
Roku surpasses 80 million active accounts
Roku has achieved a significant milestone, boasting over 80 million active accounts worldwide! This achievement highlights the shifting consumer preference towards streaming, with Roku being at the forefront of this transformation.
In an unprecedented feat, Roku users streamed more than 100 billion hours of content in 2023, averaging a record 4.1 hours per day per account in the fourth quarter. In the United States, Roku's active account base now surpasses the combined subscribers of the six largest traditional pay-TV providers.

Leveraging threat intelligence for regulatory compliance
The US Government recently announced that state-sponsored Chinese cyber group Volt Typhoon has compromised multiple critical infrastructure organizations’ IT networks in the US and is preparing “disruptive or destructive cyber attacks” against communications, energy, transport, water and waste water systems.
The announcement, which was supported by national cybersecurity agencies in Australia, Canada, UK, and New Zealand, is a sobering reminder that modern life relies on digital networks. From healthcare, banking, and socializing, to energy, water, local and national government -- everything has a digital aspect. But while digitization has delivered great leaps forward in convenience, speed, and efficiency, it has also introduced risk. Malicious forces wanting to disrupt economies, governments, and people, know that targeting digital networks is the quickest route to maximum cross-border disruption.

Putting a value on open source -- how much is free software worth?
According to a new report by Harvard Business School and University of Toronto researchers,open source contributes trillions of dollars to the global economy. If you look at the direct supply-side valuation for widely used open source software, the valuation is $4.15billion. If you look at the demand-side figures, which cover all the indirect value generated by use of open source, open source software is worth $8.8trillion. When global gross domestic product for 2024 is estimated to be $109trillion, the value of open source comes into far sharper view.
Alongside this valuation, the report authors estimate that -- if open source did not exist -- companies would have to spend around 3.5 times more on their IT and technology investments to get the same results.
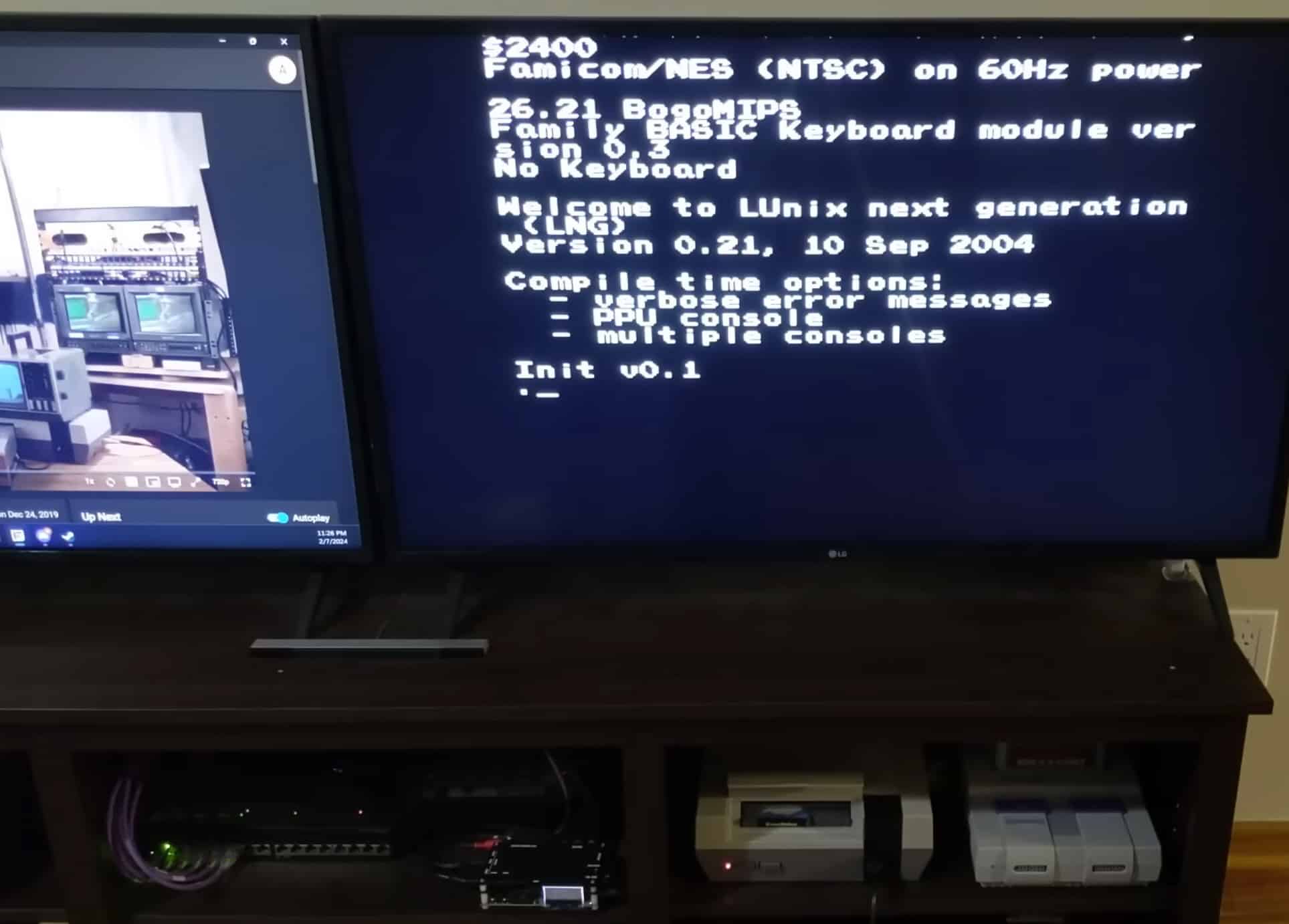
Can Linux run on Nintendo’s ancient NES game console? Someone decided to try
Inspired by the age-old question, "Can it run Linux?", an intrepid YouTuber called DeCrAzYo successfully managed to get a "Unix-like" operating system up and running on that classic 1980s Nintendo games console, the NES. There was no cheating involved either. He didn't take any shortcuts by modifying the console's internal components or by sneaking a Raspberry Pi into the mix.
His goal was to have the operating system's code executed directly via the NES processor using no more hardware than a typical game cartridge would offer, and that's exactly what he managed.

