
Dell is finally shipping the XPS 13 Developer Edition with Ubuntu Linux 20.04 LTS
If you want a laptop that comes with Linux pre-installed nowadays, there are actually a lot of options. While it used to be hard to get a computer without Windows on it, it is now a pretty easy task. You can choose from popular Linux-friendly computer sellers like System76 or Tuxedo Computers, but there is another company that sometimes gets overlooked -- Dell. Yes, one of the biggest manufacturers of Windows computers also sells "Developer Editions" of its computers that come with Ubuntu Linux pre-installed. The company has sold these Linux computers for several years.
One of the most celebrated laptops in recent years is Dell's wildly popular XPS 13. This is a thin and light notebook that offers both elegance and impressive performance. Newer models are famous for their super-thin bezels. And yes, Dell does offer a Developer Edition of the XPS 13. Believe it or not, even though Ubuntu 20.04 LTS came out in April, Dell has been shipping the laptop with the older (yet still supported) 18.04 LTS. Well, folks, as of today this changes. Dell is finally shipping the XPS 13 Developer Edition with Ubuntu Linux 20.04!

TEAMGROUP and ASUS unveil TUF Gaming Alliance T-FORCE CARDEA II PCIe M.2 SSD and DELTA 2.5-inch RGB SATA SSD
When a product is marketed to gamers, sometimes it means that it can help to improve the game experience. For instance, a gaming mouse or keyboard may provide more accurate controls. Other times, a "gaming" product is more about style -- having fancy RGB lighting or other cool "gaming" designs. Today, TEAMGROUP announces two new solid state drives that fall into the latter category. In a partnership with ASUS through the "TUF Gaming Alliance" program, T-FORCE shares the all-new TUF Gaming Alliance T-FORCE CARDEA II PCIe M.2 SSD and the TUF Gaming Alliance T-FORCE DELTA 2.5-inch RGB SATA SSD.
The T-FORCE CARDEA II uses PCIe 3.0 rather than the newer and faster PCIe 4.0, but in reality, that doesn't make any difference for gaming. Both the read and write speeds found on this drive are still quite impressive. It features an absolutely massive heatsink, making it imossible to fit inside a laptop. Hell, some desktops may have trouble accommodating it! The other drive -- the T-FORCE DELTA -- is a 2.5-inch SATA variant that has neat RGB lighting. If you have a window in your PC case, it will certainly look quite beautiful. If you don't have a case window, there is really no point in choosing it over any other SATA SSD.

Network operations in the new normal
The global pandemic has intensified the importance of networks, with more companies and individuals taking their worlds almost entirely online. But how is this affecting the teams that run them?
A new report from network operations specialist Kentik based on a survey of over 200 network professionals around the world shows that there's a mixed picture on productivity. 47 percent report feeling more productive while working from home, while 20 feel less productive and 33 percent say they have had no change in productivity.

Illumio brings zero trust to the endpoint
Endpoints are generally the weakest point of a corporate network and the problem is made more acute by the shift to remote working.
Illumio is launching a new endpoint protection solution that reduces the risk of ransomware and malware propagating laterally throughout an organization.

Developers need to think like hackers to prioritize fixes
As technology continues to evolve, software development teams are bombarded with security alerts at an increasing rate, making it almost impossible to address every potential vulnerability.
New research from WhiteSource, an open source security and license compliance management specialist, and CYR3CON, which predicts cybersecurity attacks based on AI-gathered intelligence looks at how development teams prioritize fixing vulnerabilities and compares this to discussions in hacker communities.
AI alone isn't enough to thwart cyberattacks
Crowdsourced security platform Bugcrowd has released a new report which shows that 78 percent of hackers on its site say AI-powered cybersecurity solutions alone aren’t enough to outmaneuver cyber attacks over the next decade.
The 2020 Inside the Mind of a Hacker report also reveals that 87 percent say that scanners can’t find as many critical or unknown assets as humans.

