
Syllable D900 mini wireless earbuds review
Apple's AirPods have started a conversation around wireless earbuds. Are they worth the premium over a wired pair? Is the sound quality any good? How long do they last without charging? These are the most common questions that consumers have, and it's only natural to be wondering how wireless earbuds perform and whether they are a legitimate alternative to the established wired options.
As someone who has used two excellent pairs of wireless headphones (the Noontech ZORO II and Hammo TV), I find that it's hard to go back to wired pairs. The Syllable D900 mini earbuds are no different, being a good example of a quality wireless pair that won't actually break the bank.
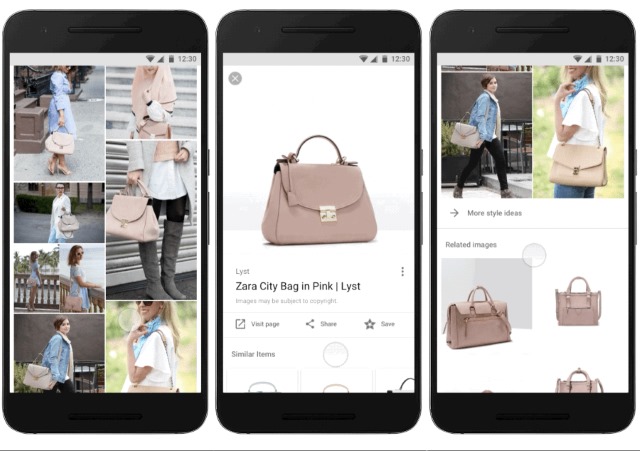
Google Image Search gets fashion-conscious with 'style ideas' on Android and the web
You'd be forgiven for thinking that Google is entirely pre-occupied with fake news and the fact-checking thereof these days, but there are still rather more interesting changes and additions being made to search. The latest new feature is "style ideas" which makes its way to the web and Android today.
Google says that the aim of the feature is to help "boost your search style IQ" -- because, after all, "when it comes to fashion, it’s hard to know where to start." What this means in practice is that when Image Search is used to track down a particular product, such as shoes or a bag, Google will show off images with those items paired with different products or displayed in different situations.

Ubuntu Linux 17.04 'Zesty Zapus' is here
Today is finally the day. Ubuntu 17.04 "Zesty Zapus" is available for download. No, this is not an Alpha or Beta, but an official stable version of the Linux-based operating system. Unfortunately, the release is a bit tainted -- it uses Unity as the official desktop environment, which Canonical has announced will be killed. Not to mention, there has been some controversy regarding some comments by Ubuntu founder Mark Shuttleworth. Just yesterday, the CEO of Canonical announced she is leaving the position.
With all of the aforementioned controversy and chaos, it is understandably hard to get too excited for "Zesty Zapus," especially as this is not a long term support version. With that said, if you are an existing Ubuntu user that likes Unity, this is certainly a worthwhile upgrade if you are OK with the shorter support. Unity may no longer have a future, but version 7 will continue to be supported -- for a while, at least.

Taking the pulse of social media to drive healthcare policy
A new study from UK think tank Demos in conjunction with health charity The King's Fund looks at how the internet and in particular social media can be used to shape health policy.
It reveals that 43 percent of internet users have now used the web to access health information, up from just 18 percent in 2007. Alongside well-administrated official sources, unregulated online forums have grown to be valuable spaces for users to discuss conditions and treatments, ask questions, and share advice with those who have had similar experiences.

RedOwl's behavioral analytics help fight insider risk
Insider attacks can prove more costly than outsider ones, yet a good deal of enterprise security effort is still expended on protecting the perimeter.
Inside risk solutions specialist RedOwl is releasing the latest version of its Insider Risk Framework, designed to offer out-of-the-box capabilities to fight insider threats and which companies can quickly deploy with minimal specialist expertise.

