Windows 10 Anniversary Update will improve interoperability between Microsoft Edge and IE 11
Since the release of Windows 10, the update of Microsoft Edge has been a little on the slow side. The addition of support for add-ons may help to increase the user base for Edge, but many enterprise customers still have a need for Internet Explorer.
When building Edge from scratch, Microsoft included Enterprise Mode to allow sites that rely on older technology to open with Internet Explorer 11 instead. With the upcoming release of Windows 10 Anniversary Update improvements are being introduced that will smooth out some of the rough edges of Enterprise Mode, including removing the friction that currently exists when switching browsers.
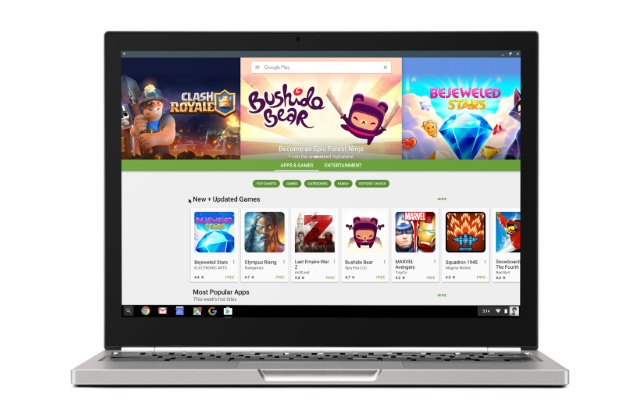
Google makes Chromebooks exciting again by adding Google Play and Android apps
Much like Windows Mobile, Chromebooks have long suffered with something of a limited range of apps. Starting today, all this changes; Google is bringing the full range of Android apps to Chromebook users via the Google Play store.
With Chromebooks having just overtaken Macs in terms of popularity, the introduction of millions of Android apps to the platform is incredibly well-timed. Before you get too excited, the rollout is not immediate. Users on the developer channel with certain Chromebook models will get access first, but there are plans to bring Google Play to more devices over the coming months.

IBM creates faster, longer lasting memory technology
IBM’s researchers have found a way to build computer memory that’s incomparably faster to anything we have today. Besides being that much faster, it’s also more enduring and dense. Sounds a bit like science fiction, doesn’t it?
The new technology is called PCM, or phase-change memory, and it revolves around storing three bits of data per cell. It doesn’t lose data when powered off, and it can live through "at least" ten million write cycles (average USB stick can endure some 3,000 cycles).

Bracketron TekGrip Power Dock is an elegant smartphone charger and mount for your car
Summertime is on the horizon, which for many folks means traveling by car. Whether taking a short drive to a local beach, or a cross-country family vacation, the warm weather makes for a fun time -- if you have air-conditioning, that is! Nowadays, smartphones make the experience even better, thanks to streaming music and GPS-based mapping services.
Unfortunately, keeping your phone charged and easily accessible is problematic. Wires can easily get tangled, and holding your phone while driving is dangerous. Not to mention, when multiple people are in the car, there may be arguments over who gets to use the 12V outlet. Today, Bracketron unveils the TekGrip Power Dock -- an elegant smartphone charger and mount that may alleviate many of the aforementioned woes.

Popular hacking site Nulled hit by cyberattackers, user info leaked
The email addresses and private messages of over 470,000 members of the popular hacking website Nulled have been leaked following a data breach.
The website served as a marketplace where its users could buy and sell the account details they stole from users along with hacking advice and tips. The data that was leaked from Nulled contained over 5,000 purchase records that detailed how the stolen information available on the site’s marketplace was exchanged between users.

The future of game development
Gaming has come a long way since the first arcade games were invented in the early 1900s. From the original pinball machine, to today’s gaming world of Virtual Reality, the gaming industry has advanced rapidly. We can look back on the gaming evolution over the decades but seeing into the future isn’t so easy.
However, based on current trends we can take some educated guesses into the future of gaming.

