year. The price? A mere $5. In addition customers can also choose unlimited photo storage for a year at only $1. Those are both great deals given what they regularly retail for --$59.99 for data storage, though if you're a Prime customer then you already have the unlimited photo storage.
Wi-Fi Barbie could be putting your kids at risk

The latest Wi-Fi enabled Hello Barbie dolls could be putting your children at risk according to security researchers.
Using a combination of speech recognition technology and wireless connection Hello Barbie provides, "...an engaging and unique Barbie experience," according to manufacturer Mattel.
© 1998-2025 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.