
Samsung pushes the Internet of Things with open ARTIK platform
Every company worth its salt is keen to get aboard the Internet of Things bandwagon, and Samsung is no different. Today the company announces its ARTIK platform which it hopes will accelerate the development of IoT apps and hardware for both consumers and the enterprise.
This is more than just a platform announcement, however; Samsung has produced three modules with a variety of integrated features ready to power the next generation of connected devices. The modules are backed up with embedded hardware security and can be tailored to a range of tasks.
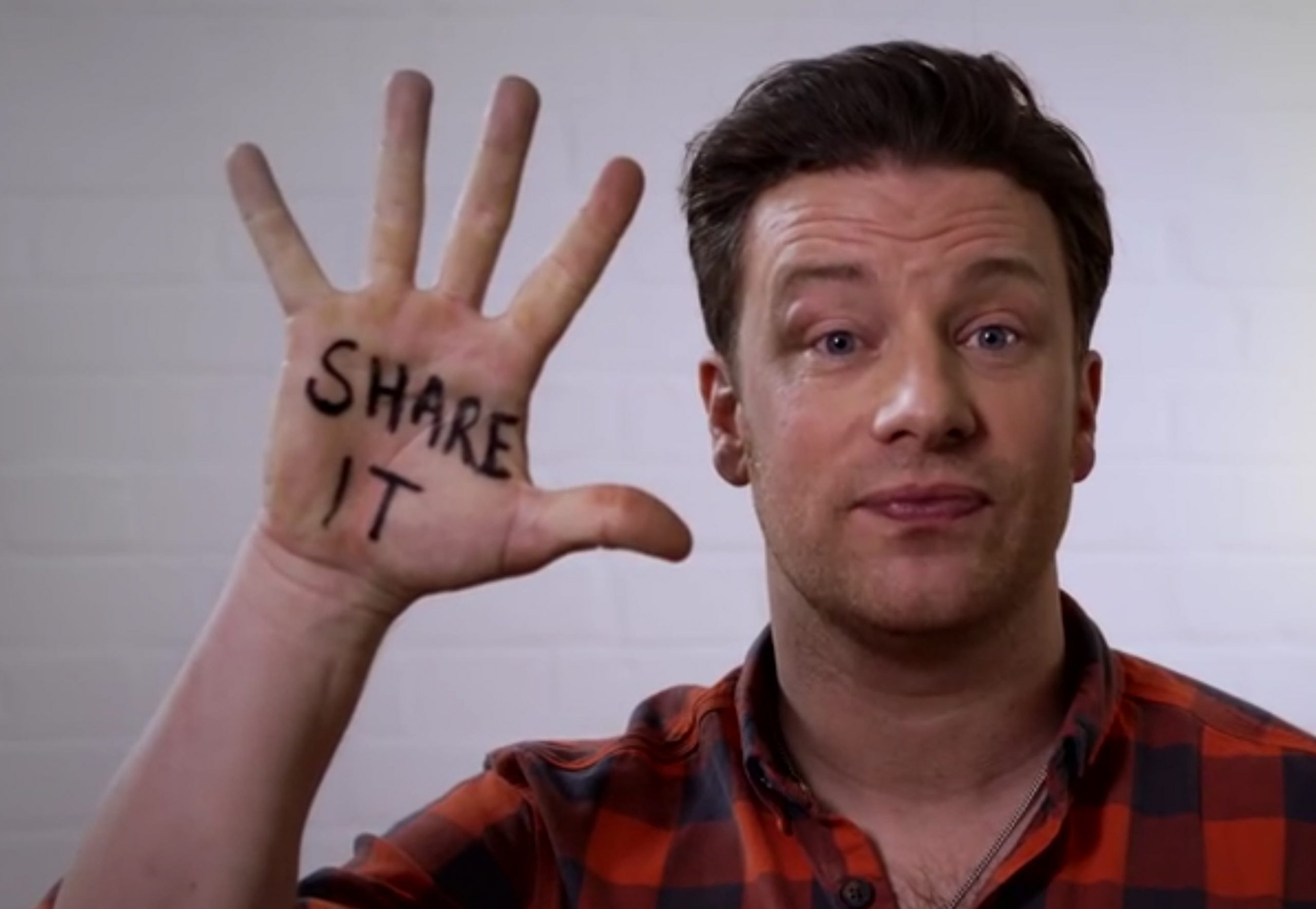
Jamie Oliver is trying to steal your passwords
Celebrity chef Jamie Oliver’s website seems to serve three main purposes these days -- provide tasty recipes to try in the kitchen, keep visitors informed about his latest campaigns and, oh yes, infect your PC with password stealing malware.
Three months ago, Malwarebytes discovered a well hidden malicious injection on the official website of Jamie Oliver which redirected unsuspecting visitors to an exploit kit. This was apparently dealt with, but then a month later the issue resurfaced. So surely, after having been infected twice, the site is now clean? I think you can guess the answer to that.

Skype Translator Preview now available to all -- ¡Una gran noticia!
I find it incredibly frustrating that the world has more than one language. True, there is beauty in different languages, but it is not ideal from a communication standpoint. Not to mention, it makes traveling a chore. When I went to Europe, most people spoke English, but when they didn't, I felt a bit vulnerable -- what if there was an emergency and people couldn't understand me? Scary stuff.
Luckily, technology is bridging the language gap; lessening, and potentially eliminating the barriers between two speakers of different types. While there are many low-level text solutions, such as Bing and Google Translate, the most exciting is Skype Translator, which also works in live audio/video chat. Currently in preview, Microsoft's solution used to require a sign-up to test it -- not anymore. Today, it becomes available to all, including you!
Windows 10 for phones Insider Preview Build 10080 expected this week
It’s been a month since the last Windows 10 for phones Insider Preview arrived -- Build 10052 -- but the good news is Microsoft is preparing a new release and Insiders on the Fast ring could receive it as soon as this week.
According to Gabriel Aul, head of the Windows Insider program, Build 10080 is the current candidate and it’s this which will be making its way onto phones, provided it passes Microsoft’s internal testing.

