Feed Sync 30K launches for tech-savvy vapers: USB-C charging, social media, and fitness tracking features

Feed has introduced the Feed Sync 30K, a disposable vape device that bridges the gap between vaping, social media connectivity, and health monitoring. This device targets the modern, tech-savvy user by incorporating several advanced features. It's important to note that BetaNews does not condone the use of vaping or any nicotine products.
The device boasts a substantial puff capacity of up to 30,000 puffs and supports USB Type-C charging, which aligns with modern electronic standards for convenience and speed. This feature is particularly practical as it allows users to charge their devices with the same type of cable used for many smartphones and laptops, enhancing usability.
With Workspaces, the best new PowerToys module yet, Microsoft is giving you a way to launch and arrange multiple apps in one click!
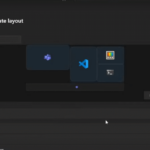
Our love of PowerToys here at BetaNews is no secret. Like other users, we eagerly await each new update to see whether there is new module or a handy new feature for an existing utility.
But equally exciting are glimpses into the future, when we learn what the PowerToys developers are working on right now. The latest news from Microsoft reveals that PowerToys Workspaces is in the pipeline, a module that makes it possible to launch multiple apps from a single shortcut. More than that, these apps can be opened in saved arrangements for the best work experiences. Think virtual desktops on steroids.
Goodbye Windows 11, hello Linux: Discover how ExTiX Deepin 24.8 can free your computer from Microsoft

ExTiX Deepin 24.8 has been launched (download here) as the latest version of the Linux distribution, now based on the newly stable Deepin 23. Released just a day after the official launch of Deepin 23 STABLE, ExTiX 24.8 offers an enhanced user experience powered by the Linux Kernel 6.10.3-amd64-exton.
This release is particularly appealing for users looking for a Deepin-based system but prefer to steer clear of software directly from Chinese companies due to privacy or trust concerns.
PowerA debuts special edition Fortnite wireless controller for Xbox and Windows

PowerA has introduced a new wireless controller designed specifically for the Xbox Series X|S, tailored to enhance the gaming experience for Fortnite players. This special edition controller is also compatible with Xbox One and Windows 10/11 PCs and comes officially licensed by Xbox.
The controller features Hall Effect triggers and thumbsticks that use magnetic sensors, potentially improving durability and precision. It also includes adjustable three-way trigger locks, four mappable advanced gaming buttons, dual rumble motors, magnetic impulse triggers for enhanced feedback, and a low-latency wireless connection.
Enterprises need to update application security practices

Organizations urgently need to modernize their application security practices so that they can support growth and mitigate risks according to a new report.
Thew study from Legit Security and TechTarget's Enterprise Strategy Group (ESG) finds nearly all organizations reporting difficulties in fixing vulnerabilities after applications are deployed, reinforcing the significance of incorporating security processes and tools in the build process.
Embracing the digital workplace: IT's new role in driving productivity

Britain is plagued by sluggish productivity, with the Office of National Statistics (ONS) reporting UK productivity growth as 'anaemic' for the past 15 years. And things are getting worse, not better.
In London -- the country's largest and richest regional economy -- output per hour worked has fallen by 2.7 percent between 2019 and 2022. But what is the root cause of this underwhelming growth?
The challenges of securing Active Directory [Q&A]

Microsoft Active Directory is used by a majority of the world’s organizations. But Cyberattacks and misconfigurations targeting AD have surged in recent years, leading to critical outages and data loss.
We spoke to Bob Bobel, CEO of Cayosoft, about how to address critical weaknesses in enterprise infrastructure associated with Microsoft Directory services.
Best Windows apps this week
Six-hundred-eight in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft is testing changes that add layout options to the 'All Apps' section of the Start menu of Windows 11. The first groups items, the second displays them in a grid.
DDoS attack activity soars in first half of 2024