Ransomware declined in January -- but don't celebrate just yet
The latest ransomware report from GuidePoint Security shows a decline in activity in January compared to the final quarter of last year, with a drop in the total number of posted victims by 33 percent and 60 percent relative to December and November 2023.
However, this is consistent with the trends of January of 2022 and 2023, both of which also followed heightened Q4 activity from the previous year.

Forest outages risk axing enterprise AD systems
A 'forest' -- in case you didn't know -- is the top-level logical container in an Active Directory configuration that holds domains, users, computers, and group policies.
This level presents a security challenge and a new survey of 1,000 IT professionals from Cayosoft reveals a 172 percent increase in forest-wide Active Directory outages since 2021.

Oladance unveils OWS Sports Open Wearable Stereo Bluetooth earphones
Oladance has rocked the open ear audio technology market with its development of Open Wearable Stereo (OWS). Unlike bone conduction technology, Oladance OWS utilizes air conduction to deliver a three-dimensional sound effect, which is designed to be more comfortable over extended periods.
Oladance's approach with OWS technology is to provide users with a connection to their surroundings that is both open and safe. Their products are designed to rest on the ear, avoiding the ear canal, which addresses potential discomfort, irritation, or hearing damage from long-term earphone use. Additionally, the Oladance app enhances the user experience by offering personalization options, including four sound modes, sound balance, and gesture and function controls.

