
Microsoft will no longer enable Do Not Track by default
Do Not Track will not be enabled by default in future versions of Microsoft web browsers, the company says. The decision comes in response to the latest draft of the World Wide Web Consortium's DNT standard which states "in the absence of user choice, there is no tracking preference expressed".
Microsoft is concerned that if the setting is enabled by default in Internet Explorer or Project Spartan, sites would have a loophole permitting them to ignore a DNT signal. In the future users will need to manually enable the feature, and Microsoft says that clear information will be provided about how to do this.

Samsung Galaxy S6 edge buyers complain of screen defects
Samsung Galaxy S6 edge customers are complaining that their handsets are being received with scratched displays and dead pixels.
Although the flagship device is not supposed to launch officially until 10 April, T-Mobile has begun shipping the smartphones in advance.

WikiLeaks leaker Chelsea Manning joins Twitter from prison
Despite being incarcerated for leaking classified documents to WikiLeaks, Chelsea Manning has joined Twitter. The solider formerly known as Bradley Manning has been approved to receive gender-reassignment hormone therapy, but is not permitted access to the internet.
To get around this restriction, supporters of Manning have set up the @xychelsea account on her behalf. Tweeting is due to start today, and Manning will dictate messages over the phone so "her own candid thoughts and comments" can be shared with Twitter users.

Samsung Galaxy S6 edge bends as easily as Apple iPhone 6 Plus
Every new high-profile smartphone is subjected to a bend test nowadays. It's become a tradition following the launch of iPhone 6 Plus, which has been found to easily bend under pressure. So, naturally, when it came time to test Samsung's new Galaxy S6 edge and HTC's new One M9, SquareTrade chose Apple's phablet to serve as the basis for comparison.
Galaxy S6 edge appears to be more fragile compared to Galaxy S6, due to the rounded screen which minimizes the level of protection offered by the surrounding metal frame. Meanwhile, HTC's One M9 has a more traditional form factor, similar to last year's One (M8), which should help it fare better. So how easily do they bend?

TrueCrypt doesn't contain NSA backdoors
A security audit of TrueCrypt has determined that the disk encryption software does not contain any backdoors that could be used by the NSA or other surveillance agencies. A report prepared by the NCC Group for Open Crypto Audit Project found that the encryption tool is not vulnerable to being compromised.
However, the software was found to contain a few other security vulnerabilities, including one relating to the use of the Windows API to generate random numbers for master encryption key material. Despite this, TrueCrypt was given a relatively clean bill of health with none of the detected vulnerabilities considered severe enough to lead "to a complete bypass of confidentiality in common usage scenarios".
Best Windows apps this week
One-hundred and twenty fifth in a series. Welcome to this week's overview of the best apps and games released for Windows in the past seven days.
Microsoft rebranded the two core apps Music and Videos this week and released them as previews for Windows 10 dropping the Xbox branding in the process.

The technology that could have prevented the Germanwings Flight 4U 9525 tragedy
In the wake of Germanwings Flight 4U 9525’s tragic crash, there has been much talk about how this will affect the aviation industry going forwards. Will all airlines adopt the "rule of two" cockpit procedure? Should there be more intense scrutiny of pilots’ mental health?
The debate over what can be done to limit a repeat of the catastrophe will rage on and on, but away from the human causes and aftermath, there is an existing technological solution that could potentially have saved the lives of all 150 on board.

System76 unveils all-new Broadwell-powered Lemur -- an affordable Ubuntu Linux laptop
While many computer manufacturers are in a race to the bottom -- both in price and quality -- some makers continue to produce reliable high-quality machines. One of these manufacturers is System76. If you aren't familiar, it manufactures and sells desktops and laptops running the Ubuntu operating system. In other words, Linux fans can buy one of these machines and have it running the Linux distro out of the box -- no need to format the drive to remove Windows.
Today, the company announces the all-new Lemur -- a laptop with a Broadwell processor. The 14.1 inch laptop not only has solid specs, but an affordable price tag too. If you are a Linux fan in the market for a new laptop, you need to take a look.

Rise of copycats in China: Samsung Galaxy S6 clone at $169 now available for sale
Samsung finally seems to have got things right in its flagship smartphone. After receiving flak for years for using stale design language and cheap plastic material in its Galaxy smartphones, the South Korean technology conglomerate took to the stage last month to announce the metal clad Samsung Galaxy S6 with glass panel at both front and back ends. But if the $679 off-contract retail price seemed exorbitant to you, there is a clone of the S6 out there costing just $169 from a shady Chinese smartphone company.
Called the Goophone S6, the handset resembles the Galaxy S6 and comes in four color options -- golden, white, black, and blue. From the chassis to the design, to the logo, the resemblance is uncanny. As for the hardware, the smartphone comes with a dual-core MTK6572 processor clocked at 1.0GHz or a quad-core MTK6582 clocked at 1.3GHz (if you're happy to shell out an extra $40), and 512MB and 1GB RAM options. The phone runs on Android 5.0 and comes with enticing air gesture control, and heart rate monitor features. Needless to mention that the Goophone S6’s offering is nowhere close to the powerhouse Samsung has launched.

BBC officially releases Doctor Who episodes on BitTorrent
Although BitTorrent’s reputation is as a means to download music and movies illegally, the company is trying to change that by offering original, and legal content via paid "bundles". It scored a success in 2014 when it released Radiohead’s Thom Yorke's new album in this way, and later in the year it will be debuting its first original television series, Children of the Machine.
But today BitTorrent announces a really impressive coup -- the BBC has agreed to put out an official digital Doctor Who box-set via the file sharing network.