In the first half of 2024, web DDoS attacks surged globally 265 percent compared to the second half of 2023, according to the latest threat analysis report from Radware.
Organizations in EMEA were the primary target of web DDoS attacks between January and June of 2024, being subject to more than 90 percent of the attacks.
Forget Microsoft Windows 11, the Chinese-made deepin Linux 23 is the operating system you really want

deepin, the renowned Linux distribution from China, has launched its latest version, V23, bringing a slew of enhancements that make it an appealing choice for both newcomers and seasoned Linux users. This update is especially valuable for those considering transitioning from Windows 11, as it provides a user-friendly interface and introduces features that enhance compatibility, stability, and modern computing demands.
The system repository in deepin V23 has undergone a comprehensive upgrade, stabilizing over 8,000 core packages to boost system security and provide extensive support for new hardware architectures such as ARM64, RISC-V, and LoongArch64. This ensures broad compatibility across various devices, making it an optimal choice for users looking to migrate from other operating systems.
Why automation isn't the answer to zero-day attacks [Q&A]

Last year saw almost 100 zero-day attacks, putting a strain on security teams and becoming known as the 'Hot Zero-Day Summer.'
In response to these attacks, the first instinct of many organizations has been to turn to automation. But Marc Rubbinaccio, manager, compliance at Secureframe, doesn't believe that this is the right approach. We spoke to him to find out more.
Key Bridge rebuild: leveraging artificial intelligence and machine learning for AEC projects

The collapse of Baltimore's Francis Scott Key Bridge sent shockwaves both nationally and internationally earlier this year. The city is now faced with the significant economic loss of a critical transport channel – and the challenging task of its reconstruction. Engineering and construction specialists anticipate that the rebuild effort could take up to 15 years. As a once-widely utilized structure, there is a deep sense of urgency to expedite the resurrection of the Key Bridge.
But current engineering and construction processes could wreak havoc on the possibility of an expeditious rebuild. The design and planning processes for large architecture, engineering and construction (AEC) projects, specifically critical infrastructure such as airports, bridges and ports, are historically rigid. Operating with a highly formalized approach derived from years of informed engineering practices, the volume of factors to contemplate around the build of a crucial transport structure is astronomical. Identifying and adhering to rigorous regulatory standards is only the first hurdle. Combine this with navigating other variables such as climate change, traffic implications and sourcing highly specialized materials, and suddenly a decade doesn’t seem like an unreasonable timeline for the construction of a major transport hub.
BSOD hits one in 200 devices daily

New analysis of system crashes shows that, without preventative IT in place, one in every 200 devices falls victim to the dreaded blue screen of death (BSOD) per day, even under 'good' operating conditions.
The research from Nexthink shows the recent CrowdStrike outage pushed the number as high as one in 10.
Google exposes Iranian cyber threats aimed at U.S. and Israel

Google's Threat Analysis Group (TAG) has recently illuminated the ongoing cyber espionage activities of APT42, an Iranian government-backed group linked to Iran’s Islamic Revolutionary Guard Corps. This cyber collective has intensified its phishing campaigns against high-profile targets in Israel and the United States, particularly focusing on individuals connected to the upcoming U.S. presidential elections.
In detailed findings released by TAG, it was revealed that APT42 has been targeting current and former officials, diplomatic circles, political campaigns, and influential figures within academic and non-governmental organizations in both nations. The U.S. and Israel combined represent about 60 percent of APT42’s cyber operations in the last six months.
Fastmail now supports passkeys
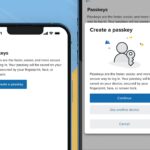
Fastmail has launched a new feature allowing users to create passkeys for their accounts, promising a faster and more secure authentication method compared to traditional passwords. Passkeys address the inherent weaknesses of passwords by using cryptographic keys that offer several advantages over conventional methods.
Passwords, the standard for online authentication, present challenges such as the difficulty in creating secure passwords and vulnerability to phishing attacks. In contrast, passkeys operate on public key cryptography, where a private key creates a signature and a public key that the website can verify. This method provides security benefits like replay resistance, where each login attempt involves a unique challenge from the website, making passkeys resistant to interception. They are also leak-resistant since only the public key can be compromised without being used to forge a login, and they are phishing-proof as passkeys are inherently tied to the website they were created for.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.