Cyber 'ad-versaries' adopt professional marketing techniques
A new report from HP Wolf Security shows cybercrime groups are using professional advertising tools to optimize their malware campaigns and convince users to take the bait.
The report identifies the DarkGate campaign which uses ad tools to sharpen attacks. Malicious PDF attachments, posing as OneDrive error messages, direct users to sponsored content hosted on a popular ad network. This leads to DarkGate malware which hands backdoor access to cybercriminals into networks, exposing victims to risks like data theft and ransomware..
Google thinks ChromeOS Flex could replace Windows 10 or Windows 11 on your PC, or even macOS on your Mac
With the end of support for Windows 10 approaching, and the launch of Windows 11 24H2 not being an option for many people because of hardware compatibility changes, Google is seizing the opportunity to push its own ChromeOS Flex.
ChromeOS Flex is Google's tweaked version of the ChromeOS operating system that can be installed on x86 hardware. The company is pitching its software at businesses and organizations promising that it has "been built with security as a first principle, not an afterthought". The self-promotion is to be found on the Chrome Enterprise blog, but there is nothing to stop home users from replacing Windows or macOS with ChromeOS Flex.
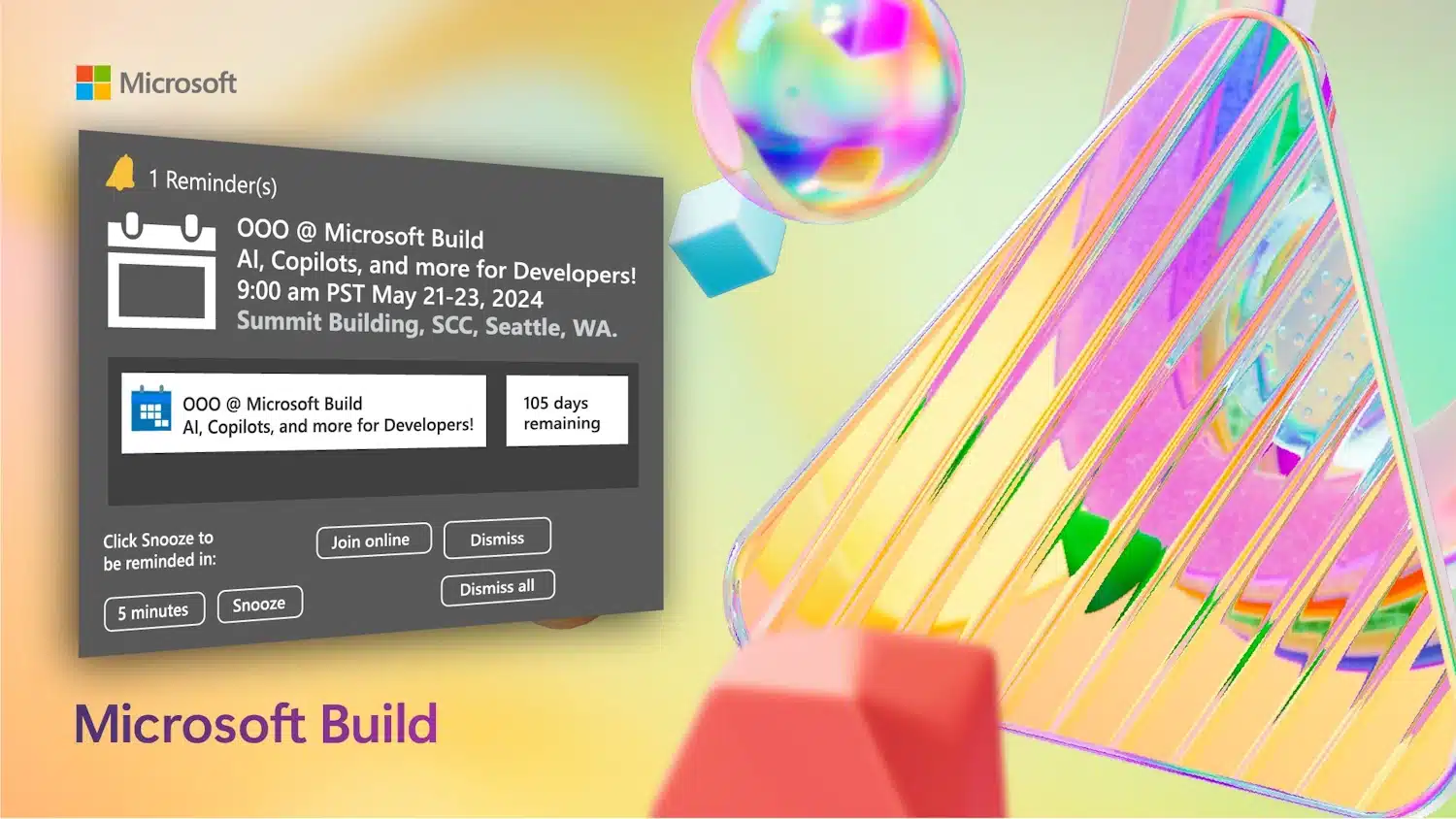
Microsoft Build 2024 confirmed for May, with 'AI, Copilots, and more' for developers
Microsoft has confirmed the dates and location of this year's Build conference for developers. The event will be held from May 21 to 23 in the Seattle Convention Center's Summit building, and it may be a chance for everyone to learn more about not only the future of Windows 11, but also the upcoming Windows 12.
Like last year, Microsoft Build 2024 is an in-person event, although online attendance is also possible. So far, Microsoft is promising "AI, Copilots, and more for Developers" and while there are no firm details of precisely what to expect, it is possible to sign up to be notified when registration opens.

