
TP-Link launches Archer GE400 Wi-Fi 7 gaming router
TP-Link has announced a new entry-level Wi-Fi 7 gaming router aimed at players who want faster wireless performance without paying a premium. The Archer GE400 rounds out TP-Link’s Wi-Fi 7 gaming range, joining the GE800 and GE650 and priced at a more affordable $219.99.
Wi-Fi 7 builds on the Wi-Fi 6E standard and improves wireless stability and responsiveness by combining higher modulation rates and multi-band communication.

How did it do that? Over half of IT leaders not confident explaining AI model decisions
A new report from Anaconda shows 51.4 percent of IT leaders say they’re not very confident in explaining AI model decisions to regulators, executives, or customers.
As a result they’re over-promising and under-delivering, and this trouble communicating creates unrealistic expectations for customers and stakeholders. 26 percent of respondents identify difficulty demonstrating ROI as a top concern. What’s more just 22 percent say they would describe their organization’s AI deployment as ‘strategic’.

Cyber incidents cost organizations millions
Security leaders estimate that, on average, cyber incidents cost their organization $3.7 million, with 46 percent suffering from an outage or disruption to their services as a consequence of attacks.
A new survey from Red Canary of 550 security leaders, from the US, UK, New Zealand, Australia, and the Nordic countries, finds that SOC teams continue to struggle with the challenges of securing cloud environments, identities, and AI technologies amid evolving threats.

Microsoft celebrates 11 years of the Windows Insider Program with new wallpapers
Microsoft is a big fan of marking milestones and anniversaries by releasing wallpaper. Now the company is doing just that to celebrate the eleventh anniversary of the Windows Insider Program.
The program was designed with a dual purpose. Firstly it gives Microsoft a way to mass test changes to its operating system, and secondly it gives eager users the chance to test out and shape the future orf Windows.

YouTube can now limit how long you spend watching Shorts
There are countless ways to waste time online, and scrolling your way through a never-ending selection of Shorts on YouTube is one of them. If you are someone who has found you have lost hours to the content served up by the platform, there is some good news.
A new digital well-being tool is starting to roll out that lets users set a time limit for the daily viewing of YouTube Shorts. While far from perfect, it may prove helpful for anyone who tends to lose track of time.

Are we human or are we security risk?
Not quite how The Killers put it, but a new report shows Human workers remain the most consistent point of attack for cybercriminals, with shadow IT and AI-driven social engineering providing attackers with both new tools and new targets.
The 2025 Global Threat Intelligence Report from Mimecast reveals key trends, including the rise of smarter, AI-powered phishing and social engineering cyberattacks, and threat groups increasingly using trusted services to evade detection and reach targets. Mimecast’s analysis finds that phishing accounts for 77 percent of all attacks up from 60 percent in 2024 with attackers likely leveraging more AI tools.

How infostealers have changed the cybersecurity landscape
Many of the recent wave of high-profile cyberattacks can be traced back to the theft of a single set of credentials which have allowed the attacker to access and move within a corporate network.
A new report from Flashpoint looks at the rise of large-scale information-stealing malware campaigns and how ‘infostealer’ malware has been a key enabler, responsible for the theft of over 1.8 billion corporate and personal email accounts, passwords, cookies, and other sensitive data.

OpenAI launches ChatGPT Atlas, a new browser built around AI -- but it’s macOS only for now
The wait is over! OpenAI today rolls out ChatGPT Atlas, its new AI web browser. Built around ChatGPT, Atlas merges browsing and conversation into one workspace, letting users ask questions, get help, and complete tasks directly on the pages they visit.
Versions for Windows, iOS, and Android are expected at some point, but for now, the browser is exclusive to macOS.

Access to public web data is essential for the AI market
New poll data reveals that 89 percent of respondents say access to public web data is critical for ensuring a fair and competitive AI market.
The survey carried out at this year’s OxyCon web intelligence event shows organizations are getting worried they are losing access to precious web data, robbing them of the ability to make the AI of the future as democratic as possible. 64 percent of respondents say their organisations has been blocked from more websites than a year ago.

