
Endpoint malware and ransomware reach new highs
New data shows that while total perimeter malware detection volume has decreased, endpoint malware detections had already surpassed the total volume seen in 2020 by the third quarter of 2021.
The latest quarterly report from WatchGuard Technologies also shows a continuing trend for a significant percentage of malware to arrive over encrypted connections, the percentage delivered via TLS jumping from 31.6 percent to 47 percent.

Patriot launches P400 PCIe Gen4x4 M.2 SSD
The transition to PCIe 4.0 is in full effect, with more and more computers and motherboards having the new standard. Whether or not the user truly needs the benefits of PCIe 4.0 is debatable, but it is still cool regardless. After all, it is important to continually push boundaries.
One of the best aspects of PCIe 4.0 is faster solid state drives. For instance, today, Patriot launches a new such SSD. Called "P400," the M.2 drive uses the 4th-gen PCIe interface to deliver fast speeds while its graphene heatshield will keep things cool.

Run Windows apps on Linux with Wine 7.0
It used to be, people would scoff at the idea of switching to a Linux-based operating system due to a lack of software. While that is still true for some folks -- especially business users -- it is less of a concern these days. Why? Well, so many things are done through the web browser nowadays, lessening dependence on Windows software. For many consumers, just having the Google Chrome browser on, say, Ubuntu, is more than enough to accomplish their wants and needs. Not to mention, there are many quality Linux apps like GIMP and DaVinci Resolve.
But OK, lets say you really want to use a Linux-based operating system, but there's some Windows-only software that you absolutely cannot live without. Thankfully, you may still be able to ditch Windows and upgrade to something like Fedora or Linux Mint. How? Thanks to the excellent Wine! This compatibility layer (don't you dare call it an emulator), can sometimes enable you to run Windows software on Linux. Today, version 7.0 is released.
Debian-based deepin Linux 20.4 is here and you should switch from Windows 11 today!
Debian is a great operating system in its own right, but also, it makes for an excellent base for other Linux distributions as well. For example, Ubuntu is probably the most well-known Linux distro and it is based on Debian. There are countless other operating systems, such as Netrunner, that stand on Debian's figurative shoulders.
The prettiest and most exciting Debian-based operating system, however, is deepin. This Chinese-developed Linux distribution is probably the most beautiful desktop operating system on the planet; it is arguably better than both macOS and Windows 11 in the style department.

Logitech Pen is a student-focused Chromebook stylus with USB-C charging
Chromebooks may not be the most powerful or useful computers, but they do excel in one specific area -- simplicity. The Linux-based Chrome OS operating system is streamlined and secure, making it a dream for system administrators and IT departments. Sure, a Windows computer may have more possibilities, but it also has a greater chance of malware.
Because Chromebooks are so simple to use and maintain, the computers have been very popular for education. Of course, the low hardware costs are often a contributing factor as well. Many new Chromebooks have touch screens, and for those machines with CCI stylus support, Logitech has a new such product to make compatible Chrome OS laptops (and tablets) even more useful in the classroom.
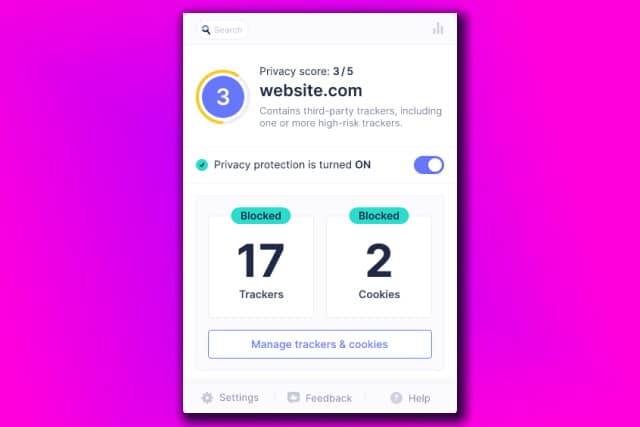
Startpage launches Privacy Protection browser extension to block cookies and ad trackers
Startpage is a familiar name for internet users with an interest in privacy. Not content with providing a privacy-centric alternative to Google's search engine, the company has launched more private rivals to other Google products, with Private Language Translator being a recent launch. Now the company has a new browser extension which has been designed to keep internet users safe.
Offering protection from "Big Tech", which Startpage points out is "recording and auctioning off your personal data" is the new Startpage Privacy Protection extension. Available for Chrome and Firefox, the extension not only blocks ad, social and cookie-based trackers, but also assigns the sites you visit a privacy score so you can learn of their trustworthiness, as well as giving you control over data collection and blocking fingerprinting.