Google will continue to dominate search ad market in 2015
Google is looking at another dominant year in the search ad market, with estimated spending to reach $81.59 billion in 2015 according to research firm eMarketer.
Holding a solid 54.7 percent of the search ad market in 2014, Google will drop 0.2 percent of the total search ad revenue. This does not mean a decrease in revenue though, going from $38.42 billion to $44.46 billion in one year.

What is Tidal lossless 'HiFi' music worth? [first-impressions review]
Fraking fantastic is my reaction to Tidal's high-definition audio. I spent much of April Fools' Day testing, and quite enjoying, the music service, although I am skeptical that most streaming subsctibers will care—not for $19.95 per month. Still, I see hope for the 10-buck standard quality other option if Tidal delivers enough artist exclusives and superior curation. The iTunes hegemony, and Apple's rapidly evolving Beats Music acquisition, is all about content, much of it available nowhere else, better presented, and more easily discovered. With musicians' support, and unique content with it, maybe, just maybe, a Tidal wave approaches.
The service essentially relaunched on March 31, 2015, with a gala event hosted by Jay-Z and other music superstars. He acquired Tidal, for $56 million two months earlier, but the lossless streaming service launched in October 2014. Architecture, audio quality, two-tier pricing, and streaming are essentially unchanged. New owners' commitment, that of other artists, big marketing push, and 30-day trial distinguish Tidal today.

Android malware drops, but there are still nearly 10 million affected devices
Google says that it is keen for Android to be a secure platform for developers and end users alike. It's not a unique claim; Apple would likely say much the same about iOS, and Microsoft about Windows Phone/Windows 10 for Phones.
To demonstrate how fervently it has been working away at improving security and introducing new security-focused features, Google today published a report looking back on Android security in 2014. Dubbed the Android Security State of the Union 2014, it makes for interesting reading. It includes the revelation that nearly 10 million Android devices have potentially harmful apps installed.
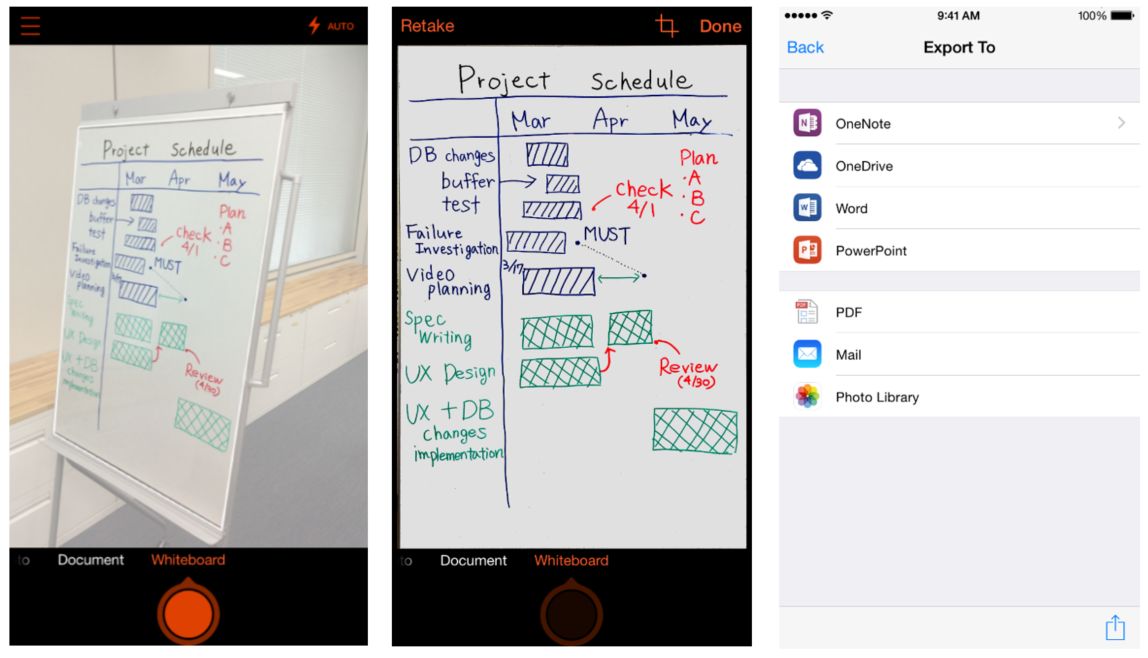
Microsoft brings Office Lens to Android and iPhone -- no longer Windows Phone exclusive
Windows Phone is Microsoft's mobile offering to the world, and some people love it. Unfortunately, the operating system's market share is extremely low, meaning many of the cool features and exclusives do not receive wide exposure. Slowly but surely, benefits that Windows Phone users pointed to as exclusives to the OS are being brought to competing platforms.
Today, Microsoft brings another Windows Phone exclusive to Android and iPhone -- Office Lens. Yes, the super-cool scanning feature is finally available to the large majority of mobile devices. Will you try it?

Copy the contents of image and text files to the clipboard with Copy Contents
You’re browsing Explorer and find an image you’d like to paste into another program. You could right-click it, select Copy, but that won’t work: Explorer copies the location of the file to the clipboard, not its contents.
One workaround is to double-click the image, open it in your default viewer, and copy it to the clipboard from there. That gets the job done, but it’s hardly convenient.



