
Microsoft releases KB5034843 update for Windows 10, adding new social sharing options
Continuing to prove that it has not forgotten about Windows 10, Microsoft has released the KB5034843 update. It not only addresses a number of issues, but also adds new features to the operating system.
The most significant change to be found in this update is the ability to share web links to a number of social platforms directly. There is also the promise that expanded support is on the horizon.

Microsoft brings USB 80Gbps support to Windows 11, plus important fixes and mobile changes, with KB5034848 update
Microsoft has released the preview version of the KB5034848 update for Windows 11. One of the biggest changes introduced by this non-security update is the addition of support for the USB 80Gbps standard, but there is much more too.
There are also numerous changes and additions relating to mobile devices, not least of which is the ability to use the Snipping Tool in Windows 11 to edit recent photos and screenshots on Android devices. The KB5034848 update also addresses a number of issues with the operating system.

Meta is deprecating Facebook News in the US and Australia, as it has done in Europe
Meta has announced that it is killing off the Facebook News tab in the United States as well as Australia. The company says that the decision has been taken because it believes "that people don’t come to Facebook for news and political content".
The Facebook News tab is set to be removed in April, and Meta says that it will be focusing "time and resources on things people tell us they want to see more of on the platform, including short form video". The dedicated tab for news has already been deprecated in France, Germany and the UK.

Linux users beware: New Bifrost malware variant poses imminent threat
Security researchers at Palo Alto Networks have uncovered a new variant of the notorious Bifrost malware, now targeting Linux systems with a cunning twist. This latest iteration employs a deceptive domain, download.vmfare[.]com, to masquerade as a legitimate VMware site, thereby bypassing security measures and compromising unsuspecting users.
Bifrost, a remote access Trojan (RAT) first identified in 2004, has been a persistent threat, enabling attackers to pilfer sensitive information such as hostnames and IP addresses. The recent surge in Linux variants of Bifrost has sent ripples of concern through the cybersecurity community, signaling a potential uptick in attacks on Linux-based systems.

Bridging the gap: Aligning OT security with the pace of new-gen technologies
The convergence of IT and OT (Operational Technology) networks has been instrumental in driving operational efficiency and innovation across industries. As businesses are rapidly heading towards Industry 4.0, the benefits of this integration are clear.
However, with digital transformation comes the risks of a constantly expanding threat landscape. The merging of IT and OT environments has amplified the risk of wide-scale disruptions and sophisticated attacks like ransomware, extending from digital to physical infrastructures. These concerns are also evident in the growing demand for OT security, as the market is projected to reach $38.2 billion by 2028.

Microsoft announces a cornucopia of Windows 11 improvements, including AI audio and photo tools, widget enhancement and more
Windows 11 users have a host of new features to look forward to, as well an enhancements to existing components. Everything from AI-powered Generative Erase and Silence removal through voice shortcut improvements to new sharing options, there few areas of the operating system that are not getting attention.
The rollouts start today and continue over the coming month, and users can also expect a new widgets experience, better Snap suggestions for screen organization and more. Today's announcement also sees Microsoft unifying the Windows Update for Business deployment service with Autopatch into a single update management solution.

Microsoft makes Copilot in Windows 11 more useful with new capabilities and plugins
Continuing to go all-in on artificial intelligence, Microsoft has announced a series of new features for its Windows 11 AI assistant. The company has announced the capabilities for Copilot as well as introducing new plugins for even more options.
The arrival of new plugins from the like of OpenTable, Shopify and Kayak helps to transform Copilot into something even more useful than it has been so far. It means that the assistant can be used to book restaurant tables as well as suggesting menus for home dining. On top of these plugin-driven additions, Copilot is also gaining new features so it can display system information on demand, and be used to control accessibility features.