Is Twitter losing the right?
If you've been using Twitter over the past week or so -- especially if you're in the UK -- you may have noticed the hashtag #Twexit trending.
This is being used to signal users' intention to abandon Twitter and decamp to upstart rival Parler. So what’s going on here and why?
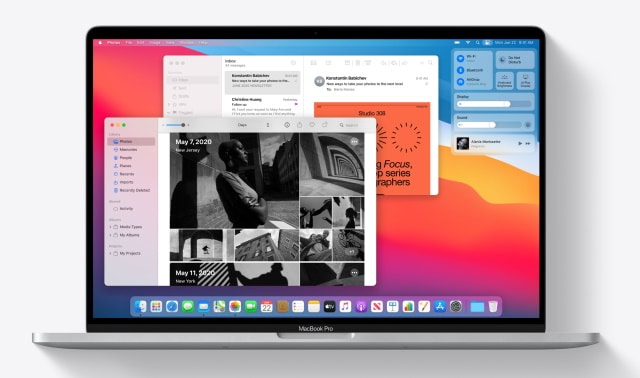
Apple unveils macOS Big Sur with a new look, Control Center, privacy improvements, and more
In addition to revealing iOS 14, iPadOS 14 and watchOS 7, at WWDC 2020 Apple also gave us a look at the future of macOS -- Big Sur.
This is a significant upgrade to the operating system, significant enough for Apple to move away from calling it macOS X, and jumping up to macOS 11. There has been a significant redesign to the interface, icons and apps, bringing macOS much more in line with iPadOS and owners of an upcoming ARM-based Mac will be able to run iOS apps natively). But Big Sur is about more than just aesthetics.

Microsoft flushes more money down the toilet by killing Mixer
Microsoft has a lot of successes, but also, the company has countless failures. With that said, failing in a business venture isn't entirely a bad thing -- it means you at least tried something. A company like Microsoft needs to take risks, but damn, sometimes it just feels like the company flushes cash down the toilet.
Case in point, back in 2016, Microsoft bought a game-streaming service (a Twitch clone) called "Beam." In 2017, the Windows-maker renamed that service to what it is known as today -- "Mixer." The company even paid millions of dollars to popular video game players to get them to stream elusively on the service. Hell, it was less than a year ago that Microsoft signed popular player "Ninja" for more than $20 million! And now, in 2020, Microsoft has killed Mixer, essentially burning many millions of dollars. Yup, the company announces that it will shutter Mixer on July 22 and then move all of its users to the Facebook Gaming platform.

Win a TCL 10 Pro Android smartphone in the BetaNews 'Welcome To Summer' giveaway!
Summer is here, but sadly, so too is COVID-19. True, much of the country is starting to "open up," but still, it is probably a good idea to limit your exposure to the public. Don't let that get you down, however, as there is plenty of summer fun to be had at home. If you have a yard, for instance, you can sunbathe and read books while laying on the grass. If you are lucky enough to own a pool, you can swim from the safety of your own property. Apartment dwellers can get in on the action too -- if you have a bathtub, you can sit in it and use your imagination to be transported to a tropical island (in your mind, at least).
Of course, just because it is the summer season, you don't have to do summery things. In fact, if you just want to sit on the couch with your smartphone and play games, watch movies, or listen to music, that is cool too. But what if your current smartphone stinks? Maybe it is slow, has bad battery life, or a cracked screen. If that is you, but you can't afford a new phone, don't worry -- we at BetaNews have five smartphones to give away! Best of all, it is a great smartphone -- the TCL 10 Pro. It has a beautiful screen with HDR support that is just perfect for watching Netflix!