The best (and more affordable) Apple Watch alternatives
The Apple Watch is only a couple of weeks old, but there have already been a few reported issues with the device. Its health sensors struggle when users have dark tattoos, some have criticized its long load times and the launch period did not go entirely to plan, with consumers having to wait longer than expected to receive their smartwatch.
However, perhaps the biggest hurdle for some consumers is the price of the Apple Watch, which ranges from $349 to more than $15,000. Of course, that hasn’t stopped the wearable gadget from racking up impressive pre-order figures, but if you are looking for an alternative wearable, we’ve listed the best below.

Slemma launches cloud data visualization tool aimed at smaller businesses
Whatever the size of a business, data is a crucial part of understanding and managing what's going on. But if that data is coming from several different programs it can be hard to pull it together to gain meaningful insights.
Slemma is a new browser-based data visualization tool that gives businesses an intuitive, collaborative and measurable view of their important metrics.

New marketing tool delivers better targeted Facebook ads
The rise of social media has meant that marketers are keen to create contextual adverts that reach their target audience, but to do it in a way that isn't intrusive or annoying.
Analytics and marketing application company Teradata is launching a new solution in the form of a digital marketing capability that enables marketers to deliver highly targeted Facebook advertising as part of an integrated solution that incorporates social advertising with email, mobile and web.

Add motion animations to your videos with Express Animate
Freeware developer NCH Software has released Express Animate, a key frame-based animation tool.
The program can import videos, images, text, shapes and audio tracks. Objects may be moved, resized or rotated, while key frame support gives smooth, high quality results.

Big Data insights is like shooting fish in a barrel
Big Data as a concept has the potential to provide so many useful insights into our daily lives and business processes, but often organizations can get caught up in the hype.
Having access to tons and tons of data is not the only step to coming up with useful insights, but organizations can use it effectively if they know how. It has been estimated that for every day in 2012, 2.5 Exabytes of data were created -- today the same figure is produced every few minutes, meaning that companies have to be more aware than ever before which data is useful and which is not.

Home and small office routers are being hijacked for DDoS attacks
The router security message really should have been driven home years ago, but it seems that a lack of basic security practices by ISPs, vendors and users has resulted in large numbers of hacker-controlled routers being used to launch DDoS attacks.
A New report from web security specialist Incapsula says it has uncovered a DDoS botnet comprising tens of thousands of hijacked routers. It's now sharing the attack details in an attempt to raise awareness about the dangers posed by under-secured, connected devices.

iPhones and iPads rule the enterprise market, Windows is slowly gaining ground
While Android is the clear leader in the mobile market, in the enterprise space arch-rival iOS is the platform that actually comes out on top. Apple's iPhones and iPads make up 72 percent of all mobile device activations, while handsets running the green droid operating system have to make do with just 26 percent.
Unsurprisingly, it is iPhone 6 which sustains Apple's enterprise dominance, coming out as the most-popular handset in the enterprise thanks to it making up 26 percent of all activations between January and March. Apple's flagship is followed by Samsung's Galaxy S5. Together, the two leading vendors offer 28 out of the 30 most-popular devices in the enterprise.

Xirrus introduces high density access points to meet extra Wi-Fi demand
Increased mobile device use and the rise of Internet of Things devices (Gartner estimates there'll be 25 billion by 2020) has led to greater demands on wireless networks with increased volumes of traffic.
Network specialist Xirrus is introducing Xtreme Density (XD) Wi-Fi access points to meet this need. The Xirrus XD4 is the only 4-radio all 802.11ac access point currently on the market.

Microsoft opens up Surface 3 mass deployments
You don't have to be a fan of the Surface lineup to like what Microsoft has done with Surface 3. It runs the full-fledged version of Windows, packs a free Office 365 subscription, gets decent battery life, is light, has a large display for a tablet, offers lots of internal storage, has a full-size USB port, and can take a Type Cover keyboard. As far as its laptop-replacement credentials go, Surface 3 most definitely bests any iPad that is on the market today. And, to top it all off, Microsoft's latest slate can be had for as little as $499.
Given the core feature set it packs, Surface 3 is well positioned to take on the iPad in the enterprise market. But, to become a truly attractive option, it needs to be easily deployable. And now Microsoft has addressed this too.

How to display Windows 8 toast notifications from your own scripts
Scripts and batch files are great for automating complex tasks, but they’re not so good at keeping you informed about their progress. Typically you’re forced to Alt+Tab back to the command prompt window to try and figure out what’s going on.
ToastNotification is a tiny console tool which offers an alternative, at least for Windows 8 users. It allows you to display toast notifications -- pop-up status messages which disappear after a few seconds -- from your own scripts.

How to protect your children from cyber-bullies and other online dangers
The research claiming that depression and anxiety among teenagers is higher than other generations fueled by sexting and online bullying clearly indicates the dangers facing young people in today’s digital world.
Yet the true extent of the problem is likely to be even worse as more and more children start engaging online from a younger age.