Get 'Electronics All-in-One For Dummies, 3rd Edition' (worth $25) for FREE
If you're looking for a new hobby that's tons of fun -- and practical to boot -- electronics might be right up your alley. And getting started has never been easier!
In Electronics All-in-One For Dummies, you'll find a plethora of helpful information, from tinkering with basic electronic components to more advanced subjects like working with digital electronics and Arduino microprocessors.
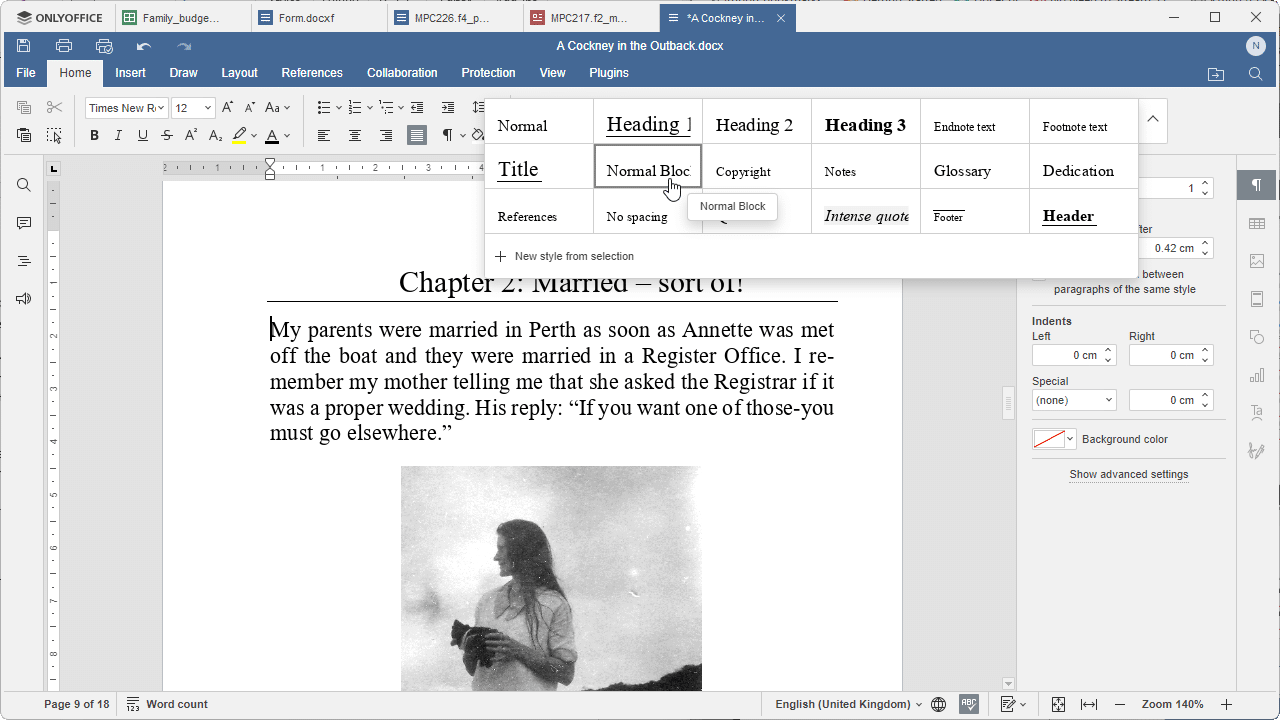
OnlyOffice 8.0 provides a slick, yet lightweight, alternative to Microsoft Office and LibreOffice
Does the world need another alternative to the almost ubiquitous Microsoft Office? While LibreOffice is its most recognizable rival, it does suffer a little from a dated user interface. Enter, stage left, OnlyOffice 8.0, an open-source rival to both that offers enough unique functionality to make it stand apart.
OnlyOffice’s first unique feature is that it contains its main features -- document editor, spreadsheet, presentations, PDF viewer/annotator and recently added forms creator -- within a single, streamlined app.

Cybersecurity staff perform multiple different roles
Staff at various levels work in multiple cybersecurity functions according to the latest report from IANS research and recruitment specialist Artico Search.
It finds 42 percent have responsibilities that span multiple cybersecurity domains. Of the AppSec staff, 74 percent also contribute to product security and 67 percent are involved in identity and access management (IAM).

