
Cooler Master and SoLa Impact team up to empower South LA youth with tech and esports
In an inspiring move, Cooler Master, known for its PC components and gaming peripherals, has joined forces with SoLa Impact, an organization focused on affordable housing development in Los Angeles. This collaboration aims to provide the underserved youth of South LA with access to cutting-edge technology and digital learning resources.
At the center of this initiative is the SoLa Tech and Entrepreneurship Center, a 13,000 square foot facility dedicated to nurturing the next generation of tech-savvy professionals, entrepreneurs, and leaders from Black and Brown communities. The center is equipped with over 100 computers, digital production and podcasting facilities, a Live Nation Music Jam Room, labs for entrepreneurship and creativity, gaming consoles, arcade games, and a state-of-the-art Esports & Gaming Arena.

Google can now train AI with Reddit posts thanks to new Data API access deal
Google and Reddit have "expanded and deepened" their existing partnership in a deal that will give the search giant near-unfettered access to content posted on the site. As well as helping users to find Reddit content via the search engine, the move also means that Redditor's posts will be used to train Google's AI models.
Reddit says that in giving Google access to it Data API, it will be "easier to discover and access the communities and conversations people are looking for". It is being pushed by both companies as a way of promoting the "open internet", but it is something that is proving conversial.

Some Windows 11 updates may soon install without reboots
A reboot is required after the installation of many updates for Windows. This is definitely the case for the monthly cumulative security updates, but also for other updates. Windows 11 displays popups to the user when a restart is required, which can be disruptive.
Sometimes, Windows may even restart the computer automatically, which can lead to data loss and other unwanted outcomes. At other times, it may not give the user a choice to reboot without installing the update.

Upgrade your Nintendo Switch and say goodbye to Joy-Con drift forever: Pre-order the CRKD Nitro Deck+ now!
CRKD, the company behind the Nitro Deck and the recently announced NEO S, has unveiled its latest offering. Called “Nitro Deck+,” it is an enhanced version of the popular Nitro Deck designed for Nintendo Switch and OLED Switch consoles. The Nitro Deck+ aims to offer Switch gamers a more feature-rich and powerful experience in handheld mode, with zero stick drift and a comfortable design.
The Nitro Deck+ was announced during the IGN FanFest event and is a result of extensive community feedback following the original Nitro Deck's release. The new model features improved ergonomics, including an adjusted placement of the right thumbstick for more intuitive, symmetrical gameplay. A standout feature of the Nitro Deck+ is its ability to connect directly to a TV without an external dock, using an integrated USB-C output and an included USB-C to HDMI adaptor.

Google expresses deep regret: Gemini image generation paused for rework
In a new announcement by Google, Senior Vice President Prabhakar Raghavan revealed that the Gemini conversational app (formerly known as Bard) has temporarily halted its image generation feature for people. This decision comes after user feedback highlighted inaccuracies and offensive content in some generated images.
Launched three weeks ago, the feature was built on the Imagen 2 AI model and aimed to provide diverse and accurate representations of people. However, it fell short, producing images that were not only incorrect but also potentially harmful.
Best Windows apps this week
Five-hundred-and-eighty-three in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
If you still run older versions of Windows 11, you may be upgraded automatically and without any say in the matter. It is still a mystery why Microsoft is not revealing the name of the next feature update for Windows 11. It could be the Windows 11 2024 Update.

The impact of AI on cybersecurity
The market for AI in cybersecurity is expected to reach more than $133 billion by 2030 according to a new report from Techopedia.
There's both a positive and negative impact from AI use. Hackers using AI has fueled a huge rise in cybercrime, expected to reach a massive $9.22 trillion cost to internet users in 2024, with the vast majority (85 percent) of cybersecurity professionals blaming AI. This rise is for these key reasons: AI increases the speed and volume of attacks, it adapts to specific defenses, and it creates more sophisticated, personalized attacks.

Why use of Apple devices is growing in the enterprise [Q&A]
The use of Apple devices in the enterprise has increased in recent years. But what's behind this trend and how much impact is it having?
We spoke to Weldon Dodd, SVP of community at Apple device management and security specialist Kandji, to discover how Apple has become a strategic choice for businesses, leading to increased employee productivity and even additional revenue opportunities.

Google Pay app being killed off in USA
Google Pay, the digital payment service that has been around for over a decade, is being killed. Starting June 4, 2024, the standalone Google Pay app will no longer be available for use in the United States. But don’t worry, Google Wallet is stepping up to take its place, offering a platform for storing payment cards, transit passes, and more.
So, what’s the deal with this change? Google Wallet is apparently five times more popular than the Google Pay app in the U.S., so it seems like a pretty logical move. Until June 4, 2024, you can still manage your Google Pay balance in the app. After that, you’ll need to head over to the Google Pay website for balance management and bank transfers.