Stop ransomware accessing your files with Privacy Fence
Privacy Fence is a free tool which aims to prevent untrusted applications from accessing your data, blocking threats like ransomware before they can do any harm.
The program starts by building a list of protected file types. Common file types are included by default, and key user folders -- Desktop, Pictures, Videos, Music and so on -- are scanned for other types you might be using. Privacy Fence then starts to build a Trusted Applications list by adding programs currently associated with your file types.

Google will soon let you share Android apps with family members
While you can share a Google Play Music subscription with your family, the same cannot be currently said about apps that you purchase from the Play store. Unless everyone is on the same Gmail account, each member has to buy the same title separately to enjoy it on their devices. Considering that both Amazon and Apple offer this feature, Google needs to follow suit.
The good news is that Google will soon introduce Family Library. This new feature will be available to Play users in the coming months and will finally allow them to share paid apps with their family members.

Brands fail to meet mobile communication expectations
Brands aren't doing enough to meet their customers' expectations for mobile communication, according to a new survey.
The study, by web convergence company tyntec and technology research specialist Ovum, of 1000 people in the US and Germany finds that customers prefer to interact with customer service agents using different communication channels depending on where they are in the transaction process, and that they expect service providers to be effective using mobile.

Stardock releases Fences 3.0, adds Windows 10 support, roll-up fences
Stardock has released Fences 3.0, a major new version of its Windows desktop organization tool. The new release brings Fences bang up to date, with support for Windows 10 and high DPI monitors.
Fences 3.0 also introduces several new features, including the ability to roll up fences to their title bar as well as support for navigating through folder structures from within the fence itself.
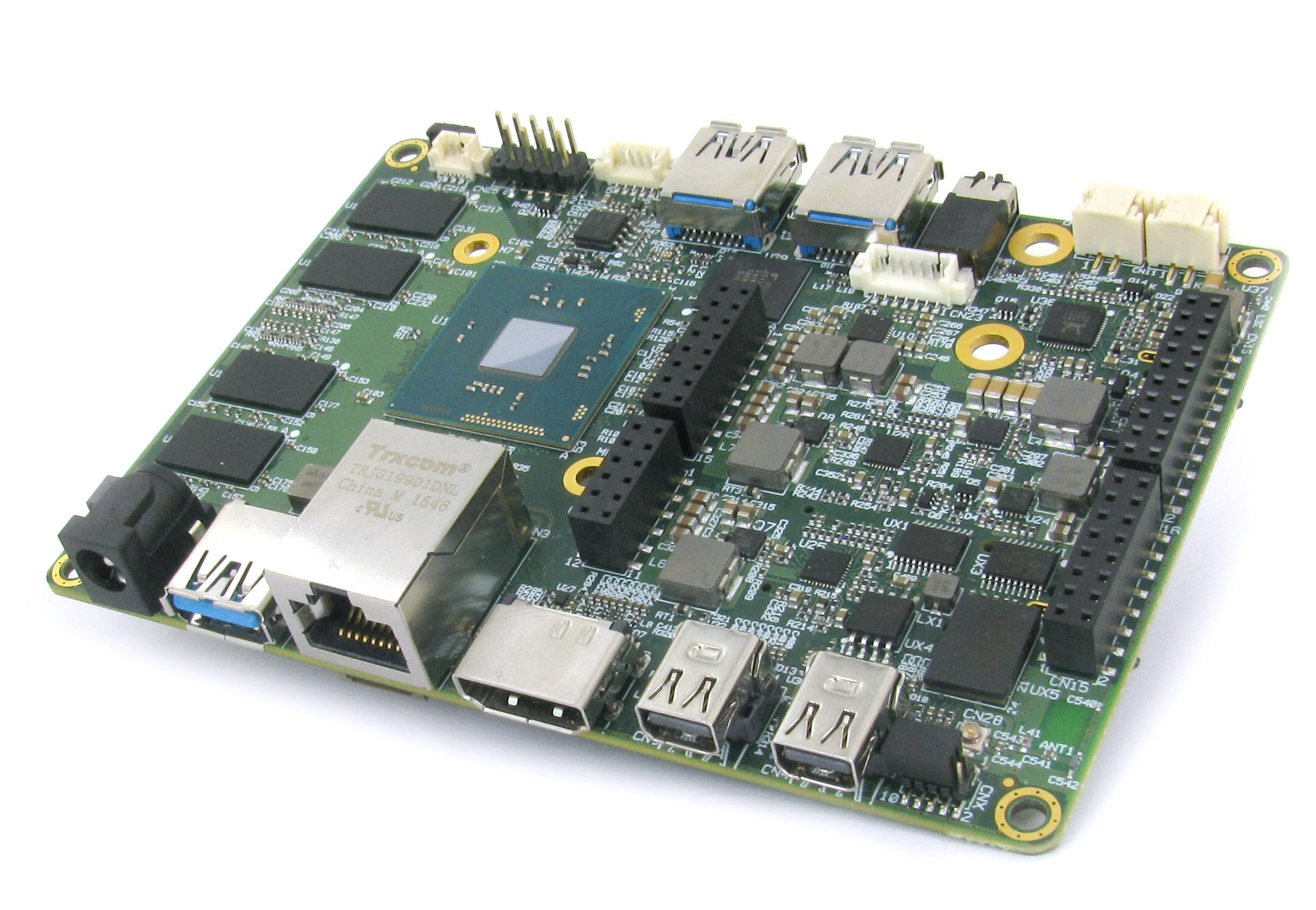
UDOO X86 is 10x more powerful than Raspberry Pi 3, and can run Windows, Android, and Linux
If you’re looking for an uncased maker board for a project, then the Raspberry Pi is usually the first choice, not least because it’s inexpensive, and powerful enough for most purposes.
However, if you need something with a lot more muscle, then the UDOO X86 certainly fits the bill. Based around an Intel X86 64-bit Quad Core processor, coupled with an onboard Intel Curie Arduino 101-compatible micro-controller, it’s got enough oomph to drive three 4K screens at the same time.