New platform improves visibility across attack surfaces
There is an increasing level of crossover and connectivity between IT, operational technology (OT) and IoT assets, which raises the risk of cyberattacks originating in IT systems and then spreading into OT environments.
To help businesses address this risk Tenable is launching a new exposure management platform that provides holistic visibility into assets across IT and OT environments.

In-house apps cause breaches at 92 percent of companies
A new study reveals that 92 percent of companies surveyed had experienced a breach in the past year due to vulnerabilities of applications developed in-house.
The report from Checkmarx shows that in recent years the responsibility for application security has shifted away from dedicated security teams and is now shared between AppSec managers and developers.

DDoS attacks against web apps and APIs surge
Globally, the average number of DDoS attacks per customer grew by 94 percent in 2023, according to a new report from Radware.
"The technological race between good and bad actors has never been more intense," says Pascal Geenens, Radware's director of threat intelligence. "With advancements like Generative AI, inexperienced threat actors are becoming more proficient and skilled attackers more emboldened. In 2024, look for attack numbers to climb and attack patterns, like the shift in Web DDoS attacks, to continue to evolve."
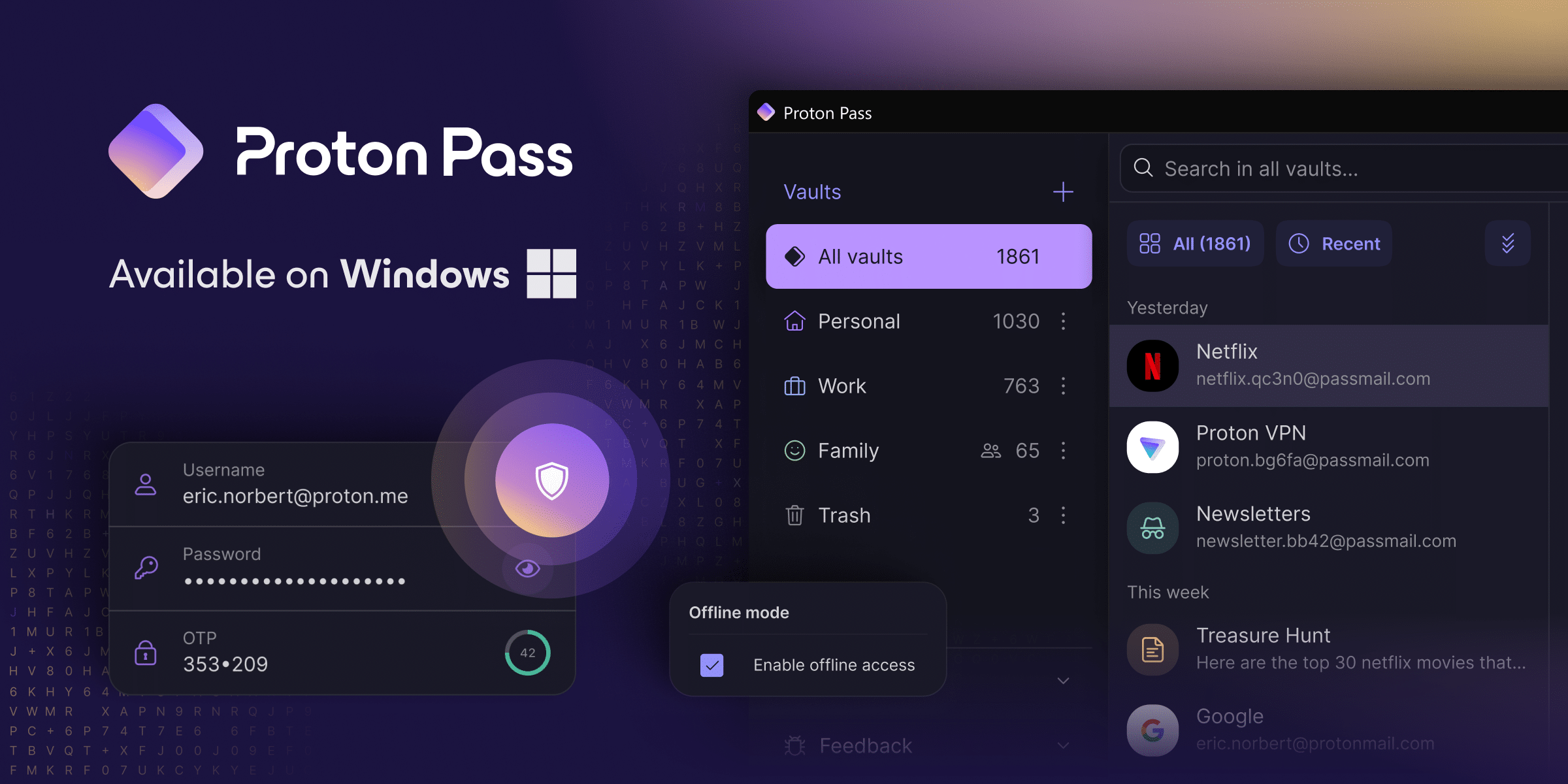