Macs will use ARM-based Apple processors instead of Intel -- is Hackintosh dead?
Today at WWDC 2020, Apple confirmed the rumors -- the company is ditching Intel processors for future Mac computers. While there are technically still some future Intel-powered Macs in the pipeline, Apple intends to eventually switch to its own in-house chips exclusively. The company expects it will take two years for the transition to complete. The last time Mac made such a switch, it was PowerPC to Intel.
Obviously, these ARM-based chips will not be able to run current versions of macOS, so Apple has also announced the next version of the OS that will be compatible. Called "Big Sur," this upcoming version of macOS will also be able to run legacy third-party x86_64 programs through its Rosetta compatibility layer. All Apple programs will be designed for the ARM chips directly.
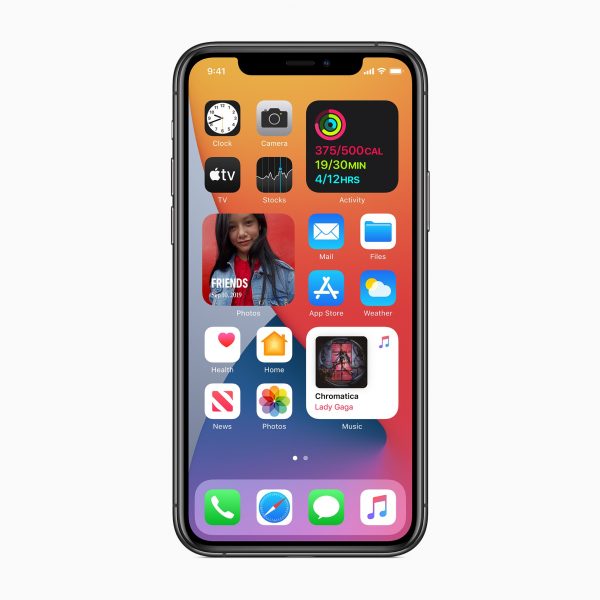
Apple reveals iOS 14 -- here's what's new
Apple's WWDC 2020 event was held virtually, open to everyone around the world to view for free. Among the many announcements to come from the event was iOS 14 -- and there's a lot to look forward to for iPhone owners.
What can you expect? Major improvements and changes are being introduced to the home screen and the way app pages work, and widgets are getting a serious overhaul. Siri sees a number of improvements, as does messaging. There's also an entire new type of apps called App Clips. Let's take a closer look.

US taxpayers think filing returns online is risky -- but they do it anyway
Thanks to the COVID-19 pandemic and extended tax filing deadline for 2020 its likely that people will be submitting their returns over a longer period this year.
New research from information security company Shred-it shows that most Americans file their tax returns online, even though many believe this puts them at greater risk of fraud.

Adobe Flash Player dies this year and you'll be told to uninstall it
Adobe Flash Player has been a blight on the internet for more years than most people care to think about, but its days are finally numbered.
We've known for a number of years that the software is reaching end of life (EOL) at the end of this year, and Adobe will stop distributing it after this date. But Adobe is going further, and will soon start to prompt people to uninstall Flash Player from their computers.
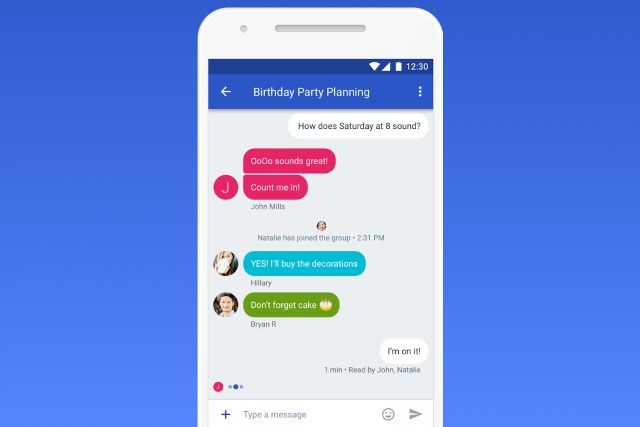
How to deregister your phone number from Google RCS chat
With absolutely zero fanfare, Google has rolled out a system that lets you turn off RCS chat features to help avoid problems such as missing messages.
The simple form that has appeared online is very similar to the one used by Apple. The online system can be used even if you do not have your previous phone with you, so you can deregister your phone number from your computer.