Compliance struggles to keep pace with new communications channels
Compliance professionals need to supervise all types of business communications, but a new survey shows that they're struggling to keep pace with the volume and variety of electronic channels.
Hosted archiving specialist Smarsh has released its sixth annual Electronic Communications Compliance Survey Report. The survey, of compliance professionals in the financial services industry, highlights that supervision practices aren't sufficiently addressing the compliance implications of ongoing trends, like increased regulatory scrutiny and the challenge of adapting to channels like social media and text messaging.

IT departments need to contribute more to digital transformation
Everyone agrees IT departments need to play a bigger role in the process of digital transformation. Those are the results of a new and extensive survey by The Economist Intelligence Unit and SAP.
The survey asked more than 800 senior executives from various industries, with more than half being IT leaders, about the process of digital transformation. Key highlight of the report is that there’s a "distinct lack of strategic co-ordination around digital transformation".

The challenge of securing smart buildings from cyber attack [Q&A]
As more and more devices get added to the Internet of Things the risks they present get larger. A recent report from the BBC has highlighted the fact that buildings and their systems for heating, lighting and even security may be at risk.
We spoke to Péter Gyöngyösi, product manager of Blindspotter at contextual intelligence specialist Balabit, to find out more about the risks smart buildings present and how landlords and tenants can guard against them.

Cortana update brings Android notifications to Windows 10 users
The ability to view notifications for multiple devices in one place is something that has been tried in various forms before. Now fans of Cortana can take advantage of notifications about their phone on their computer.
The latest version of the Cortana Android app brings the previously hinted at app notification syncing that users have been asking for for so long. First noted by a Windows 10 user on Reddit, the feature is something that we can expect to see included in the Windows 10 Anniversary Update later this summer.