Proton Pass password manager app for Windows launches with offline mode -- macOS and Linux versions on the way
Proton, the privacy and security company, has launched Proton Pass for Windows -- a new standalone desktop application that extends its secure password management beyond the web browser. Proton Pass offers an enhanced user experience by integrating more seamlessly with the Windows operating system, allowing smoother management of passwords and encrypted login information.
One of the key features of this new application is its offline mode, available to Proton Pass Plus and Unlimited users. This mode ensures access to information anytime, without needing an Internet connection, and is secured with Argon2 encryption, known for its robust defense against brute-force attacks.
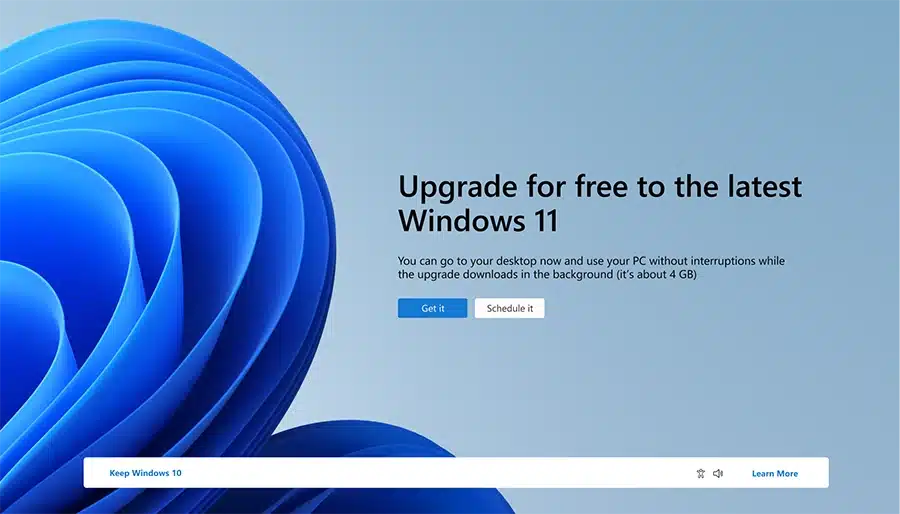
Microsoft is badgering even more Windows 10 users to upgrade to Windows 11
Windows users are well aware that Microsoft is no stranger to trying to nag them into submission. The company has a history of pestering users to switch to its web browser and to upgrade to the latest version of Windows, and this is a practice that it not only continuing, but expanding.
Microsoft has already been encouraging / nagging (delete as you see fit...) to upgrade from Windows 10 to Windows 11, and now the company has announced that it is about to take this further. It is described rather euphemistically as "expanding invitations to move to Windows 11 to more people".