High risk vulnerabilities in fintech soar over the past year
Financial services companies on the Bugcrowd platform experienced a 185 percent increase in the last 12 months for Priority One (P1) submissions, which relate to the most critical vulnerabilities.
According to activity recorded on the Bugcrowd Security Knowledge Platform, high-level trends include an increase in ransomware and the reimagining of supply chains, leading to more complex attack surfaces during the pandemic.

Enterprise SASE needs a radical approach to be effective
Although Secure Access Service Edge (SASE) is widely seen as the answer to balance network performance and security, new research from Cato Networks shows a radical approach is needed in order to reap the full benefits.
The study of over 2,000 IT leaders and nearly 1,000 channel partners doesn't show much difference between those who have and have not adopted SASE. When asked how they react to performance issues with cloud applications, 67 percent of SASE users and 61 percent of non-SASE users claim they would add bandwidth, while 19 percent of SASE users and 21 percent of non-SASE users would look to WAN optimization appliances.

Microsoft set to acquire Activision Blizzard for $68.7 billion
Microsoft today announced plans to acquire game developer giant Activision Blizzard for $68.7 billion. It is a move designed to expand the company's gaming business across PC, console, mobile and the cloud, as well as to give it a solid start in the metaverse.
This deal will make Microsoft the third largest gaming company (by revenue), behind Tencent and Sony.

Guess which government doesn't want you to use end-to-end encryption
From a privacy point of view, there is much to love about end-to-end encryption, as employed by the likes of WhatsApp. But while users may delight in the knowledge that their communication is free from surveillance, there are some groups that have a different opinion.
Law enforcement agencies have long-complained that E2E encryption stands in the way of investigations, and serves to complicate evidence gathering. Many governments are of the same mind, and it's not just those that are traditionally regarded as totalitarian by other countries. Governments from ostensibly democratic countries are opposed to E2E encryption, and some are using underhand tactics in negative PR campaigns.

Microsoft releases emergency KB5010795 update for Windows 11, and nine more out-of-band updates, to fix Patch Tuesday problems
The first Patch Tuesday of 2022 was little different to those in preceding months in as much as the updates released by Microsoft caused various problems for lots of Windows users -- quelle surprise!
As a result, the company has been forced to release a series of out-of-band updates for numerous versions of Windows. The updates (KB5010789, KB5010790, KB5010792, KB5010793, KB5010794, KB5010795, KB5010796, KB5010797, KB5010798 and KB5010799) fix problems with virtual machines, VPN connections, Windows Server Domain Controllers and more.

