Linux Mint 22.2 'Zara' beta now ready to download -- here's what's new

Linux Mint 22.2 “Zara” beta version has been released, giving testers and enthusiasts an early look at the next long term support release of the popular desktop Linux distribution. The final version will be supported until April 2029, but this preview is aimed at testing, so some issues are to be expected.
This update continues Mint’s focus on making small, but noteworthy changes. Sticky Notes now have rounded corners, Wayland support, and can sync with Android devices via the new StyncyNotes app. The login screen gains a blur effect, user avatars, and a cleaner layout.
How access to company networks is sold on the dark web for under $1,000

New analysis of illicit dark web marketplaces where cybercriminals buy and sell access to corporate networks uncovers new insights into how initial access to compromised businesses is being sold -- often for less than $1,000 -- and the steps defenders can take to disrupt the process in its earliest stages.
Rapid7’s threat intelligence researchers analyzed hundreds of posts by Initial Access Brokers (IABs) offering access to compromised networks across a range of industries and regions. Their findings show that ‘initial’ access doesn’t necessarily equate to minimal; in many cases, this access represents a deep compromise.
Spread of AI agents sparks fears of a cybersecurity crisis

A new report reveals an increasing trust gap between businesses deploying agentic AI for external communications and consumers wary of sharing personal information due to security concerns.
The research, carried out by Censuswide for Salt Security, also warns that without proper API discovery, governance and security, the very technology meant to drive smarter customer engagement could open the door to cybersecurity issues including attacks or data leakage.
Excel can now explain formulae with Copilot
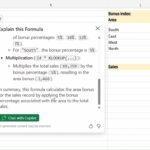
Microsoft just found a new use for AI. Excel users can now turn to the new Explain Formula feature which uses Copilot to use artificial intelligence to understand how a formula works.
There are many advantages to this. It can serve as a way to learn about how to create new formulae of your own, but it is also a handy way to not only understand how a formula works as well as a means of debugging if the output is not what you were expecting it to be.
Microsoft OneNote finally gets unformatted text pasting
Microsoft OneNote is an incredibly useful tool, and a clever one – sometime too clever. After being absent for far too long, it now finally has an unformatted text pasting option.
It is hard to believe that it has taken over twenty years for this to arrive – and it is not clear why it has taken so long – but it is finally here. No longer will you have to strip out unwanted formatting, change color and so on. Unformatted text pasting is now just a keyboard shortcut away.
Epson launches ReadyPrint subscription for unlimited color printing at a fixed monthly cost

Epson has launched ReadyPrint, a subscription-based printing service that aims to make color printing simple, predictable, and cost-effective for homes and businesses.
The plan combines an EcoTank wireless all-in-one Supertank printer with unlimited color printing, premium support, and automatic ink replacement for a fixed monthly fee.
Microsoft launches Windows 365 Reserve preview to reduce downtime
Microsoft has launched a limited public preview of Windows 365 Reserve, a new cloud-based service to help reduce downtime and disruption for business when disaster strikes.
Whether there is a system failure, a cyberattack, or something else goes wrong, Windows 365 Reserve provides access to a Cloud PC to help reduce disruptions. Microsoft says that it offers businesses “secure and on-demand Cloud PC access from anywhere when you need it most”.
Sync files quickly and securely between devices for free with Syncthing 2.0

Syncthing 2.0 has arrived, promising faster syncing, a new database system, and a number of major fixes and improvements. This open source program lets you sync files directly between computers in real time, keeping them private, encrypted, and fully under your control without the need for a central server.
Syncthing offers a simple promise: your files stay yours. You decide where they are stored, how they are transmitted between devices, and who gets access.
How to stop Instagram sharing your location
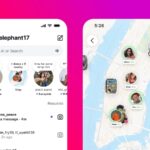
Instagram recently added a number of new features, including sharing your location. While some additions – such as reposting – were welcome, location sharing sparked concerns.
The new Instagram map feature allows the people you are connected to on the social media platform to see your location – and you can see theirs. Instagram has pitched this as being useful to parents, but many users are worried about the privacy implications of location sharing.
Kubuntu Focus launches Zr GEN 1 Linux laptop with Nvidia RTX 5090 option

Kubuntu Focus has introduced the Zr GEN 1, a high-performance Linux laptop aimed at users who want maximum mobile power. The 18.0-inch workstation replaces the previous 17.3-inch M2 GEN 5 and brings faster components, more storage capacity, and a brighter display, with shipping now available in the US and Canada.
The Zr GEN 1 runs Kubuntu 24.04 LTS and is built for developers, machine learning researchers, content creators, and others looking for fast hardware with Linux-first support.
High Court rejects Wikipedia challenge to UK online safety rules

A High Court ruling has ended Wikipedia’s attempt to overturn part of the UK’s divisive new Online Safety Act, but the legal fight over its application may not be quite over. Judges dismissed the Wikimedia Foundation’s challenge to rules that could place the encyclopaedia under the law’s strictest category of regulation.
The organization behind Wikipedia says the framework risks forcing it to verify the identities of its volunteer editors, undermining both their privacy and the way the site operates. It argues that the model, in which anyone can contribute without registering personal details, is central to the platform’s reliability and breadth of coverage.
Business is booming for AI assistants as they take on bigger roles

The AI assistant market is projected to grow from $3.35 billion this year to $21.11 billion by 2030, according to Indian research firm MarketsandMarkets.
This represents a compound annual growth rate of 44.5 percent, with North America forecast to have the largest share during that five year period.
Debian 13 'trixie' released with five years of support and new architecture options
Lucky for fans of the popular Linux operating system, Debian has released version 13, codenamed “trixie,” marking the project’s first stable release in over two years. Supported for the next five years by the Debian Security and Long Term Support teams, trixie delivers updated packages, improved hardware compatibility, and expanded architecture support, including official riscv64 support for the first time.
The release includes multiple desktop environments such as GNOME 48, KDE Plasma 6.3, LXDE 13, LXQt 2.1.0, and Xfce 4.20.
Ransomware attacks up by 41 percent globally
New data from Check Point Research reveals a sharp rise in cyberattacks globally, with business services, healthcare, and manufacturing among the hardest hit sectors.
Ransomware incidents in particular have surged, with 487 attacks reported in July, a 41 percent increase year-on-year. North America accounted for 56 percent of all reported ransomware cases, followed by Europe at 24 percent.
Ashampoo releases UnInstaller 16 with faster and more efficient software removal
Ashampoo has released UnInstaller 16 for Windows, allowing users to fully remove programs and apps with minimal effort. The latest version promises more thorough cleaning than the standard Windows tools, giving users greater control over installations while maintaining system performance. It also brings faster cleaning, expanded logging, and new resource management features.
Ashampoo UnInstaller 16 builds on the company’s existing removal tech, adding tools that track software installations in detail.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.