Damn Small Linux 2024 returns to breathe new life into old computers -- a feat Microsoft's bloated Windows 11 can't achieve
Damn Small Linux (DSL), a name that should resonate with many veteran tech enthusiasts, has made a triumphant return after a 12-year absence (albeit as a pre-release Alpha) in 2024 with a fresh iteration designed for low-spec 32-bit x86 computers. DSL 2024 is a compact Linux-based operating system that packs a punch with a bunch of useful applications, all while maintaining a small footprint.
The new DSL 2024 is not just about nostalgia; it's a practical solution for older computers, keeping them functional and out of landfills. The distribution is tailored to fit on a single CD, with a hard limit of 700MB, a significant jump from its 50MB predecessor but still a marvel in today's gigabyte-centric world. This constraint has led to a meticulous selection of applications that are functional, lightweight, and have low dependencies.

Getting up close and personal: How hyper-personalization is driving the next generation of digital applications
As technology continues to converge with our everyday lives, demand for more intuitive digital services is rising. Consumers now expect brands to provide them with more convenience and relevance than ever before.
Personalization within their digital offerings is a key way for businesses to do this, as McKinsey reports that almost three quarters of buyers now expect personalized interactions. However, personalization is just the beginning. To truly meet customer expectations, organizations must go one step further and aim for hyper-personalization.

The importance of security training in the zero trust era
Momentum for zero trust migration is accelerating across the cybersecurity community. It was a fundamental component of the Biden Administration’s 2023 National Security Strategy. Nearly 90% of global organizations have already started implementing basic aspects of a zero trust security model. And in Forrester’s 2024 predictions report, analysts forecast that dedicated roles with “zero trust” in the title are expected to double over the next year.
This is because the need for zero trust authentication has never been clearer. Conventional network security approaches are increasingly vulnerable in today's cloud enterprise environment, where post-pandemic digital transformations, software supply chains, remote work models and bring-your-own-device policies have widened the attack surface. Cloud-based cyberattacks increased by nearly 50 percent in 2022. Meanwhile, more than 10 million people were impacted by supply chain attacks over the same year.

Get 'Enterprise AI in the Cloud: A Practical Guide to Deploying End-to-End Machine Learning and ChatGPT Solutions' (worth $48.99) for FREE
Enterprise AI in the Cloud is an indispensable resource for professionals and companies who want to bring new AI technologies like generative AI, ChatGPT, and machine learning (ML) into their suite of cloud-based solutions.
If you want to set up AI platforms in the cloud quickly and confidently and drive your business forward with the power of AI, this book is the ultimate go-to guide.

Lexar launches Professional SL600 USB 3.2 Gen 2x2 portable SSD
Today, Lexar launches the Professional SL600. This portable solid state drive is designed to meet the needs of photographers, videographers, content creators, and business professionals. The new USB-C SSD boasts USB 3.2 Gen 2x2 technology, delivering impressive read and write speeds of up to 2000MB/s.
The Lexar Professional SL600 portable SSD is not only fast but also built to withstand the rigors of travel and on-location work. Its durable aluminum enclosure provides protection against bumps and drops, while its shock- and vibration-resistance ensures the safety of saved files. Additionally, the drive comes equipped with Lexar DataShield, a 256-bit AES encryption software, offering an extra layer of security for sensitive files.