Get 'Learn Java with Projects' (worth $44.99) for FREE
Learn Java with Projects stands out in the world of Java guides; while some books skim the surface and others get lost in too much detail, this one finds a nice middle ground.
You’ll begin by exploring the fundamentals of Java, from its primitive data types through to loops and arrays. Next, you’ll move on to object-oriented programming (OOP), where you’ll get to grips with key topics such as classes, objects, encapsulation, inheritance, polymorphism, interfaces, and more.
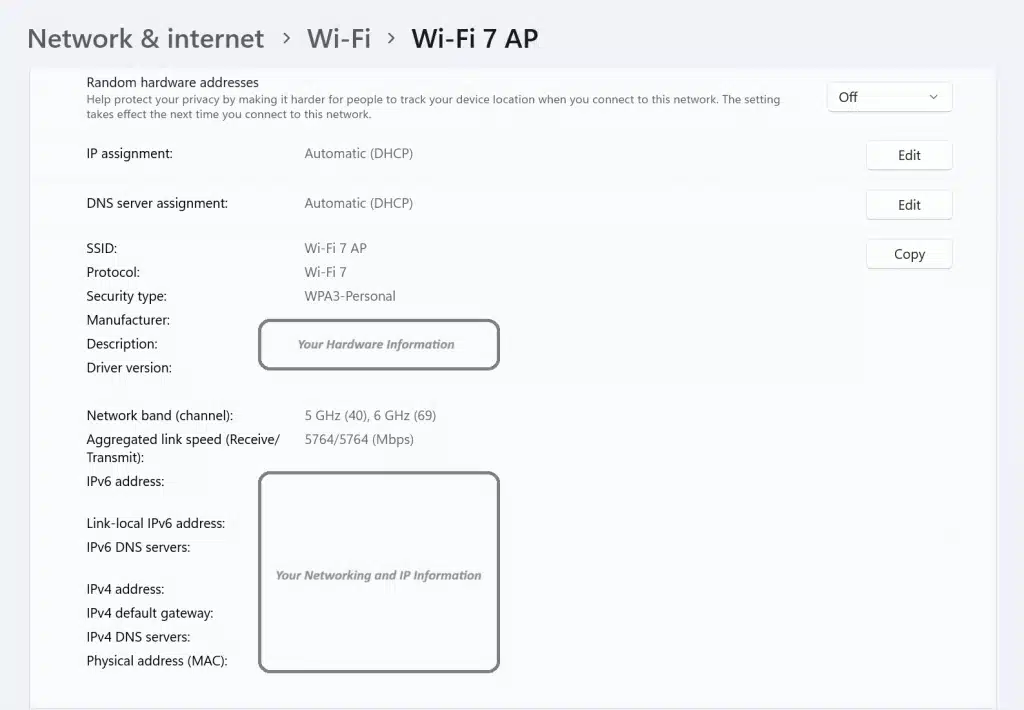
Windows 11 gains support for Wi-Fi 7
Wi-Fi 7, also known as IEEE 802.11be Extremely High Throughput (EHT), is the next generation of wireless technology. It builds on the innovations of Wi-Fi 6 and Wi-Fi 6E and promises “unprecedented speed, reliability, and efficiency for wireless devices”.
Starting today, Microsoft has introduced support for Wi-Fi 7 to the latest Windows 11 Insider build on the Canary Channel.

YEYIAN launches SHIFT 3-in-1 RGB gaming mouse and FlexCam 2K webcam
YEYIAN GAMING, a provider of pre-built gaming PCs, peripherals, and components, has launched two new products: the SHIFT 3-in-1 RGB gaming mouse and the FlexCam 2K streaming camera. These products aren’t just designed for gamers, but content creators and influencers too.
The SHIFT 3-in-1 RGB Gaming Mouse features customizable options, allowing users to adjust mouse dynamics by swapping switches. It comes with RGB lighting, a DPI levels indicator, and wireless charging capabilities, all controlled through a customizable app. The FlexCam Streaming Camera offers 2K resolution, surround LED light, a built-in mic, and intelligent remote control. Both products are compatible with various operating systems and platforms and are designed with a modern aesthetic.

21 new malware families for Mac systems discovered in 2023
Apple devices have historically had a reputation for being immune to malware, but a new report from Jamf reveals that it's tracked 300 malware families on macOS and found 21 new ones in 2023.
Jamf's latest Security 360 report examined a sample of 15 million desktop computers, tablets and smartphone devices they protect, across 90 countries and multiple platforms (macOS, iOS/iPad, Android and Windows).

Cybersecurity professionals believe AI will significantly affect their jobs
With responses from more than 1,100 cybersecurity professionals, a new survey reveals that 88 percent of respondents believe that AI will significantly impact their jobs, now or in the near future.
The study from ISC2 shows 35 percent have already witnessed its effects. However, views on exactly what the implications of AI might be are mixed.

KDE Slimbook V Linux laptop challenges Microsoft’s Windows 11 dominance
In a world dominated by Windows laptops, the KDE Slimbook V emerges as a compelling alternative, blending cutting-edge hardware with the freedom of open-source software. This collaboration between Slimbook and KDE brings to the table a Linux machine that's not just about performance but also about user choice and privacy.
At the heart of the KDE Slimbook V lies an AMD 7840HS CPU, boasting 8 cores and 16 threads, ready to tackle everything from office tasks to code compilation. Paired with the impressive AMD 780M GPU, equipped with 12 cores and RDNA 3, this laptop promises smooth gaming and 3D rendering experiences, challenging the notion that Linux laptops can't keep up with their Windows counterparts in terms of graphics performance.