Cloud adoption and increasing threats drive enterprise encryption usage
Enterprises are accelerating their use of encryption and the strategy is being driven by business units rather than IT teams.
This is among the findings of a study into encryption habits by cyber security company Thales, based on research carried out by the Ponemon Institute. It finds that 41 percent of enterprises now have an encryption strategy in place.

Solving digital problems takes too long
Resolving incidents that impact consumers takes IT teams approximately double the amount of time customers are willing to wait for a service that isn't performing properly, according to a new study.
The research by digital operations management company PagerDuty surveyed over 300 IT personnel in development and operations as well as over 300 consumers in order to identify the challenges of meeting customer expectations.

Get WinX DVD Ripper Platinum (worth $59.95) FREE for a limited time
If you want to rip and copy any DVD disc, ISO image, or DVD folders to hard drive, computer, mobile device or digital formats, then WinX DVD Ripper Platinum is the perfect tool for the job.
It usually retails for $59.95, but for a limited time BetaNews readers can get it entirely free.

Google kills off Octane JavaScript benchmark due to 'diminishing returns and over-optimization'
Google has announced that it is to retire the Octane JavaScript benchmark. The company says that while the benchmark was useful when it was introduced back in 2012, "over-optimization" by developers means that it is far less meaningful.
Google goes as far as saying that developers were essentially cheating the system. It says that compiler optimizations needed to achieve high benchmark scores have become common and, in the real world, these optimizations translate into only very small improvements in webpage performance.

Microsoft's free cloud migration assessment sells the idea of hybrid cloud to enterprises
For enterprises, datacenters are at the heart of operations. With Azure, Microsoft has a vested interest in encouraging enterprises to move these operations to the cloud, and it is with this in mind that the company has launched a cloud migration assessment tool.
The free tool has been designed to give enterprises a way to determine whether it would make sense -- and how much it would cost -- to move to a hybrid cloud solution.
How to download old versions of Firefox
Downloading the latest version of Firefox for your PC is simple. Point your browser at the site, click "Free Download" and you’ll automatically get the latest version that matches your PC.
If you regularly need to download another build, though, life gets more complicated. You have to follow an "other platform" link, maybe select a 32 or 64-bit version, or follow yet another link to work your way through a list of languages.

Windows 10 and Xbox One to gain 'self-service refunds'
Much like Steam, Microsoft's Xbox One is to gain a "self-service refund" function. The idea is to make it easier to get a refund on games and other content that is not up to scratch, not what was expected, or simply not enjoyable.
Currently in testing with alpha users, the feature is due for a wider rollout, and will also make its way to Windows 10 users in the Windows Store. Of course, it is not going to be possible to get your money back on just anything, and there are few criteria that need to be met in order to qualify.

Toshiba is in serious trouble
Toshiba has filed its delayed financial results, warning that its survival is at stake.
The tech and construction company has reported a loss of $4.8bn (£3.84bn) for the period between April and December. However, these results have not been confirmed by the company’s auditors.

Half of millennials stream pirate content -- and see nothing wrong with it
Most people alive today have seen the evolution of the internet over the course of a couple of decades, and can remember life before it was so integral. But there is a growing proportion of the population that has never lived without internet access, and such people have developed something of a different outlook on things.
Millennials, in particular, have been able to reap the benefits of being permanently connected, and have no experience of what it was like before. One of the side-effects of the always-on, always-available nature of content is that piracy has become second nature. Not only are most millennials streaming pirate content, they do not see it as wrong -- although downloading the same content is viewed differently.

Marketers underestimate GDPR's ramifications
Awareness of the GDPR has gone up, but B2B marketers are still falling behind and underestimating the impact of the new regulation, according to a new report by the DMA.
More than a quarter of businesses (28 percent) still feel unprepared, which is just a two percent decrease, compared to earlier numbers. The number of marketers that have a "good" awareness about GDPR has risen 13 percent, to 66 percent in total, the report claims. B2B marketers, however, are at the both ends of the spectrum.