Linux Mint 20.3 Cinnamon (Edge) Edition now available for download
When using a Linux-based operating system, you should always use the most recent kernel, right? Actually, no. While new kernels do add fixes and support for new hardware, they can also be less stable and cause bugs.
Unfortunately, if you have extremely new hardware, sometimes you must use a newer kernel in order to boot, as older kernels do not yet support some of your devices. For instance, Linux Mint 20.3 "Una" was released recently and it comes with Linux kernel 5.4. If that older kernel does not support your computer, it may not boot.
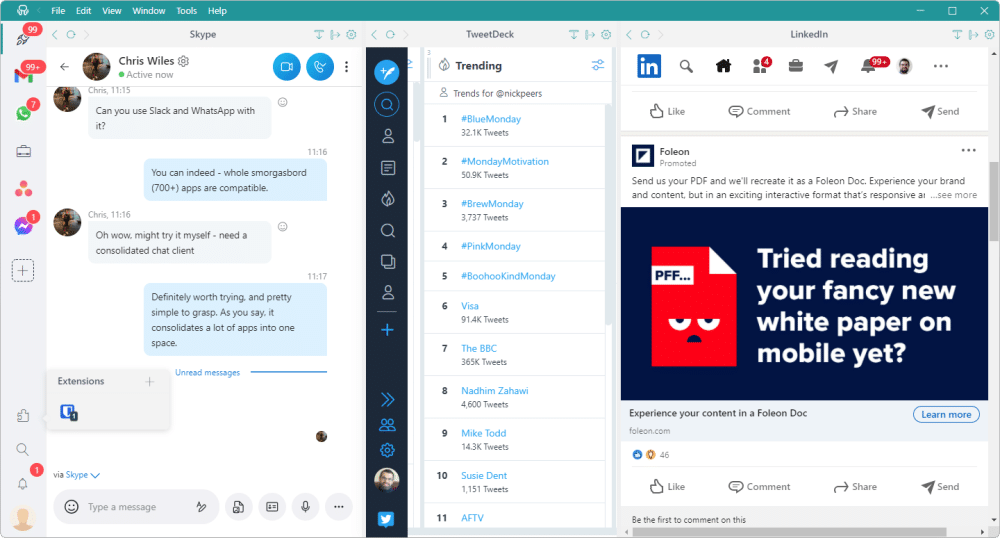
Rambox 2.0 allows you to consolidate all your major apps and services within a single workspace
Rambox LLC has started the New Year by relaunching its workspace consolidation tool with the release of Rambox 2.0. Available on Windows, macOS and Linux, the new app combines paid-for and free tiers within a single program for the first time.
Rambox originally launched in 2016 as an open-source beta under a 'Community Edition' banner. In 2018, a paid-for Pro version with additional functionality was added, and now Rambox has combined the two in a single program with both free and paid-for tiers.
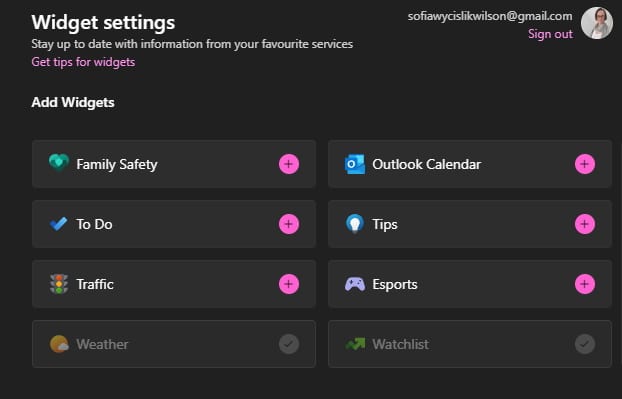
Third-party widgets are coming to Windows 11 (probably)
The Widgets component of Windows 11 was something that seemed like a great idea on paper, but has thus far failed to generate too much excitement. This is at least in part down to the fact that only official Microsoft widgets exist -- but this is going to change.
It is looking very much like Windows 11 is going to be gaining support for third-party widgets, opening up the possibility of a wider range of genuinely useful tools coming to users. There are also hints that a widget store, called the Widget Board, is on the way.

Amazon backs down on not accepting UK Visa credit cards
Back in November last year we reported on Amazon's decision to stop accepting UK issued Visa credit cards due to high processing charges.
The change was due to take place this Wednesday (January 19) but it seems that an 11th hour deal may have been reached to allow customers to continue using their Visa cards.