Microsoft says Windows update may have caused login problems
Microsoft has made another admission that its updates for Windows may have caused problems for some people. The company says that updates released for Windows 11, version 24H2, Windows 11, version 25H2, and Windows Server 2025 in August and September could have resulted in login issues for some.
There are two offending update – namely the August 29, 2025—KB5064081 (OS Build 26100.5074) Preview and September 9, 2025—KB5065426 (OS Build 26100.6584) – which Microsoft says could lead to Kerberos and New Technology LAN Manager (NTLM) authentication failures.
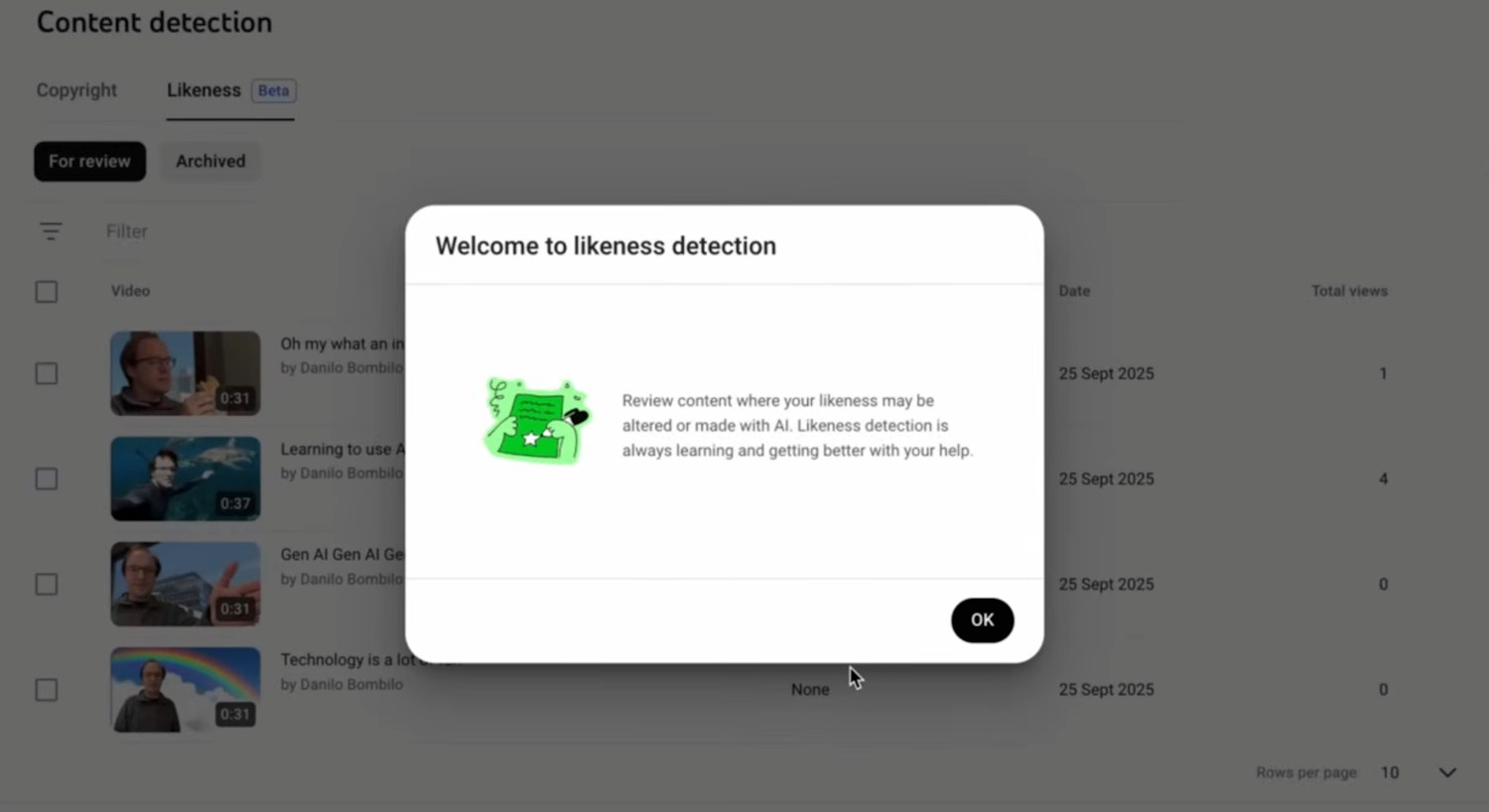
YouTube is fighting deepfakes with new Likeness Detection tool
In an age of fragmented news, deepfakes present a real problem. YouTube is taking action to stop AI-generated videos being used to impersonate people.
The company has revealed details of its new Likeness Detection tool. For now, YouTube is targeting creators, giving them access to the tool – not only because creators are among those likely to be deepfaked, but also because the company will be hoping to be able to use their influence to hype up Likeness Detection.
Meta rolls out warnings to help protect older WhatsApp and Messenger users from scams
Online scams are nothing new, but there are now more channels through which they can be run. Among them are social platforms like WhatsApp and Messenger, and it is sad fact that older users are more likely to fall victim
This is precisely why Meta is rolling out a new system of warnings that appear in its messaging apps. The aim is to make users think twice about who they connect to and who they share information with as part of Cybersecurity Awareness Month.
Instagram lets teenage users choose a different app icon
Most of the talk about teenagers using social media centers around keeping them safe or restricting what they are able to do. In many regards Instagram is no different, but now younger users are being given something extra.
Instagram’s design team has proudly announced the users with Teen accounts will be able to choose between a number of “aesthetics” for the app. Not available to anyone with a non-Teen account, the new option allows teenagers to select a different icons for the app, designed by Carlos Oliveras Colom.

How enterprise developers are moving from fragmented tools to unified platforms [Q&A]
Across large organizations, developers and DevOps teams rely on an ever-growing collection of specialized tools. But while these offer valuable flexibility, they can also create significant pain points.
We spoke to Chintana Wilamuna, VP of solutions architecture at WSO2, about how the landscape is changing from fragmented, purpose-built development tools toward comprehensive, unified platforms.

Casio unveils ring-sized G-SHOCK with full shock resistance and water protection
Clearly following the old adage that good things come in small packages, Casio has introduced the DWN-5600, a new addition to its G-SHOCK lineup that shrinks the iconic watch down to a ring-sized form, without compromising the brand’s signature durability.
Modeled after the classic 5600 series, which carries the original G-SHOCK design, the DWN-5600’s case measures just 23.4mm x 20mm with a thickness of 7.5mm.
